hexsha
stringlengths 40
40
| size
int64 5
1.04M
| ext
stringclasses 6
values | lang
stringclasses 1
value | max_stars_repo_path
stringlengths 3
344
| max_stars_repo_name
stringlengths 5
125
| max_stars_repo_head_hexsha
stringlengths 40
78
| max_stars_repo_licenses
sequencelengths 1
11
| max_stars_count
int64 1
368k
⌀ | max_stars_repo_stars_event_min_datetime
stringlengths 24
24
⌀ | max_stars_repo_stars_event_max_datetime
stringlengths 24
24
⌀ | max_issues_repo_path
stringlengths 3
344
| max_issues_repo_name
stringlengths 5
125
| max_issues_repo_head_hexsha
stringlengths 40
78
| max_issues_repo_licenses
sequencelengths 1
11
| max_issues_count
int64 1
116k
⌀ | max_issues_repo_issues_event_min_datetime
stringlengths 24
24
⌀ | max_issues_repo_issues_event_max_datetime
stringlengths 24
24
⌀ | max_forks_repo_path
stringlengths 3
344
| max_forks_repo_name
stringlengths 5
125
| max_forks_repo_head_hexsha
stringlengths 40
78
| max_forks_repo_licenses
sequencelengths 1
11
| max_forks_count
int64 1
105k
⌀ | max_forks_repo_forks_event_min_datetime
stringlengths 24
24
⌀ | max_forks_repo_forks_event_max_datetime
stringlengths 24
24
⌀ | content
stringlengths 5
1.04M
| avg_line_length
float64 1.14
851k
| max_line_length
int64 1
1.03M
| alphanum_fraction
float64 0
1
| lid
stringclasses 191
values | lid_prob
float64 0.01
1
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
9b914c7ca67354505213ab6301bf2af7b53e105e | 881 | md | Markdown | CHANGELOG.md | Japannext/hazelsync | 5a852c1b3e20af98f79f540ced3934b5116924fd | [
"Apache-2.0"
] | null | null | null | CHANGELOG.md | Japannext/hazelsync | 5a852c1b3e20af98f79f540ced3934b5116924fd | [
"Apache-2.0"
] | null | null | null | CHANGELOG.md | Japannext/hazelsync | 5a852c1b3e20af98f79f540ced3934b5116924fd | [
"Apache-2.0"
] | null | null | null | ## v1.3.0
### Features
* Metrics for backup and stream actions using Prometheus PushGateway
* Experimental metrics for backup and stream actions using InfluxDB v2 API
### Changes
* Centralizing log management and making it configurable from the main config file
## v1.2.0
### Features
* Support for PostgreSQL backups by doing rsync with WAL "streaming" (more frequent cronjobs)
* Better handling of plugins for hazel-ssh script: now any plugin can define a behavior for hazel-ssh
## v1.1.0
### Features
* Rsync-based backup support
* Support for pre/post scripts
* Hashicorp Vault backup support
* A client SSH helper to help with authorization on the host
* Support for integration with the rsync plugin
* Support for locking during backup
* Plugin system for backup/restore methods (job plugin) and the
storage backend (backend plugin)
* Support for ZFS backend
| 27.53125 | 101 | 0.766175 | eng_Latn | 0.959087 |
9b916bd2a1e5da933d972419791dbd76f3ef6fba | 4,080 | md | Markdown | jinahub/encoders/image/ImageTorchEncoder/README.md | vivek2301/executors | 8159681d68408ab8f797497bc3374be77e6ca392 | [
"Apache-2.0"
] | 4 | 2021-07-01T13:05:51.000Z | 2022-03-15T02:27:58.000Z | jinahub/encoders/image/ImageTorchEncoder/README.md | vivek2301/executors | 8159681d68408ab8f797497bc3374be77e6ca392 | [
"Apache-2.0"
] | 11 | 2021-06-22T13:53:48.000Z | 2022-02-21T10:51:53.000Z | README.md | jina-ai/executor-image-torch-encoder | 69bd316f46282df8e32f73ebf47b7bf70089abcf | [
"Apache-2.0"
] | null | null | null | # ImageTorchEncoder
**ImageTorchEncoder** wraps the models from [torchvision](https://pytorch.org/vision/stable/index.html).
**ImageTorchEncoder** receives `Documents` with `blob` attributes of type `ndarray` and shape Height x Width x Channel.
The `blob` attribute represents the image to be encoded by **ImageTorchEncoder**. This Executor will encode each
`blob` into an `ndarray` of shape `embedding_dim` and store them in the `embedding` attribute of the `Document`.
## Usage
Use the prebuilt images from Jina Hub in your Python codes, add it to your Flow and encode an image:
```python
from jina import Flow, Document
f = Flow().add(uses='jinahub+docker://ImageTorchEncoder', uses_with={'model_name': 'resnet50'})
doc = Document(uri='my_image.png')
doc.convert_image_uri_to_blob()
with f:
f.post(on='/index', inputs=doc, on_done=lambda resp: print(resp.docs[0].embedding))
```
### Encoding example
After creating a Flow, prepare your Documents to encode. They should have the blob attribute set with shape
Height x Width x Channel. Then, we can start the Flow and encode the Documents. By default, any endpoint will encode
the Documents:
```python
import numpy as np
from jina import Flow, Document
f = Flow().add(uses='jinahub+docker://ImageTorchEncoder')
doc = Document(blob=np.ones((224, 224, 3), dtype=np.uint8))
with f:
f.post(on='/index', inputs=doc, on_done=lambda resp: print(resp.docs[0].embedding))
```
### Set `volumes`
With the `volumes` attribute, you can map the torch cache directory to your local cache directory, in order to avoid downloading
the model each time you start the Flow.
```python
from jina import Flow
flow = Flow().add(
uses='jinahub+docker://ImageTorchEncoder',
volumes='/your_home_folder/.cache/torch:/root/.cache/torch'
)
```
Alternatively, you can reference the docker image in the `yml` config and specify the `volumes` configuration.
`flow.yml`:
```yaml
jtype: Flow
pods:
- name: encoder
uses: 'jinahub+docker://ImageTorchEncoder'
volumes: '/your_home_folder/.cache/torch:/root/.cache/torch'
```
And then use it like so:
```python
from jina import Flow
flow = Flow.load_config('flow.yml')
```
### Returns
`Document` with `embedding` fields filled with an `ndarray` of shape `embedding_dim` (size depends on the model) with `dtype=float32`.
### Supported models:
You can specify the model to use with the parameter `model_name`:
```python
import numpy as np
from jina import Flow, Document
f = Flow().add(
uses='jinahub+docker://ImageTorchEncoder',
uses_with={'model_name': 'alexnet'}
)
doc = Document(blob=np.ones((224, 224, 3), dtype=np.uint8))
with f:
f.post(on='/index', inputs=doc, on_done=lambda resp: print(resp.docs[0].embedding))
```
`ImageTorchEncoder` supports the following models:
* `alexnet`
* `squeezenet1_0`
* `vgg16`
* `densenet161`
* `inception_v3`
* `googlenet`
* `shufflenet_v2_x1_0`
* `mobilenet_v2`
* `mnasnet1_0`
* `resnet18`
By default, `resnet18` is the used model.
You can check the models [here](https://pytorch.org/vision/stable/models.html)
### GPU usage:
To enable GPU, you can set the `device` parameter to a cuda device.
Make sure your machine is cuda-compatible.
If you're using a docker container, make sure to add the `gpu` tag and enable
GPU access to Docker with `gpus='all'`.
Furthermore, make sure you satisfy the prerequisites mentioned in
[Executor on GPU tutorial](https://docs.jina.ai/tutorials/gpu_executor/#prerequisites).
```python
import numpy as np
from jina import Flow, Document
f = Flow().add(
uses='jinahub+docker://ImageTorchEncoder/gpu',
uses_with={'device': 'cuda'}, gpus='all'
)
doc = Document(blob=np.ones((224, 224, 3), dtype=np.uint8))
with f:
f.post(on='/index', inputs=doc, on_done=lambda resp: print(resp.docs[0].embedding))
```
## Reference
- [PyTorch TorchVision Transformers Preprocessing](https://sparrow.dev/torchvision-transforms/)
- [PyTorch TorchVision](https://pytorch.org/vision/stable/index.html)
- [TorchVision models](https://pytorch.org/vision/stable/models.html)
| 28.333333 | 134 | 0.728431 | eng_Latn | 0.820279 |
9b91d4a848335eb9e63a76bdc76dd1c6d082bb21 | 75 | md | Markdown | parser/README.md | johnperry-math/autocxx | 1ebfe2073275cec9569b53026a4ba52da1905678 | [
"Apache-2.0",
"MIT"
] | null | null | null | parser/README.md | johnperry-math/autocxx | 1ebfe2073275cec9569b53026a4ba52da1905678 | [
"Apache-2.0",
"MIT"
] | null | null | null | parser/README.md | johnperry-math/autocxx | 1ebfe2073275cec9569b53026a4ba52da1905678 | [
"Apache-2.0",
"MIT"
] | null | null | null | This crate is a [component of autocxx](https://google.github.io/autocxx/).
| 37.5 | 74 | 0.746667 | eng_Latn | 0.809006 |
9b9257a24000bae7bf18f211affe6770e798841d | 2,807 | md | Markdown | sdk-api-src/content/strmif/nn-strmif-idvdinfo2.md | amorilio/sdk-api | 54ef418912715bd7df39c2561fbc3d1dcef37d7e | [
"CC-BY-4.0",
"MIT"
] | null | null | null | sdk-api-src/content/strmif/nn-strmif-idvdinfo2.md | amorilio/sdk-api | 54ef418912715bd7df39c2561fbc3d1dcef37d7e | [
"CC-BY-4.0",
"MIT"
] | null | null | null | sdk-api-src/content/strmif/nn-strmif-idvdinfo2.md | amorilio/sdk-api | 54ef418912715bd7df39c2561fbc3d1dcef37d7e | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
UID: NN:strmif.IDvdInfo2
title: IDvdInfo2 (strmif.h)
description: The IDvdInfo2 interface reports attributes of a DVD disc or the current state of DVD playback and navigation.
helpviewer_keywords: ["IDvdInfo2","IDvdInfo2 interface [DirectShow]","IDvdInfo2 interface [DirectShow]","described","IDvdInfo2Interface","dshow.idvdinfo2","strmif/IDvdInfo2"]
old-location: dshow\idvdinfo2.htm
tech.root: dshow
ms.assetid: da30d3dc-feec-4f54-b2db-a771ce404286
ms.date: 12/05/2018
ms.keywords: IDvdInfo2, IDvdInfo2 interface [DirectShow], IDvdInfo2 interface [DirectShow],described, IDvdInfo2Interface, dshow.idvdinfo2, strmif/IDvdInfo2
req.header: strmif.h
req.include-header: Dshow.h
req.target-type: Windows
req.target-min-winverclnt: Windows XP [desktop apps \| UWP apps]
req.target-min-winversvr: Windows Server 2003 [desktop apps \| UWP apps]
req.kmdf-ver:
req.umdf-ver:
req.ddi-compliance:
req.unicode-ansi:
req.idl:
req.max-support:
req.namespace:
req.assembly:
req.type-library:
req.lib: Strmiids.lib
req.dll:
req.irql:
targetos: Windows
req.typenames:
req.redist:
ms.custom: 19H1
f1_keywords:
- IDvdInfo2
- strmif/IDvdInfo2
dev_langs:
- c++
topic_type:
- APIRef
- kbSyntax
api_type:
- COM
api_location:
- Strmiids.lib
- Strmiids.dll
api_name:
- IDvdInfo2
---
# IDvdInfo2 interface
## -description
The <code>IDvdInfo2</code> interface reports attributes of a DVD disc or the current state of DVD playback and navigation. The <a href="/windows/desktop/DirectShow/dvd-navigator-filter">DVD Navigator</a> filter implements this interface. <code>IDvdInfo2</code> is the companion interface to <a href="/windows/desktop/api/strmif/nn-strmif-idvdcontrol2">IDvdControl2</a> interface. <code>IDvdInfo2</code> groups the DVD Navigator's "get" methods and <b>IDvdControl2</b> groups the "set" methods. Together they provide DVD navigation and playback functionality beyond the DVD Annex J specification.
<div class="alert"><b>Note</b> The information provided by some of these methods can also be obtained through event notifications sent from the DVD Navigator to the application's message loop. For example, to get the current DVD domain, you can call <a href="/windows/desktop/api/strmif/nf-strmif-idvdinfo2-getcurrentdomain">IDvdInfo2::GetCurrentDomain</a> or you can handle the <a href="/windows/desktop/DirectShow/ec-dvd-domain-change">EC_DVD_DOMAIN_CHANGE</a> event in your application's message loop and extract the new domain from the event's <i>lParam1</i> parameter.</div>
<div> </div>
## -inheritance
The <b>IDvdInfo2</b> interface inherits from the <a href="/windows/desktop/api/unknwn/nn-unknwn-iunknown">IUnknown</a> interface. <b>IDvdInfo2</b> also has these types of members:
## -see-also
<a href="/windows/desktop/DirectShow/dvd-applications">DVD Applications</a>
| 42.530303 | 595 | 0.77378 | eng_Latn | 0.572597 |
9b93c489fdcd8b8e1ba55f152693e09917295348 | 234 | md | Markdown | data/j/2021/1023-germegor.md | ribacq/jirsad-website | 51ff655fad9fb3a48ea2dc49e0b3f412948e86e0 | [
"WTFPL"
] | null | null | null | data/j/2021/1023-germegor.md | ribacq/jirsad-website | 51ff655fad9fb3a48ea2dc49e0b3f412948e86e0 | [
"WTFPL"
] | null | null | null | data/j/2021/1023-germegor.md | ribacq/jirsad-website | 51ff655fad9fb3a48ea2dc49e0b3f412948e86e0 | [
"WTFPL"
] | null | null | null | # 23 octobre 2021 | Germegor
En fait, le nom « La Carmiède » ne me plaît pas du tout, d’ailleurs je confonds toujours avec Cardième ; ça sonne mal dans ma tête. Donc ça repasse au nom original imaginé d’abord, [Germegor](/germegor).
| 58.5 | 203 | 0.74359 | fra_Latn | 0.963112 |
9b958c85dc0a9d978b2befce857da5cdbe5569ab | 7,396 | md | Markdown | docs/Customizing.md | myedibleenso/goosepaper | a914d9c764fb39bb6d62875f73875ffafa6f25fa | [
"Apache-2.0"
] | null | null | null | docs/Customizing.md | myedibleenso/goosepaper | a914d9c764fb39bb6d62875f73875ffafa6f25fa | [
"Apache-2.0"
] | null | null | null | docs/Customizing.md | myedibleenso/goosepaper | a914d9c764fb39bb6d62875f73875ffafa6f25fa | [
"Apache-2.0"
] | null | null | null | # Customizing Your Feed
## Example config
You can choose what content is added to your daily goosepaper by writing your own config-file.
As an example we give the config delivered as an example `example-config.json`:
```json
{
"font_size": 12,
"stories": [
{
"provider": "weather",
"config": { "woe": 2358820, "F": true }
},
{
"provider": "twitter",
"config": {
"usernames": ["axios", "NPR"],
"limit_per": 8
}
},
{
"provider": "wikipedia_current_events",
"config": {}
},
{
"provider": "rss",
"config": {
"rss_path": "https://feeds.npr.org/1001/rss.xml",
"limit": 5
}
},
{
"provider": "reddit",
"config": { "subreddit": "news" }
},
{
"provider": "reddit",
"config": { "subreddit": "todayilearned" }
}
]
}
```
## Look & Feel
### Titles and font size
In the first part of the config you can set global parameters for your goosepaper. These do not need to be set as they have default parameters.
### Goosepaper Title
The title is at the top of the first page if your paper. The default value is "Daily Goosepaper" but you can change it like this:
```json
"title" : "Jordan's Daily Goosepaper"
```
### Subtitle
The subtitle is at the second line at the top of the first page after yout title.
```json
"subtitle" : ""
```
### Font Size
The fontsize determines the fontsize for all text in the goosepaper. Other text will be scaled accordingly, so a large body font will generally correspond (ideally, if the style is well-built) with larger headliner font sizes as well. The default is 12.
```json
"font_size" : 14
```
(This only matters if your output is set as a `.pdf`)
### Styles
There are a few prepackaged stylesheets that can be applied to your goosepaper. The default is `"FifthAvenue"`. You can change this to any of the following:
- Academy
- FifthAvenue
- Autumn
For more information on the styles and to see a gallery of the different stylesheets on the same goosepaper content, see the [Style Gallery](StyleGallery.md) page.
## Stories and StoryProviders
Stories in a Goosepaper are created by a StoryProvider. You can think of a StoryProvider as a "source." So you might have Twitter stories (`TwitterStoryProvider`), some blog posts (`RSSFeedStoryProvider`), etc.
This section aims to be a comprehensive list of all storyproviders and how to configure them.
(This was the case at time of writing.)
In addition to the storyproviders listed here, there is also a separate repository, [auxilliary-goose](https://github.com/j6k4m8/auxiliary-goose/), where you can find additional storyproviders. For info on how to customize these check out the documentation in said repository.
Stories and storyproviders are given in the config-file using the `"stories"`-key in the following way:
(remember correct comma-separation in this file).
```json
"stories" : [
{
"provider" : "Storyprovider1",
"config" : {
"PARAMETER" : "VALUE",
"PARAMETER" : "VALUE"
}
},
{
"provider" : "Storyprovider2",
"config" : {
"PARAMETER" : "VALUE",
"PARAMETER" : "VALUE"
}
},
]
```
Right now, these are the storyproviders built into this repository:
- [CustomText](#CustomText)
- [Reddit](#Reddit)
- [RSS](#RSS)
- [Twitter](#Twitter)
- [Weather](#Weather)
- [Wikipedia Current Events](#Wikipedia)
### <a name="CustomText">CustomTextStoryProvider</a>
```json
"provider": "text"
```
This storyprovider fills paragraphs with your own custom text, or with Lorem Ipsum text if you don't provide anything.
#### Paramaeters:
| Parameter | Type | Default | Description |
| ---------- | ---- | ------- | -------------------------------------------------------------- |
| `headline` | str | None | The text to use. If not provided, the default is Lorem Ipsum. |
| `text` | str | None | The text to use. If not provided, the default is Lorem Ipsum. |
| `limit` | int | 5 | The number of paragraphs to generate, if text is not provided. |
#### Example:
```json
{
"provider": "text",
"config": {
"headline": "This is a headline",
"text": "This is some text"
}
}
```
### <a name="Reddit">Reddit</a>
```json
"provider" : "reddit"
```
This storyprovider gives headlines from a selected subreddit given in config file. The story gives the title, the username of the poster, and some text.
#### Parameters:
| Parameter | Type | Default | Description |
| ---------------- | ---- | ------- | --------------------------------------- |
| `subreddit` | str | None | The subreddit to use. |
| `limit` | int | 20 | The number of stories to get. |
| `since_days_ago` | int | None | If provided, filter stories by recency. |
### <a name="RSS">RSS</a>
```json
"provider" : "rss"
```
Returns results from a given RSS feed. Feed URL must be specified in the config file.
The parameter `rss_path` has to be given a value in configfile.
Default limiting value is `5`.
#### Parameters:
| Parameter | Type | Default | Description |
| ---------------- | ---- | ------- | --------------------------------------- |
| `rss_path` | str | None | The RSS feed to use. |
| `limit` | int | 5 | The number of stories to get. |
| `since_days_ago` | int | None | If provided, filter stories by recency. |
### <a name="Twitter">Twitter</a>
```json
"provider" : "twitter"
```
Returns tweets from given users.
#### Parameters:
| Parameter | Type | Default | Description |
| ---------------- | ---------------- | ------- | ----------------------------------------------------------- |
| `usernames` | str or list[str] | None | Twitter usernames to use. Can be a single username or list. |
| `limit` | int | 8 | The number of stories to get. |
| `since_days_ago` | int | None | If provided, filter stories by recency. |
### <a name="Weather">Weather</a>
```json
"provider" : "weather"
```
Get the weather forecast for the day. This story provider is placed in the "ear" of the Goosepaper front page, as you'd expect on a real newspaper.
The weatherdata for this storyprovider is collected from [www.metaweather.com](https://www.metaweather.com/).
#### Parameters:
| Parameter | Type | Default | Description |
| --------- | ---- | ------- | ----------------------------------------------------------- |
| `woe` | str | None | The WOEID of your location. See [here](www.metaweather.com) |
| `F` | bool | True | If set to True, the forecast will be in Fahrenheit. |
### <a name="Wikipedia">Wikipedia Current Events</a>
```json
"provider" : "wikipedia_current_events"
```
Returns current events section from Wikipedia.
There are no configurable parameters for this story provider.
| 31.742489 | 276 | 0.566793 | eng_Latn | 0.981721 |
9b965325e32bc80afcc45cf2b9fba6401d6c75c3 | 5,959 | md | Markdown | _posts/2019-04-15-19_ipfs_exchange_layer.md | uni2u/uni2u.github.io | 39951485c040ca644c507db2976210400e525260 | [
"MIT"
] | null | null | null | _posts/2019-04-15-19_ipfs_exchange_layer.md | uni2u/uni2u.github.io | 39951485c040ca644c507db2976210400e525260 | [
"MIT"
] | null | null | null | _posts/2019-04-15-19_ipfs_exchange_layer.md | uni2u/uni2u.github.io | 39951485c040ca644c507db2976210400e525260 | [
"MIT"
] | null | null | null | ---
layout: post
title: "IPFS - exchange"
categories:
- IPFS_Review
tags:
- IPFS_exchange
lang: ko
author: "uni2u"
meta: "Springfield"
---
# IPFS 기본 - Exchange 계층
IPFS 의 스위칭 레이어는 **BitSwap 프로토콜**을 통해 피어 노드간에 데이터를 교환합니다. BitTorrent 와 마찬가지로
각 피어 노드는 다운로드하는 동안 다운로드 된 데이터를 다른 피어 노드에 업로드합니다. BitTorrent 프로토콜과 달리 BitSwap 은 시드 파일의 데이터블록에만 국한되지 않습니다.
전체 교환 계층에서 IPFS 의 모든 노드가 마켓을 이루고 있으며 데이터 교환은 Filecoin 이 교환 계층에서 인센티브 계층을 추가합니다. 이 마켓에서 Bitswap 은 두 가지 주요 작업을 수행합니다. 즉, 데이터 블록을 제공하는 피어에 이득 (Filecoin 에서는 코인) 을 주기위한 마켓입니다.
- 네트워크에서 클라이언트 요청 블록을 가져 오기위한 시도
- 소유 블록을 다른 노드로 보냅니다
## 1. BitSwap 프로토콜
BitSwap 은 IPFS 노드의 블록 교환 정보를 기록합니다. 소스 코드 구조는 다음과 같습니다:
``` go
// Additional state kept
type BitSwap struct {
ledgers map[NodeId]Ledger
// Ledgers known to this node, inc inactive
// 노드 명세
active map[NodeId]Peer
// currently open connections to other nodes
// 현재 연결된 피어
need_list []Multihash
// checksums of blocks this node needs
// 노드가 필요한 블록 데이터 검사 목록
have_list []Multihash
// checksums of blocks this node has
// 노드가 가지고 있는 블록 데이터 검사 목록
}
```
노드가 다른 노드로부터 데이터 블록을 요청하거나 다른 노드에 데이터 블록을 제공 할 필요가 있을 때 다음과 같이 _BitSwap_ 메시지를 보내고 이 메시지는 주로 두 부분으로 구성됩니다. 원하는 데이터 블록 목록 (want_list)과 해당 데이터 블록입니다. 전체 메시지는 **Protobuf** 를 사용하여 인코딩 됩니다:
```protobuf
message Message {
message Wantlist {
message Entry {
optional string block = 1; // the block key
optional int32 priority = 2; // the priority (normalized). default to 1
// 우선 순위 설정, 기본값 = 1
optional bool cancel = 3; // whether this revokes an entry
// 취소
}
repeated Entry entries = 1; // a list of wantlist entries
optional bool full = 2; // whether this is the full wantlist. default to false
}
optional Wantlist wantlist = 1;
repeated bytes blocks = 2;
}
```
BitSwap 시스템은 매우 중요한 두 가지 모듈이 있습니다. 요구 사항 관리자 (**Want-Manager**) 와 의사 결정 엔진 (**Decision-Engine**) 이 있습니다. Want-Manager 는 노드가 데이터를 요청할 때 로컬로 해당 결과를 리턴하거나 적합한 요청을 발행하고 후자 (Decision-Engine) 는 다른 노드에 자원을 할당하는 방법을 결정합니다. 노드가 _want_list_ 를 포함하는 메시지를 수신하면 메시지는 의사 결정 엔진으로 전달되고 엔진은 노드의 BitSwap 명세서는 요청을 처리하는 방법을 결정합니다. 전체 프로세스는 다음과 같습니다.
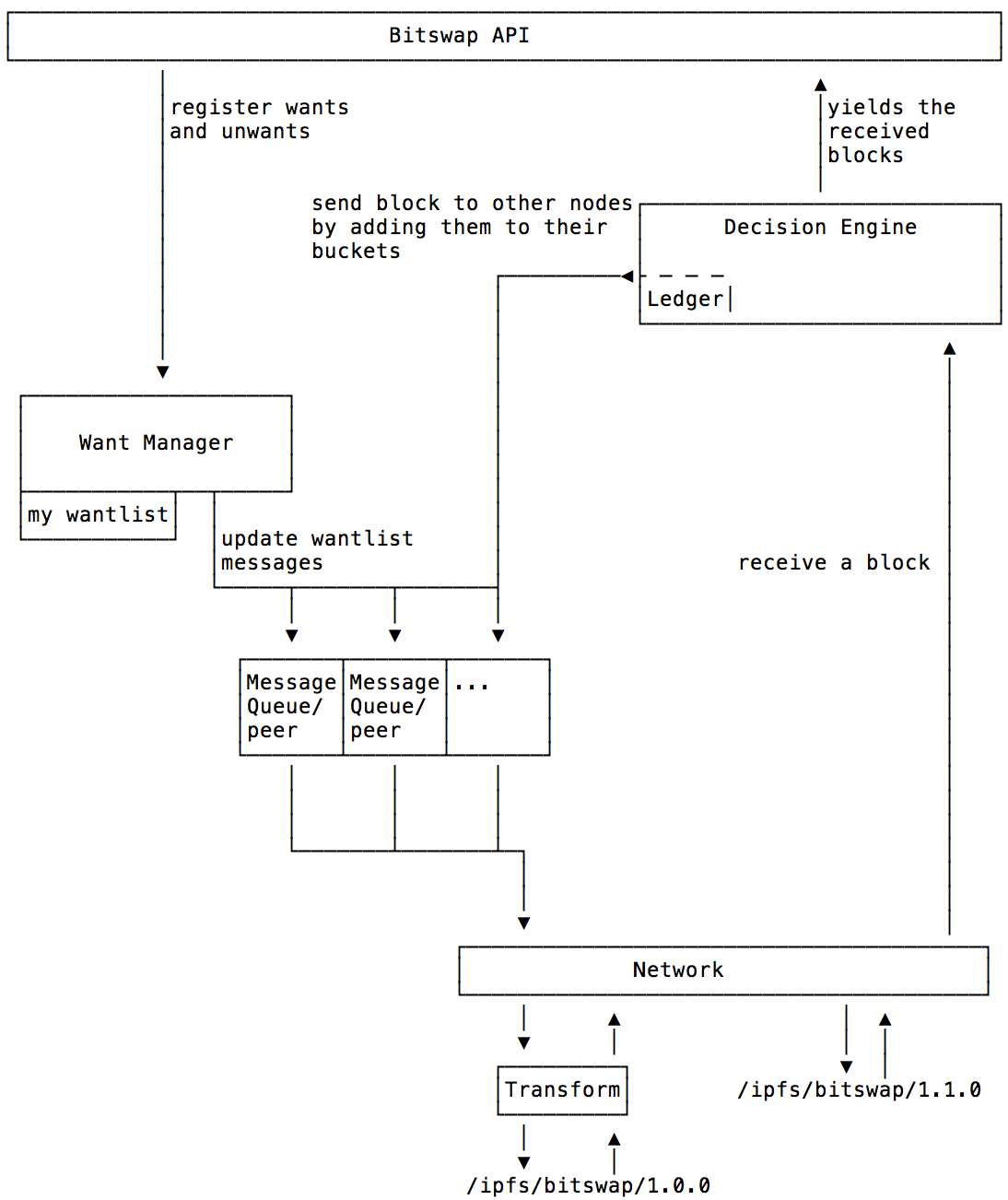
위의 프로토콜 흐름도를 통해 BitSwap 데이터 교환의 전체 과정과 peer-to-peer 연결의 수명주기를 볼 수 있습니다. 이 라이프 사이클에서 피어 노드는 일반적으로 네 가지 상태를 거칩니다:
- Open: 전송할 BitSwap 명세 상태는 연결이 설정 될 때까지 피어 노드간에 열립니다.
- Sending: want_list 및 데이터 블록은 피어 노드간에 전송됩니다.
- Close: 피어 노드는 데이터를 보낸 후에 연결을 끊습니다.
- Ignored: 피어 노드는 타임 아웃, 자동 및 낮은 크레딧과 같은 요인으로 인해 무시됩니다.
피어 노드의 소스 구조를 결합하여 IPFS 노드가 서로를 찾는 방식을 분석합니다:
``` go
type Peer struct {
nodeid NodeId
ledger Ledger
// Ledger between the node and this peer
// 노드와 피어 노드 간의 청구 명세서
last_seen Timestamp
// timestamp of last received message
// 마지막으로받은 메시지의 타임 스탬프
want_list []Multihash
// checksums of all blocks wanted by peer
// includes blocks wanted by peer's peers
// 모든 블록 검사 필요
}
// Protocol interface:
interface Peer {
open (nodeid :NodeId, ledger :Ledger);
send_want_list (want_list :WantList);
send_block (block :Block) -> (complete :Bool);
close (final :Bool);
}
```
### 1.1 Peer.open(NodeID,Ledger)
노드가 연결을 설정하면 보낸 노드는 _BitSwap_ 명세서를 초기화 합니다. 피어에 대한 명세서를 보관할 수 있습니다. 새 명세서를 새로 만들 수도 있습니다. 이는 노드 청구 일관성 문제에 따라 다릅니다. 송신 노드는 수신 노드에 통지하기 위해 청구서를 담고있는 공개 메시지를 전송할 것입니다. 수신 노드가 _Open_ 메시지를 수신 한 후 이 연결 요청을 수락할지 여부를 선택할 수 있습니다.
수신자는 송신자의 로컬 명세 데이터를 체크하는데 신뢰할 수 없는 노드를 판명합니다. 즉 전송 타임 아웃, 매우 낮은 신용 점수 및 큰 부채 비율에 기초하여 신뢰할 수 없는 노드인 것으로 판명되면 수신기는 ignore_cooldown 을 통해 이 요청을 무시하여 연결을 끊습니다. 이 목적은 부정 행위를 방지하는 것입니다.
연결이 성공하면 수신자는 로컬 명세서를 사용하여 피어 개체를 초기화하고 last_seen 타임 스탬프를 업데이트 한 다음 수신 된 명세서를 자체 명세서와 비교합니다.
두 명세서가 정확히 같으면 연결이 Open 하고 명세가 정확히 동일하지 않은 경우 노드는 새로운 명세서를 생성하고 이 명세서에 동기화를 전송합니다. 이는 앞에서 언급한 송신자 노드와 수신자 노드의 명세 일관성 문제를 보장합니다.
### 1.2 Peer.send_want_list(WantList)
연결이 이미 Open 상태에 있으면 송신자 노드는 want_list 를 연결된 모든 수신 노드에 브로드캐스트합니다. 동시에 want_list 를 수신 한 후 수신 노드는 수신자가 원하는 데이터 블록이 있는지 여부를 확인한 다음 _BitSwap_ 정책을 사용하여 데이터 블록을 보내고 전송합니다.
### 1.3 Peer.send_block(Block)
블록을 보내는 방법 로직은 매우 간단합니다. 기본적으로 송신 노드는 데이터 블록만 전송합니다. 모든 데이터를 수신 한 후 수신 노드는 Multihash 를 계산하여 예상되는 것과 일치하는지 확인한 다음 수신 확인을 반환합니다. 블록 전송을 완료 한 후, 수신 노드는 블록 정보를 need_list 에서 have_list 로 이동시키고 수신 노드와 송신 노드 모두 명세서 목록을 동시에 갱신한다. 전송 확인이 실패하면 전송 노드가 오작동하거나 의도적으로 수신 노드의 행동을 공격 할 수 있으며 수신 노드는 추가 거래를 거부 할 수 있습니다.
### 1.4 Peer.close(Bool)
peer-to-peer 연결은 두 가지 경우에 닫아야 합니다.
- **silent_want** (시간초과): 상대방으로 부터 메시지를 받지 못했을 때 노드는 `Peer.close (false)` 를 발행
- **_BitSwap_ 종료** (노드 종료): 노드는 `Peer.close (true) ` 발행
P2P 네트워크의 경우 '모든 사람들이 자신의 데이터를 공유하도록 동기를 부여하는 방법' 및 'P2P 소프트웨어의 자체 데이터 공유 전략을 이용하는 방법' 이 있습니다. IPFS 에서도 마찬가지입니다. 그 중 _BitSwap_ 전략 시스템은 '신용', '전략' 및 '명세서' 의 세 부분으로 구성됩니다.
## 2. BitSwap 신뢰 시스템
_BitSwap_ 프로토콜은 노드가 데이터를 공유하도록 동기를 부여 할 수 있어야 합니다. IPFS 는 노드 간의 데이터 전송 및 수신을 기반으로 신용 시스템을 구축합니다.
- 다른 노드로 데이터를 보내면 신용도가 증가합니다.
- 다른 노드로부터 데이터를 수신하면 신용도가 낮아집니다.
노드가 데이터만 수신하고 데이터를 업로드하지 않으면 신용도는 다른 노드에 의해 낮추어 집니다. 이것은 사이버 공격을 효과적으로 방지 할 수 있습니다.
## 3. BitSwap 정책
_BitSwap_ 신용 시스템으로 서로 다른 정책으로 구현할 수 있습니다. 각 정책은 시스템의 전반적인 성능에 다른 영향을줍니다. 정책의 목표는 다음과 같습니다:
- 노드 데이터 교환의 전반적인 성능과 효율성이 가장 높습니다.
- 데이터를 다운로드만 하고 업로드하지 않는 현상을 방지합니다.
- 일부 공격을 효과적으로 방지합니다.
- 신뢰할 수 있는 노드에 대해 느슨한 메커니즘을 설정합니다.
IPFS 는 whitepaper 에서 몇 가지 참조 정책 메커니즘을 제공합니다. 각 노드는 다른 노드가 주고받는 데이터를 기반으로 신용 및 부채 비율 (_rb_) 을 계산합니다: `r = bytes_sent / bytes_recv + 1`
데이터 전송 속도 (_P_):
`P (send | r) = 1 - (1 / (1 + exp (6-3r)))`
위 합의에 따르면 r 이 2 보다 크면 전송률 _P (send | r)_ 가 작아 지므로 다른 노드는 데이터를 계속 보내지 않습니다.
## 4. BitSwap 명세
_BitSwap_ 노드는 다른 노드와 통신하는 명세서 (데이터 송수신 레코드) 를 기록합니다. 명세 데이터 구조는 다음과 같습니다.
```go
type Ledger struct {
owner NodeId
partner NodeId
bytes_sent int
bytes_recv int
timestamp Timestamp
}
```
이를 통해 노드는 변조를 피하기 위해 히스토리를 추적 할 수 있습니다. 두 노드간에 연결이 이루어지면 _BitSwap_ 은 서로 결제 정보를 교환하고 원장이 일치하지 않으면 원장은 지워지고 다시 예약되며 악의적 노드는 이 원장을 잃어 버리고 채무를 청산 할 것으로 예상됩니다. 다른 노드는 이것을 기록 할 것이며 파트너 노드는 위법 행위로 취급하여 거래를 거부 할 수 있습니다.
| 35.052941 | 328 | 0.689377 | kor_Hang | 1.00001 |
9b96dbc33cd0c38c28e149bd1d86cf55b2e6d1da | 265 | md | Markdown | exampleSite/content/english/blog/lecture5.md | chetanpandey1266/meghna-hugo | becd816db1b18ba347b28445479896f41da01c42 | [
"MIT"
] | null | null | null | exampleSite/content/english/blog/lecture5.md | chetanpandey1266/meghna-hugo | becd816db1b18ba347b28445479896f41da01c42 | [
"MIT"
] | null | null | null | exampleSite/content/english/blog/lecture5.md | chetanpandey1266/meghna-hugo | becd816db1b18ba347b28445479896f41da01c42 | [
"MIT"
] | null | null | null | ---
title: "Lecture 5: Classification with linear models"
date: 2018-09-12T12:52:36+06:00
image_webp: images/blog/lecture5.webp
image: images/blog/lecture5.jpg
video1: ""
video2: ""
slide1: ""
slide2: ""
author: John Doe
description : "This is meta description"
--- | 22.083333 | 53 | 0.728302 | eng_Latn | 0.268989 |
9b9860273acadf394ef96685c4ed9d01c0153ad0 | 74,151 | markdown | Markdown | _posts/2007-10-31-enhanced-communication-platform-and-related-communication-method-using-the-platform.markdown | api-evangelist/patents-2007 | da723589b6977a05c0119d5476325327da6c5a5c | [
"Apache-2.0"
] | 1 | 2017-11-15T11:20:53.000Z | 2017-11-15T11:20:53.000Z | _posts/2007-10-31-enhanced-communication-platform-and-related-communication-method-using-the-platform.markdown | api-evangelist/patents-2007 | da723589b6977a05c0119d5476325327da6c5a5c | [
"Apache-2.0"
] | null | null | null | _posts/2007-10-31-enhanced-communication-platform-and-related-communication-method-using-the-platform.markdown | api-evangelist/patents-2007 | da723589b6977a05c0119d5476325327da6c5a5c | [
"Apache-2.0"
] | 2 | 2019-10-31T13:03:32.000Z | 2020-08-13T12:57:02.000Z | ---
title: Enhanced communication platform and related communication method using the platform
abstract: Pre-authorized communication services and/or transactions are provided via a plurality of networks in response to a request received from a user to provide at least one of a communication service, a transaction and user account information via a plurality of networks of different types. Prior to processing the request, there is verification of the user's authorization to receive the at least one of the communication service, the transaction, and the user account information, and that an account associated with the user has a sufficient amount currently available for payment of the at least one of the communication service and the transaction. After verification, an authorized account associated with the user is charged in real time as the at least one of the communication service and the transaction is provided.
url: http://patft.uspto.gov/netacgi/nph-Parser?Sect1=PTO2&Sect2=HITOFF&p=1&u=%2Fnetahtml%2FPTO%2Fsearch-adv.htm&r=1&f=G&l=50&d=PALL&S1=08976947&OS=08976947&RS=08976947
owner: Upaid Systems, Ltd.
number: 08976947
owner_city: Road Town
owner_country: VG
publication_date: 20071031
---
This application is a continuation and claims priority of U.S. patent application Ser. No. 10 684 396 filed Oct. 15 2003 now U.S. Pat. No. 7 308 087 which is a continuation of U.S. patent application Ser. No. 10 114 047 filed Apr. 3 2002 now U.S. Pat. No. 6 714 632 which is a continuation of U.S. patent application Ser. No. 09 851 382 filed May 9 2001 now U.S. Pat. No. 6 381 316 which is a continuation of U.S. patent application Ser. No. 09 395 868 filed Sep. 14 1999 now U.S. Pat. No. 6 320 947 and which claims priority of U.S. Patent Application Ser. Nos. 60 100 440 and 60 100 470 both filed Sep. 15 1998 the contents of each being incorporated herein by reference.
The present invention relates to communication systems for providing services to individual and corporate subscribers worldwide. More specifically the invention relates to an advanced intelligent communication system that provides subscriber requested services through existing communication switches even in those circumstances in which the hardware communication switch is not configured to provide such services. The system supports the use of personal identification number PIN access cards for use in fixed and mobile markets from any communication device located anywhere in the world and provides flexible call processing and switching services that deliver enhanced computer telephony capabilities utilizing standard communication equipment and operating systems.
Advanced communication services such as call forwarding call conferencing and voice mail have long been available to individual and corporate subscribers of telephone services. However because such services are dependent on telephone carrier equipment and because not all telephone switches can presently support all available advanced communication services many subscribers are still unable to take advantage of these services at their home or at their place of business. Furthermore even though a subscriber may have such services available at his or her normal place for communication the services may be unavailable should the user attempt access through another person s communication device a personal computer a portable telephone or a public phone. In other words access to such services is extremely limited B restricted by the equipment in use the equipment offered by the telephone carrier and the prior sign up by the particular subscriber.
Specialized equipment and proprietary software are conventionally used to provide various advanced services on a telephone system such as abbreviated dialing password service automatic alarm multiline hunting call forwarding busy no reply unconditional and selective call accept selective call back distinctive ringing network voice mail and interception service. When an analog telephone switch is used in the communication network as is the case in many remote areas few of these advanced services are available to the customer. Similarly if a basic digital switch is used some of the advanced services described above may not be available depending on the software of the digital switch.
Presently when advanced telephony services are desired to be made available to network customers within an analog switched network a proprietary digital switch must be purchased along with a proprietary computer operating system and proprietary software. If the network uses a digital switch and advanced services are desired to be added to the network a replacement digital switch and supporting software might have to be acquired. In either situation an outdated legacy switch is replaced with a new generation switch. In the alternative some features can be added to an existing digital switch by upgrading the switch and its proprietary software. Whichever upgrade measure is taken the process is expensive and time consuming to acquire install test and maintain the requisite hardware and software. Therefore whether an analog switch is upgraded to a proprietary digital switching platform such as those available from Lucent Technologies or Nortel or an existing digital switch is upgraded to provide additional services significant cost and effort are involved.
Therefore time effort and expenses would be saved if there were a way to provide enhanced communication services to customers without replacing or upgrading existing legacy switches and supporting software. The platform and method hereinafter collectively referred to as the system of the present invention meet such a need by interfacing with older legacy switches whether analog or digital and by operating on industry standard computer platforms that satisfy telephone companies functional and technical requirements.
In addition to hardware and software limitations access to advanced communication services is further limited by the payment platform utilized by the customer. Access to and payment for communication services through the use of prepaid cards such as telephone calling cards is well known in the field of electronic communication. Such prepaid calling cards are sold at department stores grocery stores convenience stores and other places of business. The prepaid calling cards can be produced in any specific amount or denomination such as 10.00 25.00 or 100.00 printed on the card. Also printed on the card are an access telephone number and additional instructional or promotional information. In addition although typically not printed on the card is a personal identification number PIN for authenticating the user. The access telephone number is the number to be initially dialed to interface with a host computer to access the desired communication service. To initiate a connection the card holder first dials the access number often a toll free number second the card holder manually enters the associated PIN and third the card holder dials the telephone number of the location to be called.
Upon verification and authorization of the entered information and the prepaid card balance the user is connected to the network. The access number links the cardholder to the computer host. Magnetic strip or bar code readers may also be used to decode information stored on the card including an account code but the additional step of manually entering a PIN is required by the user to complete a telephone call or another transaction. The PIN is intended to provide secured access to various services and features by limiting those services and features to users presumably authorized by virtue of their knowledge of the correct PIN the PIN being verified to authenticate that the cardholder is a valid user. Once a call is placed using the telephone calling card the charges for the call are billed to the card holder s account or decremented from the card.
However while prepaid calling cards have become a convenient method by which telephone calling services may be made available to customers worldwide regardless of the telephone being used such calling cards do not permit access to more advanced communication services such as voice mail call forwarding or call conferencing. The reason for this limitation is that present networks limit calling card access to simple calls for which the account represented by the card may be either debited or charged. No integrated system exists that links calling card accounts with a database for offering more advanced services such as a mailbox for voice mail messages or a pathway for conference calling or linking telephone numbers for call forwarding. In other words card holders are presently constrained from using the calling card to access contracted advanced communication services from any communication device worldwide for receiving desired advanced communication services.
Another problem associated with the use of telephone calling cards through which advanced communication services may be purchased is the management tracking and accounting of such transactions. This problem arises because most communication systems permitting use of telephone calling cards are concerned primarily with the authorized payment of delivering such services and because prepaid telephone cards often are purchased as a commodity and no linking between card usage and an identifiable account person or corporation can be maintained. In short the user does not have access to a comprehensive customer care system which incorporates the administrative card management account management security customer care and distribution management of a PIN access card system into a single software package on a public switched telephone network PSTN or any other communication network without a need to purchase proprietary application software of the leading communication giants such as Lucent Nortel etc.
The preferred embodiments of the present invention overcome the problems associated with existing mechanisms for delivering advanced communication services to customers with or without use of PIN access cards by providing an easily implemented cost effective open standards telephony solution that provides value added services such as voice mail to people and businesses regardless of the sophistication of the switch to which they are connected at a minimal cost to a local telephone company service provider or the subscribing consumer.
An object of the present invention is to provide enhanced communication services to users regardless of where the users may be located in the world and regardless of the equipment through which the communication services are directed.
Another object of the present invention is to provide enhanced communication services to users through a PIN access card.
A further object of the present invention is to provide enhanced communication services to users through an interactive voice response system.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a method of providing enhanced communication services to users the method including receiving from a user a personal identification number authenticating the personal identification number accepting a request from the user for an enhanced communication service after authentication of the personal identification number verifying that the user is authorized to receive the requested service and that an account linked to the personal identification number has sufficient value to pay for the service providing by an enhanced services platform the enhanced communication service to the user and charging the account for providing the enhanced communication service.
The enhanced communication service preferably is provided through a network including one or more of a landline communication network a wireless communication network a wide area network a global computer network a cable network and a satellite network. Also a high level application programming interface executing on the enhanced services platform independent of any hardware connecting the platform to the network is preferably used in providing the enhanced communication service. Charging for providing the enhanced communication service includes decrementing a charge from a pre paid user account or adding a charge to a credit account. The enhanced communication services provided by the enhanced services platform include outcalling voice mail functions and call conferencing functions. Additionally administration functions card management functions account management functions external carrier and rate plan functions sales administration functions and system security functions are provided with all such enhanced communications services being accessed with a personal identification number access card. The enhanced services platform includes an interactive voice response system and the enhanced communication services are accessed by a user through either an analog switch or a digital switch without upgrading the switch.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a method of providing enhanced communication services to users the method including receiving from a user a request for an enhanced communication service verifying by an enhanced services platform that the user is authorized to receive the enhanced communication service and providing by the enhanced services platform the enhanced communication service to the user through a switch which is not configured to provide the enhanced communication service without the enhanced services platform.
The enhanced communication services provided by the enhanced services platform include call forwarding functions call waiting functions automatic alarm functions abbreviated dialing functions voice mail functions call conferencing functions call acceptance rejection functions call back functions password functions and interception functions.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a telephony platform providing enhanced communication services to users the telephony platform including an input device to receive a personal identification number and an enhanced communication service selection from a user a storage device storing account data related to the user a verification module authenticating the personal identification number verifying that the user is authorized to receive the selected communication service and verifying that the stored account data has a balance sufficient to pay for the selected enhanced communication service and a processor programmed to provide the selected enhanced communication service after the verification module has successfully completed its processing.
The processor is programmed to include the cost of providing the user selected enhanced communication service in the user s account data.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a telephony platform providing enhanced communication services to users the telephony platform including an input device to receive an enhanced communication service selection from a user a storage device storing account data related to the user a verification module verifying that the user is authorized to receive the selected communication service and that the stored account data has an account balance sufficient to pay for the selected enhanced communication service and a processor programmed to provide the selected enhanced communication service after the verification module has successfully completed its processing.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a method of providing enhanced communication services to users the method including receiving from a user a personal identification number authenticating the personal identification number accepting a request from the user for an enhanced communication service verifying that an account linked to the personal identification number has sufficient value to pay for the enhanced communication service and providing by an enhanced services platform the enhanced communication service to the user.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a telephony platform providing enhanced communication services to users the telephony platform including an input device to receive a personal identification number and an enhanced communication service selection from a user a storage device storing an account value linked to the personal identification number a verification module authenticating the personal identification number and verifying that the stored account value has sufficient value to pay for the enhanced communication service and a processor programmed to provide the enhanced communication service.
Objects and advantages of the present invention are achieved in accordance with embodiments of the present invention such as a telephony platform providing enhanced communication services to users the telephony platform including an input device to receive an enhanced communication service selection from a user a storage device storing account data related to the user a verification module verifying that the stored account data has an account balance sufficient to pay for the selected enhanced communication service and a processor programmed to provide the selected enhanced communication service.
In a preferred environment embodiments of the invention allow an access card system to be installed in any telephone network in the world particularly in remote areas of the world where telephones and advanced network equipment are not easily accessible. The system provides advanced telephony services such as outdialing voice mail and call conferencing services to customers with a built in rating engine for calculating usage charges in any available public switched telephone network or any mobile telephone network. Charges for use of the system are preferably handled by an access card system which includes call center services in a comprehensive operations support system that supports all critical business functions from creation to printing distribution sales activation and use of the access card products and a comprehensive customer care system with access to customer care functions via a computer network implementing an easy to use interface such as the world wide web. The system is available for individual home or corporate use.
The system preferably has an architecture supporting both prepaid and postpaid functionality in the same platform regardless of the technological level of the switch utilized in the communication network. Because of this payment versatility the system allows extensive account management functions where management and administrative services provided business customers can differ from those offered home users.
In one embodiment the system connects to an existing public switched telephone network PSTN switch and offers advanced communication services such as voice mail call conferencing call forwarding call waiting call accept call reject call hold call park and automatic alarm transparently to subscribers connected to the PSTN switch without any upgrade in the PSTN switch. The system also provides subscribers with complete control over administrative services through an integrated interactive voice response system and password facility. This allows the PSTN provider to offer advanced communication services without upgrading the switches in the network and thus minimizing investment. These same advanced communication services can be made available by this system to telephony users over the Internet network or any online network without the need of incorporating a traditional PSTN switch in the online network.
Preferred embodiments of the present invention also preferably support multiple vendor computer telephony integration CTI boards. This is achieved through design of a high level application programming interface HAPI that isolates the application software from the board specific application programming interface. Thus the application software runs on most of the major CTI board vendors hardware. Any new CTI board vendor can be supported very quickly due to the design of the HAPI.
While a prepaid telephone calling card is typically a plastic card embossed with an account code and imprinted with an access code many possible techniques exist for utilizing such a concept to purchase communication services. The card may be plastic metal paper or a memory chip with or without a processor. In addition to prepaid cards purchased prior to initiating a request for communication services credit and debit cards are also well known to be utilized as telephone calling cards. For purposes of the preferred embodiments of this invention all types of calling cards will be referred to with the term access card to indicate a device containing an access code and a link to a customer s account for authorized access to and payment for communication services. Such a card encompasses any combination of the features of the previously discussed cards.
A preferred embodiment of the invention is readily implemented on a network by presently available communication apparatuses and electronic components. The preferred embodiments of the invention find ready application in virtually all communication systems including but not limited to private and public telecommunication networks cable networks satellite networks the Internet and other broadcast networks.
Referring now to there is illustrated a block diagram of a telephony platform of a preferred embodiment of the invention which incorporates CallManager and NetManager subsystems for access by any public system telephone network . Within the CallManager subsystem a customer uses a PIN access card to access the computer telephony network through a network of wireline telephones or wireless telephones by first dialing an access number provided to the customer upon purchasing or signing up for the access card . The access card may be a debit card credit card prepaid calling card or limit card which permit expenditures up to a predetermined limit. The card itself may be a plastic or paper card with printed and or encoded information on a magnetic strip or a microchip etc. The access number could be read by the telephone device or with a magnetic or bar code reader or the user can visually read and subsequently dial the access number from information printed on the card. Furthermore access could be directed through a personal computer with the computer automatically dialing the access number upon user command.
The PSTN of the local regional or national telephone company receives the dialed telephone transmission through the local network of wireline telephones through a wireless telephone or through a personal computer not shown coupled to the PSTN via a computer network or a modem. From the PSTN the call is routed by the network to a switch where the switch analyzes the access number and directs the call to a telephone call receiving device outside the telephony platform or to a computer network such as Internet TCP IP network or to the computer telephony interface cards CTI of the telephony platform . For those calls directed to the CTI cards the calls are directed either to the CallManager subsystem of the telephony platform through server or to the NetManager subsystem of the telephony platform through server as determined by the access number utilized. In summary and as will be discussed more thoroughly below the subsystems of the CallManager and the NetManager take control of the call and deliver the desired advanced communication service to the customer through the switch across the PSTN network even when the hardware of the switch is not configured to deliver such services.
The CallManager subsystem on the server includes client application services and Switch Manager services . Both sets of services have the ability to store information in the databases of the server . The Switch Manager services are telephony services directly available to a customer through a PIN access card that include voice mail services call conferencing and outdialing provided by software executing on the telephony platform . The software providing the Switch Manager services includes an interactive voice response system to guide the customer through available options. The client application services are also provided by software executing on the platform and constitute a complete operation support system for use by the customers the sales agents the distributorships and the call center agents see . The client application services include without limitation administration and system configuration call center functionality a card management subsystem including CardManager an account management subsystem an external carrier and rate plan subsystem a sales administration subsystem and a security subsystem. The client application services also provide a graphical user interface not shown and output device not shown for access to customer accounts and to usage information.
The CallManager subsystem manages distribution of the PIN access cards through distributorships although the telephone companies also have the option to distribute PIN access cards to the customers . The distributorships have sales agents that disseminate the PIN access cards to the customers . The sales agents can be persons convenience stores or kiosks located in public areas. If the access cards are prepaid calling cards the customer has the option of buying the cards through the sales agents of the distributorships or directly purchasing the cards from the local regional and central telephone companies .
The printing and creation of cards and billing information are all performed through the operation support subsystems referred to as the Card Manager component of the CallManager . CallManager may include a Billing Module that takes care of the billing aspects of the system. The Billing Module can be a complete billing system which may include a full function rating engine. The rating engine or rate plan can determine the monetary value of a transaction where such determination may be based on but is not limited to the origin of the transaction the destination of the transaction the type of transaction and the time of day and or day of week of the transaction.
Further the rating engine or rate plan can provide for tariff setup and configuration information management for wireless networks. The Billing Module can also include rating engines for functionalities such as long distance calling conferencing and message mapping. Further the Billing Module can provide for real time debit or charge of a customer s associated account after adding a service tax related to the transaction. Finally the Billing Module may also be integrated with a service or transaction provider s own billing system.
The billing module may contain a table for recording call data. The table may contain fields for recording information such as a card corporate ID a card division information a call extension code a call type code a call date a call duration a call destination a call pulse a call amount a call tariff time a call tariff zone a record of whether the call has been billed or not and a bill number.
The billing module may also contain a table for recording home information. The home information table can contain fields such as a home main number a home identification number a title a customer name a customer address a customer city a customer state a customer country a customer zip a customer phone number a customer fax number a customer email address a customer remarks a customer profession a customer last bill date a customer deposit amount a customer credit limit a customer credit limit left a customer current balance a customer number of active cards a customer status and a customer status change date.
The additional telephony services may be divided into access code based services terminating services PIN based services administrative services and intelligent network IN services. The server due to its open architecture design can also upgrade the switching capacity of the regional telephone company by scaling the deployment of the additional telephony and administrative services at the open system client server level rather than at the switch level. Analogous to the databases of PIN based server server has a plurality of databases to store any of the information being fed through the server to the computer telephony services . The clients of the server in addition to the customer include management accounting sales and MIS. Furthermore the NetManager provides administrative and operational client application services similar to some of the services provided under the client application services of CallManager
The access code based services of the computer telephony services of NetManager utilize calling line identification to activate the desired functionality when a predetermined code is dialed. These services include equal access abbreviated dialing automatic wake up service call conference facility billing inquiry long distance ISD with password automated directory inquiry on line help information on demand and Internet telephony.
A prime service of NetManager is equal access whereby any subscriber in any local exchange may select and have access to various long distance carriers available through that exchange. The equal access service enables pointing a subscriber to a long distance carrier effecting a call over the lines of that carrier and billing the call with the long distance carrier. Abbreviated dialing allows the subscriber to dial frequently accessed telephone numbers by dialing only short codes instead of the full telephone number. The subscriber can set or change these codes through the interactive voice response system. As to the automatic wake up service the subscriber can program any time at which he she wants to be awoken or reminded. The subscriber will be rung at the programmed time whether a regular daily time or a single instance. The call conference facility permits the subscriber to initiate conference calls and bring two or more parties into a conference. The subscriber may drop any of the parties from the conference call at any time. Bill inquiry permits subscriber online or voice actuated access to the subscriber s billing information including any balance remaining on account. Furthermore bill inquiry allows a subscriber to make real time billing inquiries such as a balance inquiry if the user has a pre paid associated account or a cumulative amount inquiry if the user s associated account is post paid. The subscriber also can secure access to long distance calling by programming a security code password as a prerequisite for completing a long distance call. Call reach is an integral part of this service in which the subscriber establishes limited call ranges by use of preprogrammed phone numbers to access specified areas and countries. The subscriber can utilize the automated directory inquiry service to obtain directory assistance. The found number may be auto dialed from this service. An extensive online help facility is available to the user through database . This facility includes instructions for various services and exemplary parameter configurations. Information on demand provides the subscriber with a single point source of information for subscriber information services information and marketing information. This information is available to the subscriber through facsimile and or data transmissions. The Internet telephony service allows both mobile and PSTN calls to be routed onto an internet IP network at low cost and high quality of service.
The terminating services are initiated when a call terminates at a subscriber invoking the pre programmed services of that particular subscriber. These features of the computer telephony services of the NetManager include call forwarding unconditional busy no reply and selective call park call hold call waiting important call waiting call screening call reject and call accept and multi line hunting facility.
The call forwarding service has four conditional options. Unconditional forwarding allows a subscriber to forward all calls to another number. Call forwarding busy allows the subscriber to designate another telephone number to receive calls should the primary number be busy. The no reply forwarding reroutes the call to a secondary number should the first number dialed fail to respond after a predetermined number of rings. Selective forwarding will forward calls in the above three scenarios only for calls originating from specific telephone numbers. The subscriber can alter any of the forwarding options from any phone. Call park allows a customer to set aside or park a call by dialing a parking code. While parked a call is both placed on hold and disassociated from the line so that the customer is free to place and receive calls even on a single line. Any line in the business group may dial a retrieval code to be connected to the parked call. An optional timed recall service guards against calls being permanently ignored or forgotten after being parked. Call hold allows a customer to place any call on hold by flashing the switch hook and dialing a hold code. This service frees the line to originate another call. Only one call per station line can be held at a time. The original connection can be retrieved by flashing and dialing the call hold access code. If the customer hangs up with a party on hold the customer is automatically rung back and connected to the held party. The call waiting service triggers a tone to a user engaged in a telephone call notifying the user that another call is attempting connection. By flashing the switch hook the called subscriber can talk to the third party while keeping the original party on hold. By flashing the hook switch again the subscriber can talk to the original party who has been on hold. Important call waiting is similar to call waiting except the subscriber is notified only if the incoming call is from a particular telephone number s that the subscriber has preprogrammed into the system. The call reject option of the call screening service allows a subscriber to filter out all incoming calls from specified numbers. The call accept service allows only specified numbers to ring through to the subscriber. Multi line hunting allows subscribers generally businesses to request that multiple non contiguous telephone numbers be grouped. When one number is busy an incoming call is automatically rolled to the next available number in the group.
The PIN based services are keyed to the personal identification number assigned to the customer and are limited to the specific authority of each customer. These services include authentication voice mail system watch and prepaid billing.
Authentication provides for the validation of the personal identification number entered by a subscriber. This service also allows the activation and deactivation of the PIN numbers. As part of activation the facility will retry activation following entry of an invalid PIN number. The number of retries is a configurable parameter. The system provides full feature voice mail for storage of messages. The subscriber can access his her voice mail box with a preprogrammed PIN number and can selectively search for and review messages delete messages and permanently save messages. System watch permits online display of the status and occupancy of the lines and channels on an administrator s or operator s console. Prepaid billing allows the subscriber to pay in advanced for a fixed dollar amount of services. Each time the subscriber makes a call or invokes a service the system validates the requested call or service for balance amount and so advises the subscriber including just prior to the balance being exhausted.
The administrative services include all parameter driven services and activation or deactivation services. These services include easy feature configuration system and traffic monitoring subscriber information access subscriber management packaging of services variable rate plans for different subscriber groups MIS reports security management and open billing. Open billing provides an open interface for real time billing settlement and reconciliation with third party external carrier or Customer Care and Billing systems. For example the system has the ability to record account receivables such as the following payments from corporate accounts payments from home accounts payments from voice mail accounts and payments from dealers. In addition the system has the ability to periodically bill subscribers for services offered by NetManager and also for services offered by third party providers.
Feature configuration permits the subscriber to preprogram and reprogram on demand the various configurable options based on each subscriber s preferences and requirements. The monitoring services permit the subscriber visual access to the activity level on the system including alarm notification idle status busy status and system statistics. The system maintains two levels of security with each subscriber having secured access to subscriber services and parameters and with system supervisors having access to a second layer of options and controls.
The IN services are the intelligent network functions and include advanced services such as toll free service premium rate calling such as 1 900 emergency service 911 distinctive ringing caller ID display CENTREX services full SS 7 functionality universal personal number service do not disturb automatic call back and opinion polling TeleVoting.
Toll free calling provides for calls to be made to an 800 number toll free to the caller and chargeable to the telephone number owner . Premium rate calling applies an additional rate or charge to calls made to A900 numbers with the additional charge being passed on to the number owner . Emergency service allows a caller abbreviated access to emergency services. When a call is made to an emergency number such as 911 operators staffing the emergency center can view critical data associated with the call such as name address telephone number and geographical location of the call. Distinctive ringing provides for a different ring pattern or tone when the call originates from a specific telephone number s . Caller ID displays the telephone number and associated subscriber name for incoming calls. Central exchange services are available to both calling and called customers. The universal personal number service allows a subscriber to have a specific personal telephone number other than an ordinary directory number. The subscriber can designate any proximate telephone in the network as his her own . A call to the subscriber s universal personal number will ring through to the designated telephone. Similarly any outgoing calls made on the designated telephone will be reflected on the subscriber s bill. In this instance the charging will be done to the universal personal number and not the number of the telephone utilized. The do not disturb service temporarily prohibits any call from ringing through to the subscriber s telephone. Instead the call is handled through the call forwarding or the voice mail facility depending on the options the subscriber has set up. Automatic call back is activated by the subscriber upon encountering a busy signal when the subscriber flashes the hook switch and enters a special code into the telephone. The busy number will be periodically polled by the system and when the number is available the subscriber s telephone will be rung and the connection completed when the subscriber lifts the handset. Opinion polling is activated by a subscriber establishing a designated telephone number recording an instructional message and coding various keyed caller entries to represent specific answers.
NetManager includes an interactive voice response system which lets a subscriber use all of the services of the system without using a touch tone telephone. NetManager additionally provides at least the following functions cost routing intercarrier transactions subscriber administration advanced service provisioning real time call rating cutoff caller authentication call progress analysis and AIN CTI advanced intelligent network computer telephony interface signaling network. The real time rating cutoff function supports real time monitoring and rating of calls against a credit amount outstanding against a pre paid account identified by for example a caller ID or a distinct account ID. Calls made by a pre paid customer or received by a pre paid customer can be debited from a customer s associated account in real time. The rating cutoff function is also capable of capturing the originating Phone ID on a real time basis and rating the calls at the appropriate rates depending upon the called location.
The rating cutoff is approved by an approval module. The approval module can have an approval master table and an approval list table. The approval master table can contain approval code and approval description fields. The approval code filed in the approval master table can be linked to an approval code field in the approval list table. The approval list table can contain approval code approval sequence number approval submitted by approval submitted date approval status approval remarks approval information and parent sequence number fields. The approval list table can thereby approve or deny rating cutoff based on the information in several fields and maintain the approval information.
In addition a security module can be used to control access to the approval module and overall system access. The security module can contain a pay module table a pay database roles table a pay operation table a pay user roles table and a pay rights table. The pay module table can maintain all of the other modules in the graphical user interface. The pay database roles table can maintain roles assigned to system users. The pay operation table can store all the operations that a user can complete. The pay user roles table can be a link table for many to many relationships related to user notes in the database i.e. administration approval need only .
If a call is attempted by a customer who is not a pre paid customer and or is not active on the system then the call will not be completed by the system. The system also has the ability to inform the customer of his her maximum allowable calling time connect the call and to inform a customer when a minimum value threshold approaches. Warnings and account balance announcements may optionally be heard by the customer.
NetManager is implemented using a fully modular software architecture which permits ready maintenance continuous enhancement and ease and flexibility of implementation. NetManager can run on industry standard PC platforms with telco grade working specifications such as an ISA PCI CPCI based CTI server running a Windows NT 4.0 server supporting DNA. Additionally NetManager and CallManager support both digital and analog interfaces.
Referring now to the back end of servers and of the NetManager and CallManager respectively are illustrated. Each server has at least three features categories hardware components including related S W drivers and databases and see an operating system preferably Unix or Window NT and software applications preferably a PIN calling application having an operation support system collectively referred to as CallManager or an enhanced computer telephony application operable on any switch system known as NetManager . As in the CTI cards interface between the switch and either software subsystem CallManager or NetManager as a conduit connected to the public communication network for the transmission and reception of information to and from the telephone device or .
Primary hardware components of the servers and preferably include ROM Bios RAM drivers processor and hard disk or other storage media which are all located at the central operations office . The central operations office contain servers for the card management subsystem a MIS system and a plurality of databases and including a central operations database and a central authentication database. The center connects to a regional office that includes a corresponding server s that house databases for supporting client applications for regional operations local authentication sales administration account management external carrier and rate plan maintenance and MIS. Additionally regional databases accept voice mail data.
The central operations office and databases and operate in connection with the CallManager server and the NetManager server which connect to the telephone company Lan Wan via a network interface card NIC and in turn interact with one or a plurality of client applications and regional offices . The regional offices include a plurality of databases for storing and retrieving information or for redirecting caller information. Each of these regional offices have a number of application and administrative functions to effectively run the PIN telephony computer system in accordance with a preferred embodiment of the invention. Call Center Agents have access to the regional databases and can retrieve customer accounting and usage information to track account and service usage generate invoices and identify customer candidates for promotions and upgrades.
The block diagram shown in reflects the interactive services of the CallManager subsystem which has links connecting the subsystem to the various users of the system including users dealers external carriers voice mail subscribers VMS sales agents print vendors and corporate and home accounts . The users include authorized customers and call center agents . The primary function of CallManager is to receive electronic transmissions from any and all of the various users of the system and respond to each user in kind utilizing the data stored in the server databases of the system.
Transmissions received by the CallManager include an activation code to activate a PIN access card a pin number for authentication an out dial number a call continuation request a voice mail box number a voice mailbox password navigation request a voice mail message to poll a request for connection to the call center and any queries by the subscriber. After receiving such information the Switch Manager which is a subsystem of the CallManager subsystem transmits the following exemplary information back to the callers subscribers or performs the following functions authentication of a PIN number followed by a greeting and a menu of options money balance left in a customer s account talk time left based on a customer s account balance a call cut off warning when a customer s account balance is approaching zero or its limit help information prompts call connection to out dialed numbers or mail boxes recorded voice mail messages or connection to call centers.
The Card Manager subsystem controls the distribution and usage of the PIN access cards and includes the following subsystems card management account management external carrier and rate plan sales administration management information system administration and batch processes for volume data transfers. The card management subsystem CMS is located at the central operations office for centralized control over the distribution and usage of the cards . The central operations office provides total control of the card configuration with services such as configurable PIN length user definable card type configuration and voice mail profiles. The CMS assists in achieving a centralized control and distribution mechanism for the definition printing physical inventory and financial value of the PIN access cards . The CMS also provides a centralized MIS for monitoring sales performance and inventory control regarding the cards within a single computerized software application.
In addition the CMS has the following particular services card types definitions PIN generation card print vendor maintenance card printing orders management accounts payable for card generation and the creation and maintenance of home and corporate voice mail accounts under the cards. The account management and administration subsystems integrate work flow into the system of a preferred embodiment of the invention with approvals introduced for all sensitive card distribution and account management functions including inventory control lost card deactivation and financial accounting. The account management subsystem contains modules that provide central and regional office users with database control manipulation and decision making support an interactive work flow for home and corporate account creation activation and maintenance itemized statement creation tracing and reporting user definition voice mail accounts and profile maintenance accounts receivable and payments history and providing information held in system databases such as itemized statements to customers on demand for customer service or other inquiries.
Under controlled circumstances corporate and home customers may submit detailed orders for PIN access cards as shown in . The account management subsystem is comprised of a corporate account management subsystem as shown in a home account management subsystem as shown in and a management subsystem for virtual telephony voice mail for corporate and home account users as shown in . The corporate management subsystem provides internal users the ability to create corporate accounts change card status request PIN s and issue cards as well as data entry and storage as shown in . Referring now to functionality provided by the home management subsystem includes the ability to create home accounts change card status request PIN s and issue cards . Finally the functionality provided by virtual telephony as shown in is to define area information to import voice mail and voice mail profile box numbers and to create new customer accounts with customer specific manipulated settings. A calling card can be owned by an individual a home sector or a corporate sector. The voice mail services of the present system in accordance with the preferred embodiments are particularly helpful in places where telephones are not easily available. In such situations a phone number is allocated to a user but no physical connection is made to a telephone device when a call is received by the phone number. Instead all calls to the number are routed to a mail box in the user s name. Hence the term virtual telephony . The user can call the mail box at any time from any phone and retrieve any messages. Alternatively the user can notify the system to make a physical connection to a telephone device available to the user for the routing of all telephone calls.
The Switch Manager subsystem which again is the telephony system for providing the out dialing call conferencing and voice mail services of the CallManager operates on a Windows NT platform or a Unix platform and non proprietary hardware such as Intel microprocessor based servers with any number of common CTI cards for example offered by Dialogic Corporation .
The out dialing module provides the complete outdialing functionality of the Switch Manager in conjunction with related functions of Card Manager in accordance with a preferred embodiment of the invention. Upon receiving a pin based telephone call initiated by a subscriber the Switch Manager responds by transmitting a greeting to the customer requesting entry of a PIN number and upon receipt of the PIN number transmits data to the Card Manager for requesting the authentication of card . The Card Manager subsystem verifies from the account manager database information from database that the account is active. The Card Manager advises the Switch Manager whether the account is valid. If the verification fails the Card Manager so communicates to the Switch Manager which transmits a corresponding message to the customer advising of the verification failure and requesting the customer to retransmit the PIN and or account number. After several such as three failures the Switch Manager will terminate the call with an appropriate message transmitted to the customer . If the PIN verification is successful the Card Manager retrieves the remaining account balance from the account manager database and transmits the balance information to the Switch Manager . The Switch Manager transmits the balance information to the customer and requests and accepts the out dialed number for completion of communication links over the PSTN validates the outdialed number for allowed call type on the card by comparing the number to the allowed numbers list in the Card Manager subsystem and performs the outdialing and call progress analysis. The Switch Manager includes a facility for making multiple calls after account and PIN authentication. At the end of a call the Switch Manager reestablishes connection with the customer advises the customer the balance remaining in the account and presents to the customer the option of making another call hanging up or initiating another Switch Manager service . The customer may initiate additional out calls as long as sufficient balance remains in the account. Similarly the customer may initiate call conferencing or voice mail functions as discussed below. Should the customer hang up or terminate the call through the menu options presented by the Switch Manager the Switch Manager will communicate the remaining balance to the Card Manager whose account management subsystem updates the customer s account information in the database .
The Switch Manager also monitors PIN usage and will terminate simultaneous account PIN use to reduce and prevent fraud. The Switch Manager provides support for multiple languages to facilitate operation of advanced telephone services over analog connections transmits a warning beep that notifies users prior to call cut off for example due to an exhausted account balance. It also provides automatic call routing to call centers upon pre determined events as defined in the card and user administration settings stored in the central and or regional database . As detailed in the calling subscriber for dialing out can use abbreviated numbers based on information previously loaded by the customer in database .
The call conferencing subsystem of the Switch Manager provides multi party call conferencing functionality to the PIN card subscriber . The subsystem provides users with an interactive voice response or operator assisted method of joining multiple connected calls into the conversation and to debit the customer s PIN access card s corresponding account balance for the charge of initiating a conference call and for the charges accruing during the call. The caller initiated conference is supported by the system by holding calls open and active as the parties to the conference call are contacted by the system and brought into the call. As with outdialing the call conferencing subsystem requires prior authentication of account and PIN number before establishing the conference call.
The voice mail subsystem of the Switch Manager as detailed in provides voice mail functionality to PIN based customers . Referring now to a user of the system sets up and accesses a voice mail box with the interactive voice response subsystem of the Switch Manager . The user has the option of setting up multiple mail boxes within a primary account and may provide various greetings messages within the various mail boxes and under various in call circumstances such as no answer or line busy. These mail boxes and messages are stored in the database of server . Referring now to when a call routed through the system encounters a voice mail subsystem condition such as no answer or line busy and the number called has a voice mail box set up on the system the Switch Manager directs the appropriate greeting to the caller and stores any response for later retrieval by the mail box owner see . The system provides password access administration of the voice mail boxes. Stored messages may be navigated and retrieved by the storage date. The customer s account card is charged or decremented for the voice mail box setup and usage.
If the PIN access card being utilized to initiate and pay for the above Switch Manager services is a top up card then the communications to the user regarding account balance insufficient balance or exhausted balance include an option for the user to add a value to or top up the card. Under such circumstances the user provides a bank account or credit card account number from which the system will in real time transfer funds into the user s telephony account.
The customer management subsystem of the account management subsystem accepts customer information from the user for opening a voice mail box account and establishing a mail box profile. The user enters the name address information and voice mail box profiles into the system which define the deposit amount maximum voice message length maximum number of messages maximum age of retained messages and voice mail box life. The system also assigns the area code and voice mail box number to the account. This account status can be changed to active suspended or deactivated. By clicking the query button the user can search the profiles which exist in the system.
The ability to assign cards to other customers is a service of the account management subsystem of the Card Manager . Upon the request of a customer to assign cards the total credit amount and remaining credit amount for each card and account assigned to that customer is displayed to the user. Depending on the customer s request specific cards may be assigned to a designated corporate or home account. In the alternative the user may enter a dollar amount of cards to be assigned and the system will determine which cards should be assigned to meet the requested credit value. Authorized corporate and home customers may effect this assignment directly without submitting a request to a central or regional office.
Referring now to the payments option of the account management subsystem allows the user to accept payments for a selected account. At the offset the user selects the transaction to be processed whether receiving a payment from a corporate or home account or receiving a sales receipt from a dealer or sales agent . The user then enters the details of the current transaction such as payment method credit card bank instrument cash etc. payment amount payment date etc. After entering the details of the payment the user has the option of accepting the transaction details or canceling them and starting with another transaction. If accepted the payment is booked or the receipt is logged and the results are stored in the database .
Call center agents have the ability through remote terminals to search the databases and for customers by account account type name services address voice mail box number etc. For example a call center agent may select an account type from a drop down menu list and view calling history profiles payments and other details for all qualifying accounts. By selecting the account type details of the account such as name address deposit credit limit and call history etc. are displayed to the user. The user can also select by corporate division or home name to display all accounts and cards assigned to the division or home. The payment details are displayed and the payment history of the current account can also be viewed. Details of the payment mode can be viewed by selecting the column Payment Method . On selecting the Accept Payments button a screen is displayed through which the payment details are accepted and posted to the database . The home search facility displays all home account numbers and home names according to a selected search criteria which is yet another provision of the account management subsystem of the Card Manager . Sorting can be done by clicking the column headings of the home list. Once a home account is selected it can be viewed or manipulated by authorized users of the system.
The ability to maintain corporate and home accounts is another service of the account management subsystem of the Card Manager . Through either a corporate or home maintenance subsystem users can view add and modify the details of any level of a corporate or home hierarchical structure and contact persons as stored in the database . Some of the details of the corporate account are business type bill cycle multiple addresses present address previous address billing address etc. customer ID financial soundness discounts contact persons contracts and contract terms and responsibility for payment. The home customer details displayed include default address billing address account ID status of account billing cycle discounts customer identity financial soundness payment information detail of card types and denomination and contracts.
Each corporate customer has a stored hierarchical structure reflecting the multi level structure of the corporation. All details of the corporate customer can be displayed including address information payment information card details and summary. A level can be added to the hierarchy by clicking on the add level button and placing the cursor on the tree displayed. The status of the corporate customer of any level can be changed by clicking on the change status button. A request for cards can be placed by depressing the request cards button. The details of the cards assigned to the corporate level can be viewed by clicking on the tab named card details. The details of the current level level on which the cursor is placed are also displayed in the grid. The name of the main corporate and the main account number allocated to that corporate customer are also displayed to the user.
On the corporate status screen any level of a corporate hierarchy s status can be changed. The different status applicable for corporate customers are prospective active suspended and deactivated. If a level in the corporate hierarchy is being deactivated or suspended the underlying levels of that corporate parent will have the same status as its related parent provided that level is not responsible for payment. When a level in the corporate hierarchy is being activated from a deactivated or suspended state the status of the underlying levels of that parent will be restored to previous original status. If the main corporate account is activated for the first time a request will be placed for generating a main account number. Detailed multi level corporation hierarchies are used by the system and its users to determine corporate divisional accounts.
The sales administration subsystem SAS subsystem of the Card Manager subsystem manages all functions associated with the sale and distribution of the PIN access cards through dealers in distributorships and sales agents . This subsystem includes the dealer management subsystem and elements of this subsystem include dealers maintenance sales agents maintenance sales territories maintenance commission models maintenance incentive models maintenance PIN access card issuance to sales agents registration of sold returned lost cards commissions calculation incentives calculation and accounts receivable management. Through this subsystem new dealers and sales agents are enrolled into the system as are new commission models new incentive models and updated dealer territories. Referring now to each dealer s name and full address are mandatory and dealer telephone number facsimile number e mail address and contact person may also be entered. Information to be entered for each new sales agent includes name address telephone number and title. The commission models are used by the system in determining payment and account balances during sales account reconciliation. Incentive model information may be entered for particular sales agents and will normally include start and end dates of the incentive program eligible persons for claiming benefits under the incentive program and the requirements of the program. The incentive models are used to compute check in check out account balances and dealer sales agent compensation. By registration of sold cards the SAS subsystem in conjunction with the card management subsystem loads customer account information into the database .
Referring now to the data flow associated with the sales agent check in is detailed. The process shown in occurs with the return of the sales agent from a sales call or sales trip. The sales agent must account for all cards registered to him her and must report the cards as having been sold as being returned or as having been damaged or destroyed. A card inventory is correspondingly updated with the returned cards being made available for subsequent sale. The sales agent s appropriate commission model is selected the number of sold lots is input and the sales agent is compensated in the form of cash or credit. All data associated with the sales agent s transactions is stored in the server database . detail the data flow associated with adding a new dealer and a new sales agent respectively to the system.
The security subsystem of the Card Manager provides the ability to assign users to organizational roles to configure security privileges for different roles and to regulate work flow through designated approved roles by utilizing user and operations administrations. The detail of this subsystem is shown in . The user can create and modify users create and modify roles to access particular subsystems of the system map operations to roles map roles to users and assign the rights allowed on each subsystem to the various roles.
Some of the functions of the Card Manager subsystem are provided by batch processes instead of online services. Most notable among these are the steps associated with issuing and managing the access cards and their corresponding PIN numbers. An example of such processing is shown in for the authentication of mobile cards . As a method to avoid fraudulent usage of access cards printed access cards must first be authenticated or registered before the system will accept the usage of the card . Such a process is initiated at the central office with a request for additional mobile or automobile cards . Once all necessary information associated with the cards is extracted from the system database the card is authenticated by updating its status in the database . At this point the card is available for use by a customer to access the services provided through the inventive system.
The external carrier and rate plan subsystem ECRS subsystem of the Card Manager is responsible for maintaining the various network and carrier rate plans available under which customers may be accessing the resources and services available through the system. System users utilize the ECRS subsystem to enter information for maintaining carrier and rate related information within the system including information identifying and detailing external carriers rate plans networks nodes zones time packages tariff times holidays contact persons and service maintenance definitions. Through the use of various well known input and query devices including graphical user interfaces and remote terminals the users can view input modify and delete any and all information related to the external carriers and various rate plans with appropriate clearance authority as provided through the system s security subsystem. Each rate plan may be limited by zone time date and user. Additionally the ECRS provides the resources through which additional surcharges may be added to rate structures for particular services utilized by customers such as call conferencing voice mail facsimile etc. The ECRS subsystem provides a built in rating engine for dynamically calculating various usage charges during the delivery of communication services for ensuring that the customer has sufficient balance or limit remaining to purchase the requested services.
A high level application programming interface HAPI is a term of art describing the application programming interface that interfaces between the system in accordance with preferred embodiments of the invention and the CTI cards regardless of the type or manufacturer of CTI card s provided. Therefore by simply updating the HAPI modules to accommodate a new CTI card the system becomes independent of whatever CTI cards are elected to be used. In other words HAPI provides a way to keep the application unchanged over multiple vendor CTI cards.
The framework of HAPI provides a set of function calls structures events errors and constants which are common across all cards supported by HAPI. The application can use these values irrespective of the card used. Thus the application developer need not worry about the target card type on which the application is going to be executed. The programmer need not know the function calls or the programming intricacies of all the type of cards on which the program is going to be run. HAPI shields these from the application and provides a common framework for the application developer. HAPI can be used with analog lines as well as digital E1 T1 ISDN lines.
While the above discussion has been directed toward providing telephony communication services to the user and subscriber in accordance with preferred embodiments of the invention the CallManager and NetManager subsystems can also be utilized to provide Internet or other online services to the user. Specifically the services of CallManager and or NetManager can be used to access any online service currently available through the use of computers and modems as illustrated by . In such an embodiment of the present invention the user inquiries would be routed through a remote access server instead of the CallManager server or the NetManager server . The remote access server would then direct the inquiry through a router to connect with the Internet network or any online access service. Once connected the user would be allowed to conduct any pre authorized online transaction such as e commerce information inquiry financial communication or entertainment for example. The rating engine for calculating user charges for receiving services selected would be modified to reflect the cost of accessing the various Internet or online services and features. The rating engine would accommodate charging plans based on service time duration and volume. By way of example and not limitation a subscriber could sign up for a PIN access card that permits access to e commerce transactions on the Internet with such transactions limited to investment trading auction bidding and travel purchases with a specific transaction limit for each such category. The user dials the remote access server which routes the call to the radius authentication server for authentication. The radius authentication server sends information to the CallManager upon authentication. The CallManager accesses the user s account and responds to the radius authentication server whether there is sufficient balance in the account and whether the requested service is valid for this user s account. The user is connected to the Internet or online service and the CallManager keeps track of the elapsed time. Charges such as online purchases accrued by the user during connection are levied against the user s account balance. The above is also referred to as real time authorization and real time debiting. If the customer disconnects before exhaustion of the account balance the radius authentication server notifies the CallManager of the call termination and the CallManager then updates the user s account balance. If the balance is exhausted during the call the CallManager sends a termination message to the remote access server which so notifies the user and terminates the connection.
Providers are presently implementing Internet and other online networks to carry voice and multimedia traffic in addition to utilizing traditional switched telephony networks. NetManager as a call processing engine for a PSTN user can also be used as a gateway for providing enhanced voice and multimedia services on the Internet or other online networks as illustrated in . In this embodiment NetManager accepts all telephony calls for digit analysis. If NetManager determines that the call is within the Internet or other online network NetManager translates the destination digits to the corresponding Internet address and sends the call back to the Internet or other online network. If the call is for the PSTN NetManager performs a gateway function and routes the call to the PSTN over signaling links such as MFC R2 ISDN PRI or SS7. The NetManager then provides all requested and authorized telephony services to both the Internet and the PSTN customers.
Although preferred embodiments of the present invention have been shown and described it will be appreciated by those skilled in the art that changes may be made in these embodiments without departing from the principle and spirit of the invention the scope of which is defined in the appended claims and their equivalents.
| 407.423077 | 2,667 | 0.8345 | eng_Latn | 0.999869 |
9b991e19f0351be105e8c775360bae3a54e0b697 | 6,737 | md | Markdown | Computer Vision II/Lecture notes/12a - Multi-View III - Reconstruction from 6 Points, Multi-View matrix for Lines.md | Vuenc/TUM | 8e60ef725f595babb6b010c3c393debec3336f2e | [
"Apache-2.0"
] | 225 | 2019-10-02T10:49:41.000Z | 2022-03-29T22:25:38.000Z | Computer Vision II/Lecture notes/12a - Multi-View III - Reconstruction from 6 Points, Multi-View matrix for Lines.md | Vuenc/TUM | 8e60ef725f595babb6b010c3c393debec3336f2e | [
"Apache-2.0"
] | 6 | 2021-02-16T12:22:43.000Z | 2021-07-31T19:35:57.000Z | Computer Vision II/Lecture notes/12a - Multi-View III - Reconstruction from 6 Points, Multi-View matrix for Lines.md | Vuenc/TUM | 8e60ef725f595babb6b010c3c393debec3336f2e | [
"Apache-2.0"
] | 69 | 2019-10-02T21:46:57.000Z | 2022-03-17T19:27:50.000Z | ## Multi-View Reconstruction
Two approaches:
1. cost-function based: maximize some objective function subject to the rank condition => non-lin. opt. problem: analogous to bundle adjustment
2. decouple structure and motion, like in the 8-point algorithm. Warning: not necessarily practical, since not necessarily optimal in the presence of noise + uncertainty (like the 8-point algorithm)
Approach 2 is called *factorization approach* (because it factors - i.e. decouples - the problem)
### Factorization Approach for Point Features
Assume: $m$ images $x_1^j, \dots, x_m^j$ each of points $p^j$, $j \in [n]$.
Rank constraint => columns of $M_{p^j}$ dependent => (first column) + $\alpha^j$ (second column) = 0. As seen above, $\alpha^j = 1/\lambda_1^j$.
![[Pasted-image-20210608164310.png|500]]
This equation is linear in the camera motion parameters $R_i, T_i$, and can be written as:
$$P_i \begin{pmatrix} R_i^s \\ T_i \end{pmatrix}
= \begin{pmatrix}
x_1^1{}^\top \otimes \widehat{x_i^1} & \alpha^1 \widehat{x_i^1} \\
x_1^2{}^\top \otimes \widehat{x_i^2} & \alpha^2 \widehat{x_i^2} \\
\vdots & \vdots \\
x_1^n{}^\top \otimes \widehat{x_i^n} & \alpha^n \widehat{x_i^n} \end{pmatrix}
\begin{pmatrix} R_i^s \\ T_i \end{pmatrix}
= 0 \in \mathbb{R}^{3n}
$$
Here simply things were re-arranged, the $R$ and $T$ matrices stacked in one long vector.
One can show: $P_i \in \mathbb{R}^{3n \times 12}$ has rank 11, if more than 6 points (in general position) are given! (Intuition behind 6: 3n rows for n images, but only 2 out of three are lin. indep.)
=> one-dim. null space => projection matrix $\Pi_i = (R_i, T_i)$ given up to scalar factor!
In practice: use > 6 points, compute solution via SVD.
Like 8-point algorithm: not optimal in the presence of noise and uncertainty.
##### Decoupling compared to 8-point algorithm
Difference from 8-point algorithm: structure and motion not fully decoupled, since the 1/depth parameters $\alpha$ are needed to construct $P_i$. However, structure and motion can be iteratively estimated by estimating motion from a structure estimate, and vice versa, until convergence. Advantage: each step has a closed-form solution. This could be initialized by an 8-point algorithm reconstruction and further improve on it using the multi-view information.
Least-squares solution to find $\alpha_j$ from $R_i, T_i$:
$$\alpha^j = - \frac{\sum_{i=2}^m (\widehat{x_i^j} T_i)^\top \widehat{x_i^j} R_i x_1^j}{\sum_{i=2}^m || \widehat{x_i^j} T_i || ^2}$$
Another interesting point: Estimating $Pi_i = (R_i, T_i)$ only requires two frames 1 and $j$, but estimating $\alpha$ requires all frames.
QUESTION: Don't we get $\alpha_j$ from $M_{p_j}$? (No... we need $R, T$ to get $M_{p_j}$).
### The Multi-View Matrix for Lines
Recall: $\ell_i^\top \Pi_i X_0 = \ell_i^\top \Pi_i V = 0$ for the coimages $\ell_i$ of a line $L$ with base $X_0$, direction $V$; we constructed the multi-view matrix for lines:
$$W_l = [\ell_1^\top \Pi_1 ; \dots; \ell_m^\top \Pi_m] \in \mathbb{R}^{m \times 4}$$
The rank constraint is that $W_l$ should have rank at most 2, since $W_l X_0 = W_l V = 0$. Goal: find more compact representaion; assume $\Pi_1 = (I, 0)$, i.e. first camera is in world coordinates.
Trick: multiply $W_l$ by 4x5 matrix $D_l$ s.t. last four columns of first row become zero, but keep rank the same.
![[matrices-WlDl-lines.png]]
Now since the first column must be lin. indep. because of the zeros in the first row, and the matrix has rank at most 1, the submatrix starting $(W_l D_l)[2:, 2:]$ must have rank 1. This submatrix is called the *multi-view matrix for lines*.
$$M_l = \begin{pmatrix}
\ell_2^\top R_2 \widehat{\ell_1} & \ell_2^\top T_2 \\
\vdots & \vdots \\
\ell_m^\top R_m \widehat{\ell_1} & \ell_m^\top T_m
\end{pmatrix} \in \mathbb{R}^{(m-1) \times 4}$$
The previous rank-2-constraint can be characterized by a rank-1-constraint on $M_l$: A meaningful preimage of $m$ observed lines can only exist if
$$\text{rank}(M_l) \leq 1.$$
In other words: all rows and all columns must be linearly dependent.
##### Trilinear Constraints for a Line (from the Rows)
Since rows of $M_l$ are lin. dep., we have for all $i, j$: $\ell_i^\top R_i \widehat{\ell_1} \sim \ell_j^\top R_j \widehat{\ell_1}$. This states that the three vectors $R_i^\top \ell_j$, $R_j^\top \ell_j$, $\ell_1$ are coplanar. So $R_i^\top \ell_i$ is orthogonal to the cross product of $R_j^\top \ell_j$ and $\ell_1$, which leads to:
$$\ell_i^\top R_i \widehat{\ell_1} R_j^\top \ell_j = 0$$
Note: this constraint only contains the rotations, not the translations! (Observing lines allows us to directly put constraints on the rotation alone.)
By the same rank-deficiency lemma from before, we get that the linear dependency of the i-th and j-th row is equivalent to
$$\ell_j^\top T_j \ell_i^\top R_i \widehat{\ell_1} - \ell_i^\top T_i \ell_j^\top R_j \widehat{\ell_1} = 0$$
This relates the first, i-th and j-th images.
Both trilinear constraints are equivalent to the rank constraint if $\ell_i^\top T_i \neq 0$.
##### Generality of three-line constraints
Any multiview constraint on lines can be reduced to constraints which involve only three lines at a time. (Argument via 2x2 minors of matrix: see slides)
### Characterization of Unique Preimages for Lines
**Lemma:** *Given three camera frames with distinct optical centers and $\ell_1, \ell_2, \ell_3 \in \mathbb{R}^3$ represent three images lines, then their preimage $L$ is uniquely determined if*
$$
\ell_i^\top T_{ji} \ell_k^\top R_{ki} \widehat{\ell_i} - \ell_k^\top T_{ki} \ell_j^\top R_{ji} \widehat{\ell_i} = 0
\quad \forall i, j, k = 1, 2, 3,
$$
*except for one degenerate case: The only degenerate case is that in which the preimages of all $\ell_i$ are the same plane.*
Note: this constraint combines the two previous trilinear constraints.
Equivalent formulation using the rank constraint:
**Theorem:** *Given $m$ vectors $\ell_i$ representing images of lines w.r.t. $m$ camera frames, they correspond to the same line in space if the rank of $M_l$ relative to any of the camera frames is 1. If its rank is 0 (i.e. $M_l=0$, the line is determined up to a plane on which then all the camera centers must lie.*
## Summary of Multi-View Chapter
| | (Pre)image | coimage | Jointly |
|-------|------------------------------|---------------------------|---------------------------|
| Point | $\text{rank}(N_p) \leq m+3$ | $\text{rank}(W_p) \leq 3$ | $\text{rank}(M_p) \leq 1$ |
| Line | $\text{rank}(N_l) \leq 2m+2$ | $\text{rank}(W_l) \leq 2$ | $\text{rank}(M_l) \leq 1$ |
The rank constraints guarantee the existence of unique preimages in non-degenerate cases. | 59.096491 | 461 | 0.692296 | eng_Latn | 0.984576 |
9b99a46a21c990b6020c24544704cdad577d3e9e | 1,806 | md | Markdown | README.md | AndersDJohnson/js-loading | ea0944994f35f38ced2fd45a5c13260060ecb33e | [
"MIT"
] | null | null | null | README.md | AndersDJohnson/js-loading | ea0944994f35f38ced2fd45a5c13260060ecb33e | [
"MIT"
] | null | null | null | README.md | AndersDJohnson/js-loading | ea0944994f35f38ced2fd45a5c13260060ecb33e | [
"MIT"
] | null | null | null | js-loading
=====================
Prevents [FOUC][fouc] (flash of unstyled content), or "unbehaviored" content,
until JavaScript loads and executes,
by providing classes to hide specified elements.
## Install
Via bower as `js-loading`.
```sh
bower install --save js-loading
```
## Usage
1. Add both CSS and JS to your page. The JS supports AMD and browser global `jsLoading`.
2. Add a `js-loading` class to your container element
(<html> element is preferred). If overriding prefix, use `${prefix}-loading` instead.
3. Add call to `jsLoading.loaded()` when your JS has loaded and executed.
Pass options if desired, e.g. `{containerSelector: 'body'}` for container selector, or `{prefix: 'my-js'}` if overriding prefix.
Refer to JS API below for complete option list.
Example:
```html
<html class="no-js js-loading">
<head>
<script>(function(H){H.className=H.className.replace(/\bno-js\b/,'js')})(document.documentElement)</script>
<link rel="stylesheet" type="text/css" href="dist/js-loading.min.css" />
</head>
<body>
<div class="js-loading-invisible">
<!-- contents will have {visibility: hidden} until JS loads -->
</div>
<div class="js-loading-hidden">
<!-- contents will have {display: none} until JS loads -->
</div>
<script src="http://code.jquery.com/jquery-1.11.0.min.js"></script>
<script src="dist/js-loading.min.js"></script>
<script>
// do stuff, then finally...
jsLoading.loaded();
</script>
</body>
</html>
```
Credit to Paul Irish for the [`.no-js` to `.js` trick](http://www.paulirish.com/2009/avoiding-the-fouc-v3/).
## JS API
See `src/js-loading.js` and the JS doc comments there.
## LESS API
See `src/js-loading-mixin.less`.
[fouc]: http://en.wikipedia.org/wiki/Flash_of_unstyled_content
| 29.129032 | 130 | 0.669435 | eng_Latn | 0.661846 |
9b99ce547d4a0c61e506a59cb8c65a5b68db8fbb | 15,813 | md | Markdown | _posts/2019-11-04-android-chapter09.md | meijamke/meijamke.github.io | 59449d21a743fd129f37a4ad7de92156d690a169 | [
"Apache-2.0"
] | null | null | null | _posts/2019-11-04-android-chapter09.md | meijamke/meijamke.github.io | 59449d21a743fd129f37a4ad7de92156d690a169 | [
"Apache-2.0"
] | null | null | null | _posts/2019-11-04-android-chapter09.md | meijamke/meijamke.github.io | 59449d21a743fd129f37a4ad7de92156d690a169 | [
"Apache-2.0"
] | null | null | null | ---
layout: post
title: "《第一行代码》Chapter 09"
subtitle: '网络技术'
author: "Jamke"
header-style: text
tags:
- Android Foundation
- AF
---
## 目录
1.[WebView](#webview)
2.[使用HTTP协议访问网络](#使用http协议访问网络)
3.[使用OkHttp访问网络](#使用okhttp访问网络)
4.[解析XML格式的数据](#解析xml格式的数据)
5.[解析JSON格式的数据](#解析json格式的数据)
6.[java回调机制](#java回调机制)
## 正文
---
#### WebView
> WebView,用于在APP内展示网页
```
//xml布局文件中,通过<WebView>标签创建一个WebView
<WebView
android:id="@+id/web_view"
android:layout_width="match_parent"
android:layout_height="match_parent"/>
//活动中,得到WebView的引用,然后设置WebView
WebView webView=findViewById(R.id.web_view);
webView.getSetting.setJavaScriptEnabled(true);//支持JavaScript脚本
webView.setWbeViewClient(new WebViewClient());//当从一个网页跳转到另一个网页时,网页依旧在WebView中显示,而不是打开浏览器
webView.loadUrl("https://github.com")//需要打开的网页的URL
//manifest文件中,申请访问网络的权限
<manifest>
...
<uses-permission android:name="android.permission.INTERNET"/>
...
</manifest>
```
---
#### 使用HTTP协议访问网络
> http协议的极简~~不靠谱~~流程:客户端发送请求,服务器收到请求后返回数据,客户端收到服务响应,客户端解析返回的数据
> Android中有两个发送http请求的方式:HttpURLConnection和HttpClient,其中HttpClient由于API过多、扩展困难等缺点,已经在Android6.0(API23)弃用。
```
private TextView mUrlResultTextView;
@Override
protected void onCreate(@Nullable Bundle savedInstanceState) {
...
mUrlResultTextView=findViewById(R.id.url_result);
...
}
//开启子线程访问网络
//由于Android的用户界面是单线程,负责从各种传感器获取事件,并绘制要设置的下一帧,假如以60帧/秒的速度运行,那么需要确保每一帧绘制的时间要小于17毫秒。换句话说,要尽可能少地在主线程上执行任务,但是联网一般需要几秒,如果在主线程上调用网络连接,用户界面就会被冻结(无法交互),冻结5秒后,Android会提示用户关闭应用。所以需要在子线程(也可以叫辅助执行线程)中调用网络连接。
new Thread(new Runnable(){
@Override
public void run(){
//构建URL
URL url=new URL("https://github.com");
//创建URL连接对象,还没有连接网络,这一步可以添加请求方法、连接属性、头字段等
HttpURLConnection urlConnection=(HttpURLConnection)url.openConnection();
//urlConnection.setRequestMethod("GET");
//urlConnection.setConnectTimeout("8000");//设置连接超时时间8000毫秒
//urlConnection.setReadTimeout("8000");//设置读取超时时间8000毫秒
try{
//从URL连接对象获取输入流
InputStream in=urlConnection.getInputStream();
//使用扫描器读取输入流
Scanner scanner=new Scanner(in);
//将分隔符设置为\A,即从输入流的起点开始分隔
scanner.useDelimiter("\\A");
//若扫描器有缓存的输入流,取出
if(scanner.hasNext())
result=scanner.next();
else
result=null;
//在主线程显示结果
showResult(result);
}catch(IOException e){
e.printStackTrace();
}finally{
//最后,释放URL连接对象
urlConnection.disconnect();
}
}
}).start();
//子线程执行完,通过调用runOnUiThread()方法可以将线程切换到主线程,然后更新主线程UI
private void showResult(String result){
runOnUiThread(new Runnable(){
public void run(){
mUrlResultTextView.setText(result);
}
});
}
//manifest文件中,申请访问网络的权限
<manifest>
...
<uses-permission android:name="android.permission.INTERNET"/>
...
</manifest>
```
---
> [更多读取输入流的方法以及各方法的优缺点](http://stackoverflow.com/questions/309424/read-convert-an-inputstream-to-a-string%EF%BC%8C%E8%AF%A6%E7%BB%86%E4%BA%86%E8%A7%A3%E5%AE%8C%E6%88%90%E8%BF%99%E4%B8%80%E6%93%8D%E4%BD%9C%E7%9A%84%E4%B8%8D%E5%90%8C%E6%96%B9%E6%B3%95%E3%80%82)
> 若想发送数据给服务器,可以在通过URL连接对象获取输入流之前,设置请求方法和要发送的数据
```
...
//设置请求方法为POST(发送数据给服务器)
urlConnection.setRequestMethod("POST");
//设置发送的数据内容
DataOutputStream out=new DataOutputStream(urlConnection.getOutputStream());
out.writeByte("userName=admin&password=1234");
...
```
---
#### 使用OkHttp访问网络
- [OkHttp](https://github.com/square/okhttp),在众多Android开源的网络通信库中,是比较出色的一个。
```
//添加依赖库
implementation "com.squareup.okhttp3:okhttp:4.2.1"
//从服务器获取数据
OkHttpClient client=new OkHttpClient();
new Thread(new Runnable(){
@Override
public void run(){
Request request=new Request.Builder()
.url("https://github.com")
.build();
try{
result=client.newCall(request).execute();
showResult(result);
}
}
}).start();
//发送数据给服务器,区别在于,需要构建一个RequestBody,添加需要发送的数据,然后传入request的post方法,发送给服务器
OkHttpClient client=new OkHttpClient();
new Thread(new Runnable(){
@Override
public void run(){
RequestBody requestBody=new FormBody.Builder()
.add("userName","admin")
.add("password","1234")
.build();
Request request=new Request.Builder()
.url("https://github.com")
.post(requestBody)
.build();
try{
result=client.newCall(request).execute();
showResult(result);
}
}
}).start();
```
---
#### 解析XML格式的数据
> 解析XML常用的方法有两种:Pull解析和SAX解析
- XML数据
```
//假设要解析的XML数据内容如下
<apps>
<app>
<id>1</id>
<name>google map</name>
<version>1.0</version>
</app>
<app>
<id>2</id>
<name>chrome</name>
<version>2.1</version>
</app>
<app>
<id>3</id>
<name>google play</name>
<version>2.3</version>
</app>
</apps>
```
- Pull解析
```
private void parseXmlWithPull(String xml){
//获得XmlPullParserFactory实例
XmlPullParserFactory factory=XmlPullParserFactory.newInstance();
//通过XmlPullParserFactory获得XmlPullParser
XmlPullParser xmlPullParser=factory.newPullParser();
//设置要解析的数据
xmlPullParser.setInput(new StringReader(xml));
//每个节点内的数据
String id="";
String name="";
String version="";
//获得当前解析事件
int eventType=xmlPullParser.getEvemtType();
while(eventtype!=XmlPullParser.END_DOCUMENT){
//获取当前节点名
String nodeName=xmlPullParser.getName();
switch(eventType){
//开始解析某个节点
case XmlPullParser.START_TAG:
if("id".equals(nodeName))
id=xmlPullParser.nextText();
else if("name".equals(nodeName))
name=xmlPullParser.nextText();
else if("version".equals(nodeName))
version=xmlPullParser.nextText();
break;
//完成解析某个节点
case XmlPullParser.END_TAG:
break;
default:
break;
}
//下一个节点
eventType=xmlPullParser.next();
}
}
```
- SAX解析
```
//新建class继承自DefaultHandler,构建SAX解析需要的Handler
public class MySAXHandler extends DefaultHandler{
private String nodeName;
private StringBuilder id;
private StringBuilder name;
private StringBuilder version;
//开始解析XML
@Override
public void startDocument() throws SAXException {
id=new StringBuilder();
name=new StringBuilder();
version=new StringBuilder();
}
//开始解析某个节点
@Override
public void startElement(String uri, String localName, String qName, Attributes attributes) throws SAXException {
//保存节点名
nodeNmae=localName;
}
//解析节点内容
@Override
public void characters(char[] ch, int start, int length) throws SAXException {
if("id".equals(nodeNmae))
id.append(ch,start,length);
else if("name".equals(nodeName))
name.append(ch,start,length);
else if("version".equals(nodeName))
version.append(ch,start,length);
}
//完成解析某个节点
@Override
public void endElement(String uri, String localName, String qName) throws SAXException {
if("app".equals(nodeName)){
//将StringBuilder清空,以便处理下一个节点
id.setLength(0);
name.setLength(0);
version.setLength(0);
}
}
//完成解析XML
@Override
public void endDocument() throws SAXException {
super.endDocument();
}
}
//使用SAX方法解析XML
private void parseXMLWithSAX(String xml){
try{
//获得SAXParserFactory实例
SAXParserFactory factory=SAXParserFactory.newInstance();
//通过SAXParserFactory获得XMLReader对象
XMLReader xmlReader=factory.newSAXParser().getXMLReader();
//通过XMLReader设置ContentHandler
xmlReader.setContentHandler(new MySAXHandler());
//xml数据传入xmlReader的parse方法,开始解析
xmlReader.parse(new InputSource(new StringReader(xml)));
}catch(Exception e){
e.printStackTrace();
}
}
```
---
> 除了上述两种方法,还有一种常用的方法:DOM解析
---
#### 解析JSON格式的数据
> 解析JSON的常用方法:JSONObject、GSON、Jackson、FastJSON等
- JSON数据
```
//假设要解析的JSON数据内容如下
{
"data": {
"address": "广东省 广州市",
"forecasts": [
{
"date": "2019-11-04",
"dayOfWeek": "1",
"dayWeather": "晴",
"nightWeather": "晴",
"dayTemp": "29℃",
"nightTemp": "19℃",
"dayWindDirection": "北",
"nightWindDirection": "北",
"dayWindPower": "4级",
"nightWindPower": "4级"
}
]}
}
```
- JSONObject
```
private void parseJSONWithJSONObject(String json){
private JSONObject forecastJson=new JSONObject(json);
private JSONObject data=forecastJson.getJSONObject("data");
private String address=data.getString("address");
private JSONArray forecast=data.getJSONArray("forecast");
private String date=forecast.getString("date");
private String dayOfWeek=forecast.getString("dayOfWeek");
private String dayCondition=forecast.getString("dayWeather");
private String nightCondition=forecast.getString("nightWeather");
private String dayTemp=forecast.getString("dayTemp");
private String nightTemp=forecast.getString("nightTemp");
private String dayWindDirection=forecast.getString("dayWindDirection");
private String nightWindDirection=forecast.getString("nightWindDirection");
private String dayWindPower=forecast.getString("dayWindPower");
private String nightWindPower=forecast.getString("nightWindPower");
}
```
- [GSON](https://github.com/google/gson)
> GSON将一段JSON格式的字符串自动映射成一个对象,从而不需要再手动编写代码一个个解析
```
//添加依赖库
dependencies {
implementation 'com.google.code.gson:gson:2.8.6'
}
//假设要解析的JSON数据如下
"forecasts": [
{
"date": "2019-11-04",
"dayOfWeek": "1",
"dayWeather": "晴",
"nightWeather": "晴",
"dayTemp": "29℃",
"nightTemp": "19℃",
"dayWindDirection": "北",
"nightWindDirection": "北",
"dayWindPower": "4级",
"nightWindPower": "4级"
},
{
"date": "2019-11-05",
"dayOfWeek": "2",
"dayWeather": "晴",
"nightWeather": "晴",
"dayTemp": "30℃",
"nightTemp": "17℃",
"dayWindDirection": "无风向",
"nightWindDirection": "无风向",
"dayWindPower": "≤3级",
"nightWindPower": "≤3级"
}
]
//解析JSON数组,需要借助TypeToken解析,创建class(类似java bean)以获得TypeToken
public class Forecast{
private String date;
private String dayOfWeek;
private String dayWeather;
private String nightWeather;
private String dayTemp;
private String nightTemp;
private String dayWindDirection;
private String nightWindDirection;
private String dayWindPower;
private String nightWindPower;
public String getDate() {
return date;
}
public void setDate(String date) {
this.date = date;
}
public String getDayOfWeek() {
return dayOfWeek;
}
public void setDayOfWeek(String dayOfWeek) {
this.dayOfWeek = dayOfWeek;
}
public String getDayWeather() {
return dayWeather;
}
public void setDayWeather(String dayWeather) {
this.dayWeather = dayWeather;
}
public String getNightWeather() {
return nightWeather;
}
public void setNightWeather(String nightWeather) {
this.nightWeather = nightWeather;
}
public String getDayTemp() {
return dayTemp;
}
public void setDayTemp(String dayTemp) {
this.dayTemp = dayTemp;
}
public String getNightTemp() {
return nightTemp;
}
public void setNightTemp(String nightTemp) {
this.nightTemp = nightTemp;
}
public String getDayWindDirection() {
return dayWindDirection;
}
public void setDayWindDirection(String dayWindDirection) {
this.dayWindDirection = dayWindDirection;
}
public String getNightWindDirection() {
return nightWindDirection;
}
public void setNightWindDirection(String nightWindDirection) {
this.nightWindDirection = nightWindDirection;
}
public String getDayWindPower() {
return dayWindPower;
}
public void setDayWindPower(String dayWindPower) {
this.dayWindPower = dayWindPower;
}
public String getNightWindPower() {
return nightWindPower;
}
public void setNightWindPower(String nightWindPower) {
this.nightWindPower = nightWindPower;
}
}
//借助GSON解析
private void parseJSONWithGson(String json){
GSON gson=new GSON();
List<Forecast> data=gson.fromJson(json, new TypeToken<List<Forecast>>(){}.getType());
for(Forecast forecast:data){
//do something yourself
}
}
```
---
- [关于GSON的更多用法](https://github.com/google/gson/blob/master/UserGuide.md)
---
#### java回调机制
- 应用场景:其他线程需要获得该线程的数据,如:
> 子线程调用网络连接得到数据,主线程可以通过回调机制获取数据;实现recyclerView的点击事件等。
- 将连接网络并返回响应的数据的功能封装成NetworkUtils类
```
public class NetworkUtils{
//该函数内部没有开启子线程执行网络连接,所以该函数不能放在主线程中直接执行,不然会阻塞主线程,造成APP崩溃
public static String getResponseFromHttp(String urlStr){
URL url=new URL(urlStr);
HttpURLConnection urlConnection=(HttpURLConnection)url.openConnection();
try{
InputStream in=urlConnection.getInputStream();
Scanner scanner=new Scanner(in);
scanner.useDelimiter("\\A");
if(scanner.hasNext())
return scanner.next();
else
return null;
}catch(IOException e){
e.printStackTrace();
}
}
//如果开启子线程执行网络连接,那么就需要考虑如何返回数据给调用方。
//因为调用方调用函数时,在函数返回数据之前,函数已经执行结束,
//此时调用方在另一个线程,而该函数在当前子线程中,在函数执行结束的情况下,无法直接通过return语句返回数据给调用方。这时回调机制即派上用场
//首先定义接口,接口中的onFinish()方法表示当服务器返回数据成功时调用,onError()方法表示当服务器返回数据失败时调用
public interface HttpCallbackListener{
void onFinish(String result);
void onError(Exception e);
}
public static void asyncGetResponseFromHttp(final String urlStr, final HttpCallbackListener litener){
new Thread(new Runnable(){
URL url=new URL(urlStr);
HttpURLConnection urlConnection=(HttpURLConnection)url.openConnection();
try{
InputStream in=urlConnection.getInputStream();
Scanner scanner=new Scanner(in);
scanner.useDelimiter("\\A");
if(scanner.hasNext())
listener.onFinish(scanner.next());
else
listener.onFinish(null);
}catch(IOException e){
listener.onError(e.printStackTrace());
}
}).start();
}
//OkHttp,自带了回调机制
public static void getResponseFromOkHttp(String urlStr, okhttp3.Callback callback){
OkHttpClient client=new OkHttpClient();
Request request=new Request().Builder()
.url(urlStr)
.build();
//与之前不同,这里调用enqueue()方法,而不是execute()方法,因为enqueue()方法会开启子线程,并将结果回调给okhttp3.Callback中
client.newCall(request).enqueue(callback);
}
}
```
```
//调用asyncGetResponseFromHttp
NetworUtils.asyncGetResponseFromHttp("https://github.com",new HttpCallbackListener(){
@Override
public void onFinish(String result){
//对返回数据处理
}
@Override
public void onError(Exception e){
//对异常情况处理
}
});
//调用getResponseFromOkHttp
NetworkUils.getResponseFromOkHttp("https://github.com",new okhttp3.Callback(){
@Override
public void onResponse(Call call, Response response) throws IOException{
//对返回数据处理
String data=response.body().string();
}
@Override
public void onFailure(Call call, IOException e){
//对异常情况处理
}
});
```
| 25.587379 | 259 | 0.638652 | yue_Hant | 0.412624 |
9b9a79111c1cc1a9ee382598c2165d591dd9221d | 764 | md | Markdown | README.md | Maastrich/mbox-to-json | 29434ce19ed2e09bf129d0db7205b869cabca637 | [
"MIT"
] | 1 | 2021-08-21T00:07:21.000Z | 2021-08-21T00:07:21.000Z | README.md | Maastrich/mbox-to-json | 29434ce19ed2e09bf129d0db7205b869cabca637 | [
"MIT"
] | null | null | null | README.md | Maastrich/mbox-to-json | 29434ce19ed2e09bf129d0db7205b869cabca637 | [
"MIT"
] | null | null | null | # Mbox Parser
mbox-tparser is a really simple package to transform mbox files to js object.
## Instalation
```sh
yarn add mbox-parser
# or
npm install mbox-parser
```
## Example 1:
Get all mails in a mbox file
```typescript
import { mboxParser } from "mbox-parser";
// here stream is a ReadStream to your mbox file
mboxParser(stream).then((mails) => {
console.log(mails);
});
```
## Example 2:
Get a specific page of a specific size in your mbox file
> First page is at number 1
```typescript
import { mboxParser } from "mbox-parser";
// here stream is a ReadStream to your mbox file
mboxParser(stream, {
pageSize: 20, // Number of mail to return
pageNumber: 4 // Index of the 'page' you want
}).then((mails) => {
console.log(mails);
});
}
```
| 17.363636 | 77 | 0.685864 | eng_Latn | 0.955833 |
9b9ab3779cd623aaa055f2a79a0fafdac42d9ae1 | 88 | md | Markdown | README.md | SoraSuegami/propagative_attestation_contracts | cb5255c95a96d0dc33681917b876593f06762a30 | [
"MIT"
] | 2 | 2020-06-26T01:33:22.000Z | 2020-07-07T01:32:59.000Z | README.md | SoraSuegami/propagative_attestation_contracts | cb5255c95a96d0dc33681917b876593f06762a30 | [
"MIT"
] | null | null | null | README.md | SoraSuegami/propagative_attestation_contracts | cb5255c95a96d0dc33681917b876593f06762a30 | [
"MIT"
] | 1 | 2020-06-25T05:11:05.000Z | 2020-06-25T05:11:05.000Z | # PDCN_contract
Contracts for PDCN (Public Device Control Network), written in Solidity
| 29.333333 | 71 | 0.818182 | kor_Hang | 0.737713 |
9b9adb0869b86b1ad1c258407d96c5e678b11167 | 2,259 | md | Markdown | README.md | MinervaLong/artistic-views | 696ebf5f9d69f36d615349f86964c8c4940a1684 | [
"MIT"
] | null | null | null | README.md | MinervaLong/artistic-views | 696ebf5f9d69f36d615349f86964c8c4940a1684 | [
"MIT"
] | 3 | 2021-06-05T10:45:48.000Z | 2021-06-10T11:23:07.000Z | README.md | MinervaLong/artistic-views | 696ebf5f9d69f36d615349f86964c8c4940a1684 | [
"MIT"
] | null | null | null | 

# Artistic Views Project
This project is meant to be a website to help no professional artists to promote their work and find alternatives spaces to show it. This alternatives are restaurants or cafes so, at the same time, it pretends to offer to these businesses an adding value for their clients.
This project is only for educational purposes although it would be nice to inspire some social initiative.
## Motivation
A couple of years ago I took draw lessons and we did some exhibitions in our educational center, but I missed the oportunity to show our work in different environments. Besides local galleries, there are not many options (it's hard enough for professionals already). Thinking about it, I came up with this idea to practice and improve my React skills.
## Status
Lerning how to implement an authentication system.
## Tech/Framework used
Built with:
* [React](https://reactjs.org/)
* [styled-components](https://styled-components.com/docs/)
* [Dummyapi.io](https://dummyapi.io/)
## Installation
In the terminal, inside the folder where you want to put your project:
```
git clone https://github.com/MinervaLong/artistic-views
cd artistic-views
npm install
npm start
```
Dependencies included:
* [react-router-dom](https://reactrouter.com/web/guides/quick-start)
* [react-hook-forms](https://react-hook-form.com/)
* [Axios](https://www.npmjs.com/package/axios)
* [Yup](https://www.npmjs.com/package/yup#mixeddefaultvalue-any-schema)
## Credits
[Credit for Sign-Up image](https://storyset.com/mobile) - Mobile illustrations by Storyset
[Credit for Login image](https://storyset.com/app) - App illustrations by Storyset
[Credit for HowItWorks section image](https://storyset.com/web) - Web illustrations by Storyset
[Credit for About image](https://storyset.com/transport) - Transport illustrations by Storyset
[Credit for diagram image](https://www.freepik.es/vectores/infografia) - Vector de Infografía creado por freepik - www.freepik.es</a>
| 43.442308 | 351 | 0.766268 | eng_Latn | 0.882027 |
9b9b3e8e87a1b463ce9803652a9e21d0c39c3fd0 | 72 | md | Markdown | README.md | jbadeau/ng-xtext | 1abeaed0e1c1b90439f60f4f490ed899a41c5f6b | [
"Apache-2.0"
] | null | null | null | README.md | jbadeau/ng-xtext | 1abeaed0e1c1b90439f60f4f490ed899a41c5f6b | [
"Apache-2.0"
] | 1 | 2018-06-20T12:40:53.000Z | 2018-06-20T12:40:53.000Z | README.md | jbadeau/ng-xtext | 1abeaed0e1c1b90439f60f4f490ed899a41c5f6b | [
"Apache-2.0"
] | null | null | null | # ng-xtext
An Angular component which integrates the xtext/orion editor
| 24 | 60 | 0.819444 | eng_Latn | 0.979251 |
9b9b9a71328f5e2e613e47adf06074ba29c2cfd4 | 2,124 | md | Markdown | m/muenz10eurobek_2009-03-04/index.md | nnworkspace/gesetze | 1d9a25fdfdd9468952f739736066c1ef76069051 | [
"Unlicense"
] | 1 | 2020-06-20T11:34:20.000Z | 2020-06-20T11:34:20.000Z | m/muenz10eurobek_2009-03-04/index.md | nagy/gesetze | 77abca2ceea3b7b89ea70afb13b5dd55415eb124 | [
"Unlicense"
] | null | null | null | m/muenz10eurobek_2009-03-04/index.md | nagy/gesetze | 77abca2ceea3b7b89ea70afb13b5dd55415eb124 | [
"Unlicense"
] | null | null | null | ---
Title: Bekanntmachung über die Ausprägung von deutschen Euro-Gedenkmünzen im Nennwert
von 10 Euro (Gedenkmünze „IAAF Leichtathletik WM Berlin 2009“)
jurabk: Münz10EuroBek 2009-03-04
layout: default
origslug: m_nz10eurobek_2009-03-04
slug: muenz10eurobek_2009-03-04
---
# Bekanntmachung über die Ausprägung von deutschen Euro-Gedenkmünzen im Nennwert von 10 Euro (Gedenkmünze „IAAF Leichtathletik WM Berlin 2009“) (Münz10EuroBek 2009-03-04)
Ausfertigungsdatum
: 2009-03-04
Fundstelle
: BGBl I: 2009, 460
## (XXXX)
Gemäß den §§ 2, 4 und 5 des Münzgesetzes vom 16. Dezember 1999 (BGBl.
I S. 2402) hat die Bundesregierung beschlossen, aus Anlass der IAAF
Leichtathletik Weltmeisterschaften 2009 in Berlin eine deutsche Euro-
Gedenkmünze im Nennwert von 10 Euro prägen zu lassen. Die Auflage der
Münze beträgt 1 890 000 Stück, darunter maximal 200 000 Stück in
Spiegelglanzausführung. Die Prägung erfolgt durch die fünf staatlichen
deutschen Münzstätten in Berlin, München, Stuttgart, Karlsruhe und
Hamburg.
Die Münze wird ab dem 9. April 2009 in den Verkehr gebracht. Sie
besteht aus einer Legierung von 925 Tausendteilen Silber und 75
Tausendteilen Kupfer, hat einen Durchmesser von 32,5 Millimetern und
eine Masse von 18 Gramm. Das Gepräge auf beiden Seiten ist erhaben und
wird von einem schützenden, glatten Randstab umgeben.
Die Bildseite der Münze zeigt eine gelungene Komposition aus der
Speerwerferin im Mittelpunkt, dem Hintergrund des dynamischen
Stadionschwunges und der Umschrift.
Die Wertseite zeigt einen Adler, den Schriftzug „BUNDESREPUBLIK
DEUTSCHLAND“, die Wertziffer und Wertbezeichnung sowie die Jahreszahl
2009 und die zwölf Europasterne.
Der glatte Münzrand enthält in vertiefter Prägung die Inschrift:
„SPORT BEWEGT DIE WELT“
sowie die Prägezeichen „A D F G J“ der deutschen Prägestätten.
Der Entwurf stammt von Herrn Bodo Broschat, Berlin.
## Schlussformel
Der Bundesminister der Finanzen
## (XXXX)
(Fundstelle: BGBl. I 2009, 460)
* * 
* 
| 35.4 | 170 | 0.794727 | deu_Latn | 0.996021 |
9b9ba8b54158d1a0bde376552430548744fd4b31 | 9,672 | md | Markdown | microsoft-365/security/defender/api-hello-world.md | MicrosoftDocs/microsoft-365-docs-pr.pt-BR | 88959f119be80545a0b854d261ba4acf2ac1e131 | [
"CC-BY-4.0",
"MIT"
] | 29 | 2019-09-17T04:18:20.000Z | 2022-03-20T18:51:42.000Z | microsoft-365/security/defender/api-hello-world.md | MicrosoftDocs/microsoft-365-docs-pr.pt-BR | 88959f119be80545a0b854d261ba4acf2ac1e131 | [
"CC-BY-4.0",
"MIT"
] | 2 | 2022-02-09T06:48:15.000Z | 2022-02-09T06:48:47.000Z | microsoft-365/security/defender/api-hello-world.md | MicrosoftDocs/microsoft-365-docs-pr.pt-BR | 88959f119be80545a0b854d261ba4acf2ac1e131 | [
"CC-BY-4.0",
"MIT"
] | 3 | 2021-03-14T23:52:56.000Z | 2021-05-31T14:02:38.000Z | ---
title: Hello World para Microsoft 365 Defender REST
description: Saiba como criar um aplicativo e usar um token para acessar as APIs de Microsoft 365 Defender
keywords: app, token, access, aad, app, application registration, powershell, script, administrador global, permission, microsoft 365 defender
search.product: eADQiWindows 10XVcnh
ms.prod: m365-security
ms.mktglfcycl: deploy
ms.sitesec: library
ms.pagetype: security
f1.keywords:
- NOCSH
ms.author: macapara
author: mjcaparas
ms.localizationpriority: medium
manager: dansimp
audience: ITPro
ms.collection: M365-security-compliance
ms.topic: conceptual
search.appverid:
- MOE150
- MET150
ms.technology: m365d
ms.openlocfilehash: 9b4280999786cda02c183bb0eb03bea8c2c93c84
ms.sourcegitcommit: d4b867e37bf741528ded7fb289e4f6847228d2c5
ms.translationtype: MT
ms.contentlocale: pt-BR
ms.lasthandoff: 10/06/2021
ms.locfileid: "60202638"
---
# <a name="hello-world-for-microsoft-365-defender-rest-api"></a>Hello World para Microsoft 365 Defender REST
[!INCLUDE [Microsoft 365 Defender rebranding](../includes/microsoft-defender.md)]
**Aplica-se a:**
- Microsoft 365 Defender
> [!IMPORTANT]
> Algumas informações estão relacionadas a produtos pré-lançados que podem ser substancialmente modificados antes de seu lançamento comercial. A Microsoft não faz garantias, expressas ou implícitas, quanto às informações fornecidas aqui.
## <a name="get-incidents-using-a-simple-powershell-script"></a>Obter incidentes usando um script simples do PowerShell
Deve levar de 5 a 10 minutos para concluir esse projeto. Essa estimativa de tempo inclui o registro do aplicativo e a aplicação do código do script de exemplo do PowerShell.
### <a name="register-an-app-in-azure-active-directory"></a>Registrar um aplicativo no Azure Active Directory
1. Entre no [Azure](https://portal.azure.com) como um usuário com a **função de administrador** global.
2. Navegue **até Azure Active Directory** registros do > **aplicativo** Novo > **registro**.

3. No formulário de registro, escolha um nome para seu aplicativo e selecione **Registrar**. Selecionar um URI de redirecionamento é opcional. Você não precisará de um para concluir este exemplo.
4. Em sua página de aplicativo, selecione **Permissões** de API Adicionar > > **APIs** de permissão que minha organização usa >, digite Proteção contra Ameaças da Microsoft e selecione Proteção contra Ameaças da Microsoft . Seu aplicativo agora pode acessar Microsoft 365 Defender.
> [!TIP]
> *A Proteção contra Ameaças* da Microsoft é um nome antigo para Microsoft 365 Defender e não aparecerá na lista original. Você precisa começar a escrever seu nome na caixa de texto para vê-lo aparecer.

- Escolha **Permissões de aplicativo** > **Incident.Read.All** e selecione Adicionar **permissões**.

5. Selecione **Conceder consentimento de administrador**. Sempre que você adicionar uma permissão, você deve selecionar **Conceder consentimento de administrador** para que ela entre em vigor.

6. Adicione um segredo ao aplicativo. Selecione **Certificados & segredos,** adicione uma descrição ao segredo e selecione **Adicionar**.
> [!TIP]
> Depois de selecionar **Adicionar**, selecione **copiar o valor secreto gerado.** Você não poderá recuperar o valor secreto depois de sair.

7. Grave sua ID de aplicativo e sua ID de locatário em algum lugar seguro. Eles estão listados em **Visão Geral** na página do aplicativo.

### <a name="get-a-token-using-the-app-and-use-the-token-to-access-the-api"></a>Obter um token usando o aplicativo e usar o token para acessar a API
Para obter mais informações sobre Azure Active Directory tokens, consulte o [tutorial do Azure AD](/azure/active-directory/develop/active-directory-v2-protocols-oauth-client-creds).
> [!IMPORTANT]
> Embora o exemplo neste aplicativo de demonstração incentive você a colar seu valor secreto para fins de teste, você nunca deve codificar segredos em um aplicativo em execução em produção. Um terceiro pode usar seu segredo para acessar recursos. Você pode ajudar a manter os segredos do seu aplicativo seguros usando o [Azure Key Vault.](/azure/key-vault/general/about-keys-secrets-certificates) Para ver um exemplo prático de como proteger seu aplicativo, consulte Gerenciar segredos em seus aplicativos de servidor com o [Azure Key Vault](/learn/modules/manage-secrets-with-azure-key-vault/).
1. Copie o script abaixo e o colar no editor de texto favorito. Salve como **Get-Token.ps1**. Você também pode executar o código como está no ISE do PowerShell, mas você deve salvá-lo, pois precisamos executar novamente quando usarmos o script de busca de incidentes na próxima seção.
Esse script gerará um token e o salvará na pasta de trabalho sob o nome, *Latest-token.txt*.
```PowerShell
# This script gets the app context token and saves it to a file named "Latest-token.txt" under the current directory.
# Paste in your tenant ID, client ID and app secret (App key).
$tenantId = '' # Paste your directory (tenant) ID here
$clientId = '' # Paste your application (client) ID here
$appSecret = '' # # Paste your own app secret here to test, then store it in a safe place!
$resourceAppIdUri = 'https://api.security.microsoft.com'
$oAuthUri = "https://login.windows.net/$tenantId/oauth2/token"
$authBody = [Ordered] @{
resource = $resourceAppIdUri
client_id = $clientId
client_secret = $appSecret
grant_type = 'client_credentials'
}
$authResponse = Invoke-RestMethod -Method Post -Uri $oAuthUri -Body $authBody -ErrorAction Stop
$token = $authResponse.access_token
Out-File -FilePath "./Latest-token.txt" -InputObject $token
return $token
```
#### <a name="validate-the-token"></a>Validar o token
1. Copie e colar o token recebido em [JWT](https://jwt.ms) para decodificá-lo.
1. *JWT* significa *JSON Web Token*. O token decodificado conterá um número de itens ou declarações formatados por JSON. Certifique-se de que *as funções* de declaração dentro do token decodificado contenham as permissões desejadas.
Na imagem a seguir, você pode ver um token decodificado adquirido de um aplicativo, com ```Incidents.Read.All``` ```Incidents.ReadWrite.All``` , e ```AdvancedHunting.Read.All``` permissões:

### <a name="get-a-list-of-recent-incidents"></a>Obter uma lista de incidentes recentes
O script a seguir **usará** Get-Token.ps1acessar a API. Em seguida, recupera uma lista de incidentes que foram atualizados pela última vez nas últimas 48 horas e salva a lista como um arquivo JSON.
> [!IMPORTANT]
> Salve esse script na mesma pasta que você salvou **Get-Token.ps1**.
```PowerShell
# This script returns incidents last updated within the past 48 hours.
$token = ./Get-Token.ps1
# Get incidents from the past 48 hours.
# The script may appear to fail if you don't have any incidents in that time frame.
$dateTime = (Get-Date).ToUniversalTime().AddHours(-48).ToString("o")
# This URL contains the type of query and the time filter we created above.
# Note that `$filter` does not refer to a local variable in our script --
# it's actually an OData operator and part of the API's syntax.
$url = "https://api.security.microsoft.com/api/incidents?$filter=lastUpdateTime+ge+$dateTime"
# Set the webrequest headers
$headers = @{
'Content-Type' = 'application/json'
'Accept' = 'application/json'
'Authorization' = "Bearer $token"
}
# Send the request and get the results.
$response = Invoke-WebRequest -Method Get -Uri $url -Headers $headers -ErrorAction Stop
# Extract the incidents from the results.
$incidents = ($response | ConvertFrom-Json).value | ConvertTo-Json -Depth 99
# Get a string containing the execution time. We concatenate that string to the name
# of the output file to avoid overwriting the file on consecutive runs of the script.
$dateTimeForFileName = Get-Date -Format o | foreach {$_ -replace ":", "."}
# Save the result as json
$outputJsonPath = "./Latest Incidents $dateTimeForFileName.json"
Out-File -FilePath $outputJsonPath -InputObject $incidents
```
Você terminou! Você conseguiu:
- Criado e registrado um aplicativo.
- Permissão concedida para que o aplicativo leia alertas.
- Conectado à API.
- Usou um script do PowerShell para retornar incidentes atualizados nas últimas 48 horas.
## <a name="related-articles"></a>Artigos relacionados
- [Microsoft 365 Defender Visão geral das APIs](api-overview.md)
- [Acessar as APIs Microsoft 365 Defender](api-access.md)
- [Criar um aplicativo para acessar Microsoft 365 Defender sem um usuário](api-create-app-web.md)
- [Criar um aplicativo para acessar Microsoft 365 Defender APIs em nome de um usuário](api-create-app-user-context.md)
- [Criar um aplicativo com acesso de parceiro de vários locatários a Microsoft 365 Defender APIs](api-partner-access.md)
- [Gerenciar segredos em seus aplicativos de servidor com o Azure Key Vault](/learn/modules/manage-secrets-with-azure-key-vault/)
- [Autorização OAuth 2.0 para entrada do usuário e acesso à API](/azure/active-directory/develop/active-directory-v2-protocols-oauth-code) | 53.436464 | 596 | 0.75517 | por_Latn | 0.975492 |
9b9c18133a607c2878e6f376f76b9a2a6dd5b632 | 5,136 | md | Markdown | README.md | antonbabenko/tfvars-annotations | dad2fc9a545c6378d41ff09a0f8c3904081b8f23 | [
"MIT"
] | 20 | 2019-05-01T09:37:20.000Z | 2021-08-18T15:37:51.000Z | README.md | antonbabenko/dynamic-tfvars | dad2fc9a545c6378d41ff09a0f8c3904081b8f23 | [
"MIT"
] | 2 | 2019-07-26T07:14:19.000Z | 2019-11-01T09:31:01.000Z | README.md | antonbabenko/dynamic-tfvars | dad2fc9a545c6378d41ff09a0f8c3904081b8f23 | [
"MIT"
] | 5 | 2019-07-27T10:09:00.000Z | 2022-02-08T06:08:13.000Z | # Update values in terraform.tfvars using annotations
## This project has become redundant (yay!)
## The same functionality is available natively in Terragrunt since [version 0.19.20](https://github.com/gruntwork-io/terragrunt/releases/tag/v0.19.20) (released 15th of August 2019).
### See [PR #3](https://github.com/antonbabenko/tfvars-annotations/pull/3) for the explanation and some extra unreleased code if you want to continue developing this for Terraform.
---
[Terraform](https://www.terraform.io/) is awesome!
As of today, Terraform 0.11 and 0.12 support only static (known, fixed, already computed) values in `tfvars` files. There is no way to use Terraform interpolation functions, or data-sources inside `tfvars` files in Terraform to update values.
While working on [modules.tf](https://github.com/antonbabenko/modules.tf-lambda) (a tool which converts visual diagrams created with [Cloudcraft.co](https://cloudcraft.co/) into Terraform configurations), I had a need to generate code which would chain invocations of [Terraform AWS modules](https://github.com/terraform-aws-modules) and pass arguments between them without requiring any extra Terraform code as a glue. [Terragrunt](https://github.com/gruntwork-io/terragrunt) is a great fit for this, it allows to reduce amount of Terraform configurations by reusing Terraform modules and providing arguments as values in `tfvars` files.
Some languages I know have concepts like annotations and decorators, so at first I made a [shell script](https://github.com/antonbabenko/modules.tf-lambda/blob/v1.2.0/templates/terragrunt-common-layer/common/scripts/update_dynamic_values_in_tfvars.sh) which replaced values in `tfvars` based on annotations and was called by Terragrunt hooks. `tfvars-annotations` shares the same goal and it has no external dependencies (except `terraform` or `terragrunt`).
## Use cases
1. modules.tf and Terragrunt (recommended)
1. Terraform (not implemented yet)
1. General example - AMI ID, AWS region
## Features
1. Supported annotations:
- [x] terragrunt_output:
- `@tfvars:terragrunt_output.vpc.vpc_id`
- `@tfvars:terragrunt_output.security-group.this_security_group_id`
- [ ] terraform_output
- [ ] data-sources generic
1. Type wrapping:
- `to_list`: Wrap original value with `[]` to make it it as a list
## How to use
Run `tfvars-annotations` before `terraform plan, apply, refresh`.
It will process tfvars file in the current directory and set updated values.
E.g.:
$ tfvars-annotations examples/project1-terragrunt/eu-west-1/app
$ terraform plan
## How to disable processing entirely
Put `@tfvars:disable_annotations` anywhere in the `terraform.tfvars` to not process the file.
## Examples
See `examples` for some basics.
## To-do
1. Get values from other sources:
- data sources generic
- aws_account_id or aws_region data sources
2. terragrunt_outputs from stacks:
- in any folder
- in current region
3. cache values unless stack is changed/updated
4. functions (limit(2), to_list)
5. rewrite in go (invoke like this => update_dynamic_values_in_tfvars ${get_parent_tfvars_dir()}/${path_relative_to_include()})
6. make it much faster, less verbose
7. add dry-run flag
8. Proposed syntax:
- `@tfvars:terragrunt_output.security-group_5.this_security_group_id.to_list`
- `@tfvars:terragrunt_output.["eu-west-1/security-group_5"].this_security_group_id.to_list`
- `@tfvars:terragrunt_output.["global/route53-zones"].zone_id`
- `@tfvars:terragrunt_data.aws_region.zone_id`
- `@tfvars:terragrunt_data.aws_region[{current=true}].zone_id`
## Bugs
1. Add support for `maps` (and lists of maps). Strange bugs with rendering comments in wrong places.
## Installation
On OSX, install it with Homebrew (not enough github stars to get it to the official repo):
```
brew install -s HomebrewFormula/tfvars-annotations.rb
```
Alternatively, you can download a [release](https://github.com/antonbabenko/tfvars-annotations/releases) suitable for your platform and unzip it. Make sure the `tfvars-annotations` binary is executable, and you're ready to go.
You can also install it like this:
```
go get github.com/antonbabenko/tfvars-annotations
```
Or run it from source:
```
go run . -debug examples/project1-terragrunt/eu-west-1/app
go run . examples/project1-terragrunt/eu-west-1/app
```
## Release
1. Make GitHub Release: `hub release create v0.0.3`. Then Github Actions will build binaries and attach them to Github release.
2. Update Homebrew version in `HomebrewFormula/tfvars-annotations.rb`. Install locally - `brew install -s HomebrewFormula/tfvars-annotations.rb`
## Authors
This project is created and maintained by [Anton Babenko](https://github.com/antonbabenko) with the help from [different contributors](https://github.com/antonbabenko/tfvars-annotations/graphs/contributors).
[](https://twitter.com/antonbabenko)
## License
This work is licensed under MIT License. See LICENSE for full details.
Copyright (c) 2019 Anton Babenko
| 41.088 | 638 | 0.771028 | eng_Latn | 0.918496 |
9b9c81ce929f8f40ebeb43d249417d4c721dcf45 | 47 | md | Markdown | README.md | augusthoel/appproject | 98293ffc6ad8780b674fd7546a253a0f6327dbd1 | [
"MIT"
] | null | null | null | README.md | augusthoel/appproject | 98293ffc6ad8780b674fd7546a253a0f6327dbd1 | [
"MIT"
] | null | null | null | README.md | augusthoel/appproject | 98293ffc6ad8780b674fd7546a253a0f6327dbd1 | [
"MIT"
] | null | null | null | # appproject
trying to make an app for android
| 15.666667 | 33 | 0.787234 | eng_Latn | 0.998615 |
9b9ca631864d79796c032f11fd047111c30cfa25 | 4,210 | md | Markdown | README.md | strudeljs/strudel | 37a22a806e6d0ee4fc38ae643caafeb2a1668e74 | [
"MIT"
] | 201 | 2017-04-19T08:26:42.000Z | 2021-12-13T01:49:50.000Z | README.md | strudeljs/strudel | 37a22a806e6d0ee4fc38ae643caafeb2a1668e74 | [
"MIT"
] | 87 | 2017-10-01T17:18:18.000Z | 2021-09-01T05:11:11.000Z | README.md | strudeljs/strudel | 37a22a806e6d0ee4fc38ae643caafeb2a1668e74 | [
"MIT"
] | 18 | 2017-10-01T11:11:58.000Z | 2020-10-23T13:42:03.000Z | <p align="center"><img width="100px" src="http://strudel.js.org/images/strudel-twoline.svg"></p>
<br>
<p align="center">
<a href="https://circleci.com/gh/strudeljs/strudel/tree/dev"><img src="https://circleci.com/gh/strudeljs/strudel.svg?style=shield&circle-token=:circle-token" alt="Build Status"></a>
<a href="https://codecov.io/gh/strudeljs/strudel"><img src="https://codecov.io/gh/strudeljs/strudel/branch/master/graph/badge.svg" alt="Codecov" /></a>
<a href="https://npmcharts.com/compare/strudel?minimal=true"><img src="https://img.shields.io/npm/dm/strudel.svg" alt="Downloads"></a>
<a href="https://www.npmjs.com/package/strudel"><img src="https://img.shields.io/npm/v/strudel.svg" alt="Version"></a>
<a href="https://www.npmjs.com/package/strudel"><img src="https://img.shields.io/npm/l/strudel.svg" alt="License"></a>
<a href="https://gitter.im/strudel-js"><img src="https://img.shields.io/gitter/room/nwjs/nw.js.svg" alt="Gitter"></a>
<br>
<a href="https://app.saucelabs.com/builds/d427e84981c34e139c003bc265cf9057"><img src="https://app.saucelabs.com/buildstatus/hayalet" alt="Build Status"></a>
</p>
## Introduction
Strudel.js is a lightweight framework that helps providing interactivity to back-end rendered pages through modern toolstack and usage of latest standards. It is designed to support writing code in elegant, DRY way in projects where you have little or no control over the HTML markup (i.e. projects based on back-end frameworks, component libraries or Content Management Systems). The main features are:
* **Declarative API**: Boilerplate reduced to minimum with handy decorators
* **Component architecture**: Modularised and encapsulated way of writing code
* **Small footprint**: Zero dependencies, concise API, ~4.5kb gzipped
* **Ecosystem**: Bunch of tools for better day-to-day developer life
## Browser Support
Strudel.js supports all the browsers that are [ES5-compliant](http://kangax.github.io/compat-table/es5/) and DOM4 compliant (IE10 and below not supported).
## Documentation
To check examples and docs visit [strudel.js.org](https://strudel.js.org).
## Ecosystem
| Project | Status | Description |
|---------|--------|-------------|
| [strudel-cli] | [![strudel-cli-status]][strudel-cli-package] | Project scaffolding |
| [strudel-redux] | [![strudel-redux-status]][strudel-redux-package] | State management |
| [eslint-plugin-strudel] | [![eslint-plugin-strudel-status]][eslint-plugin-strudel-package] | Official ESLint plugin |
| [strudel-devtools] | [![strudel-devtools-status]][strudel-devtools-package] | Browser DevTools extension |
| [strudel-jest] | [![strudel-jest-status]][strudel-jest-package] | Jest configuration preset |
[strudel-cli]: https://github.com/strudeljs/strudel-cli
[strudel-devtools]: https://github.com/strudeljs/strudel-devtools
[strudel-redux]: https://github.com/strudeljs/strudel-redux
[eslint-plugin-strudel]: https://github.com/strudeljs/eslint-plugin-strudel
[strudel-jest]: https://github.com/strudeljs/strudel-jest
[strudel-cli-status]: https://img.shields.io/npm/v/strudel-cli.svg
[strudel-devtools-status]: https://img.shields.io/chrome-web-store/v/akafkoceecgepokmamadojdimijcpnkl.svg
[strudel-redux-status]: https://img.shields.io/npm/v/strudel-redux.svg
[eslint-plugin-strudel-status]: https://img.shields.io/npm/v/eslint-plugin-strudel.svg
[strudel-jest-status]: https://img.shields.io/npm/v/strudel-jest.svg
[strudel-cli-package]: https://npmjs.com/package/strudel-cli
[strudel-devtools-package]: https://chrome.google.com/webstore/detail/strudel-devtools/akafkoceecgepokmamadojdimijcpnkl
[strudel-redux-package]: https://npmjs.com/package/strudel-cli
[eslint-plugin-strudel-package]: https://npmjs.com/package/eslint-plugin-strudel
[strudel-jest-package]: https://npmjs.com/package/strudel-jest
## Contribution
Please make sure to read the [Contributing Guide](https://github.com/strudeljs/strudel/blob/dev/.github/CONTRIBUTING.md) before making a pull request.
## Stay in touch
* [Twitter](https://twitter.com/strudeljs)
* [Blog](https://medium.com/strudel-js)
## License
[MIT](https://opensource.org/licenses/MIT)
Copyright (c) 2017-present, Mateusz Łuczak
| 58.472222 | 403 | 0.74133 | kor_Hang | 0.189905 |
9b9cde4a46c47a29de437b23db8c6eabd9042e39 | 644 | md | Markdown | _posts/2020-01-25-chatbot.md | MassDo/massdo.github.io | 57c9c20487bb5348b3acd9c335a9cefca39be141 | [
"BSD-3-Clause",
"MIT"
] | null | null | null | _posts/2020-01-25-chatbot.md | MassDo/massdo.github.io | 57c9c20487bb5348b3acd9c335a9cefca39be141 | [
"BSD-3-Clause",
"MIT"
] | null | null | null | _posts/2020-01-25-chatbot.md | MassDo/massdo.github.io | 57c9c20487bb5348b3acd9c335a9cefca39be141 | [
"BSD-3-Clause",
"MIT"
] | null | null | null | ---
title: "Chatbot (Flask)"
date: 2020-01-25
tags: [chatbot, flask, python]
---
Utilisation du framework Flask, pour la réalisation d'un chatbot, qui trouve des adresses et des anecdotes !
<img src="{{ site.url }}{{ site.baseurl }}/images/chatbot/chatbot1.gif" alt="chatbot">
Design responsive réalisé sans framework (flexbox uniquement)
<img src="{{ site.url }}{{ site.baseurl }}/images/chatbot/chatbot2.gif" alt="chatbot">
Compétences du projet:
Flask / Ajax / responsive design / Api / Pytest / Heroku
Accéder au [Chatbot](https://magicalgrandpy.herokuapp.com/) ou à son code sur [GitHub](https://github.com/MassDo/Projet-7-GrandPy)
| 32.2 | 130 | 0.725155 | fra_Latn | 0.495694 |
9b9ef73d296adea5c34fefeb4f1dd5bddfa9c3c2 | 3,405 | md | Markdown | README.zh.md | TristanTang/auto-excel | 2ae82bc2b80c4f52366984064a4115afe5bf0ac8 | [
"MIT"
] | null | null | null | README.zh.md | TristanTang/auto-excel | 2ae82bc2b80c4f52366984064a4115afe5bf0ac8 | [
"MIT"
] | null | null | null | README.zh.md | TristanTang/auto-excel | 2ae82bc2b80c4f52366984064a4115afe5bf0ac8 | [
"MIT"
] | null | null | null | 中文 | [English](https://github.com/feng-haitao/auto-excel/blob/master/README.md) | [文档](https://juejin.cn/post/6917606463921717262)
## 为什么使用AutoExcel?
Excel导入导出在软件开发中非常常见,只要你接触过开发,就一定会遇到。相信很多人会跟我一样选择用Apache POI来完成这项工作,在感受到POI功能强大的同时,我的团队也遇到了以下问题:
1. 直接使用POI操作Excel将产生大量硬编码,你会在编码中写死行索引和列索引
2. 大量不可复用的格式控制编码,如背景色、对齐方式、单元格样式等
3. 实施顾问明明提供了现成的模板,却还要开发用代码实现一遍,开发效率低下
4. 模板调整时不得不动用开发资源
5. 简单的导出也需要写特定的代码
**AutoExcel**解决了上述问题,它非常简单,只需要少量的代码即可完成复杂的导入导出;使用它时,程序员对导入导出无感,即不需要直接操作POI;与此同时,实施顾问提供的Excel即是导入导出模板,除非新增数据源或字段,否则模板更新不需要动用开发资源。
**AutoExcel**并没有对POI进行过重的封装,而是充分利用了Excel本身具有的特性——名称管理器,通过一些小技巧,将单元格与数据源产生映射,从而解耦程序员与POI,避免产生硬编码,让导入导出工作变得愉快而不再是枯燥乏味。
## 特点
- 模板导出
- 支持多个sheet
- 支持基础对象和表格数据
- 单个sheet支持多个不定长数据源
- 支持横向填充数据
- 自动应用单元格样式
- 自动填充行号
- 自动填充公式
- 自动合计
- 直接导出
- 支持多个sheet
- 导出带基本样式
- 自动列宽
- 导入
- 支持多个sheet
- 数据类型自动转换
- 支持百万数据秒级导入导出
## 功能预览
| 导出前 | 导出后 |
| ------------------------------------------------------------ | ------------------------------------------------------------ |
|  |  |
|  |  |
|  |  |
|  |  |
实现以上所有导出只需要编写以下少量代码(你需要额外的代码来准备数据源,例如从数据库中获取。示例中使用DataGenerator生成demo数据)
```java
// 设置导出参数,如数据源名称、数据源等
List<TemplateExportPara> paras = new ArrayList<>();
paras.add(new TemplateExportPara("BusinessUnit", DataGenerator.genBusinessUnit()));
paras.add(new TemplateExportPara("Contract", DataGenerator.genContracts()));
paras.add(new TemplateExportPara("Project", DataGenerator.genProjects(1)));
List<Product> products = DataGenerator.genProducts(1);
TemplateExportPara para3 = new TemplateExportPara("Product", products);
// 单个sheet有多个数据源时,上方数据源应设置为插入
para3.setInserted(true);
paras.add(para3);
TemplateExportPara para5 = new TemplateExportPara("Product2", products);
// 横向填充
para5.setDataDirection(DataDirection.Right);
paras.add(para5);
//(可选操作)移除不需要的sheet
ExcelSetting excelSetting = new ExcelSetting();
excelSetting.setRemovedSheets(Arrays.asList("will be removed"));
AutoExcel.save(this.getClass().getResource("/template/Export.xlsx").getPath(),
this.getClass().getResource("/").getPath() + "AutoExcel.xlsx",
paras,
excelSetting);
```
## 百万数据耗时测试
单位:毫秒
| | 10W行10列数据 | 100W行10列数据 |
| --------- | ------------- | -------------- |
| 模板导出 | 6,258 | 23,540 |
| 直接导出 | 5,711 | 24,952 |
| 导入 | 4,466 | 21,595 |
| 导入+转换 | 4,823 | 26,279 |
## Maven
```xml
<dependency>
<groupId>net.fenghaitao</groupId>
<artifactId>auto-excel</artifactId>
<version>2.0.0</version>
</dependency>
```
更多功能请前往[文档](https://juejin.cn/post/6917606463921717262)
| 35.46875 | 192 | 0.669604 | yue_Hant | 0.636267 |
9b9ef79f54dee13e8b9a8b8301c905f7196dbb52 | 10,192 | md | Markdown | manual/MANUAL-Crear-encuestas-en-Google-Forms.md | MarAvFe/sorbi | 04837f9fd7e358f80cdd2cf508bc0665325887b2 | [
"Apache-2.0"
] | null | null | null | manual/MANUAL-Crear-encuestas-en-Google-Forms.md | MarAvFe/sorbi | 04837f9fd7e358f80cdd2cf508bc0665325887b2 | [
"Apache-2.0"
] | null | null | null | manual/MANUAL-Crear-encuestas-en-Google-Forms.md | MarAvFe/sorbi | 04837f9fd7e358f80cdd2cf508bc0665325887b2 | [
"Apache-2.0"
] | null | null | null | Manual para crear Encuestas en Google Forms
===
Introducción
---
Este documento guiará al lector a través de las capacidades de Google Forms para crear diferentes tipos de preguntas. Pretende servir como guía paso a paso pero también como documento de consulta.
Justificación
---
La información nos permite tomar decisiones y aprender sobre nuestro entorno; se puede recopilar en el mundo por medio de las personas o de observación del ambiente. La ciencia y el estudio nos han llevado a confiar en la estadística como método de conclusión de información de comportamiento regular. Este comportamiento regular se puede observar censando sobre una muestra de tamaño considerable una serie repetitiva de preguntas para obtener tendencias que tienen las personas en su vivir diario. En este lugar entra el rol de nuestro instrumento, la encuesta.
Si tenemos que preguntar a un grupo de 5 personas sobre sus nombres, su ocupación y algunas preguntar sobre su ambiente laboral sencillas, podríamos utilizar una encuesta, y hacérsela llegar a cada persona para que la llenen y nos devuelvan los datos y poder tabular los resultados y terminar en quizá, un par de horas. Pero si tuvieramos que consultar a 200 personas, ya nos podría tomar una o hasta dos semanas de aplicar el instrumento y aplicar los datos. Aquí tenemos un problema, que se llama escalabilidad. La vía manual, que es la tabulación humana de estas encuestas, tiene un límite de procesamiento definido por la capacidad operativa del recurso humano.
Actualmente podemos sacar beneficio de herramientas que nos eliminan una de estas barreras, que es el trabajo de tabulación y aplicación de la encuesta automatizada. Si bien es cierto, aún hay que tomarse el tiempo para diseñar el instrumento, con un par de clicks, se puede hacer llegar electrónicamente esta encuesta a 10.000 personas, que puedan tomarse 10 minutos para completarla y luego estoy listo para procesar los datos, ya que los datos quedan agrupados y recopilados en un banco común. Y usualmente una mayor muestra me da mejores proyecciones poblacionales.
Para esta parte del proceso, utilizaremos una herramienta llamada Google Forms, la cuál ofrece una amplia gamma de tipos de preguntas y respuestas abiertas o cerradas y demás. Esto nos permitirá dedicar el tiempo del recurso humano fuera de la repetitiva tarea de digitar gran cantidad de datos, hacia la tarea de analizar los resultados y proveer un contexto más completo relativo a la información recaudada.
Requisitos
---
- Una cuenta de Google
- Una encuesta que digitalizar
- Una conexión a internet
Generalidades
---
Debe tomar en cuenta que la herramienta utiliza una nomenclatura para las preguntas de la encuesta un tanto diferente de lo que estamos acostumbrados. Principalmente debemos recordar que cuando queramos modelar una pregunta de "selección única", deberemos escoger "selección múltiple". Y que la modelar una pregunta de "seleccińo única", deberemoe escoger "casillas de verificación". Esto lo veremos con más detalle más adelante
Encuesta de ejemplo
---
Para tomar un ambiente verosímil que sirva de marco de trabajo, nuestra encuesta tendrá las siguientes preguntas:
1. ¿Cuál es su nombre?
2. ¿Considera usted que sigue un horario saludable de tiempos de comidas?
3. Seleccione los tiempos de comida que efectúa regularmente
4. ¿Qué cuidados conoce relativos a enfermedades gastrointestinales?
5. ¿Cuántas veces al año visita al médico?
Note cómo esta pequeña encuesta cuenta con preguntas abiertas, cerradas, opcionales, obligatorias, con rangos de respuesta y verdadero y falso.
Pasos
---
### Crear la encuesta
Para poder compartirla con colaboradores o participantes, debemos crear una encuesta que será almacenada en Google Drive (la nube), como un archivo con su respectivo nombre. Abajo se detallan los pasos para crear este archivo.
<table>
<tr>
<td width="30%">
<ul>
<li>Abra su navegador de internet de preferencia y escriba en la barra de direcciones <a href="http://forms.google.com/">http://forms.google.com/</a></li><br>
<li>En la pantalla que aparecerá, ingrese su correo electrónico y contraseña para iniciar sesión.</li>
</ul>
</td>
<td width="70%"><img src="./img/iniciar-sesion.png" alt="iniciar-sesion" /></td>
</tr>
<tr>
<td>
<ul>
<li>Cree un formulario seleccionando la opción de la izquierda que dice "En Blanco" con un gran "+" en el centro.</li>
</ul>
</td>
<td><img src="./img/crear-formulario.png" alt="crear-formulario" /></td>
</tr>
<tr>
<td>
<ul>
<li>A continuación deberá ser redirigido a la siguiente pantalla.</li>
<li>Para editar el nombre del archivo de la encuesta, debe hacer click sobre el texto de "Formulario sin título" de la esquina superior derecha. Esto cambiará también el título a mostrar a los participantes. Sin embargo si desea mostrar un nombre diferente, puede editarlo haciendo click sobre el título de la encuesta en negrita en el centro de la pantalla</li>
<li>Debajo de este título, existe un campo para una descripción del formulario donde podrá insertar un encabezado o descripción de la misma. El motivo de la encuesta, los objetivos o cualquier detalle que sea de interés al colaborador o participante.</li>
</ul>
</td>
<td><img src="./img/nuevo-formulario.png" alt="nuevo-formulario" /></td>
</tr>
<tr>
<td>
<ul>
<li>Este es el resultado de definir el nombre del archivo con un código de ejemplo de la encuesta y un título amistoso al participante.</li>
</ul>
</td>
<td><img src="./img/formulario-editado.png" alt="formulario-editado" /></td>
</tr>
</table>
<div class="page-break" />
### Agregar una pregunta de respuesta breve
Este proceso se repetirá tantas veces en la encuesta como preguntas existan. Según nuestro caso de ejemplo, lo haremos 5 veces. En resumen, se debe agregar el enunciado de la pregunta, seleccionar el tipo de pregunta y agregar sus respuestas según aplique. A continuación el proceso:
<table>
<tr>
<td width="30%">
<ul>
<li>Retomando en la pantalla anterior, note la "Pregunta sin título" que aparece por defecto. Haga click y cambie este título por el enunciado de la pregunta</li><br>
<li>Al hacer esto, se despliega al lado derecho un cuadro para seleccionar el tipo de pregunta. Proceda a seleccionar "Respuesta breve".</li>
<li>Una pregunta de respuesta breve no tiene opciones ya que es abierta. Por lo tanto habremos terminado con esta pregunta</li>
</ul>
</td>
<td width="70%"><img src="./img/pregunta-1.png" alt="pregunta-1" /></td>
</tr>
</table>
<div class="page-break" />
### Agregar una pregunta de verdadero o falso
Siguiendo la linea del procedimiento anterior:
<table>
<tr>
<td width="30%">
<ul>
<li>Retomando en la pantalla anterior, note que a la derecha de la pregunta aparece un botón con un "+". Haga click sobre él para agregar una nueva pregunta.</li><br>
<li>Al hacer esto, se despliega Un nuevo espacio para agregar una pregunta. Escriba el título de la segunda pregunta y seleccione el tipo "Selección múltiple".</li>
</ul>
</td>
<td width="70%"><img src="./img/pregunta-2.png" alt="pregunta-2" /></td>
</tr>
<tr>
<td width="30%">
<ul>
<li>Haga click en el título de "Opción 1" para agregar "Si"</li><br>
<li>Luego haga click sobre "Añadir opción" para agregar "No"</li>
</ul>
</td>
<td width="70%"><img src="./img/pregunta-2-llena.png" alt="pregunta-2-llena" /></td>
</tr>
</table>
<div class="page-break" />
### Agregar una pregunta de selección múltiple
Siguiendo la linea del procedimiento anterior:
<table>
<tr>
<td width="30%">
<ul>
<li>Agregue una nueva pregunta.</li><br>
<li>Escriba el título de la tercera pregunta y seleccione el tipo "Casillas de verificación".</li>
</ul>
</td>
<td width="70%"><img src="./img/pregunta-3.png" alt="pregunta-3" /></td>
</tr>
<tr>
<td width="30%">
<ul>
<li>Agregue cada una de las opciones disponibles en la encuesta. En este caso escribiremos 5 tiempos de comidas.</li>
</ul>
</td>
<td width="70%"><img src="./img/pregunta-3-llena.png" alt="pregunta-3-llena" /></td>
</tr>
</table>
<div class="page-break" />
### Agregar una pregunta con rangos de respuesta
Siguiendo la linea del procedimiento anterior:
<table>
<tr>
<td width="30%">
<ul>
<li>Agregue una nueva pregunta.</li><br>
<li>Escriba el título de la quinta pregunta y seleccione el tipo "Selección múltiple".</li>
<li>Note cómo a pesar de tener un enfoque de rangos, la pregunta se puede escribir como de selección única.</li>
</ul>
</td>
<td width="70%"><img src="./img/pregunta-5.png" alt="pregunta-5" /></td>
</tr>
</table>
<div class="page-break" />
### Compartir la encuesta
Para compartir la encuesta con colaboradores o participantes directamente, debemos obtener el enlace (link) de la encuesta o ingresar el correo electrónico de la persona.
<table>
<tr>
<td width="30%">
<ul>
<li>En la parte superior derecha de la página, seleccione el botón blanco que dice "Enviar".</li><br>
</ul>
</td>
<td width="70%"><img src="./img/boton-enviar.png" alt="boton-enviar" /></td>
</tr>
<tr>
<td width="30%">
<ul>
<li>Si queremos enviarlo por invitación al correo electrónico, solo debemos llenar el formulario que se despliega en pantalla y escribir el correo de cada participante.</li><br>
</ul>
</td>
<td width="70%"><img src="./img/enviar-correo.png" alt="enviar-correo" /></td>
</tr>
<tr>
<td width="30%">
<ul>
<li>Si queremos compartir un enlace por un enlace común como un correo institucional con varios destinatarios o un grupo de whatsapp, haremos click sobre el botón que parece un clip acostado</li>
<li>Luego haga click sobre "COPIAR" en la esquina inferior derecha de la ventana</li>
<li>Si gusta, por comodidad puede acortar el enlace marcando la caja de "Acortar URL". Esto creará un nuevo enlace más corto pero siempre hacia la misma encuesta.</li>
</ul>
</td>
<td width="70%"><img src="./img/enviar-url.png" alt="enviar-url" /></td>
</tr>
</table>
| 47.404651 | 665 | 0.725962 | spa_Latn | 0.994268 |
9b9fd5da3c449e615f418a5028682e7be8b000d1 | 294 | md | Markdown | README.md | mayarid/mql | ae86e3c7575d31d014f0bc2befff7509842d40ee | [
"MIT"
] | null | null | null | README.md | mayarid/mql | ae86e3c7575d31d014f0bc2befff7509842d40ee | [
"MIT"
] | null | null | null | README.md | mayarid/mql | ae86e3c7575d31d014f0bc2befff7509842d40ee | [
"MIT"
] | null | null | null | # MAYAR Query Languge
Agnostic query language for infrastructure as a code.
# Example
```python
from mql import MQLParser
import pprint
p = MQLParser(debug=False)
def query(query):
result = p.parse(query)
pprint.pprint(result)
while True:
q = input("MQL> ")
query("{};".format(q))
``` | 14.7 | 53 | 0.704082 | eng_Latn | 0.527529 |
9ba00a39f1a3423a045f897af858d406bbef0056 | 94 | md | Markdown | .changeset/tall-ties-juggle.md | PH4NTOMiki/kit | 4e4625ea6d9a084bc767ae216704aacd95fe8730 | [
"MIT"
] | null | null | null | .changeset/tall-ties-juggle.md | PH4NTOMiki/kit | 4e4625ea6d9a084bc767ae216704aacd95fe8730 | [
"MIT"
] | null | null | null | .changeset/tall-ties-juggle.md | PH4NTOMiki/kit | 4e4625ea6d9a084bc767ae216704aacd95fe8730 | [
"MIT"
] | null | null | null | ---
'@sveltejs/adapter-vercel': patch
---
The output of serverless now is ESM instead of CJS
| 15.666667 | 50 | 0.712766 | eng_Latn | 0.981874 |
9ba026fe042771bcd31a708fa235a8afb17abaee | 1,179 | md | Markdown | README.md | entityc/ec-tutorials | 0776f9ac7b17017d303ca01cf487aea6c938c538 | [
"BSD-3-Clause"
] | 1 | 2022-02-18T17:08:52.000Z | 2022-02-18T17:08:52.000Z | README.md | entityc/ec-tutorials | 0776f9ac7b17017d303ca01cf487aea6c938c538 | [
"BSD-3-Clause"
] | null | null | null | README.md | entityc/ec-tutorials | 0776f9ac7b17017d303ca01cf487aea6c938c538 | [
"BSD-3-Clause"
] | null | null | null | # ec-tutorials
This repository contains tutorials about the [Entity Compiler](https://github.com/entityc/entity-compiler) including an example application you can build with the compiler and templates.
|Tutorial|Description|
| ------ | --------- |
| [Entity Compiler](EntityCompiler) | Covers the Entity Compiler and its template engine that forms the foundation you will need to understand the other tutorials. |
| [Tutorial Microservice](TutorialMicroservice) | This tutorial takes you step by step in creating a microservice that can host these tutorials.|
| *more to come* | There is another tutorial in the works around localization. |
## Licensing
All projects of the EntityC Organization are under the BSD 3-clause License.
See [LICENSE.md](LICENSE.md) for details.
## Contributing
Contributors are welcome. Before contributing please read the following [Contributing Guidelines](CONTRIBUTING.md).
## Code of Conduct
The Code of Conduct governs how we behave in public or in private whenever the project will be judged by our actions. We expect it to be honored by everyone who contributes to this project.
See [Code of Conduct](CODE_OF_CONDUCT.md) for details.
| 45.346154 | 189 | 0.778626 | eng_Latn | 0.996107 |
9ba04463bf305bd3750a26e3aa991ee95ca9b303 | 1,604 | md | Markdown | includes/storsimple-8000-add-remove-volume-backup-policy-u2.md | changeworld/azure-docs.sv-se | 6234acf8ae0166219b27a9daa33f6f62a2ee45ab | [
"CC-BY-4.0",
"MIT"
] | null | null | null | includes/storsimple-8000-add-remove-volume-backup-policy-u2.md | changeworld/azure-docs.sv-se | 6234acf8ae0166219b27a9daa33f6f62a2ee45ab | [
"CC-BY-4.0",
"MIT"
] | null | null | null | includes/storsimple-8000-add-remove-volume-backup-policy-u2.md | changeworld/azure-docs.sv-se | 6234acf8ae0166219b27a9daa33f6f62a2ee45ab | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
author: alkohli
ms.service: storsimple
ms.topic: include
ms.date: 10/26/2018
ms.author: alkohli
ms.openlocfilehash: 92036cebf0541f9e9928acf1a9c32db0037bde48
ms.sourcegitcommit: 2ec4b3d0bad7dc0071400c2a2264399e4fe34897
ms.translationtype: MT
ms.contentlocale: sv-SE
ms.lasthandoff: 03/28/2020
ms.locfileid: "67187534"
---
#### <a name="to-add-or-remove-a-volume"></a>Så här lägger du till eller tar bort en volym
1. Gå till din StorSimple-enhet och klicka på **Säkerhetskopieringspolicy**.
2. Markera och klicka på den princip som du vill ändra i tabelllistan för principerna. Högerklicka om du vill anropa snabbmenyn och välj sedan **Lägg till/ta bort volym**.

3. Markera eller avmarkera kryssrutan om du vill lägga till eller ta bort volymen i bladet **Lägg till/ta** bort volym. Flera volymer markeras/avmarkeras genom att markera eller avmarkera motsvarande kryssrutor.

Om du tilldelar volymer från olika volymbehållare till en säkerhetskopieringsprincip måste du komma ihåg att växla över dessa volymbehållare tillsammans. Du kommer att se en varning om detta.

4. Du meddelas när säkerhetskopieringsprincipen ändras. Listan för principer för säkerhetskopiering uppdateras också.

| 43.351351 | 211 | 0.792394 | swe_Latn | 0.980333 |
9ba12da7610b53eeebd6ca6656ba3eb9b3e27306 | 185 | md | Markdown | README.md | Thann/jquery-magicRows | 6c68a68ba791daf9ca1ca99ea7d43742f123e44a | [
"Unlicense"
] | null | null | null | README.md | Thann/jquery-magicRows | 6c68a68ba791daf9ca1ca99ea7d43742f123e44a | [
"Unlicense"
] | null | null | null | README.md | Thann/jquery-magicRows | 6c68a68ba791daf9ca1ca99ea7d43742f123e44a | [
"Unlicense"
] | null | null | null | # jquery-magicRows
Inserts invisible rows so when one El expands the row below always gets pushed down
Only needed for bootstrap 3.x and below because flexboxes dont have this problem
| 37 | 83 | 0.816216 | eng_Latn | 0.998923 |
9ba2337603fe8051e7afea7c3455b57dbca87172 | 249 | md | Markdown | java/docs/SourceType.md | dlens/dlxapi | 189a6519240ce625d7a9cdb89e305a335d2aa045 | [
"MIT"
] | null | null | null | java/docs/SourceType.md | dlens/dlxapi | 189a6519240ce625d7a9cdb89e305a335d2aa045 | [
"MIT"
] | 1 | 2020-08-20T17:31:43.000Z | 2020-08-20T17:31:43.000Z | java/docs/SourceType.md | dlens/dlxapi | 189a6519240ce625d7a9cdb89e305a335d2aa045 | [
"MIT"
] | null | null | null |
# SourceType
## Enum
* `ESTIMATE` (value: `"ESTIMATE"`)
* `GOOGLESHEETS` (value: `"GOOGLESHEETS"`)
* `MANUALENTRY` (value: `"MANUALENTRY"`)
* `SPREADSHEET` (value: `"SPREADSHEET"`)
* `SYSTEM` (value: `"SYSTEM"`)
* `DLC` (value: `"DLC"`)
| 11.857143 | 42 | 0.586345 | yue_Hant | 0.987653 |
9ba2de6e5b8f5ff10e4068bf6ba58b09cb749132 | 1,279 | md | Markdown | Docs/HashGenerator.md | lleocastro/encryptor | 33ac996f6a2966f79337c2e0bcdc7c2b392a8cee | [
"MIT"
] | null | null | null | Docs/HashGenerator.md | lleocastro/encryptor | 33ac996f6a2966f79337c2e0bcdc7c2b392a8cee | [
"MIT"
] | null | null | null | Docs/HashGenerator.md | lleocastro/encryptor | 33ac996f6a2966f79337c2e0bcdc7c2b392a8cee | [
"MIT"
] | null | null | null | ## PHP Hash Generator
> Generates an encrypted hash of 107 byte for max security of data
```php
//Construct the HashGenerator.
$encryption = new HashGenerator("2a", "MTc2MzMxNDQ4NTdmZDg4Yz", "8");
//or, not args. Use default settings.
$encryption = new HashGenerator();
//Generate hash
$hash = $encryption->encode("Hello World!");
//Output: "UYFSOVDTqZVNjxmUHNVbrVzUVFDeSV0d1N1aGN1THhTdWRkUyElakRnSEpEaKRUQ0oURxUFVYhmTSVEb1QFWwJXZVVjNWRlUO10aWNzVVlDW";
//or, use variables.
$data = "Hello World!";
$hash = $encryption->encode($data);
//Output: "UYFSOVDTqZVNjxmUHNVbrVzUVFDeSV0d1N1aGN1THhTdWRkUyElakRnSEpEaKRUQ0oURxUFVYhmTSVEb1QFWwJXZVVjNWRlUO10aWNzVVlDW";
```
## Comparable Hashs
> Compare if two hashes are equals returning a boolean value
```php
//Data comparable - is hash a "Hello World!"
$hashGenerated = "UYFSOVDTqZVNjxmUHNVbrVzUVFDeSV0d1N1aGN1THhTdWRkUyElakRnSEpEaKRUQ0oURxUFVYhmTSVEb1QFWwJXZVVjNWRlUO10aWNzVVlDW";
$dataComparable = "Welcome";
$equals = $encryption->isEquals($dataComparable, $hashGenerated); //Return false, because "Hello World!" !== "Welcome".
$equals = $encryption->isEquals("Hello World!", $hashGenerated); //Return true, because "Hello World!" === "Hello World!".
```
## Exceptions
`InvalidArgumentException` - if arguments not valid.
| 31.195122 | 128 | 0.770915 | yue_Hant | 0.453411 |
9ba2fe9871811e64fb8eb6eaa4b276bfa67faeac | 27 | md | Markdown | README.md | GuestEG/Type07 | 22736c416a01ccb19f10225af8a4606f9a75b6fd | [
"MIT"
] | null | null | null | README.md | GuestEG/Type07 | 22736c416a01ccb19f10225af8a4606f9a75b6fd | [
"MIT"
] | null | null | null | README.md | GuestEG/Type07 | 22736c416a01ccb19f10225af8a4606f9a75b6fd | [
"MIT"
] | null | null | null | # Type07
Type07 Prototype/
| 9 | 17 | 0.777778 | slk_Latn | 0.373132 |
9ba475246f1303e5176d0e3da59ffcfbf02065f3 | 422 | md | Markdown | README.md | akshaybharambe14/spinner | 3a2db14f3a33a1b0c692f754ed960f4279a8084e | [
"MIT"
] | 1 | 2020-01-23T11:49:34.000Z | 2020-01-23T11:49:34.000Z | README.md | akshaybharambe14/spinner | 3a2db14f3a33a1b0c692f754ed960f4279a8084e | [
"MIT"
] | null | null | null | README.md | akshaybharambe14/spinner | 3a2db14f3a33a1b0c692f754ed960f4279a8084e | [
"MIT"
] | null | null | null | # A simple Spinner with configurable speed and duration

## Example
```go
package main
import (
"time"
"github.com/akshaybharambe14/spinner"
)
func main() {
s := spinner.New(spinner.Default, 5, spinner.NoDuration)
q := make(chan struct{})
go func() {
// work
time.Sleep(time.Second * 5)
// end
q <- struct{}{}
}()
s.Start(q)
}
```
| 14.066667 | 60 | 0.563981 | eng_Latn | 0.660913 |
9ba5703eafd4ff1fb2b1ccfabfd9e0db3fbec7f5 | 9,470 | md | Markdown | cn.zh-cn/API参考/源端为Elasticsearch-云搜索服务.md | huaweicloudDocs/dgc | eef6266fe71cb39b9912d442c2f17e672ba4d23a | [
"RSA-MD"
] | 2 | 2020-04-23T03:13:48.000Z | 2020-05-12T09:12:00.000Z | cn.zh-cn/API参考/源端为Elasticsearch-云搜索服务.md | huaweicloudDocs/dgc | eef6266fe71cb39b9912d442c2f17e672ba4d23a | [
"RSA-MD"
] | null | null | null | cn.zh-cn/API参考/源端为Elasticsearch-云搜索服务.md | huaweicloudDocs/dgc | eef6266fe71cb39b9912d442c2f17e672ba4d23a | [
"RSA-MD"
] | 3 | 2020-01-02T08:19:06.000Z | 2021-01-07T01:29:26.000Z | # 源端为Elasticsearch/云搜索服务<a name="dgc_02_0293"></a>
## JSON样例<a name="zh-cn_topic_0108272828_section33401108172339"></a>
```
"from-config-values": {
"configs": [
{
"inputs": [
{
"name": "fromJobConfig.index",
"value": "cdm"
},
{
"name": "fromJobConfig.type",
"value": "es"
},
{
"name": "fromJobConfig.columnList",
"value": "a1:numeric&s1:string"
},
{
"name": "fromJobConfig.splitNestedField",
"value": "true"
},
{
"name": "fromJobConfig.queryString",
"value": "last_name:Smith"
}
],
"name": "fromJobConfig"
}
]
}
```
## 参数说明<a name="zh-cn_topic_0108272828_section61808073174843"></a>
<a name="zh-cn_topic_0108272828_table6307873415412"></a>
<table><thead align="left"><tr id="zh-cn_topic_0108272828_row2882542015412"><th class="cellrowborder" valign="top" width="22.657734226577343%" id="mcps1.1.5.1.1"><p id="zh-cn_topic_0108272828_p5315765115412"><a name="zh-cn_topic_0108272828_p5315765115412"></a><a name="zh-cn_topic_0108272828_p5315765115412"></a>参数</p>
</th>
<th class="cellrowborder" valign="top" width="20.157984201579843%" id="mcps1.1.5.1.2"><p id="zh-cn_topic_0108272828_p1080249515412"><a name="zh-cn_topic_0108272828_p1080249515412"></a><a name="zh-cn_topic_0108272828_p1080249515412"></a>是否必选</p>
</th>
<th class="cellrowborder" valign="top" width="16.2983701629837%" id="mcps1.1.5.1.3"><p id="zh-cn_topic_0108272828_p258693615412"><a name="zh-cn_topic_0108272828_p258693615412"></a><a name="zh-cn_topic_0108272828_p258693615412"></a>类型</p>
</th>
<th class="cellrowborder" valign="top" width="40.885911408859116%" id="mcps1.1.5.1.4"><p id="zh-cn_topic_0108272828_p821526915412"><a name="zh-cn_topic_0108272828_p821526915412"></a><a name="zh-cn_topic_0108272828_p821526915412"></a>说明</p>
</th>
</tr>
</thead>
<tbody><tr id="zh-cn_topic_0108272828_row3532522715412"><td class="cellrowborder" valign="top" width="22.657734226577343%" headers="mcps1.1.5.1.1 "><p id="zh-cn_topic_0108272828_p31423427144217"><a name="zh-cn_topic_0108272828_p31423427144217"></a><a name="zh-cn_topic_0108272828_p31423427144217"></a>fromJobConfig.index</p>
</td>
<td class="cellrowborder" valign="top" width="20.157984201579843%" headers="mcps1.1.5.1.2 "><p id="zh-cn_topic_0108272828_p62269650144217"><a name="zh-cn_topic_0108272828_p62269650144217"></a><a name="zh-cn_topic_0108272828_p62269650144217"></a>是</p>
</td>
<td class="cellrowborder" valign="top" width="16.2983701629837%" headers="mcps1.1.5.1.3 "><p id="zh-cn_topic_0108272828_p10676914144217"><a name="zh-cn_topic_0108272828_p10676914144217"></a><a name="zh-cn_topic_0108272828_p10676914144217"></a>String</p>
</td>
<td class="cellrowborder" valign="top" width="40.885911408859116%" headers="mcps1.1.5.1.4 "><p id="zh-cn_topic_0108272828_p59523723144217"><a name="zh-cn_topic_0108272828_p59523723144217"></a><a name="zh-cn_topic_0108272828_p59523723144217"></a>抽取数据的索引,类似关系数据库中的数据库名称。</p>
</td>
</tr>
<tr id="zh-cn_topic_0108272828_row2888033144824"><td class="cellrowborder" valign="top" width="22.657734226577343%" headers="mcps1.1.5.1.1 "><p id="zh-cn_topic_0108272828_p32604129144824"><a name="zh-cn_topic_0108272828_p32604129144824"></a><a name="zh-cn_topic_0108272828_p32604129144824"></a>fromJobConfig.type</p>
</td>
<td class="cellrowborder" valign="top" width="20.157984201579843%" headers="mcps1.1.5.1.2 "><p id="zh-cn_topic_0108272828_p23688773144824"><a name="zh-cn_topic_0108272828_p23688773144824"></a><a name="zh-cn_topic_0108272828_p23688773144824"></a>是</p>
</td>
<td class="cellrowborder" valign="top" width="16.2983701629837%" headers="mcps1.1.5.1.3 "><p id="zh-cn_topic_0108272828_p39742454144824"><a name="zh-cn_topic_0108272828_p39742454144824"></a><a name="zh-cn_topic_0108272828_p39742454144824"></a>String</p>
</td>
<td class="cellrowborder" valign="top" width="40.885911408859116%" headers="mcps1.1.5.1.4 "><p id="zh-cn_topic_0108272828_p65022171144824"><a name="zh-cn_topic_0108272828_p65022171144824"></a><a name="zh-cn_topic_0108272828_p65022171144824"></a>抽取数据的类型,类似关系数据库中的表名。</p>
</td>
</tr>
<tr id="zh-cn_topic_0108272828_row5037735615412"><td class="cellrowborder" valign="top" width="22.657734226577343%" headers="mcps1.1.5.1.1 "><p id="zh-cn_topic_0108272828_p52978520144217"><a name="zh-cn_topic_0108272828_p52978520144217"></a><a name="zh-cn_topic_0108272828_p52978520144217"></a>fromJobConfig.columnList</p>
</td>
<td class="cellrowborder" valign="top" width="20.157984201579843%" headers="mcps1.1.5.1.2 "><p id="zh-cn_topic_0108272828_p63401693144217"><a name="zh-cn_topic_0108272828_p63401693144217"></a><a name="zh-cn_topic_0108272828_p63401693144217"></a>否</p>
</td>
<td class="cellrowborder" valign="top" width="16.2983701629837%" headers="mcps1.1.5.1.3 "><p id="zh-cn_topic_0108272828_p35263486144217"><a name="zh-cn_topic_0108272828_p35263486144217"></a><a name="zh-cn_topic_0108272828_p35263486144217"></a>String</p>
</td>
<td class="cellrowborder" valign="top" width="40.885911408859116%" headers="mcps1.1.5.1.4 "><p id="zh-cn_topic_0108272828_p37770149144217"><a name="zh-cn_topic_0108272828_p37770149144217"></a><a name="zh-cn_topic_0108272828_p37770149144217"></a>需要抽取的字段列表,字段名之间使用<span class="parmvalue" id="zh-cn_topic_0108272828_parmvalue1296851616438"><a name="zh-cn_topic_0108272828_parmvalue1296851616438"></a><a name="zh-cn_topic_0108272828_parmvalue1296851616438"></a>“&”</span>分隔,例如:<span class="parmvalue" id="zh-cn_topic_0108272828_parmvalue2845770316447"><a name="zh-cn_topic_0108272828_parmvalue2845770316447"></a><a name="zh-cn_topic_0108272828_parmvalue2845770316447"></a>“id&gid&name”</span>。</p>
</td>
</tr>
<tr id="zh-cn_topic_0108272828_row1583494418571"><td class="cellrowborder" valign="top" width="22.657734226577343%" headers="mcps1.1.5.1.1 "><p id="zh-cn_topic_0108272828_p16834174416571"><a name="zh-cn_topic_0108272828_p16834174416571"></a><a name="zh-cn_topic_0108272828_p16834174416571"></a>fromJobConfig.splitNestedField</p>
</td>
<td class="cellrowborder" valign="top" width="20.157984201579843%" headers="mcps1.1.5.1.2 "><p id="zh-cn_topic_0108272828_p883484425711"><a name="zh-cn_topic_0108272828_p883484425711"></a><a name="zh-cn_topic_0108272828_p883484425711"></a>否</p>
</td>
<td class="cellrowborder" valign="top" width="16.2983701629837%" headers="mcps1.1.5.1.3 "><p id="zh-cn_topic_0108272828_p8057768172040"><a name="zh-cn_topic_0108272828_p8057768172040"></a><a name="zh-cn_topic_0108272828_p8057768172040"></a>Boolean</p>
</td>
<td class="cellrowborder" valign="top" width="40.885911408859116%" headers="mcps1.1.5.1.4 "><p id="zh-cn_topic_0108272828_p9286172411394"><a name="zh-cn_topic_0108272828_p9286172411394"></a><a name="zh-cn_topic_0108272828_p9286172411394"></a>选择是否将nested字段的json内容拆分,例如:将<span class="uicontrol" id="zh-cn_topic_0108272828_uicontrol2957184253017"><a name="zh-cn_topic_0108272828_uicontrol2957184253017"></a><a name="zh-cn_topic_0108272828_uicontrol2957184253017"></a>“a:{ b:{ c:1, d:{ e:2, f:3 } } }”</span> 拆成三个字段<span class="uicontrol" id="zh-cn_topic_0108272828_uicontrol139867186304"><a name="zh-cn_topic_0108272828_uicontrol139867186304"></a><a name="zh-cn_topic_0108272828_uicontrol139867186304"></a>“a.b.c”</span>、<span class="uicontrol" id="zh-cn_topic_0108272828_uicontrol62201525173012"><a name="zh-cn_topic_0108272828_uicontrol62201525173012"></a><a name="zh-cn_topic_0108272828_uicontrol62201525173012"></a>“a.b.d.e”</span>、<span class="uicontrol" id="zh-cn_topic_0108272828_uicontrol6379733173013"><a name="zh-cn_topic_0108272828_uicontrol6379733173013"></a><a name="zh-cn_topic_0108272828_uicontrol6379733173013"></a>“a.b.d.f”</span>。</p>
</td>
</tr>
<tr id="zh-cn_topic_0108272828_row135064715715"><td class="cellrowborder" valign="top" width="22.657734226577343%" headers="mcps1.1.5.1.1 "><p id="zh-cn_topic_0108272828_p1235024712574"><a name="zh-cn_topic_0108272828_p1235024712574"></a><a name="zh-cn_topic_0108272828_p1235024712574"></a>fromJobConfig.queryString</p>
</td>
<td class="cellrowborder" valign="top" width="20.157984201579843%" headers="mcps1.1.5.1.2 "><p id="zh-cn_topic_0108272828_p2035074705717"><a name="zh-cn_topic_0108272828_p2035074705717"></a><a name="zh-cn_topic_0108272828_p2035074705717"></a>否</p>
</td>
<td class="cellrowborder" valign="top" width="16.2983701629837%" headers="mcps1.1.5.1.3 "><p id="zh-cn_topic_0108272828_p13400129013"><a name="zh-cn_topic_0108272828_p13400129013"></a><a name="zh-cn_topic_0108272828_p13400129013"></a>String</p>
</td>
<td class="cellrowborder" valign="top" width="40.885911408859116%" headers="mcps1.1.5.1.4 "><p id="zh-cn_topic_0108272828_p16865173219416"><a name="zh-cn_topic_0108272828_p16865173219416"></a><a name="zh-cn_topic_0108272828_p16865173219416"></a>使用Elasticsearch的查询字符串(query string)对源数据进行过滤,CDM只迁移满足过滤条件的数据。</p>
</td>
</tr>
</tbody>
</table>
| 96.632653 | 1,149 | 0.708659 | yue_Hant | 0.255702 |
9ba5bf5f7e066fcc3d30f99f0533b7d4436cc0b4 | 24 | md | Markdown | README.md | tianhongjie/config | c6cc5ed8b32c535341b7016ec8e389bd481d75ff | [
"CC0-1.0"
] | null | null | null | README.md | tianhongjie/config | c6cc5ed8b32c535341b7016ec8e389bd481d75ff | [
"CC0-1.0"
] | null | null | null | README.md | tianhongjie/config | c6cc5ed8b32c535341b7016ec8e389bd481d75ff | [
"CC0-1.0"
] | null | null | null | # config
Charlie Config
| 8 | 14 | 0.791667 | nno_Latn | 0.680671 |
9ba5e8e14c771743fa104a0acaf7947bbc995e3d | 1,335 | md | Markdown | docs/vs-2015/code-quality/c6329.md | LouisFr81/visualstudio-docs.fr-fr | e673e36b5b37ecf1f5eb97c42af84eed9c303200 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/vs-2015/code-quality/c6329.md | LouisFr81/visualstudio-docs.fr-fr | e673e36b5b37ecf1f5eb97c42af84eed9c303200 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/vs-2015/code-quality/c6329.md | LouisFr81/visualstudio-docs.fr-fr | e673e36b5b37ecf1f5eb97c42af84eed9c303200 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
title: C6329 | Microsoft Docs
ms.custom: ''
ms.date: 11/15/2016
ms.prod: visual-studio-dev14
ms.reviewer: ''
ms.suite: ''
ms.technology:
- vs-devops-test
ms.tgt_pltfrm: ''
ms.topic: article
f1_keywords:
- C6329
helpviewer_keywords:
- C6329
ms.assetid: 5765bd4d-5fa1-4e51-82d6-c1837b4743db
caps.latest.revision: 7
author: mikeblome
ms.author: mblome
manager: ghogen
ms.openlocfilehash: 18ca2f21ecd31ac1926f290fe9349e600ec15d6f
ms.sourcegitcommit: af428c7ccd007e668ec0dd8697c88fc5d8bca1e2
ms.translationtype: MT
ms.contentlocale: fr-FR
ms.lasthandoff: 11/16/2018
ms.locfileid: "51767762"
---
# <a name="c6329"></a>C6329
[!INCLUDE[vs2017banner](../includes/vs2017banner.md)]
avertissement C6329 : retourner la valeur d’un appel à \<fonction > ne doit pas être comparée à \<numéro >
Le programme compare un nombre par rapport à la valeur de retour d’un appel à `CreateFile`. Si `CreateFile` réussit, elle retourne un handle ouvert vers l’objet. Si elle échoue, elle retourne `INVALID_HANDLE_VALUE`.
## <a name="example"></a>Exemple
Ce code peut entraîner l’avertissement :
```cpp
if (CreateFile() == NULL)
{
return;
}
```
## <a name="example"></a>Exemple
Ce code corrige l’erreur :
```cpp
if (CreateFile() == INVALID_HANDLE_VALUE)
{
return;
}
```
| 23.421053 | 218 | 0.701124 | fra_Latn | 0.399531 |
9ba96788b36dcb5c932caae6601ce717bd6883e5 | 2,813 | md | Markdown | README.md | guibwl/hooks-reducer | 9e0334ae36b85a4ba3aba0835f7c2f5fd1c244a1 | [
"MIT"
] | 1 | 2020-11-21T16:10:43.000Z | 2020-11-21T16:10:43.000Z | README.md | guibwl/hooks-reducer | 9e0334ae36b85a4ba3aba0835f7c2f5fd1c244a1 | [
"MIT"
] | null | null | null | README.md | guibwl/hooks-reducer | 9e0334ae36b85a4ba3aba0835f7c2f5fd1c244a1 | [
"MIT"
] | null | null | null | ## Why
Your may like use Redux to manage and share a global state in your Application,
but you also like to use React-hooks. hooks-reducer let you keep Redux programming mode.
so you can easy to switch React.Component and Redux to React-hooks and hooks-reducer.
## feature
- Use with React hooks.
- Global state in Application.
- Share state to any descendant component.
- Keep Redux programming mode, easy to update for old application.
## Usage
#### Inject store to your Application.
```jsx
import {HooksProvider} from 'hooks-reducer';
import rootReducer from './yourConfigs/rootReducer.js';
const store = rootReducer;
function App() {
return (
<HooksProvider hooksStore={store}>
<MyComponent/>
</HooksProvider>
)
}
ReactDom.render(
<App/>,
document.getElementById('root')
);
```
#### Use mergeReducer to combine your reducers.
```js
import {mergeReducer} from 'hooks-reducer';
import * as reducerFoo from './pageFoo/reducerFoo.js';
import * as reducerBar from './pageBar/reducerBar.js';
const rootReducer = mergeReducer({
reducerFoo,
reducerBar
});
export default rootReducer;
```
#### Connect your component and hooks-reducer, get state and action.
```jsx
import {useEffect} from 'react';
import {connect} from 'hooks-reducer';
const enhancedAction = (data) => (state, dispatch) => {
// request service or do some other things...
dispatch({type: 'enhancedAction', data: data});
};
const generalAction = (data) =>
({type: 'enhancedAction', data: data});
function Component(props) {
const [state, dispatch] = props.reducer;
// Get your state in props.reducer;
// Don`t recommend you use dispatch, should use action instead.
const {generalAction, enhancedAction} = props.actions;
// Get your actions in props.actions;
useEffect(() => {
enhancedAction('Any type of data');
}, []);
console.log('My state: ', state);
return (
<div>
Hello world!
<button onClick={generalAction.bind(null, 'Any type of data')}>
Action now!
</button>
</div>
)
}
const MyComponent = connect(
Component,
'reducer', // Define your reducer key name in props
{
enhancedAction,
generalAction
// Define more action...
},
'actions' // Define your actions key name in props
);
export default MyComponent;
```
#### Example of reducer:
```js
const initialState = {
data: ''// Any type of data.
};
function reducerBar(state=initialState, action) {
switch (action.type) {
case 'updateData':
return {...state, data: action.data};
case 'resetData':
return initialState;
default:
return state;
}
}
export default reducerBar;
``` | 22.869919 | 88 | 0.644152 | eng_Latn | 0.869497 |
9bac9758decd8728fde03ab8757e001f1bf19c2e | 67 | md | Markdown | README.md | ShubhamKahlon57/Letsupgrade-python-Batch-7 | 7989c2d2f17e58dd4ee8f278c37d2c1d18e5e3af | [
"Apache-2.0"
] | null | null | null | README.md | ShubhamKahlon57/Letsupgrade-python-Batch-7 | 7989c2d2f17e58dd4ee8f278c37d2c1d18e5e3af | [
"Apache-2.0"
] | null | null | null | README.md | ShubhamKahlon57/Letsupgrade-python-Batch-7 | 7989c2d2f17e58dd4ee8f278c37d2c1d18e5e3af | [
"Apache-2.0"
] | null | null | null | # Letsupgrade-python-Batch-7
Assignment submission of Letsupgrade
| 22.333333 | 37 | 0.835821 | eng_Latn | 0.873662 |
9bacbb9ddf96f0a60f9d9420826fca4e8d88c45f | 21 | md | Markdown | README.md | Emmanuel-9/Consultancy | a13a63efcfd733a21e24334e1bf0850d764ac8d4 | [
"MIT"
] | null | null | null | README.md | Emmanuel-9/Consultancy | a13a63efcfd733a21e24334e1bf0850d764ac8d4 | [
"MIT"
] | null | null | null | README.md | Emmanuel-9/Consultancy | a13a63efcfd733a21e24334e1bf0850d764ac8d4 | [
"MIT"
] | null | null | null | ## CONSULTANCY APP
| 5.25 | 18 | 0.666667 | kor_Hang | 0.998084 |
9bae5a3a83696d9e9a87b1f67ac02bcbae82dd60 | 72 | md | Markdown | README.md | insanitywholesale/yavvar | 50054eed8d8b75aa22319cf6a4897288cd77f62c | [
"BSD-2-Clause"
] | null | null | null | README.md | insanitywholesale/yavvar | 50054eed8d8b75aa22319cf6a4897288cd77f62c | [
"BSD-2-Clause"
] | null | null | null | README.md | insanitywholesale/yavvar | 50054eed8d8b75aa22319cf6a4897288cd77f62c | [
"BSD-2-Clause"
] | null | null | null | # yavvar
askhseis algorithmikh kai antikeimenostrefh ston fakelo plain
| 18 | 61 | 0.847222 | hun_Latn | 0.093045 |
9baf8cd26f12cc20b59a1676d86f21649a47a427 | 1,328 | md | Markdown | _posts/2016-10-13-github-jekyll-setup.md | the7sign/the7sign.github.io | 69d0ac65c957d6412641549f80fa9ba58772b079 | [
"MIT"
] | null | null | null | _posts/2016-10-13-github-jekyll-setup.md | the7sign/the7sign.github.io | 69d0ac65c957d6412641549f80fa9ba58772b079 | [
"MIT"
] | null | null | null | _posts/2016-10-13-github-jekyll-setup.md | the7sign/the7sign.github.io | 69d0ac65c957d6412641549f80fa9ba58772b079 | [
"MIT"
] | null | null | null | ---
layout: post
title: "GitHub & Jekyll Setup"
date: 2016-10-12 00:00:00
categories: web
tags: github jekyll setup
comments: true
---
깃허브를 이용해 마크다운 블로그를 만드는 방법을 찾다가 jekyll 이라는 걸 확인하고 아래와 같이 설정해서 사용중입니다.
(참고로 윈도우10 기준입니다)
## Ruby & Ruby Devkit 설치
[http://rubyinstaller.org/downloads/][rubyinstall] 에 접속 해서 최신 버전의 파일을 다운받는다.
작성일 기준으로 rubyinstaller-2.3.1-x64.exe / DevKit-mingw64-64-4.7.2-20130224-1432-sfx.exe

위와 같이 설치중 가운데 부분의 PATH 설정을 체크 한 후 사용한다. (안해서 설치는 되지만 후에 개발중 편의를 위해서)
DevKit의 경우 적절한 위치에 압축을 푼다. (ex C:\RubyDevKit)
## Jekyll 설치
콘솔창을 RubyDevKit 위치에서 열고 아래와 같이 입력한다.
``` bash
gem install jekyll
```
> **Note**
> - SSL_connect returned=1 errno=0 state=SSLv3 read server certificate B: certificate verify failed (https://api.rubygems.org/specs.4.8.gz)
> - 설치중에 위의 메시지처럼 SSL인증 오류가 발생하는 케이스가 있는데 이럴때는 아래와 같은 형태로 install 작업을 진행한다.
> - gem install jekyll --source http://rubygems.org
페이징용으로 아래의 gem도 추가 설치 한다.
``` bash
gem install jekyll-paginate
```
## 테마 설치
기본적으로 테마 설치 없이도 사용이 가능하지만 디자인을 위해서 아래 사이트에서 내려받는것을 추천한다.
[http://jekyllthemes.org/][jekylltheme]
선택된 테마의 사이트로 이동해서 git clone으로 소스를 내려받으면 기본 설정은 완료된다.
[rubyinstall]: http://rubyinstaller.org/downloads/
[jekylltheme]: http://jekyllthemes.org/
내려받은 소스의 문서를 바탕으로 마크다운문법에 맞춰 작성한다. | 22.896552 | 141 | 0.71762 | kor_Hang | 1.000004 |
9bb03a1eab5495553e26228d9366a7ca24bed276 | 20 | md | Markdown | README.md | Hidayetarslan/react-example-todo | 4f19ba957a70f439d9f20cd6df4d5f1f49dc438d | [
"Apache-2.0"
] | null | null | null | README.md | Hidayetarslan/react-example-todo | 4f19ba957a70f439d9f20cd6df4d5f1f49dc438d | [
"Apache-2.0"
] | null | null | null | README.md | Hidayetarslan/react-example-todo | 4f19ba957a70f439d9f20cd6df4d5f1f49dc438d | [
"Apache-2.0"
] | null | null | null | # react-example-todo | 20 | 20 | 0.8 | eng_Latn | 0.886421 |
9bb09281171781683f438df8716b932f6a415537 | 413 | md | Markdown | README.md | jormin/yii2-phpexcel | 2b3ffba0028ddb626bdf3872eec578ce739e0687 | [
"MIT"
] | null | null | null | README.md | jormin/yii2-phpexcel | 2b3ffba0028ddb626bdf3872eec578ce739e0687 | [
"MIT"
] | null | null | null | README.md | jormin/yii2-phpexcel | 2b3ffba0028ddb626bdf3872eec578ce739e0687 | [
"MIT"
] | null | null | null | # 说明
Yii2 处理 Excel 文件, 修改自[moonlandsoft/yii2-phpexcel](https://github.com/moonlandsoft/yii2-phpexcel)。
修改项:
1. 导出文件后退出脚本导致程序后续代码无法执行的问题
## 安装
1. 安装包文件
``` bash
$ composer require jormin/yii2-phpexcel
```
## 使用
1. 代码中使用参见 [moonlandsoft/yii2-phpexcel](https://github.com/moonlandsoft/yii2-phpexcel)
## License
The MIT License (MIT). Please see [License File](LICENSE.md) for more information.
| 17.208333 | 97 | 0.714286 | yue_Hant | 0.281906 |
9bb133687df8aa8aaa0134bf74c84a8440dc1209 | 2,995 | md | Markdown | src/en/2020-04-cq/04/02.md | PrJared/sabbath-school-lessons | 94a27f5bcba987a11a698e5e0d4279b81a68bc9a | [
"MIT"
] | 68 | 2016-10-30T23:17:56.000Z | 2022-03-27T11:58:16.000Z | src/en/2020-04-cq/04/02.md | PrJared/sabbath-school-lessons | 94a27f5bcba987a11a698e5e0d4279b81a68bc9a | [
"MIT"
] | 367 | 2016-10-21T03:50:22.000Z | 2022-03-28T23:35:25.000Z | src/en/2020-04-cq/04/02.md | PrJared/sabbath-school-lessons | 94a27f5bcba987a11a698e5e0d4279b81a68bc9a | [
"MIT"
] | 109 | 2016-08-02T14:32:13.000Z | 2022-03-31T10:18:41.000Z | ---
title: Invaluable and Unreachable
date: 18/10/2020
---
#### inGest
In one of the most fascinating ways, Job 28:12–21 describes God’s wisdom and the futility of human endeavor to obtain it outside of Him. Job does this by pointing out two things: (1) the value of wisdom, and (2) the hiddenness of its source. The ultimate purpose of this passage shows that God’s ideal for us is (1) beyond human estimate and (2) beyond human intellectual, physical, and spiritual ability. The first is the limit of our potential to understand, while the second is the limitation of our actual understanding. This chapter in Job concludes with the comforting thought that in God, what was once impossible without Him becomes totally attainable by Him (Job 28:28).
**Its Worth**
From verses 15–17, gold is mentioned four times and in four various forms. The first word in verse 15, segore, occurs only twice in the Bible (the other is in Hosea 13:8). In verse 16, Job refers to the gold (kethem) of Ophir, which is often translated as fine gold. Verse 17 mentions gold (zahab) with glass or crystal in the beginning of the verse and fine gold (paz) at the end—the first is widely mentioned in the Bible, more than three hundred times, while the latter is mentioned less than ten times. The former denotes the golden color, while the latter refers to refined gold.
Job uses four different words for gold to refer to the worth of wisdom. The passage states that what God requires of us is unattainable and priceless. The value of God’s ideal for His children could not be purchased with any form of gold, whether it be common, special, rare, refined, or the purest gold of all. This wisdom that is not common, but rather religious in its affairs and salvific in its nature, is not for sale—it exceeds all estimable value.
**Its Place**
Even if, for the sake of argument, someone had what it takes to purchase this wisdom that leads to salvation, another challenge confronts us: the place where this wisdom resides is unapproachable. Job seeks to explain that no one knows where this wisdom is or where it came from; it has carefully hidden itself from our eyes and may as well be higher than the highest bird can fly.
Some believe that the Rüppell’s griffon vulture is the highest-flying bird in the world, reaching heights of nearly 40,000 feet in the air! Speaking of the unreachable heights of God’s wisdom, Job says that it is concealed even from the birds of the air that, in some cases, are able to fly as high as commercial airliners. “It is hidden from the eyes of all living” (Job 28:21) means that if it were possible to combine all human intelligence to seek out the location of this wisdom, the search would be in vain.
“Behold, the fear of the Lord, that is wisdom, and to depart from evil is understanding” (Job 28:28). Although God’s ideal for us is above the highest human thought and more costly than silver, gold, or precious rubies, it is attainable through “fear of the Lord.”
`` | 124.791667 | 679 | 0.777963 | eng_Latn | 0.999986 |
9bb413d93ca138dd0c1a9158ceb96a9e2768d54f | 128 | md | Markdown | README.md | vkom76/light-chat | 933f6241ea5b9d29199981325ba1c85ff0537bf9 | [
"Apache-2.0"
] | null | null | null | README.md | vkom76/light-chat | 933f6241ea5b9d29199981325ba1c85ff0537bf9 | [
"Apache-2.0"
] | null | null | null | README.md | vkom76/light-chat | 933f6241ea5b9d29199981325ba1c85ff0537bf9 | [
"Apache-2.0"
] | null | null | null | # LightChat Web App
Пример чата - веб-приложение создаваемое в рамках прохождения Спринт-1,2 Middle Front-end Яндекс.Практикум.
| 42.666667 | 107 | 0.8125 | rus_Cyrl | 0.726708 |
9bb62e8124a644166ed814c060b515ad8a18fe4f | 200 | md | Markdown | README.md | JapeshBagga/javascript-quiz | 30bd3c3f75e3065e3da287c22ebd35dbdac5955b | [
"Apache-2.0"
] | 1 | 2020-10-15T07:33:59.000Z | 2020-10-15T07:33:59.000Z | README.md | JapeshBagga/javascript-quiz | 30bd3c3f75e3065e3da287c22ebd35dbdac5955b | [
"Apache-2.0"
] | null | null | null | README.md | JapeshBagga/javascript-quiz | 30bd3c3f75e3065e3da287c22ebd35dbdac5955b | [
"Apache-2.0"
] | 2 | 2020-10-01T14:56:57.000Z | 2020-10-01T20:24:19.000Z | ## Javascript quiz
## Introduction
A simple quiz template written in js/jquery and is responsively designed.
In the future, I will add a generator to add questions, etc.
## How to use ?
| 10 | 73 | 0.705 | eng_Latn | 0.997851 |
9bb797e7f2a5b7d2ab048781a70d295c5aa98ae3 | 363 | md | Markdown | api/docs/stentor-models.googlemapslocation.lng.md | stentorium/stentor | f49b51e8b4f82012d1ac8ddd15af279bd4619229 | [
"Apache-2.0"
] | 2 | 2019-12-30T19:23:17.000Z | 2021-07-06T02:47:39.000Z | api/docs/stentor-models.googlemapslocation.lng.md | stentorium/stentor | f49b51e8b4f82012d1ac8ddd15af279bd4619229 | [
"Apache-2.0"
] | 74 | 2020-01-07T00:25:16.000Z | 2022-02-23T04:06:56.000Z | api/docs/stentor-models.googlemapslocation.lng.md | stentorium/stentor | f49b51e8b4f82012d1ac8ddd15af279bd4619229 | [
"Apache-2.0"
] | 1 | 2021-01-01T08:57:23.000Z | 2021-01-01T08:57:23.000Z | <!-- Do not edit this file. It is automatically generated by API Documenter. -->
[Home](./index.md) > [stentor-models](./stentor-models.md) > [GoogleMapsLocation](./stentor-models.googlemapslocation.md) > [lng](./stentor-models.googlemapslocation.lng.md)
## GoogleMapsLocation.lng property
<b>Signature:</b>
```typescript
lng: number;
```
| 30.25 | 183 | 0.694215 | yue_Hant | 0.445224 |
9bb7b577cfb2797d601adf9f0ace25405fb25331 | 680 | md | Markdown | content/restapi/checkout.md | SenseNet/docs.sensenet.com | 595eae271a1a2b72e84bba1caaebba7cb73b605d | [
"MIT"
] | 1 | 2022-01-31T13:51:01.000Z | 2022-01-31T13:51:01.000Z | content/restapi/checkout.md | SenseNet/docs.sensenet.com | 595eae271a1a2b72e84bba1caaebba7cb73b605d | [
"MIT"
] | 60 | 2020-04-21T10:31:32.000Z | 2021-11-05T08:14:00.000Z | content/restapi/checkout.md | SenseNet/docs.sensenet.com | 595eae271a1a2b72e84bba1caaebba7cb73b605d | [
"MIT"
] | 6 | 2020-04-28T13:16:25.000Z | 2022-01-26T11:21:04.000Z | ---
title: CheckOut
metaTitle: "sensenet API - CheckOut"
metaDescription: "CheckOut"
---
## CheckOut
- Method: **POST**
- Icon: **"checkout"**.
Creates a new version of the requested content and locks it exclusively for the current user.
The version number is changed according to the content's versioning mode.
### Request example:
```
POST /odata.svc/Root/...('targetContent')/CheckOut
```
### Parameters:
There are no parameters.
### Return value:
The modified content. (Type: `Content`).
### Requirements:
- **AllowedRoles**: Everyone
- **RequiredPermissions**: Save
- **RequiredPolicies**: VersioningAndApproval
- **Scenarios**: ListItem, ExploreActions, ContextMenu
| 21.935484 | 93 | 0.716176 | eng_Latn | 0.672015 |
9bb82f5e4fc010f29fa34918266d0c4be30b1a71 | 612 | md | Markdown | CONTRIBUTING.md | ryan-blunden/docker-weekly-data | 3ab5b04403f3c28988f24e385c59fde46fc5fe47 | [
"MIT"
] | 1 | 2017-05-23T10:50:47.000Z | 2017-05-23T10:50:47.000Z | CONTRIBUTING.md | ryan-blunden/docker-weekly-api | 3ab5b04403f3c28988f24e385c59fde46fc5fe47 | [
"MIT"
] | null | null | null | CONTRIBUTING.md | ryan-blunden/docker-weekly-api | 3ab5b04403f3c28988f24e385c59fde46fc5fe47 | [
"MIT"
] | null | null | null | # Contributing guide
*** Currently a blank canvas upon which beautiful instructions will be painted on in the near future. ***
Must read:
- https://help.github.com/articles/setting-guidelines-for-repository-contributors/
- https://github.com/nayafia/contributing-template/blob/master/CONTRIBUTING-template.md
- http://mozillascience.github.io/working-open-workshop/contributing/
## How to file a bug report (try using issue and pull request templates)
## How to suggest a new feature
## How to set up your environment and run tests
## Wanted types of contributions
## How contributors should get in touch | 34 | 105 | 0.776144 | eng_Latn | 0.926305 |
9bb9aab39c12972408a5cc8e55a6d0afaf2e0f0e | 1,184 | md | Markdown | spring-boot-actuator/README.md | jeikerxiao/SpringBootStudy | 3947994c553374d6006bb269f42d5f534bb03ca0 | [
"MIT"
] | 3 | 2017-06-27T03:34:24.000Z | 2018-12-20T09:38:16.000Z | spring-boot-actuator/README.md | jeikerxiao/spring-boot | 3947994c553374d6006bb269f42d5f534bb03ca0 | [
"MIT"
] | null | null | null | spring-boot-actuator/README.md | jeikerxiao/spring-boot | 3947994c553374d6006bb269f42d5f534bb03ca0 | [
"MIT"
] | 1 | 2022-02-21T01:53:53.000Z | 2022-02-21T01:53:53.000Z | # spring-boot-actuator
Actuator 是 Spring Boot 提供的对应用系统的自省和监控的集成功能,可以对应用系统进行配置查看、相关功能统计等。
## 依赖
pom.xml
```xml
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
```
## 配置
application.properties
关闭权限控制,使接口都可见,不然会报401-Unauthorized.
```
management.security.enabled=false
```
## Actuator 功能
|HTTP方法| 路径| 描述| 鉴权
|---|---|---|---
|GET| /autoconfig| 查看自动配置的使用情况| true
|GET| /configprops |查看配置属性,包括默认配置|true
|GET| /beans |查看bean及其关系列表 |true
|GET| /dump |打印线程栈 |true
|GET| /env |查看所有环境变量 |true
|GET| /env/{name} |查看具体变量值 |true
|GET| /health |查看应用健康指标 |false
|GET| /info |查看应用信息 |false
|GET| /mappings |查看所有url映射 |true
|GET| /metrics |查看应用基本指标 |true
|GET| /metrics/{name} |查看具体指标 |true
|POST| /shutdown |关闭应用 |true
|GET| /trace |查看基本追踪信息 |true
## 运行
GET:
http://localhost:8080/health
```javascript
{
"status": "UP",
"diskSpace": {
"status": "UP",
"total": 120108089344,
"free": 10089127936,
"threshold": 10485760
}
}
```
| 17.411765 | 65 | 0.666385 | yue_Hant | 0.317848 |
9bba7aec76ef76a01bdaa8e2eec74d1da4c0e319 | 2,156 | md | Markdown | README.md | dananderson/sdl2-link | 5d875f12a1444d3aef0d87eec2ac813d77f9392e | [
"MIT"
] | 4 | 2018-06-04T16:22:34.000Z | 2019-06-17T17:58:49.000Z | README.md | dananderson/sdl2-link | 5d875f12a1444d3aef0d87eec2ac813d77f9392e | [
"MIT"
] | null | null | null | README.md | dananderson/sdl2-link | 5d875f12a1444d3aef0d87eec2ac813d77f9392e | [
"MIT"
] | 1 | 2019-06-17T18:01:25.000Z | 2019-06-17T18:01:25.000Z | # sdl2-link
FFI bindings for SDL 2.0.
sdl2-link provides a fluent API that allows for specifying the native call module and the SDL 2.0
extensions to be loaded. The result of load() is a namespace containing the available functions, constants,
macros and structs. The naming follows the SDL 2.0 C API as closely as possible.
* Supports FFI-compatible native call libraries, including fastcall and ffi.
* Supports SDL 2.0 extensions:
* SDL2_image
* SDL2_mixer
* SDL2_ttf
## Requirements
* The SDL 2.0 library must be available through the system's library path.
* Supply an FFI-compatible native call libraries via dependency injection.
* [fastcall](https://www.npmjs.com/package/fastcall) (Recommended)
* [ffi-napi](https://www.npmjs.com/package/ffi-napi) + [ref-napi](https://www.npmjs.com/package/ref-napi)
* [ffi](https://www.npmjs.com/package/ffi) + [ref](https://www.npmjs.com/package/ref)
## Installation
```
npm install sdl2-link
```
## Getting Started
### SDL 2.0 API
```javascript
import sdl2link from 'sdl2-link';
const SDL = sdl2link()
.withFastcall(require('fastcall'))
.load();
SDL.SDL_Init(SDL.SDL_INIT_VIDEO);
```
### SDL 2.0 Extensions
```javascript
import sdl2link from 'sdl2-link';
const SDL = sdl2link()
.withFastcall(require('fastcall'))
.withTTF()
.load();
SDL.TTF_Init();
SDL.SDL_Init(SDL.SDL_INIT_VIDEO);
```
## Caveats
Some of the Joystick and GameController APIs are not compatible with fastcall. All these APIs have been separated out
into a separate extension that can only be loaded with ffi. If you are using fastcall, you can safely use ffi to load
the joystick extension.
## SDL 2.0 Documentation
The namespace (object) sdl2-link returns contains constants, structs and functions exactly as they appear in the SDL 2.0 API. Use the official SDL 2.0 documentation for reference.
* [SDL2](https://wiki.libsdl.org/CategoryAPI)
* [SDL2_ttf](https://www.libsdl.org/projects/SDL_ttf/docs/SDL_ttf.html)
* [SDL2_image](https://www.libsdl.org/projects/SDL_image/docs/SDL_image.html)
* [SDL2_mixer](https://www.libsdl.org/projects/SDL_mixer/docs/index.html)
| 29.135135 | 179 | 0.731911 | eng_Latn | 0.779197 |
9bbad0ad2c97b6fe7901c703cdc655e83c3c9c54 | 2,670 | md | Markdown | readme.md | phytonmk/useDeferredState | 23ff8caef6163b3e9562c7beeafe2465028dcf50 | [
"MIT"
] | 3 | 2021-02-27T13:53:32.000Z | 2021-07-18T05:35:47.000Z | readme.md | phytonmk/useDeferredState | 23ff8caef6163b3e9562c7beeafe2465028dcf50 | [
"MIT"
] | null | null | null | readme.md | phytonmk/useDeferredState | 23ff8caef6163b3e9562c7beeafe2465028dcf50 | [
"MIT"
] | null | null | null | # useDeferredState
A React hook for deferring state change. That's essential when your UI needs to wait for disappearing animation is complete to unmount component.
## Motivation
The problem of waiting a disappearing animation in React is common and usually being skipped as non-trivial. The goal of the project is to make an easy solution of the problem possible in declarative React way.
## Installation
```bash
yarn add use-deferred-state
```
or, using npm
```bash
npm install use-deferred-state
```
## Usage
```tsx
useDeferredState<BaseState>(baseState: BaseState, instantValues: BaseState[] = [], defferFor = 500): BaseState
```
The hook takes a `baseState` and returns it as is but all `baseState` changes are deferred for `defferFor` ms.
You can also pass an `instantValues` – array of possible base state values. When the provided base is equal (by `===` operator) to one of instant values, the returned value is changed immediately.
In example with modal window, displayed in section below, you need to pass `true` as one of instant values, that's creates the following state flows: [show modal -> mount modal], [hide modal -> wait for 500ms -> unmount modal]
### Minimal Example
```tsx
import useDeferredState from 'use-deferred-state';
export const MyReactComponennts = () => {
const [showModal, setShowModal] = React.useState(false);
const renderModal = useDeferredState(showModal, [true], 500);
...
};
```
### Full example
```tsx
import React from 'react';
import { useDeferredState } from 'use-deferred-state';
export const ExampleApp = () => {
const [showModal, setShowModal] = React.useState(false);
const renderModal = useDeferredState(showModal, [true], 500);
return (
<div>
<button className="toggleButton" onClick={() => setShowModal((prevState) => !prevState)}>
{showModal ? 'hide' : 'show'}
</button>
<p>Modal rendered: {String(renderModal)}</p>
{renderModal && (
<div className={showModal ? 'modal visible' : 'modal'}>
<h2>Hello world</h2>
<p>
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et
dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex
ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat
nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit
anim id est laborum.
</p>
</div>
)}
</div>
);
};
```

## Licence
MIT
| 31.411765 | 226 | 0.694757 | eng_Latn | 0.887445 |
9bbafa32b4d70d57465a0feff2deb5a4c650f549 | 1,838 | md | Markdown | README.md | tinohager/Nager.ArduinoStepperMotor | 96e54bc020a0ba44e3ea4b315c5e2b19c0edd97c | [
"MIT"
] | 1 | 2019-07-21T19:01:39.000Z | 2019-07-21T19:01:39.000Z | README.md | nager/Nager.ArduinoStepperMotor | 96e54bc020a0ba44e3ea4b315c5e2b19c0edd97c | [
"MIT"
] | null | null | null | README.md | nager/Nager.ArduinoStepperMotor | 96e54bc020a0ba44e3ea4b315c5e2b19c0edd97c | [
"MIT"
] | 1 | 2019-09-23T09:57:25.000Z | 2019-09-23T09:57:25.000Z | # Nager.ArduinoStepperMotor
This project was developed to control a stepper motor smoothly and to adjust the speed during operation. Most of the libaries I tested at that time had an acceleration curve but always stopped when changing to another speed and then started again. There are two ways to communicate with the Arduino, one is via serial communication or by using a network module. If you have difficulties and the motor only whistles you should adjust the acceleration curve in the Arduino file.
## Project Skier Simulator
[](https://www.youtube.com/watch?v=VNwVPjmE1V4)<br>
Watch the video on Youtube


### Serial Commands (Baudrate 115200)
Command | Description |
--- | --- |
`enablemotordriver` | Enable the motor driver, the motor has voltage
`disablemotordriver` | Disable the motor driver, the motor has no voltage
`speed` | Values between -255 and 255
`limitenable` | The motor can only move between the limits
`limitdisable` | No limits active
`setlimitleft` | Set the current position as left limit
`setlimitright` | Set the current position as right limit
`step` | Motor move one step
`ramp` | Returns the current ramp
`setramp` | Set a new ramp (setramp=0008000) rampIndex 0 -> 8000
### Required Hardware
Quantity | Product |
--- | --- |
1x | [A4988 Stepper Driver Control Expansion Board](https://amzn.to/2X9j6cO) |
1x | [UEETEK 4 Stück 1M Stepper Motor Cable HX2.54 4-pin to 6-pin](https://amzn.to/31w3uz7) |
1x | [Usongshine Stepper Motor Nema 17 1.5A 17HS4401S](https://amzn.to/2KO4jO8) |
1x | [PChero Mechanic Endstop with LED Indicator](https://amzn.to/2UIAZh4) |
## Test Software
For control via serial communication I have developed a small test application.

| 42.744186 | 476 | 0.757345 | eng_Latn | 0.965845 |
9bbc08e5a6e2734e51296e0dae10da347a4e43cc | 2,250 | md | Markdown | src/en/2018-01/03/04.md | PrJared/sabbath-school-lessons | 94a27f5bcba987a11a698e5e0d4279b81a68bc9a | [
"MIT"
] | 68 | 2016-10-30T23:17:56.000Z | 2022-03-27T11:58:16.000Z | src/en/2018-01/03/04.md | PrJared/sabbath-school-lessons | 94a27f5bcba987a11a698e5e0d4279b81a68bc9a | [
"MIT"
] | 367 | 2016-10-21T03:50:22.000Z | 2022-03-28T23:35:25.000Z | src/en/2018-01/03/04.md | OsArts/Bible-study | cfcefde42e21795e217d192a8b7a703ebb7a6c01 | [
"MIT"
] | 109 | 2016-08-02T14:32:13.000Z | 2022-03-31T10:18:41.000Z | ---
title: Christ, the Redeemer
date: 16/01/2018
---
Debt is not a principle of heaven. But Adam and Eve sinned, and a broken law meant death. Thus, humanity became debtors to divine justice. We were bankrupt, spiritually insolvent from a debt that we could never repay.
God’s love for us set in motion the plan of redemption. Jesus became a “surety” for us (Heb. 7:22). It is Christ’s identity as the Redeemer that reveals the most important transaction ever made. Only the sacrifice of His life could accomplish the required payment of divine justice. Jesus paid the debt of sin that we owed as justice and mercy embraced at the cross. The universe had never seen or witnessed the display of such wealth as was used in the payment for the redemption of humankind (Eph. 5:2).
“By pouring the whole treasury of heaven into this world, by giving us in Christ all heaven, God has purchased the will, the affections, the mind, the soul, of every human being.”—Ellen G. White, Christ’s Object Lessons, p. 326.
`Read each text and list what Christ has saved us from: Col. 1:13; 1 Thess. 1:10; 1 Pet. 1:18; Heb. 2:14, 15; Gal. 3:13; Rev. 1:5.`
The Greek word tetelestai in John 19:30 has been called the most important word ever spoken. It means “It is finished,” and is the last utterance Jesus made on the cross. His final declaration meant that His mission was accomplished and our debt was “paid in full.” He did not utter it as one with no hope but as one who succeeded in the redemption of a lost world. Looking at the cross of redemption reveals a past event with a present effect and a future hope. Jesus gave His life to destroy sin, death, and the works of the devil once and for all. This means that although undeserving, we are redeemed (Eph. 1:7). To glimpse the wonders of salvation is to tread holy ground.
Christ as the Redeemer is the most sublime image of God. His supreme interest is to redeem us. This reveals His perspective toward humanity and especially how He values a relationship with us. With justice satisfied, Christ turns His attention to our response to His sacrifice.
`Think about it: Christ paid the debt, fully and completely, for all the evil you have ever done. What must your response be? (See Job 42:5, 6.)` | 125 | 677 | 0.768 | eng_Latn | 0.999861 |
9bbc0b79e114501ac4bccf0d9858628d6f5f277c | 2,559 | md | Markdown | apps/mjml-app.md | mbunkus/appimage.github.io | 7e4c5c59fcec8dca3feb490dab968fb6dad36358 | [
"MIT"
] | 228 | 2017-08-23T13:35:04.000Z | 2022-03-30T20:57:21.000Z | apps/mjml-app.md | mbunkus/appimage.github.io | 7e4c5c59fcec8dca3feb490dab968fb6dad36358 | [
"MIT"
] | 1,504 | 2017-08-21T15:06:59.000Z | 2022-03-31T20:22:42.000Z | apps/mjml-app.md | mbunkus/appimage.github.io | 7e4c5c59fcec8dca3feb490dab968fb6dad36358 | [
"MIT"
] | 530 | 2017-08-23T13:28:42.000Z | 2022-03-31T20:03:25.000Z | ---
layout: app
permalink: /mjml-app/
description: The desktop app for MJML
license: MIT
icons:
- mjml-app/icons/128x128/mjml-app.png
screenshots:
- mjml-app/screenshot.png
authors:
- name: mjmlio
url: https://github.com/mjmlio
links:
- type: GitHub
url: mjmlio/mjml-app
- type: Download
url: https://github.com/mjmlio/mjml-app/releases
desktop:
Desktop Entry:
Name: MJML
Comment: The desktop app for MJML
Exec: AppRun
Terminal: false
Type: Application
Icon: mjml-app
X-AppImage-Version: 2.9.0
X-AppImage-BuildId: c83c6a60-39d5-11a8-0da3-55726cf66691
Categories: Utility
AppImageHub:
X-AppImage-Signature: no valid OpenPGP data found. the signature could not be verified.
Please remember that the signature file (.sig or .asc) should be the first file
given on the command line.
X-AppImage-Type: 2
X-AppImage-Architecture: x86_64
X-AppImage-Payload-License: MIT
electron:
license: MIT
description: The desktop app for MJML
repository: https://github.com/mjmlio/mjml-app
electronWebpack:
title: true
renderer:
webpackConfig: "./webpack/renderer.js"
dependencies:
balloon-css: "^0.5.0"
classnames: "^2.2.5"
codemirror: "^5.36.0"
electron-debug: "^1.5.0"
electron-json-storage: "^4.0.2"
electron-updater: "^2.21.3"
es6-promisify: "^6.0.0"
fuse.js: "^3.2.0"
immutable: "^3.8.2"
js-beautify: "^1.7.5"
mjml: "^4.0.3"
mjml-migrate: "^4.0.1"
ncp: "^2.0.0"
node-mailjet: "^3.2.1"
react: "^16.2.0"
react-collapse: "^4.0.3"
react-dom: "^16.2.0"
react-hot-loader: "^4.0.0"
react-icons: "^2.2.7"
react-mortal: "^3.2.0"
react-redux: "^5.0.7"
react-router: "^3.0.2"
react-router-redux: "^4.0.8"
react-select: "^1.2.1"
react-split-pane: "^0.1.77"
react-steack: "^1.3.1"
redux: "^3.7.2"
redux-actions: "^2.3.0"
redux-thunk: "^2.2.0"
source-map-support: "^0.5.4"
superagent-promise: "^1.1.0"
trash: "^4.3.0"
resolutions:
webpack-sources: 1.0.1
authors:
- name: Meriadec Pillet
url: https://github.com/meriadec
- name: Cedric Cavrois
url: https://github.com/kmcb777
- name: Nicolas Garnier
url: https://github.com/ngarnier
- name: Giulio M.
url: https://github.com/Mistra
- name: Mateusz Dabrowski
url: https://github.com/MateuszDabrowski
- name: Robbie Antenesse
url: https://github.com/Alamantus
- name: Jon Bickelhaupt
url: https://github.com/jbickelhaupt
main: main.js
---
| 24.84466 | 91 | 0.635014 | kor_Hang | 0.19469 |
9bbd1b188055f2df01db28c654cf1fbf187026e2 | 17,836 | md | Markdown | dsc/resources/authoringResourceClass.md | RyanKing77/powerShell-Docs.sv-se | ef71140b9c24055ea5f9413a1bb348572536b941 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | dsc/resources/authoringResourceClass.md | RyanKing77/powerShell-Docs.sv-se | ef71140b9c24055ea5f9413a1bb348572536b941 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | dsc/resources/authoringResourceClass.md | RyanKing77/powerShell-Docs.sv-se | ef71140b9c24055ea5f9413a1bb348572536b941 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
ms.date: 06/12/2017
keywords: DSC, powershell, konfiguration, installation
title: Skriva en anpassad DSC-resurs med PowerShell-klasser
ms.openlocfilehash: 34356f65bcb83153e7395a16d2a4a5cf2e507332
ms.sourcegitcommit: e7445ba8203da304286c591ff513900ad1c244a4
ms.translationtype: MT
ms.contentlocale: sv-SE
ms.lasthandoff: 04/23/2019
ms.locfileid: "62076726"
---
# <a name="writing-a-custom-dsc-resource-with-powershell-classes"></a>Skriva en anpassad DSC-resurs med PowerShell-klasser
> Gäller för: Windows PowerShell 5.0
Med introduktionen av PowerShell-klasser i Windows PowerShell 5.0, kan du nu ange en DSC-resurs genom att skapa en klass. Klassen definierar både schemat och implementeringen av resurs, så du behöver inte skapa en separat MOF-fil. Mappstrukturen för en MOF-baserade resurs är också enklare eftersom en **DSCResources** mappen är inte nödvändigt.
I en klassbaserade DSC resursen definieras schemat som egenskaper för klassen som kan ändras med attribut som ska ange typen av egenskap... Resursen har implementerats av **Get()**, **Set()**, och **Test()** metoder (motsvarar den **Get-TargetResource**, **Set-TargetResource**, och **Test TargetResource** funktioner i en resurs för skript.
I det här avsnittet skapar vi en enkel resurs med namnet **FileResource** som hanterar en fil i en angiven sökväg.
Mer information om DSC-resurser finns i [skapa anpassade Windows PowerShell Desired State Configuration resurser](authoringResource.md)
>**Obs:** Allmän samlingar stöds inte i MOF-baserade resurser.
## <a name="folder-structure-for-a-class-resource"></a>Mappstruktur för en resurs för klass
Skapa följande mappstruktur för att implementera en anpassad DSC-resurs med en PowerShell-klass. Klassen är definierad i **MyDscResource.psm1** och modulmanifestet har definierats i **MyDscResource.psd1**.
```
$env:ProgramFiles\WindowsPowerShell\Modules (folder)
|- MyDscResource (folder)
MyDscResource.psm1
MyDscResource.psd1
```
## <a name="create-the-class"></a>Skapa klassen
Du kan använda nyckelordet class för att skapa en PowerShell-klass. Om du vill ange att en klass är en DSC-resurs, använda den **DscResource()** attribut. Namnet på klassen är namnet på den DSC-resursen.
```powershell
[DscResource()]
class FileResource {
}
```
### <a name="declare-properties"></a>Deklarera egenskaper
Schema för DSC-resurs har definierats som egenskaper i klassen. Vi deklarera tre egenskaper enligt följande.
```powershell
[DscProperty(Key)]
[string]$Path
[DscProperty(Mandatory)]
[Ensure] $Ensure
[DscProperty(Mandatory)]
[string] $SourcePath
[DscProperty(NotConfigurable)]
[Nullable[datetime]] $CreationTime
```
Observera att egenskaperna ändras av attribut. Enligt attribut är följande:
- **DscProperty(Key)**: Egenskapen krävs. Egenskapen är en nyckel. Värdena för alla egenskaper markerats som nycklar måste kombineras för att unikt identifiera en resursinstans i en konfiguration.
- **DscProperty(Mandatory)**: Egenskapen krävs.
- **DscProperty(NotConfigurable)**: Egenskapen är skrivskyddad. Egenskaper som är markerade med det här attributet kan inte anges av en konfiguration, men fylls med den **Get()** metod när det finns.
- **DscProperty()**: Egenskapen kan konfigureras, men det är inte obligatoriskt.
Den **$Path** och **$SourcePath** egenskaper är båda strängar. Den **$CreationTime** är en [DateTime](/dotnet/api/system.datetime) egenskapen. Den **$Ensure** egenskapen är en uppräkningstyp definieras enligt följande.
```powershell
enum Ensure
{
Absent
Present
}
```
### <a name="implementing-the-methods"></a>Implementera metoderna
Den **Get()**, **Set()**, och **Test()** metoder är detsamma som det **Get-TargetResource**, **Set-TargetResource** , och **Test TargetResource** funktioner i en resurs för skript.
Den här koden innehåller också funktionen CopyFile() en hjälpfunktionen som kopierar filen från **$SourcePath** till **$Path**.
```powershell
<#
This method is equivalent of the Set-TargetResource script function.
It sets the resource to the desired state.
#>
[void] Set()
{
$fileExists = $this.TestFilePath($this.Path)
if ($this.ensure -eq [Ensure]::Present)
{
if(-not $fileExists)
{
$this.CopyFile()
}
}
else
{
if ($fileExists)
{
Write-Verbose -Message "Deleting the file $($this.Path)"
Remove-Item -LiteralPath $this.Path -Force
}
}
}
<#
This method is equivalent of the Test-TargetResource script function.
It should return True or False, showing whether the resource
is in a desired state.
#>
[bool] Test()
{
$present = $this.TestFilePath($this.Path)
if ($this.Ensure -eq [Ensure]::Present)
{
return $present
}
else
{
return -not $present
}
}
<#
This method is equivalent of the Get-TargetResource script function.
The implementation should use the keys to find appropriate resources.
This method returns an instance of this class with the updated key
properties.
#>
[FileResource] Get()
{
$present = $this.TestFilePath($this.Path)
if ($present)
{
$file = Get-ChildItem -LiteralPath $this.Path
$this.CreationTime = $file.CreationTime
$this.Ensure = [Ensure]::Present
}
else
{
$this.CreationTime = $null
$this.Ensure = [Ensure]::Absent
}
return $this
}
<#
Helper method to check if the file exists and it is file
#>
[bool] TestFilePath([string] $location)
{
$present = $true
$item = Get-ChildItem -LiteralPath $location -ErrorAction Ignore
if ($item -eq $null)
{
$present = $false
}
elseif ($item.PSProvider.Name -ne "FileSystem")
{
throw "Path $($location) is not a file path."
}
elseif ($item.PSIsContainer)
{
throw "Path $($location) is a directory path."
}
return $present
}
<#
Helper method to copy file from source to path
#>
[void] CopyFile()
{
if (-not $this.TestFilePath($this.SourcePath))
{
throw "SourcePath $($this.SourcePath) is not found."
}
[System.IO.FileInfo] $destFileInfo = New-Object -TypeName System.IO.FileInfo($this.Path)
if (-not $destFileInfo.Directory.Exists)
{
Write-Verbose -Message "Creating directory $($destFileInfo.Directory.FullName)"
<#
Use CreateDirectory instead of New-Item to avoid code
to handle the non-terminating error
#>
[System.IO.Directory]::CreateDirectory($destFileInfo.Directory.FullName)
}
if (Test-Path -LiteralPath $this.Path -PathType Container)
{
throw "Path $($this.Path) is a directory path"
}
Write-Verbose -Message "Copying $($this.SourcePath) to $($this.Path)"
# DSC engine catches and reports any error that occurs
Copy-Item -LiteralPath $this.SourcePath -Destination $this.Path -Force
}
```
### <a name="the-complete-file"></a>Den fullständiga filen
Fullständig klassfil följer.
```powershell
enum Ensure
{
Absent
Present
}
<#
This resource manages the file in a specific path.
[DscResource()] indicates the class is a DSC resource
#>
[DscResource()]
class FileResource
{
<#
This property is the fully qualified path to the file that is
expected to be present or absent.
The [DscProperty(Key)] attribute indicates the property is a
key and its value uniquely identifies a resource instance.
Defining this attribute also means the property is required
and DSC will ensure a value is set before calling the resource.
A DSC resource must define at least one key property.
#>
[DscProperty(Key)]
[string]$Path
<#
This property indicates if the settings should be present or absent
on the system. For present, the resource ensures the file pointed
to by $Path exists. For absent, it ensures the file point to by
$Path does not exist.
The [DscProperty(Mandatory)] attribute indicates the property is
required and DSC will guarantee it is set.
If Mandatory is not specified or if it is defined as
Mandatory=$false, the value is not guaranteed to be set when DSC
calls the resource. This is appropriate for optional properties.
#>
[DscProperty(Mandatory)]
[Ensure] $Ensure
<#
This property defines the fully qualified path to a file that will
be placed on the system if $Ensure = Present and $Path does not
exist.
NOTE: This property is required because [DscProperty(Mandatory)] is
set.
#>
[DscProperty(Mandatory)]
[string] $SourcePath
<#
This property reports the file's create timestamp.
[DscProperty(NotConfigurable)] attribute indicates the property is
not configurable in DSC configuration. Properties marked this way
are populated by the Get() method to report additional details
about the resource when it is present.
#>
[DscProperty(NotConfigurable)]
[Nullable[datetime]] $CreationTime
<#
This method is equivalent of the Set-TargetResource script function.
It sets the resource to the desired state.
#>
[void] Set()
{
$fileExists = $this.TestFilePath($this.Path)
if ($this.ensure -eq [Ensure]::Present)
{
if (-not $fileExists)
{
$this.CopyFile()
}
}
else
{
if ($fileExists)
{
Write-Verbose -Message "Deleting the file $($this.Path)"
Remove-Item -LiteralPath $this.Path -Force
}
}
}
<#
This method is equivalent of the Test-TargetResource script function.
It should return True or False, showing whether the resource
is in a desired state.
#>
[bool] Test()
{
$present = $this.TestFilePath($this.Path)
if ($this.Ensure -eq [Ensure]::Present)
{
return $present
}
else
{
return -not $present
}
}
<#
This method is equivalent of the Get-TargetResource script function.
The implementation should use the keys to find appropriate resources.
This method returns an instance of this class with the updated key
properties.
#>
[FileResource] Get()
{
$present = $this.TestFilePath($this.Path)
if ($present)
{
$file = Get-ChildItem -LiteralPath $this.Path
$this.CreationTime = $file.CreationTime
$this.Ensure = [Ensure]::Present
}
else
{
$this.CreationTime = $null
$this.Ensure = [Ensure]::Absent
}
return $this
}
<#
Helper method to check if the file exists and it is file
#>
[bool] TestFilePath([string] $location)
{
$present = $true
$item = Get-ChildItem -LiteralPath $location -ea Ignore
if ($item -eq $null)
{
$present = $false
}
elseif ($item.PSProvider.Name -ne "FileSystem")
{
throw "Path $($location) is not a file path."
}
elseif ($item.PSIsContainer)
{
throw "Path $($location) is a directory path."
}
return $present
}
<#
Helper method to copy file from source to path
#>
[void] CopyFile()
{
if (-not $this.TestFilePath($this.SourcePath))
{
throw "SourcePath $($this.SourcePath) is not found."
}
[System.IO.FileInfo] $destFileInfo = new-object System.IO.FileInfo($this.Path)
if (-not $destFileInfo.Directory.Exists)
{
Write-Verbose -Message "Creating directory $($destFileInfo.Directory.FullName)"
<#
Use CreateDirectory instead of New-Item to avoid code
to handle the non-terminating error
#>
[System.IO.Directory]::CreateDirectory($destFileInfo.Directory.FullName)
}
if (Test-Path -LiteralPath $this.Path -PathType Container)
{
throw "Path $($this.Path) is a directory path"
}
Write-Verbose -Message "Copying $($this.SourcePath) to $($this.Path)"
# DSC engine catches and reports any error that occurs
Copy-Item -LiteralPath $this.SourcePath -Destination $this.Path -Force
}
} # This module defines a class for a DSC "FileResource" provider.
```
## <a name="create-a-manifest"></a>Skapa ett manifest
Om du vill göra en MOF-baserade resurs ska vara tillgängliga för DSC-motorn måste du inkludera en **DscResourcesToExport** instruktionen i manifestfilen som instruerar modulen att exportera resursen. Vår manifest ser ut så här:
```powershell
@{
# Script module or binary module file associated with this manifest.
RootModule = 'MyDscResource.psm1'
DscResourcesToExport = 'FileResource'
# Version number of this module.
ModuleVersion = '1.0'
# ID used to uniquely identify this module
GUID = '81624038-5e71-40f8-8905-b1a87afe22d7'
# Author of this module
Author = 'Microsoft Corporation'
# Company or vendor of this module
CompanyName = 'Microsoft Corporation'
# Copyright statement for this module
Copyright = '(c) 2014 Microsoft. All rights reserved.'
# Description of the functionality provided by this module
# Description = ''
# Minimum version of the Windows PowerShell engine required by this module
PowerShellVersion = '5.0'
# Name of the Windows PowerShell host required by this module
# PowerShellHostName = ''
}
```
## <a name="test-the-resource"></a>Testa resursen
När du har sparat den klass och manifestfiler i mappstrukturen enligt beskrivningen ovan, kan du skapa en konfiguration som använder den nya resursen. Information om hur du kör en DSC-konfiguration finns i [tillämpa konfigurationer](../pull-server/enactingConfigurations.md). Följande konfiguration ska kontrollera om filen vid `c:\test\test.txt` finns och, om inte, kopierar du filen från `c:\test.txt` (du bör skapa `c:\test.txt` innan du kör konfigurationen).
```powershell
Configuration Test
{
Import-DSCResource -module MyDscResource
FileResource file
{
Path = "C:\test\test.txt"
SourcePath = "c:\test.txt"
Ensure = "Present"
}
}
Test
Start-DscConfiguration -Wait -Force Test
```
## <a name="supporting-psdscrunascredential"></a>Stöd för PsDscRunAsCredential
>**Obs:** **PsDscRunAsCredential** stöds i PowerShell 5.0 och senare.
Den **PsDscRunAsCredential** egenskapen kan användas i [DSC-konfigurationer](../configurations/configurations.md) resource förhindra om du vill ange att resursen ska köras under en angiven uppsättning autentiseringsuppgifter.
Mer information finns i [kör DSC med autentiseringsuppgifterna för användaren](../configurations/runAsUser.md).
### <a name="require-or-disallow-psdscrunascredential-for-your-resource"></a>Aktivera eller inaktivera PsDscRunAsCredential för din resurs
Den **DscResource()** attributet tar en valfri parameter **RunAsCredential**.
Den här parametern antar ett av tre värden:
- `Optional` **PsDscRunAsCredential** är valfritt för konfigurationer som anropar den här resursen. Detta är standardvärdet.
- `Mandatory` **PsDscRunAsCredential** måste användas för alla konfigurationer som anropar den här resursen.
- `NotSupported` Konfigurationer som anropar den här resursen kan inte använda **PsDscRunAsCredential**.
- `Default` Samma som `Optional`.
Till exempel använda följande attribut för att ange att din anpassade resursen inte stöder användning av **PsDscRunAsCredential**:
```powershell
[DscResource(RunAsCredential=NotSupported)]
class FileResource {
}
```
### <a name="declaring-multiple-class-resources-in-a-module"></a>Deklarerar flera klass resurser i en modul
En modul kan definiera flera klassbaserade DSC-resurser. Du kan skapa mappstrukturen på följande sätt:
1. Definiera den första resursen i det ”<ModuleName>.psm1” fil- och efterföljande resurser under den **DSCResources** mapp.
```
$env:ProgramFiles\WindowsPowerShell\Modules (folder)
|- MyDscResource (folder)
|- MyDscResource.psm1
MyDscResource.psd1
|- DSCResources
|- SecondResource.psm1
```
2. Definiera alla resurser under den **DSCResources** mapp.
```
$env:ProgramFiles\WindowsPowerShell\Modules (folder)
|- MyDscResource (folder)
|- MyDscResource.psm1
MyDscResource.psd1
|- DSCResources
|- FirstResource.psm1
SecondResource.psm1
```
> [!NOTE]
> I exemplen ovan lägger du till PSM1 filer under den **DSCResources** till den **NestedModules** nyckeln i PSD1-fil.
### <a name="access-the-user-context"></a>Komma åt användarkontexten
Du kan använda automatiska variabeln för att komma åt användarkontext från inom en anpassad resurs `$global:PsDscContext`.
Följande kod skulle till exempel skriva användarkontext där resursen körs till en dataström med utförliga utdata:
```powershell
if (PsDscContext.RunAsUser) {
Write-Verbose "User: $global:PsDscContext.RunAsUser";
}
```
## <a name="see-also"></a>Se även
[Skapa anpassade Windows PowerShell Desired State Configuration-resurser](authoringResource.md)
| 32.786765 | 462 | 0.662312 | swe_Latn | 0.343419 |
9bbdc552680ba8467eb9c150df77a1ac6d94143a | 689 | md | Markdown | 2020/CVE-2020-18756.md | justinforbes/cve | 375c65312f55c34fc1a4858381315fe9431b0f16 | [
"MIT"
] | 2,340 | 2022-02-10T21:04:40.000Z | 2022-03-31T14:42:58.000Z | 2020/CVE-2020-18756.md | justinforbes/cve | 375c65312f55c34fc1a4858381315fe9431b0f16 | [
"MIT"
] | 19 | 2022-02-11T16:06:53.000Z | 2022-03-11T10:44:27.000Z | 2020/CVE-2020-18756.md | justinforbes/cve | 375c65312f55c34fc1a4858381315fe9431b0f16 | [
"MIT"
] | 280 | 2022-02-10T19:58:58.000Z | 2022-03-26T11:13:05.000Z | ### [CVE-2020-18756](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-18756)



### Description
An arbitrary memory access vulnerability in the EPA protocol of Dut Computer Control Engineering Co.'s PLC MAC1100 allows attackers to read the contents of any variable area.
### POC
#### Reference
- https://github.com/Ni9htMar3/vulnerability/blob/master/PLC/DCCE/DCCE%20MAC1100%20PLC_read.md
#### Github
No PoCs found on GitHub currently.
| 38.277778 | 174 | 0.759071 | eng_Latn | 0.232845 |
9bbede61ad7f56d528e38228cda96271ea9eee42 | 9,844 | md | Markdown | README.md | italybythenumbers/data.italybythenumbers | 4a6abc5f82ba0f3be47de4ab072d32572c26029f | [
"MIT"
] | null | null | null | README.md | italybythenumbers/data.italybythenumbers | 4a6abc5f82ba0f3be47de4ab072d32572c26029f | [
"MIT"
] | null | null | null | README.md | italybythenumbers/data.italybythenumbers | 4a6abc5f82ba0f3be47de4ab072d32572c26029f | [
"MIT"
] | null | null | null | ## Generazione datasette
```
csvs-to-sqlite \
./csv/bilancio-dello-stato \
./sqlite/bilancio-dello-stato.db \
-s ';' \
--replace-tables
```
## Esecuzione datasette
```
docker run -p 8001:8001 -v `pwd`:/mnt \
datasetteproject/datasette \
datasette -p 8001 -h 0.0.0.0 \
--config allow_download:off \
/mnt/sqlite/bilancio-dello-stato.db \
--metadata /mnt/metadata.json \
--template-dir /mnt/templates/ \
--static static:/mnt/static
```
## Bilancio dello stato
Tutti i dati sono originati dal [Ministero dell'Economia e Finanze](http://www.mef.gov.it/) ed hanno licenza [CC-BY](http://creativecommons.org/licenses/by/4.0/)
### Serie Storiche
#### Disegno Legge di Bilancio Presentato - Serie storica - Spese per Amministrazione Missione Programma Macroaggregato
Prodotto contenente la serie storica dei dati della spesa relativi al Disegno Legge di Bilancio Presentato aggregati per l'esercizio finanziario di riferimento
**sorgente**: https://bdap-opendata.mef.gov.it/content/disegno-legge-di-bilancio-presentato-serie-storica-spese-aggregato-amministrazione-missione
**CSV**: [`csv/bilancio-dello-stato/serie/dlb.csv`](csv/bilancio-dello-stato/serie/dlb.csv)
#### Legge di Bilancio Pubblicata - Serie storica - Spese per Amministrazione Missione Programma Macroaggregato
Prodotto contenente la serie storica dei dati della spesa relativi alla Legge di Bilancio aggregati per Amministrazione Missione Programma Macroaggregato
**sorgente**: https://bdap-opendata.mef.gov.it/content/legge-di-bilancio-cruscotto-spese-amministrazione-missione-programma-macroaggregato
**CSV**: [`csv/bilancio-dello-stato/serie/lbp.csv`](csv/bilancio-dello-stato/serie/lbp.csv)
#### Rendiconto Pubblicato - Serie storica - Saldi
Dati di Saldi relativi al Rendiconto Pubblicato per l'esercizio finanziario di riferimento
**sorgente**: https://bdap-opendata.mef.gov.it/content/rendiconto-pubblicato-serie-storica-saldiold
**CSV**: [`csv/bilancio-dello-stato/serie/rend_saldi.csv`](csv/bilancio-dello-stato/serie/rend_saldi.csv)
### Bilancio 2019
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/content/2019-disegno-legge-di-bilancio-presentato-elaborabile-spese-capitolo
**CSV**: [`csv/bilancio-dello-stato/2019/dlb.csv`](csv/bilancio-dello-stato/2019/dlb.csv)
### Bilancio 2018
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2018
**CSV**: [`csv/bilancio-dello-stato/2018/dlb.csv`](csv/bilancio-dello-stato/2018/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2018
**CSV**: [`csv/bilancio-dello-stato/2018/lbnv1.csv`](csv/bilancio-dello-stato/2018/lbnv1.csv)
#### Seconda Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv2_spe_elb_cap_01_2018
**CSV**: [`csv/bilancio-dello-stato/2018/lbnv2.csv`](csv/bilancio-dello-stato/2018/lbnv2.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2018
**CSV**: [`csv/bilancio-dello-stato/2018/lbp.csv`](csv/bilancio-dello-stato/2018/lbp.csv)
### Bilancio 2017
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2017
**CSV**: [`csv/bilancio-dello-stato/2017/dlb.csv`](csv/bilancio-dello-stato/2017/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2017
**CSV**: [`csv/bilancio-dello-stato/2017/lbnv1.csv`](csv/bilancio-dello-stato/2017/lbnv1.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2017
**CSV**: [`csv/bilancio-dello-stato/2017/lbp.csv`](csv/bilancio-dello-stato/2017/lbp.csv)
#### Rendiconto Pubblicato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/content/2017-rendiconto-pubblicato-elaborabile-spese-capitolo
**CSV**: [`csv/bilancio-dello-stato/2017/rend.csv`](csv/bilancio-dello-stato/2017/rend.csv)
### Bilancio 2016
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2016
**CSV**: [`csv/bilancio-dello-stato/2016/dlb.csv`](csv/bilancio-dello-stato/2016/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2016
**CSV**: [`csv/bilancio-dello-stato/2016/lbnv1.csv`](csv/bilancio-dello-stato/2016/lbnv1.csv)
#### Seconda Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv2_spe_elb_cap_01_2016
**CSV**: [`csv/bilancio-dello-stato/2016/lbnv2.csv`](csv/bilancio-dello-stato/2016/lbnv2.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2016
**CSV**: [`csv/bilancio-dello-stato/2016/lbp.csv`](csv/bilancio-dello-stato/2016/lbp.csv)
### Bilancio 2015
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2015
**CSV**: [`csv/bilancio-dello-stato/2015/dlb.csv`](csv/bilancio-dello-stato/2015/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2015
**CSV**: [`csv/bilancio-dello-stato/2015/lbnv1.csv`](csv/bilancio-dello-stato/2015/lbnv1.csv)
#### Seconda Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv2_spe_elb_cap_01_2015
**CSV**: [`csv/bilancio-dello-stato/2015/lbnv2.csv`](csv/bilancio-dello-stato/2015/lbnv2.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2015
**CSV**: [`csv/bilancio-dello-stato/2015/lbp.csv`](csv/bilancio-dello-stato/2015/lbp.csv)
### Bilancio 2014
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2014
**CSV**: [`csv/bilancio-dello-stato/2014/dlb.csv`](csv/bilancio-dello-stato/2014/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2014
**CSV**: [`csv/bilancio-dello-stato/2014/lbnv1.csv`](csv/bilancio-dello-stato/2014/lbnv1.csv)
#### Seconda Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv2_spe_elb_cap_01_2014
**CSV**: [`csv/bilancio-dello-stato/2014/lbnv2.csv`](csv/bilancio-dello-stato/2014/lbnv2.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2014
**CSV**: [`csv/bilancio-dello-stato/2014/lbp.csv`](csv/bilancio-dello-stato/2014/lbp.csv)
### Bilancio 2013
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2013
**CSV**: [`csv/bilancio-dello-stato/2013/dlb.csv`](csv/bilancio-dello-stato/2013/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2013
**CSV**: [`csv/bilancio-dello-stato/2013/lbnv1.csv`](csv/bilancio-dello-stato/2013/lbnv1.csv)
#### Seconda Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv2_spe_elb_cap_01_2013
**CSV**: [`csv/bilancio-dello-stato/2013/lbnv2.csv`](csv/bilancio-dello-stato/2013/lbnv2.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2013
**CSV**: [`csv/bilancio-dello-stato/2013/lbp.csv`](csv/bilancio-dello-stato/2013/lbp.csv)
### Bilancio 2012
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2012
**CSV**: [`csv/bilancio-dello-stato/2012/dlb.csv`](csv/bilancio-dello-stato/2017/2012.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2012
**CSV**: [`csv/bilancio-dello-stato/2012/lbnv1.csv`](csv/bilancio-dello-stato/2012/lbnv1.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2012
**CSV**: [`csv/bilancio-dello-stato/2012/lbp.csv`](csv/bilancio-dello-stato/2012/lbp.csv)
### Bilancio 2011
#### Disegno Legge di Bilancio Presentato Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_dlb_spe_elb_cap_01_2011
**CSV**: [`csv/bilancio-dello-stato/2011/dlb.csv`](csv/bilancio-dello-stato/2011/dlb.csv)
#### Prima Nota di Variazione Approvata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_nv1_spe_elb_cap_01_2011
**CSV**: [`csv/bilancio-dello-stato/2011/lbnv1.csv`](csv/bilancio-dello-stato/2011/lbnv1.csv)
#### Legge di Bilancio Pubblicata Elaborabile Spese Capitolo
**sorgente**: https://bdap-opendata.mef.gov.it/opendata/spd_lbf_spe_elb_cap_01_2011
**CSV**: [`csv/bilancio-dello-stato/2011/lbp.csv`](csv/bilancio-dello-stato/2011/lbp.csv)
| 44.143498 | 161 | 0.766863 | ita_Latn | 0.393395 |
9bbf80efd52364801006b289d0c6268a29d35dc9 | 8,712 | md | Markdown | _posts/2014-05-16-virtual-ap-sta-mode.md | DongminWu/blog_backup | 1d6af165827eea4b45c938a6410c8a380886b14d | [
"MIT"
] | null | null | null | _posts/2014-05-16-virtual-ap-sta-mode.md | DongminWu/blog_backup | 1d6af165827eea4b45c938a6410c8a380886b14d | [
"MIT"
] | null | null | null | _posts/2014-05-16-virtual-ap-sta-mode.md | DongminWu/blog_backup | 1d6af165827eea4b45c938a6410c8a380886b14d | [
"MIT"
] | null | null | null | ---
layout: post
title: 虚拟AP和基础网模式
date: 2014-05-16
categories: Openwrt
---
今天的又在做毕设。
昨天把网页设置的部分完了一点。
今天想添加新功能,虚拟AP,AP模式和基础网模式互换
## Part.1 虚拟AP
就是用一个路由器广播多个ssid
这样的可以完成不同用户的独立控制。
比如呢。我给家里的wifi分隔一下,一个是`Myself`,我自己用的。另一个是`Guest`,用来给访客用
给自己的流量自然要多分一点,给访客的就让他们能够看网页就好啦~~~
这个功能在`/etc/config/wireless`中有设置
先看wireless里面的config信息
```
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11ng'
option path 'platform/ar933x_wmac'
list ht_capab 'SHORT-GI-20'
list ht_capab 'SHORT-GI-40'
list ht_capab 'RX-STBC1'
list ht_capab 'DSSS_CCK-40'
option disabled '0'
option channel 'auto'
option htmode 'HT40+'
option country 'CN'
option noscan '1'
config wifi-iface
option device 'radio0'
option network 'lan'
option mode 'ap'
option encryption 'none'
option ssid 'pipi1net'
config wifi-iface
option device 'radio0'
option network 'lan'
option mode 'ap'
option encryption 'none'
option ssid 'pipi2net'
```
参考资料在这里:[Wireless configuration](http://wiki.openwrt.org/doc/uci/wireless) | [利用nodogsplash 打造多节点超强无线广告机 ](http://blog.sina.com.cn/s/blog_6838386a0101d7gh.html)
我这里就是建立了两个不同的ap
一个是`pipi1net`,另一个是`pipi2net`
用uci实现
#### 添加一个虚拟ap
```
uci add wireless wifi-iface
uci set wireless.@wifi-iface[1].device=radio0
uci set wireless.@wifi-iface[1].network=lan
uci set wireless.@wifi-iface[1].mode=ap
uci set wireless.@wifi-iface[1].encryption=none
uci set wireless.@wifi-iface[1].ssid=pipi2net
uci commit
```
#### 删除虚拟ap
```
uci delete wireless.@wifi-iface[1]
uci commit
```
记得如果要立即看到效果的话要添加`/etc/init.d/network restart`啊啊啊
## Part.2 基础网和AP模式互换
基础网模式就是wifi-client,就是像手机一样用wifi连接在某个ap上作为从机
AP模式是wifi-AP
主要参考资料:[Routed AP](http://wiki.openwrt.org/doc/recipes/routedap) | [Routed Client](http://wiki.openwrt.org/doc/recipes/routedclient)
我的这个模块拿到手里面的时候就是默认的AP模式
改为基础网(sta)模式要修改的地方
(修改第一个wifi ap)
```
uci del wireless.@wifi-device[0].disabled
uci del wireless.@wifi-iface[0].network
uci set wireless.@wifi-iface[0].mode=sta
uci commit wireless
wifi
```
**PS:wifi命令相当于原来的/etc/init.d/network restart**
然后就开始扫描空间中的wifi信号
iwlist scan
官网资料上面说如果出现了Devic Busy或者资源被占用之类的事情
可以执行
killall -9 wpa_supplicant
iwlist scan
我在图书馆的扫描结果如下:
```
wlan0 Scan completed :
Cell 01 - Address: 00:1F:64:EB:4F:78
Channel:1
Frequency:2.412 GHz (Channel 1)
Quality=29/70 Signal level=-81 dBm
Encryption key:off
ESSID:"Cert_Download"
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s
9 Mb/s; 12 Mb/s; 18 Mb/s
Bit Rates:24 Mb/s; 36 Mb/s; 48 Mb/s; 54 Mb/s
Mode:Master
Extra:tsf=00000011157e1d06
Extra: Last beacon: 740ms ago
IE: Unknown: 000D436572745F446F776E6C6F6164
IE: Unknown: 010882848B960C121824
IE: Unknown: 030101
IE: Unknown: 0706434E20010D14
IE: Unknown: 2A0100
IE: Unknown: 32043048606C
IE: Unknown: 2D1AAD0103FFFF000000000000000000000000000000040
IE: Unknown: 331AAD0103FFFF000000000000000000000000000000040
IE: Unknown: 3D160100170000000000000000000000000000000000000
IE: Unknown: 34160100170000000000000000000000000000000000000
IE: Unknown: 4A0E14000A002C01C800140005001900
IE: Unknown: 7F0101
IE: Unknown: DD180050F2020101060003A4000027A4000042435E00623
IE: Unknown: DD0900037F01010000FF7F
Cell 02 - Address: 00:1F:64:EC:4F:78
Channel:1
Frequency:2.412 GHz (Channel 1)
Quality=31/70 Signal level=-79 dBm
Encryption key:off
ESSID:"BUPT-3"
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s
9 Mb/s; 12 Mb/s; 18 Mb/s
Bit Rates:24 Mb/s; 36 Mb/s; 48 Mb/s; 54 Mb/s
Mode:Master
Extra:tsf=4b000011157e26e8
Extra: Last beacon: 710ms ago
IE: Unknown: 0006425550542D33
IE: Unknown: 010882848B960C121824
IE: Unknown: 030101
IE: Unknown: 0706434E20010D14
IE: Unknown: 2A0100
IE: Unknown: 32043048606C
IE: Unknown: 2D1AAD0103FFFF000000000000000000000000000000040
IE: Unknown: 331AAD0103FFFF000000000000000000000000000000040
IE: Unknown: 3D160100170000000000000000000000000000000000000
IE: Unknown: 34160100170000000000000000000000000000000000000
IE: Unknown: 4A0E14000A002C01C800140005001900
IE: Unknown: 7F0101
IE: Unknown: DD180050F2020101060003A4000027A4000042435E00623
IE: Unknown: DD0900037F01010000FF7F
Cell 03 - Address: 00:1F:64:ED:4F:78
Channel:1
Frequency:2.412 GHz (Channel 1)
Quality=30/70 Signal level=-80 dBm
Encryption key:on
ESSID:"eID_WAPI"
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s
9 Mb/s; 12 Mb/s; 18 Mb/s
Bit Rates:24 Mb/s; 36 Mb/s; 48 Mb/s; 54 Mb/s
Mode:Master
Extra:tsf=32000011157e379a
Extra: Last beacon: 2000ms ago
IE: Unknown: 00086549445F57415049
IE: Unknown: 010882848B960C121824
IE: Unknown: 030101
IE: Unknown: 0706434E20010D14
IE: Unknown: 2A0100
IE: Unknown: 44140100010000147201010000147201001472010000
IE: Unknown: 32043048606C
IE: Unknown: 2D1AAD0103FFFF000000000000000000000000000000040
IE: Unknown: 331AAD0103FFFF000000000000000000000000000000040
IE: Unknown: 3D160100170000000000000000000000000000000000000
IE: Unknown: 34160100170000000000000000000000000000000000000
IE: Unknown: 4A0E14000A002C01C800140005001900
IE: Unknown: 7F0101
IE: Unknown: DD180050F2020101060003A4000027A4000042435E00623
IE: Unknown: DD0900037F01010000FF7F
Cell 04 - Address: 3E:4B:D6:A1:34:28
Channel:6
Frequency:2.437 GHz (Channel 6)
Quality=26/70 Signal level=-84 dBm
Encryption key:on
ESSID:"AWIN-JPMT21CIJMJ"
Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s
9 Mb/s; 12 Mb/s; 18 Mb/s
Bit Rates:24 Mb/s; 36 Mb/s; 48 Mb/s; 54 Mb/s
Mode:Master
Extra:tsf=00000002ea7a06c0
Extra: Last beacon: 410ms ago
.........................实在太长了就截取到这里吧
```
于是呢我们就能找到想要加入的wfi网络的SSID和加密协议了~
根据这个信息使用UCI命令再次修改`/etc/config/wireless`
尝试连接至**BUPT-3**
```
uci set wireless.@wifi-iface[0].ssid=BUPT-3
uci set wireless.@wifi-iface[0].network=wan
uci commit
```
设置之后的`/etc/cofig/wireless`文件`wifi-iface[0]`部分内容如下
```
config wifi-iface
option device 'radio0'
option encryption 'none'
option mode 'sta'
option network 'wan'
option ssid 'BUPT-3'
```
执行`wifi`命令之后出现一下信息
```
[ 1275.460000] wlan0: authenticate with 00:1f:64:ec:4f:78
[ 1275.470000] wlan0: send auth to 00:1f:64:ec:4f:78 (try 1/3)
[ 1275.530000] wlan0: authenticated
[ 1275.540000] wlan0: associate with 00:1f:64:ec:4f:78 (try 1/3)
[ 1275.550000] wlan0: RX AssocResp from 00:1f:64:ec:4f:78 (capab=0x421 status=0
aid=9)
[ 1275.560000] wlan0: associated
[ 1275.560000] IPv6: ADDRCONF(NETDEV_CHANGE): wlan0: link becomes ready
```
成功变为基础网模式
再次切换为AP模式只需恢复原有config即可
```
uci set wireless.@wifi-iface[0].network=lan
uci set wireless.@wifi-iface[0].ssid=pipinet
uci set wireless.@wifi-iface[0].mode=ap
uci commit
```
| 32.147601 | 161 | 0.569789 | yue_Hant | 0.359335 |
9bc0467e30f4865b758d397e3f643d98e59fffb5 | 2,133 | md | Markdown | CONTRIBUTING.md | andrew-demb/peachpie | b9c9321f1016c59521c84af66832d806e32b8b4a | [
"Apache-2.0"
] | 1,576 | 2017-07-05T14:51:20.000Z | 2022-03-30T13:27:42.000Z | CONTRIBUTING.md | andrew-demb/peachpie | b9c9321f1016c59521c84af66832d806e32b8b4a | [
"Apache-2.0"
] | 884 | 2017-08-12T04:16:13.000Z | 2022-03-23T10:57:25.000Z | CONTRIBUTING.md | andrew-demb/peachpie | b9c9321f1016c59521c84af66832d806e32b8b4a | [
"Apache-2.0"
] | 182 | 2017-07-15T14:54:37.000Z | 2022-03-10T05:57:13.000Z | # Contribution Guidelines
## Prerequisites
By contributing to the Peachpie Compiler Platform, you state that:
* The contribution is your own original work and does not infringe any copyrights.
* Your work is not owned by your employer (or you have been given copyright assignment in writing) and you are therefore allowed to assign the copyrights to your contribution to Peachpie.
* You [license](https://github.com/iolevel/peachpie/blob/master/LICENSE.txt) the contribution under the terms applied to the rest of the Peachpie project.
## Coding Standards
### Code style
For the Peachpie project (excluding files written in PHP), the standard .NET coding guidelines apply.
Please refer to the [Framework Design Guidelines](https://msdn.microsoft.com/en-us/library/ms229042%28v=vs.110%29.aspx) for more information.
### Unit tests
Please run all unit tests prior to creating a PR. All pull requests that did not pass the automated CI testing will be rejected.
## Contributing to Peachpie
Before you make a commit, please ensure that it meets the following requirements:
* Your commit is a small logical unit that represents a reasonable change.
* You should include new or changed tests relevant to the changes you are making.
* Please avoid unnecessary whitespace. Check for whitespace with `git diff --check` and `git diff --cached --check` before commiting.
* The code included in your commit should compile without errors or warnings.
* All tests should be passing.
* A reasonable amount of comments is included in order for the code to be transparent for all users.
### Submit your PR
Once you believe your commit meets the above requirements, feel free to submit your pull request. Kindly ensure you have met the following guidelines:
* In the pull request, summarize the contents of your commit or issues that you are resolving.
* Once the pull request is in, please do not delete the branch or close the pull request (unless something is wrong with it).
* We will respond to your pull request in a reasonable timeframe. Should there be a reason for us to reject your PR, we will let you know in the comments.
| 59.25 | 187 | 0.784341 | eng_Latn | 0.999718 |
9bc0e50adc6f129b1bed025b714dfbbc2ff15675 | 4,770 | md | Markdown | repos/debian/remote/oldoldstable-20211011-slim.md | Michaelzp1/repo-info | 542b4a638ccca7bd3368d3131b0a9a71d2b8185d | [
"Apache-2.0"
] | 400 | 2016-08-11T10:14:00.000Z | 2022-03-24T09:41:03.000Z | repos/debian/remote/oldoldstable-20211011-slim.md | Michaelzp1/repo-info | 542b4a638ccca7bd3368d3131b0a9a71d2b8185d | [
"Apache-2.0"
] | 47 | 2016-08-18T22:30:36.000Z | 2022-02-24T01:27:22.000Z | repos/debian/remote/oldoldstable-20211011-slim.md | Michaelzp1/repo-info | 542b4a638ccca7bd3368d3131b0a9a71d2b8185d | [
"Apache-2.0"
] | 319 | 2016-08-24T06:35:11.000Z | 2022-03-22T17:07:28.000Z | ## `debian:oldoldstable-20211011-slim`
```console
$ docker pull debian@sha256:26e0a9d420a9e06ab03cc7a69743fbfd888fc2af159f1837a0e94729d9d329e2
```
- Manifest MIME: `application/vnd.docker.distribution.manifest.list.v2+json`
- Platforms: 5
- linux; amd64
- linux; arm variant v5
- linux; arm variant v7
- linux; arm64 variant v8
- linux; 386
### `debian:oldoldstable-20211011-slim` - linux; amd64
```console
$ docker pull debian@sha256:5d1e4df796f8ee15cbfd5e46932af78c0d351c6053e44c17c0c9f95acdc67f68
```
- Docker Version: 20.10.7
- Manifest MIME: `application/vnd.docker.distribution.manifest.v2+json`
- Total Size: **22.5 MB (22527518 bytes)**
(compressed transfer size, not on-disk size)
- Image ID: `sha256:d852065264ac8a67bdb251ec797a82b7c9fac214c893ee302aced55997ef22ce`
- Default Command: `["bash"]`
```dockerfile
# Tue, 12 Oct 2021 01:21:26 GMT
ADD file:6f0d65d34e99acc0a838582bb0c52c8b12eadb39798d231caf702a8f3a9f4de2 in /
# Tue, 12 Oct 2021 01:21:26 GMT
CMD ["bash"]
```
- Layers:
- `sha256:1599ff3b20b129431eddbefc2dc08a6a0aa8ef68faf34d44eea8c9cfdf5eb921`
Last Modified: Tue, 12 Oct 2021 01:27:30 GMT
Size: 22.5 MB (22527518 bytes)
MIME: application/vnd.docker.image.rootfs.diff.tar.gzip
### `debian:oldoldstable-20211011-slim` - linux; arm variant v5
```console
$ docker pull debian@sha256:1c1201bdfd440e4c7f9ae2c594825f3f62e4f4485eae81b122f22424d745006f
```
- Docker Version: 20.10.7
- Manifest MIME: `application/vnd.docker.distribution.manifest.v2+json`
- Total Size: **21.2 MB (21204338 bytes)**
(compressed transfer size, not on-disk size)
- Image ID: `sha256:9138868e8021053dbf3833b593e719e5132d5539ea38441c9c7fabad87a2bbc3`
- Default Command: `["bash"]`
```dockerfile
# Tue, 12 Oct 2021 00:52:30 GMT
ADD file:287e595e03955546f25eb897aa7553ee626ae6c6b64b8164d5d3b42297641edc in /
# Tue, 12 Oct 2021 00:52:31 GMT
CMD ["bash"]
```
- Layers:
- `sha256:cee58a8ba33bca4d50453537ed50c73bed23501940fc2a62da2ac84e166732e7`
Last Modified: Tue, 12 Oct 2021 01:09:04 GMT
Size: 21.2 MB (21204338 bytes)
MIME: application/vnd.docker.image.rootfs.diff.tar.gzip
### `debian:oldoldstable-20211011-slim` - linux; arm variant v7
```console
$ docker pull debian@sha256:cba44244e91c243cd754845d3b910882c83f8c6324c8d4c4a3505840f5f8145d
```
- Docker Version: 20.10.7
- Manifest MIME: `application/vnd.docker.distribution.manifest.v2+json`
- Total Size: **19.3 MB (19316443 bytes)**
(compressed transfer size, not on-disk size)
- Image ID: `sha256:825f907336d8205e7b0130eabb99133cde40dbaf9ca278d973318836dda78f46`
- Default Command: `["bash"]`
```dockerfile
# Tue, 12 Oct 2021 01:30:44 GMT
ADD file:dfe14f5069e960939daf937d576bddf08c2dd9386730c01bc365ac610b035f71 in /
# Tue, 12 Oct 2021 01:30:45 GMT
CMD ["bash"]
```
- Layers:
- `sha256:dc641641f7cb36d80035d98c2c9fe584419cdca7cf5ded32111b25f4945753fe`
Last Modified: Tue, 12 Oct 2021 01:47:18 GMT
Size: 19.3 MB (19316443 bytes)
MIME: application/vnd.docker.image.rootfs.diff.tar.gzip
### `debian:oldoldstable-20211011-slim` - linux; arm64 variant v8
```console
$ docker pull debian@sha256:07f91a5d79ab9d7d492307d76b77db6e241d5f830bd0d6323f7a03cf2add0608
```
- Docker Version: 20.10.7
- Manifest MIME: `application/vnd.docker.distribution.manifest.v2+json`
- Total Size: **20.4 MB (20389428 bytes)**
(compressed transfer size, not on-disk size)
- Image ID: `sha256:e9e8adb4c56e2f66a90d67602595080738aeb7f949a6ed4881f2fd101fc69e5e`
- Default Command: `["bash"]`
```dockerfile
# Tue, 12 Oct 2021 01:42:04 GMT
ADD file:5d456d87f1a04e598f5e60aff2dfe22e2c5e218cc255dd5383e4a29659c30471 in /
# Tue, 12 Oct 2021 01:42:05 GMT
CMD ["bash"]
```
- Layers:
- `sha256:51a573003c28d47d7b57a5fef8f423cf0a6d3c7f1f7fd8b538b4ae893fa860d4`
Last Modified: Tue, 12 Oct 2021 01:49:52 GMT
Size: 20.4 MB (20389428 bytes)
MIME: application/vnd.docker.image.rootfs.diff.tar.gzip
### `debian:oldoldstable-20211011-slim` - linux; 386
```console
$ docker pull debian@sha256:4f4f5898707a9955c71cb072fa46effc42556fb4829ed1f2ff71758df4d8213e
```
- Docker Version: 20.10.7
- Manifest MIME: `application/vnd.docker.distribution.manifest.v2+json`
- Total Size: **23.2 MB (23156644 bytes)**
(compressed transfer size, not on-disk size)
- Image ID: `sha256:e2078108904ce9e8978355229f5e5c709403d783d7cf4c34adbc74354722e644`
- Default Command: `["bash"]`
```dockerfile
# Tue, 12 Oct 2021 01:40:45 GMT
ADD file:0c0934e7f8d30895fa74e47b73ad9064299cbf54de898ee430dbcde8b3a2d130 in /
# Tue, 12 Oct 2021 01:40:45 GMT
CMD ["bash"]
```
- Layers:
- `sha256:0ff128fa75c485cac31b556b81d71c790608f3404c66504c40ac9940109223bb`
Last Modified: Tue, 12 Oct 2021 01:49:26 GMT
Size: 23.2 MB (23156644 bytes)
MIME: application/vnd.docker.image.rootfs.diff.tar.gzip
| 33.125 | 92 | 0.767715 | yue_Hant | 0.171757 |
9bc3838d398c9a3dda33e395cdf9879e2ef79dcf | 20 | md | Markdown | README.md | zeelos/leshan-client-demo | 6f8f1511efcc4d235358b80ef861a4ee3204c584 | [
"Apache-2.0"
] | null | null | null | README.md | zeelos/leshan-client-demo | 6f8f1511efcc4d235358b80ef861a4ee3204c584 | [
"Apache-2.0"
] | null | null | null | README.md | zeelos/leshan-client-demo | 6f8f1511efcc4d235358b80ef861a4ee3204c584 | [
"Apache-2.0"
] | null | null | null | # leshan-client-demo | 20 | 20 | 0.8 | cat_Latn | 0.324919 |
9bc4a3e40940d3f6c8b7776cde4bf6f16c60fa8f | 378 | markdown | Markdown | guitar/improvisation/general/triads/index.markdown | fabriciofmsilva/aprenda-musica | da537cf773fb30313448322e9c5af25409ee97f1 | [
"MIT"
] | null | null | null | guitar/improvisation/general/triads/index.markdown | fabriciofmsilva/aprenda-musica | da537cf773fb30313448322e9c5af25409ee97f1 | [
"MIT"
] | 1 | 2021-03-30T08:38:38.000Z | 2021-03-30T08:38:38.000Z | guitar/improvisation/general/triads/index.markdown | fabriciofmsilva/aprenda-musica | da537cf773fb30313448322e9c5af25409ee97f1 | [
"MIT"
] | null | null | null | ---
layout: post
title: "Improvisation harmonic implications with triads"
lead: "Improvisation harmonic implications with triads with Tomo Fujita"
lang: en
author:
- name: "Ibanez Guitar"
url: "https://www.youtube.com/channel/UCatC7redhzZ-ayFqwWDXMTQ"
tags: [guitar, improvisation]
videos:
- url: https://www.youtube.com/embed/m8a8qT4kCNc
platform: youtube
---
| 27 | 72 | 0.738095 | eng_Latn | 0.369329 |
9bc7080be5771dae217bdce61df02c065f935cff | 2,404 | md | Markdown | ce/customer-service/unified-routing-faqs.md | fowl2/dynamics-365-customer-engagement | 225343498d8ca6ae112467f2f9000232eb605927 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ce/customer-service/unified-routing-faqs.md | fowl2/dynamics-365-customer-engagement | 225343498d8ca6ae112467f2f9000232eb605927 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ce/customer-service/unified-routing-faqs.md | fowl2/dynamics-365-customer-engagement | 225343498d8ca6ae112467f2f9000232eb605927 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
title: "Frequently asked questions about unified routing | MicrosoftDocs"
description: "Learn about the frequently asked questions (FAQs) for unified routing in Customer Service and Omnichannel for Customer Service."
author: neeranelli
ms.author: nenellim
manager: shujoshi
ms.date: 04/09/2021
ms.topic: article
ms.service: "dynamics-365-customerservice"
---
# FAQs about unified routing in Customer Service, Omnichannel for Customer Service
## Overview
This topic contains the FAQs that you as an administrator, supervisor, or agent might have about unified routing.
### What SKUs must I have to get unified routing?
Customers will get unified routing for entities, such as Cases, Leads, and custom entities as a part of the Customer Service Enterprise license. When you purchase channels (Chat and Digital messaging), you'll get unified routing for chat and messaging channels automatically.
### What will happen to my current workstreams after unified routing is installed?
For messaging channels, a migration utility will be available to upgrade the workstream and associated routing rules. For entity routing, you'll configure new workstream and rules in unified routing.
### Will unified routing support activity routing?
Yes, unified routing supports routing activities, including email.
### What happens to my existing queues after I migrate to unified routing?
The existing queues will be automatically migrated to unified routing.
### Will intelligent skill finder be available in all geographical regions?
Intelligent skill finder requires AI Builder to create and train the machine learning (ML) model. If AI Builder is not available in the customer region where unified routing is, the customer will get a generic error when trying to setup the model.
### Can I use intelligent skill finder with email activities?
Yes, intelligent skill finder can be enabled for any entity that is enabled for routing by using any text-based field. For email body skill finder, an additional step is required because email body (description) includes HTML tags that can impact the ML model. You'll extract the text from HTML, copy it into another text field, then configure the ML model against the new field.
### See also
[Overview of unified routing](overview-unified-routing.md)
[System requirements for Omnichannel for Customer Service](system-requirements-omnichannel.md)
| 51.148936 | 379 | 0.797837 | eng_Latn | 0.998267 |
9bc7f03fdfb3ac4e70e760e744718b978d6e1275 | 907 | md | Markdown | AlchemyInsights/commercial-dialogues/offboard-devices-from-microsoft-defender-advanced-threat-protection.md | isabella232/OfficeDocs-AlchemyInsights-pr.pt-PT | 90231c80c97b1b9ed11265c724351335698b74e2 | [
"CC-BY-4.0",
"MIT"
] | 1 | 2020-05-19T19:07:32.000Z | 2020-05-19T19:07:32.000Z | AlchemyInsights/commercial-dialogues/offboard-devices-from-microsoft-defender-advanced-threat-protection.md | MicrosoftDocs/OfficeDocs-AlchemyInsights-pr.pt-PT | 0ab4044e197cacbe672dd3619523546c471d53c2 | [
"CC-BY-4.0",
"MIT"
] | 4 | 2020-06-02T23:16:58.000Z | 2022-02-09T06:59:55.000Z | AlchemyInsights/commercial-dialogues/offboard-devices-from-microsoft-defender-advanced-threat-protection.md | isabella232/OfficeDocs-AlchemyInsights-pr.pt-PT | 90231c80c97b1b9ed11265c724351335698b74e2 | [
"CC-BY-4.0",
"MIT"
] | 4 | 2019-10-09T20:26:06.000Z | 2021-10-09T10:39:37.000Z | ---
title: Dispositivos offboard do Microsoft Defender Advanced Threat Protection
ms.author: v-jmathew
author: v-jmathew
manager: dansimp
audience: Admin
ms.topic: article
ms.service: o365-administration
ROBOTS: NOINDEX, NOFOLLOW
localization_priority: Normal
ms.collection: Adm_O365
ms.custom:
- "9000760"
- "7391"
ms.openlocfilehash: 60a25c92b45e050893cc20545fc7a9b753c01009197b209c63e3bc56accf1e04
ms.sourcegitcommit: b5f7da89a650d2915dc652449623c78be6247175
ms.translationtype: MT
ms.contentlocale: pt-PT
ms.lasthandoff: 08/05/2021
ms.locfileid: "53967848"
---
# <a name="offboard-devices-from-microsoft-defender-advanced-threat-protection"></a>Dispositivos offboard do Microsoft Defender Advanced Threat Protection
Consulte [Offboard Windows 10 dispositivos](https://go.microsoft.com/fwlink/?linkid=2143629) [ou Dispositivos não Windows Dispositivos](https://go.microsoft.com/fwlink/?linkid=2143630).
| 36.28 | 185 | 0.823594 | por_Latn | 0.124659 |
9bc88194d889224c27eefa2d2a1e2bbf27ee05b9 | 24 | md | Markdown | README.md | talentchain/talchain | 26d2f6c26ed92202f4e3735fd4875cdf1a1b2620 | [
"MIT"
] | 3 | 2017-08-27T04:50:46.000Z | 2017-08-27T07:44:17.000Z | README.md | talentchain/talchain | 26d2f6c26ed92202f4e3735fd4875cdf1a1b2620 | [
"MIT"
] | null | null | null | README.md | talentchain/talchain | 26d2f6c26ed92202f4e3735fd4875cdf1a1b2620 | [
"MIT"
] | null | null | null | # talchain
Talent Chain
| 8 | 12 | 0.791667 | eng_Latn | 0.501969 |
9bc8f114d238ea02aded5d4b087f768435f6d5e3 | 2,139 | md | Markdown | index.md | Chris35Wills/Chris35Wills.github.io | eb3990caae6c8bde16a609a60f8a7860859f2095 | [
"MIT"
] | 1 | 2021-09-15T17:19:03.000Z | 2021-09-15T17:19:03.000Z | index.md | Chris35Wills/Chris35Wills.github.io | eb3990caae6c8bde16a609a60f8a7860859f2095 | [
"MIT"
] | null | null | null | index.md | Chris35Wills/Chris35Wills.github.io | eb3990caae6c8bde16a609a60f8a7860859f2095 | [
"MIT"
] | 2 | 2020-05-06T21:04:26.000Z | 2021-09-15T17:19:05.000Z | ---
layout: page
title: Chris Williams
permalink: /
---
<div style="float:right; padding-left:20px" markdown="1">
<!---->

</div>
<!--Following work as a glaciology researcher over the past few years, I am now working at the British Geological Survey. I’ve a keen interest in geospatial problem solving and environmental spatio-temporal relationships.-->
Welcome! I'm the Geospatial Analysis Lead working at the British Geological Survey. My background is in physical geography, glaciology research and geomorphology. I spend much of my time leading and working with teams to construct spatial solutions and products addressing a range of geo-environmental data problems. Technically, many of the workflows developed are built using Python and R, as well as including various GIS software platforms including ArcGIS and QGIS.
I am particularly interested in spatio-temporal problem solving and the streamlining of data access and processing workflows.<!--; ultimately, to enable the development of more informed decisions for the purpose of environmental and social sustainable development.-->
If you want to know more, don't hesitate to get in touch.
*All views expressed on this website are my own.*
<!--**Past projects include:**
- the development of synthetic fjord bathymetry in the absence of data - read a paper on it [here](https://www.the-cryosphere.net/11/363/2017/tc-11-363-2017.html) and the most recent release of the code [here](https://zenodo.org/record/827347#.Waa1ociGPcs)
- automated assessment of crevasse patterns for assessing crevasse evolution - check out the most recent release of the code [here](https://zenodo.org/record/830251#.Waa1f8iGPcs)
- spatially distributed grid based mass balance modelling - [here's a model you can play with](https://github.com/Chris35Wills/SEB_model_java_files)
- hyperspectral image analysis over tidewater glaciers to identify presence of water
- glacier reconstruction through the compilation of old (topographic maps) and new datasets (contemporary field surveys)
--> | 76.392857 | 471 | 0.791024 | eng_Latn | 0.990166 |
9bc9026bf8a2b422eeec60a706246b1b35e20303 | 25 | md | Markdown | README.md | UKHomeOffice/dq-packer-int-tableau | f4bc67223db088595931cb46cce8028c75928df9 | [
"MIT"
] | null | null | null | README.md | UKHomeOffice/dq-packer-int-tableau | f4bc67223db088595931cb46cce8028c75928df9 | [
"MIT"
] | null | null | null | README.md | UKHomeOffice/dq-packer-int-tableau | f4bc67223db088595931cb46cce8028c75928df9 | [
"MIT"
] | 1 | 2021-04-11T09:26:10.000Z | 2021-04-11T09:26:10.000Z | # dq-packer-int-tableau
| 12.5 | 24 | 0.72 | deu_Latn | 0.164816 |
9bc9694767d1fed2823f09d6cd0522986cc094be | 1,330 | md | Markdown | 2020/12/07/2020-12-07 07:25.md | zhzhzhy/WeiBoHot_history | 32ce4800e63f26384abb17d43e308452c537c902 | [
"MIT"
] | 3 | 2020-07-14T14:54:15.000Z | 2020-08-21T06:48:24.000Z | 2020/12/07/2020-12-07 07:25.md | zhzhzhy/WeiBoHot_history | 32ce4800e63f26384abb17d43e308452c537c902 | [
"MIT"
] | null | null | null | 2020/12/07/2020-12-07 07:25.md | zhzhzhy/WeiBoHot_history | 32ce4800e63f26384abb17d43e308452c537c902 | [
"MIT"
] | null | null | null | 2020年12月07日07时数据
Status: 200
1.焉栩嘉道歉需要付费观看
微博热度:1183171
2.摩萨德指挥官疑似在以色列遭枪杀
微博热度:839709
3.贾玲回应刘德华喊她演夫人
微博热度:833669
4.大雪
微博热度:719075
5.温碧霞身材
微博热度:611410
6.人工智能还原的宋朝皇帝
微博热度:546745
7.天天向上
微博热度:405519
8.MAMA颁奖典礼上的消毒人员
微博热度:396101
9.白岩松问为啥洒水车几乎每年都致结冰
微博热度:366685
10.生姜价格翻了近一倍
微博热度:349959
11.徐佳莹生子
微博热度:345636
12.BLACKPINK最佳女团奖
微博热度:331807
13.印小天发文
微博热度:252396
14.时代周刊称2020是最糟糕的一年
微博热度:251976
15.爱的厘米
微博热度:231163
16.小伊伊怀孕
微博热度:211037
17.刘亦菲为唐嫣庆生
微博热度:198651
18.大雪过后贪吃蛇出动
微博热度:185279
19.物业用鼓风机帮业主清车上积雪
微博热度:182050
20.巨人
微博热度:176798
21.牌牌琦
微博热度:175761
22.赵本山潘长江视频太好笑了
微博热度:174426
23.王勉怂了
微博热度:172456
24.R1SE酒醉的壶人
微博热度:156949
25.TWICE没拿到奖
微博热度:136852
26.张艺兴舞台好燃
微博热度:127353
27.武磊进球
微博热度:126357
28.闽南没有siri
微博热度:125429
29.今年全球汽车销量或萎缩五分之一
微博热度:124663
30.美国男子三周内失去四位至亲
微博热度:124644
31.希林娜依高容祖儿神仙合唱
微博热度:124642
32.BoA和泰民一起跳Only One
微博热度:121228
33.王嘉尔普通话好听
微博热度:95871
34.徐守盛
微博热度:91709
35.虞书欣钻边复古红丝绒裙
微博热度:91545
36.李斯丹妮教腾格尔唱耶斯莫拉
微博热度:88095
37.蒙面唱将
微博热度:86003
38.战网崩了
微博热度:80811
39.张定宇学医是为照顾妈妈
微博热度:78403
40.焉栩嘉回应
微博热度:77433
41.国家宝藏
微博热度:75438
42.刘德华请贾玲演自己夫人
微博热度:72765
43.美国新冠肺炎超1470万例
微博热度:68547
44.扑通心动表彰大会
微博热度:68098
45.亚冠
微博热度:67276
46.时代少年团全开麦
微博热度:64404
47.东北奶奶院里堆出雪人世界
微博热度:62757
48.我们的歌
微博热度:61356
49.肖战
微博热度:60768
50.2020MAMA
微博热度:56307
| 6.519608 | 20 | 0.769925 | yue_Hant | 0.373231 |
9bc9a2638bcb0258e56e1fa8a8a66a15cb6ce084 | 10,192 | md | Markdown | algorithm/greedy.md | joinee0208/Algorithm-Guide | 019eafeaa5de25e24030ea31f5c0b5d3aee982eb | [
"Apache-2.0"
] | 726 | 2020-04-29T02:05:43.000Z | 2020-08-07T02:02:01.000Z | algorithm/greedy.md | joinee0208/Algorithm-Guide | 019eafeaa5de25e24030ea31f5c0b5d3aee982eb | [
"Apache-2.0"
] | 1 | 2021-08-09T10:42:32.000Z | 2021-08-12T07:20:09.000Z | algorithm/greedy.md | joinee0208/Algorithm-Guide | 019eafeaa5de25e24030ea31f5c0b5d3aee982eb | [
"Apache-2.0"
] | 112 | 2020-04-29T04:34:41.000Z | 2020-08-06T12:16:37.000Z | # **贪心算法**
## 思路
若在求解一个问题时,能根据每次所得到的局部最优解,推导出全局最优或最优目标。
那么,我们可以根据这个策略,每次得到局部最优解答,逐步而推导出问题,这种策略称为**贪心法**
**【例1】**在N行M列的正整数矩阵中,要求从每行中选出1个数,使得选出的总共N个数的和最大。
**【算法分析】**
要使总和最大,则每个数要尽可能大,自然应该选每行中最大的那个数。因此,我们设计出如下算法:
读入N, M,矩阵数据;
``` c
Total = 0;
for (int l= 1; l<= N; ++l)
{ //对N行进行选择
选择第I行最大的数,记为K;
Total +=K;
}
输出最大总和Total;
```
从上例中我们可以看出,和递推法相仿,贪心法也是从问题的某一个初始解出发,向给定的目标递推。但不同的是,推进的每一步不是依据某一固定的递推式,而是做一个局部的最优选择,即贪心选择(在例中,这种贪心选择表现为选择一行中的最大整数),这样,不断的将问题归纳为若干相似的子问题,最终产生出一个全局最优解。
特别注意的是,局部贪心的选择是否可以得出全局最优是能否采用贪心法的关键所在。对于能否使用贪心策略,应从理论上予以证明。下面我们看看另一个问题。
**【例2】部分背包问题**
给定一个最大载重量为M的卡车和N种食品,有食盐,白糖,大米等。已知第i种食品的最多拥有Wi公斤,其商品价值为Vi元/公斤,编程确定一个装货方案,使得装入卡车中的所有物品总价值最大。
**【算法分析】**
因为每一个物品都可以分割成单位块,单位块的利益越大显然总收益越大,所以它局部最优满足全局最优,可以用贪心法解答,方法如下:先将单位块收益按从大到小进行排列,然后用循环从单位块收益最大的取起,直到不能取为止便得到了最优解。
因此我们非常容易设计出如下算法:
问题初始化; //读入数据
按Vi从大到小将商品排序;
``` c++
i=1;
do
{
if (m==0) break; //如果卡车满载则跳出循环
m=m-w[i];
if (m>=0) //将第i种商品全部装入卡车
else 将(m+w[i]) 重量的物品i装入卡车;
i=i+1; //选择下一种商品
}while (m>0&&i<=n);
```
在解决上述问题的过程中,首先根据题设条件,找到了贪心选择标准(Vi),并依据这个标准直接逐步去求最优解,这种解题策略被称为贪心法。
## 贪心解决的问题
**因此,利用贪心策略解题,需要解决两个问题:**
**首先,确定问题是否能用贪心策略求解;一般来说,适用于贪心策略求解的问题具有以下特点:**
**①**可通过局部的贪心选择来达到问题的全局最优解。运用贪心策略解题,一般来说需要一步步的进行多次的贪心选择。在经过一次贪心选择之后,原问题将变成一个相似的,但规模更小的问题,而后的每一步都是当前看似最佳的选择,且每一个选择都仅做一次。
**②**原问题的最优解包含子问题的最优解,即问题具有最优子结构的性质。在背包问题中,第一次选择单位重量价值最大的货物,它是第一个子问题的最优解,第二次选择剩下的货物中单位重量价值最大的货物,同样是第二个子问题的最优解,依次类推。
**③**其次,如何选择一个贪心标准?正确的贪心标准可以得到问题的最优解,在确定采用贪心策略解决问题时,不能随意的判断贪心标准是否正确,尤其不要被表面上看似正确的贪心标准所迷惑。在得出贪心标准之后应给予严格的数学证明。
## 例题讲解
**下面来看看0-1背包问题。**
给定一个最大载重量为M的卡车和N种动物。已知第i种动物的重量为Wi,其最大价值为Vi,设定M,Wi,Vi均为整数,编程确定一个装货方案,使得装入卡车中的所有动物总价值最大。
【分析】对于n种动物,要么被装,要么不装,也就是说在满足卡车载重的条件下,如何选择动物,使得动物价值最大的问题。
即确定一组x1,x2,…,xn, xi∈{0,1}
` f(x)=max(∑xi*vi) 其中,∑(xi*wi)≦w`
从直观上来看,我们可以按照上例一样选择那些价值大,而重量轻的动物。也就是可以按价值质量比(vi/wi)的大小来进行选择。可以看出,每做一次选择,都是从剩下的动物中选择那些vi/wi最大的,这种局部最优的选择是否能满足全局最优呢?我们来看看一个简单的例子:
设n=3,卡车最大载重量是100,三种动物a、b、c的重量分别是40,50,70,其对应的总价值分别是80、100、150。
情况a:按照上述思路,三种动物的vi/wi分别为2,2,2.14。显然,我们首先选择动物c,得到价值150,然后任意选择a或b,由于卡车最大载重为100,因此卡车不能装载其他动物。
情况b:不按上述约束条件,直接选择a和b。可以得到价值80+100=180,卡车装载的重量为40+50=90。没有超过卡车的实际载重,因此也是一种可行解,显然,这种解比上一种解要优化。
问题出现在什么地方呢?我们看看图23
从图23中明显可以看出,情况a,卡车的空载率比情况b高。也就是说,上面的分析,只考虑了货物的价值质量比,而没有考虑到卡车的运营效率,因此,局部的最优化,不能导致全局的最优化。
因此,贪心不能简单进行,而需要全面的考虑,最后得到证明。
**【例3】排队打水问题**
有N个人排队到R个水龙头去打水,他们装满水桶的时间为T1,T2,…,Tn为整数且各不相等,应如何安排他们的打水顺序才能使他们花费的时间最少?
**【算法分析】**
由于排队时,越靠前面的计算的次数越多,显然越小的排在越前面得出的结果越小(可以用数学方法简单证明,这里就不再赘述),所以这道题可以用贪心法解答,基本步骤:
1. 将输入的时间按从小到大排序;
2. 将排序后的时间按顺序依次放入每个水龙头的队列中;
3. 统计,输出答案。
**【样例输入】**
4 2 //4人打水,2个水龙头
2 6 4 5 //每个打水时间
### 实现代码
``` c++
cin>>n>>r;
memset(s,0,sizeof(s)); //初始化
j=0; min=0;
for (i=1;i<=n;++i) //用贪心法求解
{
j++;
if (j==r+1) j=1;
s[j]+=a[i];
min+=s[j];
}
cout<<min; //输出解答
```
**【例4】均分纸牌(NOIP2002)**
有 N 堆纸牌,编号分别为 1,2,…, N。每堆上有若干张,但纸牌总数必为 N 的倍数。可以在任一堆上取若干张纸牌,然后移动。
移牌规则为:在编号为 1 堆上取的纸牌,只能移到编号为 2 的堆上;在编号为 N 的堆上取的纸牌,只能移到编号为 N-1 的堆上;其他堆上取的纸牌,可以移到相邻左边或右边的堆上。
现在要求找出一种移动方法,用最少的移动次数使每堆上纸牌数都一样多。
例如 N=4,4 堆纸牌数分别为: ① 9 ② 8 ③ 17 ④ 6
移动3次可达到目的:
从 ③ 取4张牌放到④(9 8 13 10)->从③取3张牌放到 ②(9 11 10 10)-> 从②取1张牌放到①(10 10 10 10)。
【输入格式】
N(N 堆纸牌,1 <= N <= 100)
A1 A2 … An (N 堆纸牌,每堆纸牌初始数,l<= Ai <=10000)
【输出格式】
所有堆均达到相等时的最少移动次数。
【样例输入】Playcard.in
4
9 8 17 6
【样例输出】Playcard.out
3
【算法分析】
如果你想到把每堆牌的张数减去平均张数,题目就变成移动正数,加到负数中,使大家都变成0,那就意味着成功了一半!拿例题来说,平均张数为10,原张数9,8,17,6,变为-1,-2,7,-4,其中没有为0的数,我们从左边出发:要使第1堆的牌数-1变为0,只须将-1张牌移到它的右边(第2堆)-2中;结果是-1变为0,-2变为-3,各堆牌张数变为0,-3,7,-4;同理:要使第2堆变为0,只需将-3移到它的右边(第3堆)中去,各堆牌张数变为0,0,4,-4;要使第3堆变为0,只需将第3堆中的4移到它的右边(第4堆)中去,结果为0,0,0,0,完成任务。每移动1次牌,步数加1。也许你要问,负数张牌怎么移,不违反题意吗?其实从第i堆移动-m张牌到第i+1堆,等价于从第i+1堆移动m张牌到第i堆,步数是一样的。
如果张数中本来就有为0的,怎么办呢?如0,-1,-5,6,还是从左算起(从右算起也完全一样),第1堆是0,无需移牌,余下与上相同;再比如-1,-2,3,10,-4,-6,从左算起,第1次移动的结果为0,-3,3,10,-4,-6;第2次移动的结果为0,0,0,10,-4,-6,现在第3堆已经变为0了,可节省1步,余下继续。
### 实现代码
``` c++
cin>>n;
ave=0;step=0;
for (i=1;i<=n;++i)
{
cin>>a[i]; ave+=a[i]; //读入各堆牌张数,求总张数ave
}
ave/=n; //求牌的平均张数ave
for (i=1;i<=n;++i) a[i]-=ave; //每堆牌的张数减去平均数
i=1;j=n;
while (a[i]==0&&i<n) ++i; //过滤左边的0
while (a[j]==0&&j>1) --j; //过滤右边的0
while (i<j)
{
a[i+1]+=a[i]; //将第i堆牌移到第i+1堆中去
a[i]=0; //第i堆牌移走后变为0
++step; //移牌步数计数
++i; //对下一堆牌进行循环操作
while (a[i]==0&&i<j) ++i; //过滤移牌过程中产生的0
}
cout<<step<<endl;
```
**【例5】删数问题(NOI94)**
输入一个高精度的正整数N,去掉其中任意S个数字后剩下的数字按原左右次序组成一个新的正整数。编程对给定的N和S,寻找一种方案使得剩下的数字组成的新数最小。
输出新的正整数。(N不超过240位)输入数据均不需判错。
【输入】
n
s
【输出】
最后剩下的最小数。
【样例输入】
175438
4
【样例输出】
13
【算法分析】
由于正整数n的有效数位为240位,所以很自然地采用字符串类型存贮n。那么如何决定哪s位被删除呢?是不是最大的s个数字呢?显然不是,大家很容易举出一些反例。
为了尽可能逼近目标,我们选取的贪心策略为:每一步总是选择一个使剩下的数最小的数字删去,即按高位到低位的顺序搜索,若各位数字递增,则删除最后一个数字;否则删除第一个递减区间的首字符,这样删一位便形成了一个新数字串。
然后回到串首,按上述规则再删下一个数字。重复以上过程s次为止,剩下的数字串便是问题的解了。
例如:n=175438
s=4
删数的过程如下:
n=175438 //删掉7
15438 //删掉5
1438 //删掉4
138 //删掉8
13 //解为13
这样,删数问题就与如何寻找递减区间首字符这样一个简单的问题对应起来。不过还要注意一个细节性的问题,就是可能会出现字符串串首有若干0的情况,甚至整个字符串都是0的情况。按以上贪心策略编制的程序框架如下
``` c++
输入n,s;
for (i=1;i<=s;++i) { //一共要删除s个字符
for ( j=0;j<len-1;++j ) //从串首开始找,len是n的长度
if ( n[j]>n[j+1] ) { //找到第一个符合条件的
for ( k=j;k<len-1;++k ) //删除字符串n的第j个字符 ,后面字符往前整
n[k]=n[k+1];
break;
}
--len; //长度减1
}
输出n; //删去串首可能产生的无用零
```
**【例6】拦截导弹问题(NOIP1999)**
某国为了防御敌国的导弹袭击,开发出一种导弹拦截系统,但是这种拦截系统有一个缺陷:虽然它的第一发炮弹能够到达任意的高度,但是以后每一发炮弹都不能高于前一发的高度。某天,雷达捕捉到敌国的导弹来袭,由于该系统还在试用阶段。所以一套系统有可能不能拦截所有的导弹。
输入导弹依次飞来的高度(雷达给出的高度不大于30000的正整数)。计算要拦截所有导弹最小需要配备多少套这种导弹拦截系统。
**【输入格式】**
n颗依次飞来的高度(1≤n≤1000).
**【输出格式】**
要拦截所有导弹最小配备的系统数k。
**【输入样例】missile.in**
389 207 155 300 299 170 158 65
**【输出样例】missile.out**
2
**【输入输出样例】**
输入:导弹高度: 7 9 6 8 5
输出:导弹拦截系统K=2
输入:导弹高度: 4 3 2
输出:导弹拦截系统K=1
**【算法分析】**
按照题意,被一套系统拦截的所有导弹中,最后一枚导弹的高度最低。设:
k为当前配备的系统数;
l[k]为被第k套系统拦截的最后一枚导弹的高度,简称系统k的最低高度(1≤k≤n)。
我们首先设导弹1被系统1所拦截(k←1,l[k]←导弹1的高度)。然后依次分析导弹2,…,导弹n的高度。
若导弹i的高度高于所有系统的最低高度,则断定导弹i不能被这些系统所拦截,应增设一套系统来拦截导弹I(k←k+1,l[k]←导弹i的高度);若导弹i低于某些系统的最低高度,那么导弹i均可被这些系统所拦截。
究竟选择哪个系统拦截可使得配备的系统数最少,我们不妨采用贪心策略,选择其中最低高度最小(即导弹i的高度与系统最低高度最接近)的一套系统p(l[p]=min{l[j]|l[j]>导弹i的高度};l[p]←导弹i的高度)(i≤j≤k)。这样可使得一套系统拦截的导弹数尽可能增多。
依次类推,直至分析了n枚导弹的高度为止。此时得出的k便为应配备的最少系统数。
### 实现代码
``` c++
k=1;l[k]=导弹1的高度;
for (i=2;i<=n;++i)
{
p=0;
for (j=1;j<=k;++j)
if (l[j]>=导弹i的高度) { if (p==0) p=j;
else if (l[j]<l[p]) p=j;}
if (p==0) { ++k;l[k]=导弹i的高度; }
else l[p]=导弹i的高度;
}
输出应配备的最少系统数K。
```
【例7】活动选择
学校在最近几天有n个活动,这些活动都需要使用学校的大礼堂,在同一时间,礼堂只能被一个活动使。由于有些活动时间上有冲突,学校办公室人员只好让一些活动放弃使用礼堂而使用其他教室。
现在给出n个活动使用礼堂的起始时间begini和结束时间endi(begini < endi),请你帮助办公室人员安排一些活动来使用礼堂,要求安排的活动尽量多。
【输入】 第一行一个整数n(n<=1000);
接下来的n行,每行两个整数,第一个begini,第二个是endi(begini< endi <=32767)
【输出】 输出最多能安排的活动个数。
【样例输入】
11
3 5
1 4
12 14
8 12
0 6
8 11
6 10
5 7
3 8
5 9
2 13
【样例输出】
4
【算法分析】
• 算法模型:给n个开区间(begini,endi), 选择尽量多的区间, 使得两两不交。
• 做法: 首先按照end1<=end2<…<=endn的顺序排序,依次考虑各个活动, 如果没有和已经选择的活动冲突, 就选; 否则就不选。
• 正确性: 如果不选end1, 假设第一个选择的是endi,则如果endi和end1不交叉则多选一个end1更划算; 如果交叉则把endi换成end1不影响后续选择。
### 实现代码
``` c++
#include<iostream>
using namespace std;
int n,begin[1001],end[1001];
void init()
{
cin>>n;
for(int i=1;i<=n;i++)
cin>>begin[i]>>end[i];
}
void qsort(int x,int y)
{
int i,j,mid,t;
i=x;j=y;mid=end[(x+y)/2];
while(i<=j)
{
while(end[i]<mid) ++i;
while(end[j]>mid) --j;
if(i<=j)
{
t=end[j];end[j]=end[i];end[i]=t;
t=begin[j];begin[j]=begin[i];begin[i]=t;
++i;j;
}
}
if(x<j) qsort(x,j);
if(i<y) qsort(i,y);
}
void solve()
{
int ans=0;
for(int i=1,t=-1;i<=n;++i) //在初始化循环变量的同时,初始化t。
//令t=-1可以使第一个区间与其他区间的操作相同。
if(begin[i]>=t) {++ans;t=end[i];}//如果当前活动与之前最后结束的活动不冲突,
就接受当前活动。
cout<<ans<<endl;
}
int main()
{
init();
qsort(1,n);
solve();
return 0;
}
```
【例8】整数区间
请编程完成以下任务:
1.从文件中读取闭区间的个数及它们的描述;
2.找到一个含元素个数最少的集合,使得对于每一个区间,都至少有一个整数属于该集合,输出该集合的元素个数。
【输入】
首行包括区间的数目n,1<=n<=10000,接下来的n行,每行包括两个整数a,b,被一空格隔开,0<=a<=b<=10000,它们是某一个区间的开始值和结束值。
【输出】
第一行集合元素的个数,对于每一个区间都至少有一个整数属于该区间,且集合所包含元素数目最少。
【样例输入】
4
3 6
2 4
0 2
4 7
【样例输出】
2
【算法分析】
算法模型:给n个闭区间[ai,bi], 在数轴上选尽量少的点,使每个区间内至少有一个点。
算法:首先按b1<=b2<=...<=bn排序。每次标记当前区间的右端点x,并右移当前区间指针,直到当前区间不包含x,再重复上述操作。
如下图,如果选灰色点,移动到黑色点更优。
``` c++
#include<iostream>
using namespace std;
int a[10001],b[10001],sum=0,n,m;
void qsort(int x,int y) //多关键字快排
{
int i,j,mid1,mid2,t;
i=x;j=y;mid1=b[(x+y)/2];mid2=a[(x+y)/2];
while(i<=j)
{ while(b[i]<mid1||((b[i]==mid1)&&(a[i]<mid2))) ++i;
while(b[j]>mid1||((b[j]==mid1)&&(a[j]>mid2))) --j;
if(i<=j)
{ t=b[j];b[j]=b[i];b[i]=t;
t=a[j];a[j]=a[i];a[i]=t;
++i; --j;
}
}
if(x<j) qsort(x,j);
if(i<y) qsort(i,y);
}
int main()
{
cin>>n;
for(int i=1;i<=n;++i)cin>>a[i]>>b[i];
qsort(1,n);
for(int i=1,x=-1;i<=n;++i) //在初始化循环变量的同时,初始化x。
//令x=-1可以使第一个区间与其他区间的操作
相同。
{
if (x>=a[i]) continue; //如果当前区间包含标记点,就跳过。
++sum; x=b[i]; //更新标记点。
}
cout<<sum<<endl;
return 0;
}
```
| 18.167558 | 354 | 0.597429 | yue_Hant | 0.31597 |
9bcb987467722e8c5349a66b067e7a421548418f | 76 | md | Markdown | dds-cloud-fog-edge.md | peterpolidoro/cybernetic-architecture-presentation | d5a099002b60525c3db608e7e8d20e7053e526d1 | [
"BSD-3-Clause"
] | null | null | null | dds-cloud-fog-edge.md | peterpolidoro/cybernetic-architecture-presentation | d5a099002b60525c3db608e7e8d20e7053e526d1 | [
"BSD-3-Clause"
] | null | null | null | dds-cloud-fog-edge.md | peterpolidoro/cybernetic-architecture-presentation | d5a099002b60525c3db608e7e8d20e7053e526d1 | [
"BSD-3-Clause"
] | null | null | null | ---
layout: presentation
---
[](iic)
| 12.666667 | 45 | 0.631579 | eng_Latn | 0.19182 |
9bce9c167519f175313d9a45addd8c8542906e21 | 465 | md | Markdown | markdown/Conflicts/883.md | akaalias/plotto-for-obsidian | f4627272b018a76ac772f1ed2b9b3747928eb636 | [
"MIT"
] | null | null | null | markdown/Conflicts/883.md | akaalias/plotto-for-obsidian | f4627272b018a76ac772f1ed2b9b3747928eb636 | [
"MIT"
] | null | null | null | markdown/Conflicts/883.md | akaalias/plotto-for-obsidian | f4627272b018a76ac772f1ed2b9b3747928eb636 | [
"MIT"
] | null | null | null | ## 883
- Previous: [[1209 | 1209a]] [[1298]] [[955]]
- A, a hunted outlaw in disguise, takes refuge with an enemy, [[A-3]]
- A, a hunted outlaw, takes refuge with an enemy, [[A-3]]; and [[A-3]], considering himself bound by the laws of hospitality, conceals A and saves him from his pursuers, [[A-6]], [[A-6]]
- Next: [[923 | 923 ch A-5 to A-3]] [[1022]]
## B Clause
- Finding a Sustaining Power in Misfortune
## Group
- Enterprise
### Subgroup
- Deliverance
| 29.0625 | 186 | 0.645161 | eng_Latn | 0.993081 |
9bcf75dc91b6d7d6b3d6dfd0a9eac45d0fd4a521 | 40 | md | Markdown | erpc-sys/README.md | frankrap/erpc-rs | 2de6224732db91e766b848e7f3c01cee7252496b | [
"Apache-2.0"
] | 8 | 2020-01-23T22:29:29.000Z | 2022-02-01T00:52:31.000Z | erpc-sys/README.md | frankrap/erpc-rs | 2de6224732db91e766b848e7f3c01cee7252496b | [
"Apache-2.0"
] | null | null | null | erpc-sys/README.md | frankrap/erpc-rs | 2de6224732db91e766b848e7f3c01cee7252496b | [
"Apache-2.0"
] | null | null | null | # erpc-sys
The Rust FFI bindings of eRPC | 20 | 29 | 0.775 | eng_Latn | 0.657522 |
9bd06f9ef702c9eaf5ad04b8c3e6a695e006345d | 1,461 | md | Markdown | docs/csharp/misc/cs1101.md | lucieva/docs.cs-cz | a688d6511d24a48fe53a201e160e9581f2effbf4 | [
"CC-BY-4.0",
"MIT"
] | 1 | 2018-12-19T17:04:23.000Z | 2018-12-19T17:04:23.000Z | docs/csharp/misc/cs1101.md | lucieva/docs.cs-cz | a688d6511d24a48fe53a201e160e9581f2effbf4 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/csharp/misc/cs1101.md | lucieva/docs.cs-cz | a688d6511d24a48fe53a201e160e9581f2effbf4 | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
title: CS1101 chyby kompilátoru
ms.date: 07/20/2015
f1_keywords:
- CS1101
helpviewer_keywords:
- CS1101
ms.assetid: d6fc8834-eadf-4497-b442-0751895e6764
ms.openlocfilehash: 863c2adb9e2a174f371b17ef911c0038e5c92aea
ms.sourcegitcommit: 412bbc2e43c3b6ca25b358cdf394be97336f0c24
ms.translationtype: MT
ms.contentlocale: cs-CZ
ms.lasthandoff: 08/25/2018
ms.locfileid: "42925141"
---
# <a name="compiler-error-cs1101"></a>CS1101 chyby kompilátoru
Modifikátor parametru "ref" nelze kombinovat s modifikátorem this.
Když `this` – klíčové slovo upraví první parametr statická metoda, signalizuje kompilátoru, že metoda je metodou rozšíření. Bez parametrů jsou potřeba nebo povoleno na první parametr metody rozšíření.
## <a name="example"></a>Příklad
Následující příklad generuje CS1101:
```csharp
// cs1101.cs
// Compile with: /target:library
public static class Extensions
{
// No type parameters.
public static void Test(ref this int i) {} // CS1101
// Single type parameter.
public static void Test<T>(ref this T t) {}// CS1101
// Multiple type parameters.
public static void Test<T,U,V>(ref this U u) {}// CS1101
}
```
## <a name="see-also"></a>Viz také
- [Rozšiřující metody](../../csharp/programming-guide/classes-and-structs/extension-methods.md)
- [this](../../csharp/language-reference/keywords/this.md)
- [ref](../../csharp/language-reference/keywords/ref.md)
| 32.466667 | 203 | 0.714579 | ces_Latn | 0.876242 |
9bd12c8034ad6b89e26c4c514a406b028c901443 | 1,134 | md | Markdown | content/blog/man-dies-after-wreck-on-chicon.md | emmadigital/austinlaw | 86800e56e9d74fcd48b44ef567957b3bc347e338 | [
"MIT"
] | null | null | null | content/blog/man-dies-after-wreck-on-chicon.md | emmadigital/austinlaw | 86800e56e9d74fcd48b44ef567957b3bc347e338 | [
"MIT"
] | null | null | null | content/blog/man-dies-after-wreck-on-chicon.md | emmadigital/austinlaw | 86800e56e9d74fcd48b44ef567957b3bc347e338 | [
"MIT"
] | 2 | 2020-09-03T08:40:31.000Z | 2021-09-03T03:48:18.000Z | ---
template: SinglePost
title: Man dies after wreck on Chicon
status: Published
date: 2009-10-15
featuredImage: /images/accident-arround-austin.jpg
excerpt: A 59-year-old man died Medical Center Brackenridge on Wednesday morning
about three hours after his car collided with a pickup at East Seventh and
Chicon streets, Austin police said.
categories:
- category: Accidents
meta:
title: Man dies after wreck on Chicon
description: A 59-year-old man died Medical Center Brackenridge on Wednesday
morning about three hours after his car collided with a pickup at East
Seventh and Chicon streets, Austin police said.
---
<!--StartFragment-->
A 59-year-old man died Medical Center Brackenridge on Wednesday morning about three hours after his car collided with a pickup at East Seventh and Chicon streets, Austin police said.
According to police, the pickup was heading north on Chicon when the driver ran a red light and hit the car at 1:29 a.m. The driver of the pickup was in critical condition at Brackenridge on Wednesday, Austin police said. Police did not release the name of either driver.
<!--EndFragment--> | 47.25 | 271 | 0.782187 | eng_Latn | 0.998383 |
9bd13e6c3c7480293bdfc68c4cbc9e30ec371681 | 2,890 | md | Markdown | articles/supply-chain/procurement/tasks/approve-vendors-specific-procurement-categories.md | MicrosoftDocs/Dynamics-365-Operations.lt-lt | 4edb9b5897a1f4cc990027074662bd1e8d56ea17 | [
"CC-BY-4.0",
"MIT"
] | 3 | 2020-05-18T17:14:28.000Z | 2022-01-30T03:33:06.000Z | articles/supply-chain/procurement/tasks/approve-vendors-specific-procurement-categories.md | MicrosoftDocs/Dynamics-365-Operations.lt-lt | 4edb9b5897a1f4cc990027074662bd1e8d56ea17 | [
"CC-BY-4.0",
"MIT"
] | 6 | 2017-12-12T12:37:43.000Z | 2019-04-30T11:46:17.000Z | articles/supply-chain/procurement/tasks/approve-vendors-specific-procurement-categories.md | MicrosoftDocs/Dynamics-365-Operations.lt-lt | 4edb9b5897a1f4cc990027074662bd1e8d56ea17 | [
"CC-BY-4.0",
"MIT"
] | 2 | 2018-02-28T23:29:31.000Z | 2019-10-12T18:18:06.000Z | ---
title: Konkrečių įsigijimo kategorijų tiekėjų tvirtinimas
description: Šioje temoje aiškinama, kaip patvirtinti konkrečių įsigijimo kategorijų Dynamics 365 Supply Chain Management tiekėjus.
author: Henrikan
ms.date: 07/30/2019
ms.topic: business-process
ms.prod: ''
ms.technology: ''
ms.search.form: VendTable, DirPartyEcoResCategory, EcoResCategorySingleLookup, ProcCategoryHierarchyManagement
audience: Application User
ms.reviewer: kamaybac
ms.search.region: Global
ms.author: henrikan
ms.search.validFrom: 2016-06-30
ms.dyn365.ops.version: AX 7.0.0
ms.openlocfilehash: 1a885ba924137c56583db9f81b34db9a20f33bc4
ms.sourcegitcommit: 3b87f042a7e97f72b5aa73bef186c5426b937fec
ms.translationtype: HT
ms.contentlocale: lt-LT
ms.lasthandoff: 09/29/2021
ms.locfileid: "7569438"
---
# <a name="approve-vendors-for-specific-procurement-categories"></a>Konkrečių įsigijimo kategorijų tiekėjų tvirtinimas
[!include [banner](../../includes/banner.md)]
Šioje temoje aiškinama, kaip patvirtinti konkrečių įsigijimo kategorijų Dynamics 365 Supply Chain Management tiekėjus. Sukūrus pirkimo paraišką, gali reikėti pasirinkti patvirtintą arba pageidaujamą tiekėją, atsižvelgiant į tai, kaip nustatytos pirkimo strategijos. Šioje procedūroje parodoma, kaip nurodyti, kad konkrečios įsigijimo kategorijos tiekėjas yra patvirtintas arba pageidaujamas. Šią užduotį paprastai atlieka pirkimų profesionalai. Šią procedūrą galite naudoti demonstracinių duomenų įmonėje USMF.
1. Naršymo srityje eikite į **Moduliai > Įsigijimas ir išteklių paskirstymas > Tiekėjai > Visi tiekėjai**.
2. Pasirinkite tiekėją, kurį norite nustatyti kaip patvirtintą arba pageidaujamą kategorijos tiekėją.
3. Veiksmų srityje spustelėkite **Bendra**.
4. Pažymėkite **Kategorijos**.
5. Pažymėkite **Įtraukti kategoriją**.
6. Lauke **Kategorija** pažymėkite **BIURO IR STALO PRIEDAI (BIURO IR STALO PRIEDAI)**.
7. Lauke **Tiekėjų kategorijos būsena** pažymėkite **Pageidaujama**. Galima nurodyti daugiau nei vieną pageidaujamą kategorijos tiekėją.
8. Pasirinkite **Įrašyti**.
9. Naršymo srityje eikite į **Moduliai > Įsigijimas ir išteklių paskirstymas > Įsigijimo kategorijos**.
10. Medyje pažymėkite **KORP. ĮSIGIJIMO KATEGORIJOS\BIURO IR STALO PRIEDAI**.
11. Išplėskite skyrių **Tiekėjai**. Patikrinkite, ar jūsų pasirinktas tiekėjas rodomas kaip pageidaujamas kategorijos Biuro ir stalo reikmenys tiekėjas. Jei vykdote šią procedūrą kaip užduoties vadovą, gali reikėti pažymėti mygtuką **Atrakinti**, kad galėtumėte slinkti žemyn tiekėjų sąrašu. Šiame puslapyje taip pat galima įtraukti pageidaujamų ir patvirtintų tiekėjų.
12. Medyje išplėskite **BIURO IR STALO PRIEDAI** ir pažymėkite **Žirklės**.
13. Lauke **Paveldimi tiekėjai iš pirminės kategorijos:** pažymėkite **Ne**.
14. Lauke **Paveldimi tiekėjai iš pirminės kategorijos:** pažymėkite **Taip**.
[!INCLUDE[footer-include](../../../includes/footer-banner.md)] | 62.826087 | 510 | 0.805882 | lit_Latn | 0.999985 |
9bd1d85757fc0dd92110c4f006e52587f67b05dc | 2,373 | md | Markdown | README.md | bahamas10/node-nagios-web-server | 9c4d9c7c33f7a07479e3d092fa00aca73c467559 | [
"MIT"
] | 2 | 2018-09-26T20:15:43.000Z | 2020-07-29T12:11:45.000Z | README.md | bahamas10/node-nagios-web-server | 9c4d9c7c33f7a07479e3d092fa00aca73c467559 | [
"MIT"
] | null | null | null | README.md | bahamas10/node-nagios-web-server | 9c4d9c7c33f7a07479e3d092fa00aca73c467559 | [
"MIT"
] | null | null | null | Nagios Web Server
=================
A CGI / PHP node runner script to replace Apache for Nagios
Installation
------------
[sudo] npm install -g nagios-web-server
Example
-------
$ nagios-web-server -H 0.0.0.0 -p 8080 -c /opt/local/libexec/nagios-cgi-bin -P /opt/local/share/nagios
listening on http://0.0.0.0:8080
PHP Warning: date(): It is not safe to rely on the system's timezone settings. You are *required* to use the date.timezone setting or the date_default_timezone_set() function. In case you used any of those methods and you are still getting this warning, you most likely misspelled the timezone identifier. We selected the timezone 'UTC' for now, but please set date.timezone to select your timezone. in /opt/local/share/nagios/index.php on line 53
10.0.1.229 - - [19/May/2015:12:57:50 -0400] "GET / HTTP/1.1" 200 - "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36"
10.0.1.229 - - [19/May/2015:12:57:50 -0400] "GET / HTTP/1.1" 200 - "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36"
10.0.1.229 - - [19/May/2015:12:57:50 -0400] "GET /side.php HTTP/1.1" 200 - "http://nagios.rapture.com:8085/" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36"
Usage
-----
$ nagios-web-server -h
usage: nagios-web-server [options]
options
-c, --cgi-dir <dir> [env NAGIOS_WEB_SERVER_CGIDIR] the directory where nagios CGI scripts live, defaults to /opt/local/libexec/nagios/cgi-bin
-H, --host <host> [env NAGIOS_WEB_SERVER_HOST] the host on which to listen, defaults to 0.0.0.0
-h, --help print this message and exit
-P, --php-dir <dir> [env NAGIOS_WEB_SERVER_PHPDIR] the directory where nagios PHP scripts live, defaults to /opt/local/share/nagios
-p, --port <port> [env NAGIOS_WEB_SERVER_PORT] the port on which to listen, defaults to 8085
-U, --user <user> [env NAGIOS_WEB_SERVER_USER] username to login to nagios CGI scripts, defaults to nagiosadmin
-u, --updates check npm for available updates
-v, --version print the version number and exit
License
-------
MIT License
| 57.878049 | 452 | 0.673831 | eng_Latn | 0.599582 |
9bd1f94b6267041c505207a0be3d423370b623d2 | 1,455 | md | Markdown | _posts/2009-12-20-hunger-the-great-risk.md | BlogToolshed50/aquatours.net | 668e4417c4157fbeb6a5a34c47121541e5118a61 | [
"CC-BY-4.0"
] | null | null | null | _posts/2009-12-20-hunger-the-great-risk.md | BlogToolshed50/aquatours.net | 668e4417c4157fbeb6a5a34c47121541e5118a61 | [
"CC-BY-4.0"
] | null | null | null | _posts/2009-12-20-hunger-the-great-risk.md | BlogToolshed50/aquatours.net | 668e4417c4157fbeb6a5a34c47121541e5118a61 | [
"CC-BY-4.0"
] | null | null | null | ---
id: 35
title: 'Hunger – The Great Risk'
date: 2009-12-20T11:14:49+00:00
author: admin
layout: post
guid: http://aquatours.net/?p=35
permalink: /2009/12/20/hunger-the-great-risk/
categories:
- General
---
It is a matter of deep concern to learn from the UN agency that one out of six people in the world are hungry without proper food. This level is found to historic high due to the global economic recession aggravated by high food prices. These hungry people receive less than 1800 calories per day that is the benchmark level fixed. The undernourished people worldwide live mostly in the developing countries.
According to the UN agency, this scenario is bound to pose greater risk to the society as a whole, leading to social unrest and lack of security. Despite the strong 2009 cereal production and mild retreat in the food prices when compared to the year 2008, it is estimated that there is an increase of 24% in the price of vital food items than 2006. The report given by UN agency indicates that the urban poor are going to be affected much due to this economic scenario.
Sub-Saharan Africa is having the highest hunger rate with 265 million undernourished people. As much as 1.05 billion people world over are said to be hungry that is 11% more than what we had last year. Unless the respective governments do not concentrate on agrarian reforms to feed these hungry lot, it is going to create greater security risk in the world. | 90.9375 | 469 | 0.790378 | eng_Latn | 0.999856 |
9bd2b5d23a1d3c829b861ff449eba5828301efe4 | 4,404 | md | Markdown | _posts/2021-06-13-AlphaGo-AlphaZero-MuZero.md | siatwangmin/siatwangmin.github.io | 9575847884d588ec4232191220efebb87446fae9 | [
"MIT"
] | null | null | null | _posts/2021-06-13-AlphaGo-AlphaZero-MuZero.md | siatwangmin/siatwangmin.github.io | 9575847884d588ec4232191220efebb87446fae9 | [
"MIT"
] | null | null | null | _posts/2021-06-13-AlphaGo-AlphaZero-MuZero.md | siatwangmin/siatwangmin.github.io | 9575847884d588ec4232191220efebb87446fae9 | [
"MIT"
] | null | null | null | ---
layout: post
title: AlphaGo AlphaZero MuZero
subtitle: MuZero
date: 2021-06-13 19:54:00
author: wangmin
header-img: img/home-bg-art.jpg
catalog: true
tags: DeepMind Alpha-Go
---
# AlphaGo, AlphaZero, MuZero
## Mastering Atari, Go, chess and shogi by planning with a learned model
1. 构建一个agent具有规划的能力一直是AI中给一个主要挑战
2. 在有simulator的情况下,Tree based planning methods success,但是在现实过程中,管理环境的动态是非常复杂和未知。
3. lookahead search have achieved remarkable successes in artificial intelligence.
4. RL 2 principal categories:
1. **Model-based reinforcement learning** (RL)11 aims to address this issue
1. 典型做法Markov decision process(MDP)
1. 典型的方法是讲model构建为一个MDP
1. state transition model: 给定action的情况下,预测下一个状态:
2. reward model: 在状态转移过程中的reward.
2. MDP planning algorithms: compute the optimal value function or optimal policy for MDP。
1. value iteration
2. Monte Carlo tree search
2. first learning a model of the environment’s dynamics
1. 1.
2. reconstructing the true environmental state
3. the sequance of full observations
3. then planning with respect to the learned model
2. **model-free RL**方法在Atari 2600上面表现不错
1. 直接与环境进行交互,来学习optimal policy or value fucntions
2. 但是这种方式在要求精确的或者复杂的lookahead的领域表现不好。
5. Here we present the MuZero algorithm, which, by combining a **tree-based search** with **a learned model**, achieves superhuman performance in a range of challenging and visually complex domains, **without any knowledge of their underlying dynamics.**
1. Based on AlphaZero, Powerful search and policy iteration algorithms, but incroporates a learned model into the **training procedure**????
2. Broader set of environments including signle agent domains and non-zero rewards at intermediate time steps.
3. **Main Ideas**: predict those aspects of the future that are directly relevant for planning.
1. 输入当前画面,然后转化为hidden state
2. at each step, the model produces a policy, value fucntion , immdediate reward prediction
3. model it trained end to end with the sole objective of accurately estimante these 3 import quantities, to match the improved policy and value function generated by search, as well as the observed reward.
4. 没有要求模型要精确的记录所有的**hidden state**, 那么就可以丢去很多冗余的信息。
5. Instead, the hidden states are free to represent any state that correctly estimates the policy, value function and reward。
6. Other Methods
1. model-based planning approaches
2. Tree-based planning approaches
## Mastering the game of Go with deep neural networks and tree search
1. State
2. Action
3. Agent
4. Policy $\pi$:
1. Policy function $\pi(a|s) \in [0, 1]$
$$
\pi(a|s) = P(A = a | S = s)
$$
2. it is the probability of taking action A = a given $s$, e.g.,
1. $\pi(left | s) = 0.2$
2. $\pi(right | s) = 0.1$
3. $\pi(up | s) = 0.7$
3. Upon oberving state S = s, the agent's action A can be random
5. Reward
6. State transition
1. state transition can be random
2. Rondomness is from the environment
3. $p(s\prime|s, a) = P(S\prime=s\prime|S=s, A= a)$
7. Randomness is RL
1. Action have randomness
2. State transition have randomness
8. Rewards
9. Returns
1. aka cumulative future reward
$U_t = R_t + R_{t+1} + R_{t+2} + R_{t+3} + ...$
2. Discounted return: aka cumulative siscounted future reward
1. $U_t = R_t + \gamma^1 R_{t+1} + \gamma^2 R_{t+2} + \gamma^3 R_{t+3} + ...$
10. **Action-Value Function**
1. Definition: Action-Value function for policy $\pi$
1. $Q_{\pi}(s_t, a_t) = E[U_t|S_t = s_t, A_t = a_t]$
For policy $\pi, Q_{\pi}(s, a)$ evaluates how good it is for an agent to pick action $a$ while being in state $s$
2. Definition: Optimal Action-value function
1. $Q^*(s_t, a_t) = max_{\pi}Q_{pi}(s_t, a_t)$
11. **State-value function**
1. $V_{\pi}(s_t) = E_A[Q_{\pi}(s_t, A)] = \sum_{a}\pi (a | s_t)*Q_{\pi}(s_t, a)$
For fixed policy $\pi, V_{\pi}(s)$ evaluates how good the situation is in state $s$
$E_s[V_{\pi}(S)]$ evaluates how good the policy $\pi$ is.
12. Example
1. how does AI control the agent?
1. SUppose we have a good policy $\pi (a | s)$
1. Upon observe the state $s_t$
2. random sampling : $a_t \~ () $ | 34.952381 | 254 | 0.670527 | eng_Latn | 0.975352 |
9bd318f4bc2883a6b3002e8032286b1148a223f5 | 3,250 | md | Markdown | docs/code-quality/ca2217-do-not-mark-enums-with-flagsattribute.md | BrainCraze/visualstudio-docs.de-de | 3758c943d5f4eacbdc0d975cb114f287018463dd | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/code-quality/ca2217-do-not-mark-enums-with-flagsattribute.md | BrainCraze/visualstudio-docs.de-de | 3758c943d5f4eacbdc0d975cb114f287018463dd | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/code-quality/ca2217-do-not-mark-enums-with-flagsattribute.md | BrainCraze/visualstudio-docs.de-de | 3758c943d5f4eacbdc0d975cb114f287018463dd | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
title: 'CA2217: Enumerationen mit FlagsAttribute markieren | Microsoft Docs'
ms.custom: ''
ms.date: 11/04/2016
ms.technology:
- vs-ide-code-analysis
ms.topic: conceptual
f1_keywords:
- DoNotMarkEnumsWithFlags
- CA2217
helpviewer_keywords:
- DoNotMarkEnumsWithFlags
- CA2217
ms.assetid: 1b6f626c-66bf-45b0-a3e2-7c41ee9ceda7
author: gewarren
ms.author: gewarren
manager: douge
ms.workload:
- multiple
ms.openlocfilehash: 0a2cdfcf4014d00ca2d975a04a8bb81191a717e0
ms.sourcegitcommit: 6a9d5bd75e50947659fd6c837111a6a547884e2a
ms.translationtype: MT
ms.contentlocale: de-DE
ms.lasthandoff: 04/16/2018
---
# <a name="ca2217-do-not-mark-enums-with-flagsattribute"></a>CA2217: Enumerationen nicht mit FlagsAttribute markieren
|||
|-|-|
|TypeName|DoNotMarkEnumsWithFlags|
|CheckId|CA2217|
|Kategorie|Microsoft.Usage|
|Unterbrechende Änderung|Nicht unterbrechende Änderung|
## <a name="cause"></a>Ursache
Eine extern sichtbare Enumeration wird mit gekennzeichnet <xref:System.FlagsAttribute> und verfügt über ein oder mehr Werte, die keine Potenzen von 2 oder eine Kombination aus den anderen sind Werte für die Enumeration definiert.
## <a name="rule-description"></a>Regelbeschreibung
Eine Enumeration müssen <xref:System.FlagsAttribute> vorhanden, nur, wenn jeder Wert, der in der Enumeration definiert, eine Potenz von zwei ist oder eine Kombination aus Werte definierten.
## <a name="how-to-fix-violations"></a>Behandeln von Verstößen
Um einen Verstoß gegen diese Regel zu beheben, entfernen Sie <xref:System.FlagsAttribute> aus der Enumeration.
## <a name="when-to-suppress-warnings"></a>Wann sollten Warnungen unterdrückt werden?
Unterdrücken Sie keine Warnung dieser Regel.
## <a name="example"></a>Beispiel
Das folgende Beispiel zeigt eine Enumeration, die Farbe, mit dem Wert 3, also weder eine Potenz von 2 noch eine Kombination der definierten Werte. Die Color-Enumeration sollten nicht gekennzeichnet werden, mit der <xref:System.FlagsAttribute>.
[!code-cpp[FxCop.Usage.EnumNoFlags#1](../code-quality/codesnippet/CPP/ca2217-do-not-mark-enums-with-flagsattribute_1.cpp)]
[!code-csharp[FxCop.Usage.EnumNoFlags#1](../code-quality/codesnippet/CSharp/ca2217-do-not-mark-enums-with-flagsattribute_1.cs)]
[!code-vb[FxCop.Usage.EnumNoFlags#1](../code-quality/codesnippet/VisualBasic/ca2217-do-not-mark-enums-with-flagsattribute_1.vb)]
## <a name="example"></a>Beispiel
Das folgende Beispiel zeigt eine Enumeration, Tage, die die Anforderungen für eine mit das System.FlagsAttribute markiert werden erfüllt.
[!code-cpp[FxCop.Usage.EnumNoFlags2#1](../code-quality/codesnippet/CPP/ca2217-do-not-mark-enums-with-flagsattribute_2.cpp)]
[!code-csharp[FxCop.Usage.EnumNoFlags2#1](../code-quality/codesnippet/CSharp/ca2217-do-not-mark-enums-with-flagsattribute_2.cs)]
[!code-vb[FxCop.Usage.EnumNoFlags2#1](../code-quality/codesnippet/VisualBasic/ca2217-do-not-mark-enums-with-flagsattribute_2.vb)]
## <a name="related-rules"></a>Verwandte Regeln
[CA1027: Enumerationen mit FlagsAttribute markieren](../code-quality/ca1027-mark-enums-with-flagsattribute.md)
## <a name="see-also"></a>Siehe auch
<xref:System.FlagsAttribute?displayProperty=fullName> | 50.78125 | 246 | 0.770462 | deu_Latn | 0.809786 |
9bd3adf071e5c09b46e830a595834561f26e6978 | 2,884 | md | Markdown | ios/Readme.md | angrybear11/firebase-auth-migration-helpers | 49c04bce65130e03b2f4bc7eb76c85d26904e698 | [
"Apache-2.0"
] | 14 | 2016-06-02T21:48:01.000Z | 2018-03-01T09:02:55.000Z | ios/Readme.md | angrybear11/firebase-auth-migration-helpers | 49c04bce65130e03b2f4bc7eb76c85d26904e698 | [
"Apache-2.0"
] | 8 | 2016-06-23T18:38:39.000Z | 2017-08-18T10:54:35.000Z | ios/Readme.md | angrybear11/firebase-auth-migration-helpers | 49c04bce65130e03b2f4bc7eb76c85d26904e698 | [
"Apache-2.0"
] | 9 | 2016-06-23T18:40:52.000Z | 2018-06-20T21:41:57.000Z | FIRAuthMigrator
===============
An Objective-C code sample for migrating logged in users from a legacy Firebase
iOS SDK to the new Firebase SDK.
Pre-requisites
--------------
Before using this code, you must add the Firebase/Auth modules to your project.
Getting Started
---------------
1. Add the FIRAuthMigrator.h and FIRAuthMigrator.m to your project.
2. If you are using Swift, add `#import "FIRAuthMigrator.h"` to your Bridging
Header file. If you do not have a Bridging Header file, create one:
1. Create a new file call `{Project}-Bridging-Header.h`.
1. File > New > File...
2. iOS > Source > Header File
3. Enter the file name and click `Create`.
2. In your project's `Build Settings`, click `All`, and enter the path to
your briding header file for `Objective-C Bridging Header`.
3. In your AppDelegate's `application:didFinishLaunchingWithOptions:` method,
call `migrateAuth:` to log in any user who was previously logged in with the
legacy SDK.
```objective-c
// Objective-C
[[FIRAuthMigrator authMigrator] migrate:^(FIRUser *user, NSError *error) {
if (error != nil) {
// There was an error.
return;
}
if (user == nil) {
// No user was logged in.
return;
}
// user is logged in
}];
```
```swift
// Swift
FIRAuthMigrator.authMigrator().migrate() { (user, error) in
if error != nil {
// There was an error.
return
}
if user == nil {
// No user was logged in.
return
}
// user is logged in
}
```
4. Whenever you log in a user, call `clearLegacyAuth`. This is a precaution
to make sure that a user from a legacy SDK never overrides a newer log in.
```objective-c
// Objective-C
[[FIRAuthMigrator authMigrator] clearLegacyAuth];
```
```swift
// Swift
FIRAuthMigrator.authMigrator().clearLegacyAuth()
```
Support
-------
If you've found an error in this sample, please file an issue:
https://github.com/firebase/firebase-auth-migration-helpers/issues
Patches are encouraged, and may be submitted by forking this project and
submitting a pull request through GitHub.
License
-------
Copyright 2016 Google, Inc.
Licensed to the Apache Software Foundation (ASF) under one or more contributor
license agreements. See the NOTICE file distributed with this work for
additional information regarding copyright ownership. The ASF licenses this
file to you under the Apache License, Version 2.0 (the "License"); you may not
use this file except in compliance with the License. You may obtain a copy of
the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS, WITHOUT
WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the
License for the specific language governing permissions and limitations under
the License.
| 31.692308 | 79 | 0.713939 | eng_Latn | 0.988746 |
9bd566b3cf118673251e97be56ebd65efdfa7ee8 | 438 | md | Markdown | README.md | ryujt/pagination | 0308febcf359b03e70f3502e106eea406e8be912 | [
"MIT"
] | null | null | null | README.md | ryujt/pagination | 0308febcf359b03e70f3502e106eea406e8be912 | [
"MIT"
] | null | null | null | README.md | ryujt/pagination | 0308febcf359b03e70f3502e106eea406e8be912 | [
"MIT"
] | null | null | null | # pagination
웹에서 사용할 수 있는 pagination 오픈소스 라이브러리 두 개에 대한 설명입니다.
***
첫 번째 라이브러리는 단순하면서 비교적 사용방법이 쉬운 luckmoshy 라이브러리입니다.
아래 링크를 따라가시면 소스와 상세 정보를 얻을 수 있습니다.
* [https://github.com/luckmoshy/luckmoshypagnation.js](https://github.com/luckmoshy/luckmoshypagnation.js)
***
두 번째 라이브러리는 luckmoshy 보다는 자주 사용되는 pagination.js입니다.
기능과 옵션이 조금 더 다양한 편입니다.
* [https://pagination.js.org/](https://pagination.js.org/)
***
아래는 동영상 설명 링크입니다.
* [작성중]()
| 20.857143 | 106 | 0.716895 | kor_Hang | 1.00001 |
9bd85361c7432626e0366960d31738e075e2f828 | 71,611 | md | Markdown | p/pfaendfreigrbek_2011/index.md | nnworkspace/gesetze | 1d9a25fdfdd9468952f739736066c1ef76069051 | [
"Unlicense"
] | 1 | 2020-06-20T11:34:20.000Z | 2020-06-20T11:34:20.000Z | p/pfaendfreigrbek_2011/index.md | nagy/gesetze | 77abca2ceea3b7b89ea70afb13b5dd55415eb124 | [
"Unlicense"
] | null | null | null | p/pfaendfreigrbek_2011/index.md | nagy/gesetze | 77abca2ceea3b7b89ea70afb13b5dd55415eb124 | [
"Unlicense"
] | null | null | null | ---
Title: Bekanntmachung zu § 850c der Zivilprozessordnung
jurabk: PfändfreiGrBek 2011
layout: default
origslug: pf_ndfreigrbek_2011
slug: pfaendfreigrbek_2011
---
# Bekanntmachung zu § 850c der Zivilprozessordnung (PfändfreiGrBek 2011)
Ausfertigungsdatum
: 2011-05-09
Fundstelle
: BGBl I: 2011, 825
## (XXXX)
Auf Grund des § 850c Absatz 2a Satz 2 der Zivilprozessordnung, der
durch Artikel 1 Nummer 4 Buchstabe c des Gesetzes vom 13. Dezember
2001 (BGBl. I S. 3638) eingefügt worden ist, wird bekannt gemacht:
1. Die unpfändbaren Beträge nach § 850c Absatz 1 und 2 Satz 2 der
Zivilprozessordnung erhöhen sich zum 1. Juli 2011
in Absatz 1 Satz 1
* von 985,15 auf 1 028,89 Euro monatlich,
von 226,72 auf 236,79 Euro wöchentlich,
von 45,34 auf 47,36 Euro täglich,
in Absatz 1 Satz 2
* von 2 182,15 auf 2 279,03 Euro monatlich,
von 502,20 auf 524,49 Euro wöchentlich,
von 100,44 auf 104,90 Euro täglich,
von 370,76 auf 387,22 Euro monatlich,
von 85,32 auf 89,11 Euro wöchentlich,
von 17,06 auf 17,82 Euro täglich,
von 206,56 auf 215,73 Euro monatlich,
von 47,54 auf 49,65 Euro wöchentlich,
von 9,51 auf 9,93 Euro täglich,
in Absatz 2 Satz 2
* von 3 020,06 auf 3 154,15 Euro monatlich,
von 695,03 auf 725,89 Euro wöchentlich,
von 139,01 auf 145,18 Euro täglich,
2. Die unpfändbaren Beträge nach § 850f Absatz 3 Satz 1 und 2 der
Zivilprozessordnung erhöhen sich
* von 2 985,00 auf 3 117,53 Euro monatlich,
von 678,70 auf 708,83 Euro wöchentlich,
von 131,25 auf 137,08 Euro täglich.
Die ab 1. Juli 2011 geltenden Pfändungsfreibeträge ergeben sich im
Übrigen aus den als Anhang abgedruckten Tabellen.
## Schlussformel
Die Bundesministerin der Justiz
## Anhang
(Fundstelle: BGBl. I 2011, 826 - 840)
Auszahlung für Monate
##
* *
* Pfändbarer Betrag bei
Unterhaltspflicht für ... Personen
* * Nettolohn
monatlich
* 0
* 1
* 2
* 3
* 4
* 5 und
mehr
* * in Euro
* * bis 1 029,99
* –
* –
* –
* –
* –
* –
* * 1 030,00 bis 1 039,99
* 0,78
* –
* –
* –
* –
* –
* * 1 040,00 bis 1 049,99
* 7,78
* –
* –
* –
* –
* –
* * 1 050,00 bis 1 059,99
* 14,78
* –
* –
* –
* –
* –
* * 1 060,00 bis 1 069,99
* 21,78
* –
* –
* –
* –
* –
* * 1 070,00 bis 1 079,99
* 28,78
* –
* –
* –
* –
* –
* * 1 080,00 bis 1 089,99
* 35,78
* –
* –
* –
* –
* –
* * 1 090,00 bis 1 099,99
* 42,78
* –
* –
* –
* –
* –
* * 1 100,00 bis 1 109,99
* 49,78
* –
* –
* –
* –
* –
* * 1 110,00 bis 1 119,99
* 56,78
* –
* –
* –
* –
* –
* * 1 120,00 bis 1 129,99
* 63,78
* –
* –
* –
* –
* –
* * 1 130,00 bis 1 139,99
* 70,78
* –
* –
* –
* –
* –
* * 1 140,00 bis 1 149,99
* 77,78
* –
* –
* –
* –
* –
* * 1 150,00 bis 1 159,99
* 84,78
* –
* –
* –
* –
* –
* * 1 160,00 bis 1 169,99
* 91,78
* –
* –
* –
* –
* –
* * 1 170,00 bis 1 179,99
* 98,78
* –
* –
* –
* –
* –
* * 1 180,00 bis 1 189,99
* 105,78
* –
* –
* –
* –
* –
* * 1 190,00 bis 1 199,99
* 112,78
* –
* –
* –
* –
* –
* * 1 200,00 bis 1 209,99
* 119,78
* –
* –
* –
* –
* –
* * 1 210,00 bis 1 219,99
* 126,78
* –
* –
* –
* –
* –
* * 1 220,00 bis 1 229,99
* 133,78
* –
* –
* –
* –
* –
* * 1 230,00 bis 1 239,99
* 140,78
* –
* –
* –
* –
* –
* * 1 240,00 bis 1 249,99
* 147,78
* –
* –
* –
* –
* –
* * 1 250,00 bis 1 259,99
* 154,78
* –
* –
* –
* –
* –
* * 1 260,00 bis 1 269,99
* 161,78
* –
* –
* –
* –
* –
* * 1 270,00 bis 1 279,99
* 168,78
* –
* –
* –
* –
* –
* * 1 280,00 bis 1 289,99
* 175,78
* –
* –
* –
* –
* –
* * 1 290,00 bis 1 299,99
* 182,78
* –
* –
* –
* –
* –
* * 1 300,00 bis 1 309,99
* 189,78
* –
* –
* –
* –
* –
* * 1 310,00 bis 1 319,99
* 196,78
* –
* –
* –
* –
* –
* * 1 320,00 bis 1 329,99
* 203,78
* –
* –
* –
* –
* –
* * 1 330,00 bis 1 339,99
* 210,78
* –
* –
* –
* –
* –
* * 1 340,00 bis 1 349,99
* 217,78
* –
* –
* –
* –
* –
* * 1 350,00 bis 1 359,99
* 224,78
* –
* –
* –
* –
* –
* * 1 360,00 bis 1 369,99
* 231,78
* –
* –
* –
* –
* –
* * 1 370,00 bis 1 379,99
* 238,78
* –
* –
* –
* –
* –
* * 1 380,00 bis 1 389,99
* 245,78
* –
* –
* –
* –
* –
* * 1 390,00 bis 1 399,99
* 252,78
* –
* –
* –
* –
* –
* * 1 400,00 bis 1 409,99
* 259,78
* –
* –
* –
* –
* –
* * 1 410,00 bis 1 419,99
* 266,78
* –
* –
* –
* –
* –
* * 1 420,00 bis 1 429,99
* 273,78
* 1,95
* –
* –
* –
* –
* * 1 430,00 bis 1 439,99
* 280,78
* 6,95
* –
* –
* –
* –
* * 1 440,00 bis 1 449,99
* 287,78
* 11,95
* –
* –
* –
* –
* * 1 450,00 bis 1 459,99
* 294,78
* 16,95
* –
* –
* –
* –
* * 1 460,00 bis 1 469,99
* 301,78
* 21,95
* –
* –
* –
* –
* * 1 470,00 bis 1 479,99
* 308,78
* 26,95
* –
* –
* –
* –
* * 1 480,00 bis 1 489,99
* 315,78
* 31,95
* –
* –
* –
* –
* * 1 490,00 bis 1 499,99
* 322,78
* 36,95
* –
* –
* –
* –
* * 1 500,00 bis 1 509,99
* 329,78
* 41,95
* –
* –
* –
* –
* * 1 510,00 bis 1 519,99
* 336,78
* 46,95
* –
* –
* –
* –
* * 1 520,00 bis 1 529,99
* 343,78
* 51,95
* –
* –
* –
* –
* * 1 530,00 bis 1 539,99
* 350,78
* 56,95
* –
* –
* –
* –
* * 1 540,00 bis 1 549,99
* 357,78
* 61,95
* –
* –
* –
* –
* * 1 550,00 bis 1 559,99
* 364,78
* 66,95
* –
* –
* –
* –
* * 1 560,00 bis 1 569,99
* 371,78
* 71,95
* –
* –
* –
* –
* * 1 570,00 bis 1 579,99
* 378,78
* 76,95
* –
* –
* –
* –
* * 1 580,00 bis 1 589,99
* 385,78
* 81,95
* –
* –
* –
* –
* * 1 590,00 bis 1 599,99
* 392,78
* 86,95
* –
* –
* –
* –
* * 1 600,00 bis 1 609,99
* 399,78
* 91,95
* –
* –
* –
* –
* * 1 610,00 bis 1 619,99
* 406,78
* 96,95
* –
* –
* –
* –
* * 1 620,00 bis 1 629,99
* 413,78
* 101,95
* –
* –
* –
* –
* * 1 630,00 bis 1 639,99
* 420,78
* 106,95
* –
* –
* –
* –
* * 1 640,00 bis 1 649,99
* 427,78
* 111,95
* 3,26
* –
* –
* –
* * 1 650,00 bis 1 659,99
* 434,78
* 116,95
* 7,26
* –
* –
* –
* * 1 660,00 bis 1 669,99
* 441,78
* 121,95
* 11,26
* –
* –
* –
* * 1 670,00 bis 1 679,99
* 448,78
* 126,95
* 15,26
* –
* –
* –
* * 1 680,00 bis 1 689,99
* 455,78
* 131,95
* 19,26
* –
* –
* –
* * 1 690,00 bis 1 699,99
* 462,78
* 136,95
* 23,26
* –
* –
* –
* * 1 700,00 bis 1 709,99
* 469,78
* 141,95
* 27,26
* –
* –
* –
* * 1 710,00 bis 1 719,99
* 476,78
* 146,95
* 31,26
* –
* –
* –
* * 1 720,00 bis 1 729,99
* 483,78
* 151,95
* 35,26
* –
* –
* –
* * 1 730,00 bis 1 739,99
* 490,78
* 156,95
* 39,26
* –
* –
* –
* * 1 740,00 bis 1 749,99
* 497,78
* 161,95
* 43,26
* –
* –
* –
* * 1 750,00 bis 1 759,99
* 504,78
* 166,95
* 47,26
* –
* –
* –
* * 1 760,00 bis 1 769,99
* 511,78
* 171,95
* 51,26
* –
* –
* –
* * 1 770,00 bis 1 779,99
* 518,78
* 176,95
* 55,26
* –
* –
* –
* * 1 780,00 bis 1 789,99
* 525,78
* 181,95
* 59,26
* –
* –
* –
* * 1 790,00 bis 1 799,99
* 532,78
* 186,95
* 63,26
* –
* –
* –
* * 1 800,00 bis 1 809,99
* 539,78
* 191,95
* 67,26
* –
* –
* –
* * 1 810,00 bis 1 819,99
* 546,78
* 196,95
* 71,26
* –
* –
* –
* * 1 820,00 bis 1 829,99
* 553,78
* 201,95
* 75,26
* –
* –
* –
* * 1 830,00 bis 1 839,99
* 560,78
* 206,95
* 79,26
* –
* –
* –
* * 1 840,00 bis 1 849,99
* 567,78
* 211,95
* 83,26
* –
* –
* –
* * 1 850,00 bis 1 859,99
* 574,78
* 216,95
* 87,26
* 0,73
* –
* –
* * 1 860,00 bis 1 869,99
* 581,78
* 221,95
* 91,26
* 3,73
* –
* –
* * 1 870,00 bis 1 879,99
* 588,78
* 226,95
* 95,26
* 6,73
* –
* –
* * 1 880,00 bis 1 889,99
* 595,78
* 231,95
* 99,26
* 9,73
* –
* –
* * 1 890,00 bis 1 899,99
* 602,78
* 236,95
* 103,26
* 12,73
* –
* –
* * 1 900,00 bis 1 909,99
* 609,78
* 241,95
* 107,26
* 15,73
* –
* –
* * 1 910,00 bis 1 919,99
* 616,78
* 246,95
* 111,26
* 18,73
* –
* –
* * 1 920,00 bis 1 929,99
* 623,78
* 251,95
* 115,26
* 21,73
* –
* –
* * 1 930,00 bis 1 939,99
* 630,78
* 256,95
* 119,26
* 24,73
* –
* –
* * 1 940,00 bis 1 949,99
* 637,78
* 261,95
* 123,26
* 27,73
* –
* –
* * 1 950,00 bis 1 959,99
* 644,78
* 266,95
* 127,26
* 30,73
* –
* –
* * 1 960,00 bis 1 969,99
* 651,78
* 271,95
* 131,26
* 33,73
* –
* –
* * 1 970,00 bis 1 979,99
* 658,78
* 276,95
* 135,26
* 36,73
* –
* –
* * 1 980,00 bis 1 989,99
* 665,78
* 281,95
* 139,26
* 39,73
* –
* –
* * 1 990,00 bis 1 999,99
* 672,78
* 286,95
* 143,26
* 42,73
* –
* –
* * 2 000,00 bis 2 009,99
* 679,78
* 291,95
* 147,26
* 45,73
* –
* –
* * 2 010,00 bis 2 019,99
* 686,78
* 296,95
* 151,26
* 48,73
* –
* –
* * 2 020,00 bis 2 029,99
* 693,78
* 301,95
* 155,26
* 51,73
* –
* –
* * 2 030,00 bis 2 039,99
* 700,78
* 306,95
* 159,26
* 54,73
* –
* –
* * 2 040,00 bis 2 049,99
* 707,78
* 311,95
* 163,26
* 57,73
* –
* –
* * 2 050,00 bis 2 059,99
* 714,78
* 316,95
* 167,26
* 60,73
* –
* –
* * 2 060,00 bis 2 069,99
* 721,78
* 321,95
* 171,26
* 63,73
* –
* –
* * 2 070,00 bis 2 079,99
* 728,78
* 326,95
* 175,26
* 66,73
* 1,34
* –
* * 2 080,00 bis 2 089,99
* 735,78
* 331,95
* 179,26
* 69,73
* 3,34
* –
* * 2 090,00 bis 2 099,99
* 742,78
* 336,95
* 183,26
* 72,73
* 5,34
* –
* * 2 100,00 bis 2 109,99
* 749,78
* 341,95
* 187,26
* 75,73
* 7,34
* –
* * 2 110,00 bis 2 119,99
* 756,78
* 346,95
* 191,26
* 78,73
* 9,34
* –
* * 2 120,00 bis 2 129,99
* 763,78
* 351,95
* 195,26
* 81,73
* 11,34
* –
* * 2 130,00 bis 2 139,99
* 770,78
* 356,95
* 199,26
* 84,73
* 13,34
* –
* * 2 140,00 bis 2 149,99
* 777,78
* 361,95
* 203,26
* 87,73
* 15,34
* –
* * 2 150,00 bis 2 159,99
* 784,78
* 366,95
* 207,26
* 90,73
* 17,34
* –
* * 2 160,00 bis 2 169,99
* 791,78
* 371,95
* 211,26
* 93,73
* 19,34
* –
* * 2 170,00 bis 2 179,99
* 798,78
* 376,95
* 215,26
* 96,73
* 21,34
* –
* * 2 180,00 bis 2 189,99
* 805,78
* 381,95
* 219,26
* 99,73
* 23,34
* –
* * 2 190,00 bis 2 199,99
* 812,78
* 386,95
* 223,26
* 102,73
* 25,34
* –
* * 2 200,00 bis 2 209,99
* 819,78
* 391,95
* 227,26
* 105,73
* 27,34
* –
* * 2 210,00 bis 2 219,99
* 826,78
* 396,95
* 231,26
* 108,73
* 29,34
* –
* * 2 220,00 bis 2 229,99
* 833,78
* 401,95
* 235,26
* 111,73
* 31,34
* –
* * 2 230,00 bis 2 239,99
* 840,78
* 406,95
* 239,26
* 114,73
* 33,34
* –
* * 2 240,00 bis 2 249,99
* 847,78
* 411,95
* 243,26
* 117,73
* 35,34
* –
* * 2 250,00 bis 2 259,99
* 854,78
* 416,95
* 247,26
* 120,73
* 37,34
* –
* * 2 260,00 bis 2 269,99
* 861,78
* 421,95
* 251,26
* 123,73
* 39,34
* –
* * 2 270,00 bis 2 279,99
* 868,78
* 426,95
* 255,26
* 126,73
* 41,34
* –
* * 2 280,00 bis 2 289,99
* 875,78
* 431,95
* 259,26
* 129,73
* 43,34
* 0,10
* * 2 290,00 bis 2 299,99
* 882,78
* 436,95
* 263,26
* 132,73
* 45,34
* 1,10
* * 2 300,00 bis 2 309,99
* 889,78
* 441,95
* 267,26
* 135,73
* 47,34
* 2,10
* * 2 310,00 bis 2 319,99
* 896,78
* 446,95
* 271,26
* 138,73
* 49,34
* 3,10
* * 2 320,00 bis 2 329,99
* 903,78
* 451,95
* 275,26
* 141,73
* 51,34
* 4,10
* * 2 330,00 bis 2 339,99
* 910,78
* 456,95
* 279,26
* 144,73
* 53,34
* 5,10
* * 2 340,00 bis 2 349,99
* 917,78
* 461,95
* 283,26
* 147,73
* 55,34
* 6,10
* * 2 350,00 bis 2 359,99
* 924,78
* 466,95
* 287,26
* 150,73
* 57,34
* 7,10
* * 2 360,00 bis 2 369,99
* 931,78
* 471,95
* 291,26
* 153,73
* 59,34
* 8,10
* * 2 370,00 bis 2 379,99
* 938,78
* 476,95
* 295,26
* 156,73
* 61,34
* 9,10
* * 2 380,00 bis 2 389,99
* 945,78
* 481,95
* 299,26
* 159,73
* 63,34
* 10,10
* * 2 390,00 bis 2 399,99
* 952,78
* 486,95
* 303,26
* 162,73
* 65,34
* 11,10
* * 2 400,00 bis 2 409,99
* 959,78
* 491,95
* 307,26
* 165,73
* 67,34
* 12,10
* * 2 410,00 bis 2 419,99
* 966,78
* 496,95
* 311,26
* 168,73
* 69,34
* 13,10
* * 2 420,00 bis 2 429,99
* 973,78
* 501,95
* 315,26
* 171,73
* 71,34
* 14,10
* * 2 430,00 bis 2 439,99
* 980,78
* 506,95
* 319,26
* 174,73
* 73,34
* 15,10
* * 2 440,00 bis 2 449,99
* 987,78
* 511,95
* 323,26
* 177,73
* 75,34
* 16,10
* * 2 450,00 bis 2 459,99
* 994,78
* 516,95
* 327,26
* 180,73
* 77,34
* 17,10
* * 2 460,00 bis 2 469,99
* 1 001,78
* 521,95
* 331,26
* 183,73
* 79,34
* 18,10
* * 2 470,00 bis 2 479,99
* 1 008,78
* 526,95
* 335,26
* 186,73
* 81,34
* 19,10
* * 2 480,00 bis 2 489,99
* 1 015,78
* 531,95
* 339,26
* 189,73
* 83,34
* 20,10
* * 2 490,00 bis 2 499,99
* 1 022,78
* 536,95
* 343,26
* 192,73
* 85,34
* 21,10
* * 2 500,00 bis 2 509,99
* 1 029,78
* 541,95
* 347,26
* 195,73
* 87,34
* 22,10
* * 2 510,00 bis 2 519,99
* 1 036,78
* 546,95
* 351,26
* 198,73
* 89,34
* 23,10
* * 2 520,00 bis 2 529,99
* 1 043,78
* 551,95
* 355,26
* 201,73
* 91,34
* 24,10
* * 2 530,00 bis 2 539,99
* 1 050,78
* 556,95
* 359,26
* 204,73
* 93,34
* 25,10
* * 2 540,00 bis 2 549,99
* 1 057,78
* 561,95
* 363,26
* 207,73
* 95,34
* 26,10
* * 2 550,00 bis 2 559,99
* 1 064,78
* 566,95
* 367,26
* 210,73
* 97,34
* 27,10
* * 2 560,00 bis 2 569,99
* 1 071,78
* 571,95
* 371,26
* 213,73
* 99,34
* 28,10
* * 2 570,00 bis 2 579,99
* 1 078,78
* 576,95
* 375,26
* 216,73
* 101,34
* 29,10
* * 2 580,00 bis 2 589,99
* 1 085,78
* 581,95
* 379,26
* 219,73
* 103,34
* 30,10
* * 2 590,00 bis 2 599,99
* 1 092,78
* 586,95
* 383,26
* 222,73
* 105,34
* 31,10
* * 2 600,00 bis 2 609,99
* 1 099,78
* 591,95
* 387,26
* 225,73
* 107,34
* 32,10
* * 2 610,00 bis 2 619,99
* 1 106,78
* 596,95
* 391,26
* 228,73
* 109,34
* 33,10
* * 2 620,00 bis 2 629,99
* 1 113,78
* 601,95
* 395,26
* 231,73
* 111,34
* 34,10
* * 2 630,00 bis 2 639,99
* 1 120,78
* 606,95
* 399,26
* 234,73
* 113,34
* 35,10
* * 2 640,00 bis 2 649,99
* 1 127,78
* 611,95
* 403,26
* 237,73
* 115,34
* 36,10
* * 2 650,00 bis 2 659,99
* 1 134,78
* 616,95
* 407,26
* 240,73
* 117,34
* 37,10
* * 2 660,00 bis 2 669,99
* 1 141,78
* 621,95
* 411,26
* 243,73
* 119,34
* 38,10
* * 2 670,00 bis 2 679,99
* 1 148,78
* 626,95
* 415,26
* 246,73
* 121,34
* 39,10
* * 2 680,00 bis 2 689,99
* 1 155,78
* 631,95
* 419,26
* 249,73
* 123,34
* 40,10
* * 2 690,00 bis 2 699,99
* 1 162,78
* 636,95
* 423,26
* 252,73
* 125,34
* 41,10
* * 2 700,00 bis 2 709,99
* 1 169,78
* 641,95
* 427,26
* 255,73
* 127,34
* 42,10
* * 2 710,00 bis 2 719,99
* 1 176,78
* 646,95
* 431,26
* 258,73
* 129,34
* 43,10
* * 2 720,00 bis 2 729,99
* 1 183,78
* 651,95
* 435,26
* 261,73
* 131,34
* 44,10
* * 2 730,00 bis 2 739,99
* 1 190,78
* 656,95
* 439,26
* 264,73
* 133,34
* 45,10
* * 2 740,00 bis 2 749,99
* 1 197,78
* 661,95
* 443,26
* 267,73
* 135,34
* 46,10
* * 2 750,00 bis 2 759,99
* 1 204,78
* 666,95
* 447,26
* 270,73
* 137,34
* 47,10
* * 2 760,00 bis 2 769,99
* 1 211,78
* 671,95
* 451,26
* 273,73
* 139,34
* 48,10
* * 2 770,00 bis 2 779,99
* 1 218,78
* 676,95
* 455,26
* 276,73
* 141,34
* 49,10
* * 2 780,00 bis 2 789,99
* 1 225,78
* 681,95
* 459,26
* 279,73
* 143,34
* 50,10
* * 2 790,00 bis 2 799,99
* 1 232,78
* 686,95
* 463,26
* 282,73
* 145,34
* 51,10
* * 2 800,00 bis 2 809,99
* 1 239,78
* 691,95
* 467,26
* 285,73
* 147,34
* 52,10
* * 2 810,00 bis 2 819,99
* 1 246,78
* 696,95
* 471,26
* 288,73
* 149,34
* 53,10
* * 2 820,00 bis 2 829,99
* 1 253,78
* 701,95
* 475,26
* 291,73
* 151,34
* 54,10
* * 2 830,00 bis 2 839,99
* 1 260,78
* 706,95
* 479,26
* 294,73
* 153,34
* 55,10
* * 2 840,00 bis 2 849,99
* 1 267,78
* 711,95
* 483,26
* 297,73
* 155,34
* 56,10
* * 2 850,00 bis 2 859,99
* 1 274,78
* 716,95
* 487,26
* 300,73
* 157,34
* 57,10
* * 2 860,00 bis 2 869,99
* 1 281,78
* 721,95
* 491,26
* 303,73
* 159,34
* 58,10
* * 2 870,00 bis 2 879,99
* 1 288,78
* 726,95
* 495,26
* 306,73
* 161,34
* 59,10
* * 2 880,00 bis 2 889,99
* 1 295,78
* 731,95
* 499,26
* 309,73
* 163,34
* 60,10
* * 2 890,00 bis 2 899,99
* 1 302,78
* 736,95
* 503,26
* 312,73
* 165,34
* 61,10
* * 2 900,00 bis 2 909,99
* 1 309,78
* 741,95
* 507,26
* 315,73
* 167,34
* 62,10
* * 2 910,00 bis 2 919,99
* 1 316,78
* 746,95
* 511,26
* 318,73
* 169,34
* 63,10
* * 2 920,00 bis 2 929,99
* 1 323,78
* 751,95
* 515,26
* 321,73
* 171,34
* 64,10
* * 2 930,00 bis 2 939,99
* 1 330,78
* 756,95
* 519,26
* 324,73
* 173,34
* 65,10
* * 2 940,00 bis 2 949,99
* 1 337,78
* 761,95
* 523,26
* 327,73
* 175,34
* 66,10
* * 2 950,00 bis 2 959,99
* 1 344,78
* 766,95
* 527,26
* 330,73
* 177,34
* 67,10
* * 2 960,00 bis 2 969,99
* 1 351,78
* 771,95
* 531,26
* 333,73
* 179,34
* 68,10
* * 2 970,00 bis 2 979,99
* 1 358,78
* 776,95
* 535,26
* 336,73
* 181,34
* 69,10
* * 2 980,00 bis 2 989,99
* 1 365,78
* 781,95
* 539,26
* 339,73
* 183,34
* 70,10
* * 2 990,00 bis 2 999,99
* 1 372,78
* 786,95
* 543,26
* 342,73
* 185,34
* 71,10
* * 3 000,00 bis 3 009,99
* 1 379,78
* 791,95
* 547,26
* 345,73
* 187,34
* 72,10
* * 3 010,00 bis 3 019,99
* 1 386,78
* 796,95
* 551,26
* 348,73
* 189,34
* 73,10
* * 3 020,00 bis 3 029,99
* 1 393,78
* 801,95
* 555,26
* 351,73
* 191,34
* 74,10
* * 3 030,00 bis 3 039,99
* 1 400,78
* 806,95
* 559,26
* 354,73
* 193,34
* 75,10
* * 3 040,00 bis 3 049,99
* 1 407,78
* 811,95
* 563,26
* 357,73
* 195,34
* 76,10
* * 3 050,00 bis 3 059,99
* 1 414,78
* 816,95
* 567,26
* 360,73
* 197,34
* 77,10
* * 3 060,00 bis 3 069,99
* 1 421,78
* 821,95
* 571,26
* 363,73
* 199,34
* 78,10
* * 3 070,00 bis 3 079,99
* 1 428,78
* 826,95
* 575,26
* 366,73
* 201,34
* 79,10
* * 3 080,00 bis 3 089,99
* 1 435,78
* 831,95
* 579,26
* 369,73
* 203,34
* 80,10
* * 3 090,00 bis 3 099,99
* 1 442,78
* 836,95
* 583,26
* 372,73
* 205,34
* 81,10
* * 3 100,00 bis 3 109,99
* 1 449,78
* 841,95
* 587,26
* 375,73
* 207,34
* 82,10
* * 3 110,00 bis 3 119,99
* 1 456,78
* 846,95
* 591,26
* 378,73
* 209,34
* 83,10
* * 3 120,00 bis 3 129,99
* 1 463,78
* 851,95
* 595,26
* 381,73
* 211,34
* 84,10
* * 3 130,00 bis 3 139,99
* 1 470,78
* 856,95
* 599,26
* 384,73
* 213,34
* 85,10
* * 3 140,00 bis 3 149,99
* 1 477,78
* 861,95
* 603,26
* 387,73
* 215,34
* 86,10
* * 3 150,00 bis 3 154,15
* 1 484,78
* 866,95
* 607,26
* 390,73
* 217,34
* 87,10
* * Der Mehrbetrag über 3 154,15 Euro ist voll pfändbar.
Auszahlung für Wochen
##
* *
* Pfändbarer Betrag bei
Unterhaltspflicht für ... Personen
* * Nettolohn
wöchentlich
* 0
* 1
* 2
* 3
* 4
* 5 und
mehr
* * in Euro
* * bis 237,49
* –
* –
* –
* –
* –
* –
* * 237,50 bis 239,99
* 0,50
* –
* –
* –
* –
* –
* * 240,00 bis 242,49
* 2,25
* –
* –
* –
* –
* –
* * 242,50 bis 244,99
* 4,00
* –
* –
* –
* –
* –
* * 245,00 bis 247,49
* 5,75
* –
* –
* –
* –
* –
* * 247,50 bis 249,99
* 7,50
* –
* –
* –
* –
* –
* * 250,00 bis 252,49
* 9,25
* –
* –
* –
* –
* –
* * 252,50 bis 254,99
* 11,00
* –
* –
* –
* –
* –
* * 255,00 bis 257,49
* 12,75
* –
* –
* –
* –
* –
* * 257,50 bis 259,99
* 14,50
* –
* –
* –
* –
* –
* * 260,00 bis 262,49
* 16,25
* –
* –
* –
* –
* –
* * 262,50 bis 264,99
* 18,00
* –
* –
* –
* –
* –
* * 265,00 bis 267,49
* 19,75
* –
* –
* –
* –
* –
* * 267,50 bis 269,99
* 21,50
* –
* –
* –
* –
* –
* * 270,00 bis 272,49
* 23,25
* –
* –
* –
* –
* –
* * 272,50 bis 274,99
* 25,00
* –
* –
* –
* –
* –
* * 275,00 bis 277,49
* 26,75
* –
* –
* –
* –
* –
* * 277,50 bis 279,99
* 28,50
* –
* –
* –
* –
* –
* * 280,00 bis 282,49
* 30,25
* –
* –
* –
* –
* –
* * 282,50 bis 284,99
* 32,00
* –
* –
* –
* –
* –
* * 285,00 bis 287,49
* 33,75
* –
* –
* –
* –
* –
* * 287,50 bis 289,99
* 35,50
* –
* –
* –
* –
* –
* * 290,00 bis 292,49
* 37,25
* –
* –
* –
* –
* –
* * 292,50 bis 294,99
* 39,00
* –
* –
* –
* –
* –
* * 295,00 bis 297,49
* 40,75
* –
* –
* –
* –
* –
* * 297,50 bis 299,99
* 42,50
* –
* –
* –
* –
* –
* * 300,00 bis 302,49
* 44,25
* –
* –
* –
* –
* –
* * 302,50 bis 304,99
* 46,00
* –
* –
* –
* –
* –
* * 305,00 bis 307,49
* 47,75
* –
* –
* –
* –
* –
* * 307,50 bis 309,99
* 49,50
* –
* –
* –
* –
* –
* * 310,00 bis 312,49
* 51,25
* –
* –
* –
* –
* –
* * 312,50 bis 314,99
* 53,00
* –
* –
* –
* –
* –
* * 315,00 bis 317,49
* 54,75
* –
* –
* –
* –
* –
* * 317,50 bis 319,99
* 56,50
* –
* –
* –
* –
* –
* * 320,00 bis 322,49
* 58,25
* –
* –
* –
* –
* –
* * 322,50 bis 324,99
* 60,00
* –
* –
* –
* –
* –
* * 325,00 bis 327,49
* 61,75
* –
* –
* –
* –
* –
* * 327,50 bis 329,99
* 63,50
* 0,80
* –
* –
* –
* –
* * 330,00 bis 332,49
* 65,25
* 2,05
* –
* –
* –
* –
* * 332,50 bis 334,99
* 67,00
* 3,30
* –
* –
* –
* –
* * 335,00 bis 337,49
* 68,75
* 4,55
* –
* –
* –
* –
* * 337,50 bis 339,99
* 70,50
* 5,80
* –
* –
* –
* –
* * 340,00 bis 342,49
* 72,25
* 7,05
* –
* –
* –
* –
* * 342,50 bis 344,99
* 74,00
* 8,30
* –
* –
* –
* –
* * 345,00 bis 347,49
* 75,75
* 9,55
* –
* –
* –
* –
* * 347,50 bis 349,99
* 77,50
* 10,80
* –
* –
* –
* –
* * 350,00 bis 352,49
* 79,25
* 12,05
* –
* –
* –
* –
* * 352,50 bis 354,99
* 81,00
* 13,30
* –
* –
* –
* –
* * 355,00 bis 357,49
* 82,75
* 14,55
* –
* –
* –
* –
* * 357,50 bis 359,99
* 84,50
* 15,80
* –
* –
* –
* –
* * 360,00 bis 362,49
* 86,25
* 17,05
* –
* –
* –
* –
* * 362,50 bis 364,99
* 88,00
* 18,30
* –
* –
* –
* –
* * 365,00 bis 367,49
* 89,75
* 19,55
* –
* –
* –
* –
* * 367,50 bis 369,99
* 91,50
* 20,80
* –
* –
* –
* –
* * 370,00 bis 372,49
* 93,25
* 22,05
* –
* –
* –
* –
* * 372,50 bis 374,99
* 95,00
* 23,30
* –
* –
* –
* –
* * 375,00 bis 377,49
* 96,75
* 24,55
* –
* –
* –
* –
* * 377,50 bis 379,99
* 98,50
* 25,80
* 0,78
* –
* –
* –
* * 380,00 bis 382,49
* 100,25
* 27,05
* 1,78
* –
* –
* –
* * 382,50 bis 384,99
* 102,00
* 28,30
* 2,78
* –
* –
* –
* * 385,00 bis 387,49
* 103,75
* 29,55
* 3,78
* –
* –
* –
* * 387,50 bis 389,99
* 105,50
* 30,80
* 4,78
* –
* –
* –
* * 390,00 bis 392,49
* 107,25
* 32,05
* 5,78
* –
* –
* –
* * 392,50 bis 394,99
* 109,00
* 33,30
* 6,78
* –
* –
* –
* * 395,00 bis 397,49
* 110,75
* 34,55
* 7,78
* –
* –
* –
* * 397,50 bis 399,99
* 112,50
* 35,80
* 8,78
* –
* –
* –
* * 400,00 bis 402,49
* 114,25
* 37,05
* 9,78
* –
* –
* –
* * 402,50 bis 404,99
* 116,00
* 38,30
* 10,78
* –
* –
* –
* * 405,00 bis 407,49
* 117,75
* 39,55
* 11,78
* –
* –
* –
* * 407,50 bis 409,99
* 119,50
* 40,80
* 12,78
* –
* –
* –
* * 410,00 bis 412,49
* 121,25
* 42,05
* 13,78
* –
* –
* –
* * 412,50 bis 414,99
* 123,00
* 43,30
* 14,78
* –
* –
* –
* * 415,00 bis 417,49
* 124,75
* 44,55
* 15,78
* –
* –
* –
* * 417,50 bis 419,99
* 126,50
* 45,80
* 16,78
* –
* –
* –
* * 420,00 bis 422,49
* 128,25
* 47,05
* 17,78
* –
* –
* –
* * 422,50 bis 424,99
* 130,00
* 48,30
* 18,78
* –
* –
* –
* * 425,00 bis 427,49
* 131,75
* 49,55
* 19,78
* –
* –
* –
* * 427,50 bis 429,99
* 133,50
* 50,80
* 20,78
* 0,69
* –
* –
* * 430,00 bis 432,49
* 135,25
* 52,05
* 21,78
* 1,44
* –
* –
* * 432,50 bis 434,99
* 137,00
* 53,30
* 22,78
* 2,19
* –
* –
* * 435,00 bis 437,49
* 138,75
* 54,55
* 23,78
* 2,94
* –
* –
* * 437,50 bis 439,99
* 140,50
* 55,80
* 24,78
* 3,69
* –
* –
* * 440,00 bis 442,49
* 142,25
* 57,05
* 25,78
* 4,44
* –
* –
* * 442,50 bis 444,99
* 144,00
* 58,30
* 26,78
* 5,19
* –
* –
* * 445,00 bis 447,49
* 145,75
* 59,55
* 27,78
* 5,94
* –
* –
* * 447,50 bis 449,99
* 147,50
* 60,80
* 28,78
* 6,69
* –
* –
* * 450,00 bis 452,49
* 149,25
* 62,05
* 29,78
* 7,44
* –
* –
* * 452,50 bis 454,99
* 151,00
* 63,30
* 30,78
* 8,19
* –
* –
* * 455,00 bis 457,49
* 152,75
* 64,55
* 31,78
* 8,94
* –
* –
* * 457,50 bis 459,99
* 154,50
* 65,80
* 32,78
* 9,69
* –
* –
* * 460,00 bis 462,49
* 156,25
* 67,05
* 33,78
* 10,44
* –
* –
* * 462,50 bis 464,99
* 158,00
* 68,30
* 34,78
* 11,19
* –
* –
* * 465,00 bis 467,49
* 159,75
* 69,55
* 35,78
* 11,94
* –
* –
* * 467,50 bis 469,99
* 161,50
* 70,80
* 36,78
* 12,69
* –
* –
* * 470,00 bis 472,49
* 163,25
* 72,05
* 37,78
* 13,44
* –
* –
* * 472,50 bis 474,99
* 165,00
* 73,30
* 38,78
* 14,19
* –
* –
* * 475,00 bis 477,49
* 166,75
* 74,55
* 39,78
* 14,94
* 0,03
* –
* * 477,50 bis 479,99
* 168,50
* 75,80
* 40,78
* 15,69
* 0,53
* –
* * 480,00 bis 482,49
* 170,25
* 77,05
* 41,78
* 16,44
* 1,03
* –
* * 482,50 bis 484,99
* 172,00
* 78,30
* 42,78
* 17,19
* 1,53
* –
* * 485,00 bis 487,49
* 173,75
* 79,55
* 43,78
* 17,94
* 2,03
* –
* * 487,50 bis 489,99
* 175,50
* 80,80
* 44,78
* 18,69
* 2,53
* –
* * 490,00 bis 492,49
* 177,25
* 82,05
* 45,78
* 19,44
* 3,03
* –
* * 492,50 bis 494,99
* 179,00
* 83,30
* 46,78
* 20,19
* 3,53
* –
* * 495,00 bis 497,49
* 180,75
* 84,55
* 47,78
* 20,94
* 4,03
* –
* * 497,50 bis 499,99
* 182,50
* 85,80
* 48,78
* 21,69
* 4,53
* –
* * 500,00 bis 502,49
* 184,25
* 87,05
* 49,78
* 22,44
* 5,03
* –
* * 502,50 bis 504,99
* 186,00
* 88,30
* 50,78
* 23,19
* 5,53
* –
* * 505,00 bis 507,49
* 187,75
* 89,55
* 51,78
* 23,94
* 6,03
* –
* * 507,50 bis 509,99
* 189,50
* 90,80
* 52,78
* 24,69
* 6,53
* –
* * 510,00 bis 512,49
* 191,25
* 92,05
* 53,78
* 25,44
* 7,03
* –
* * 512,50 bis 514,99
* 193,00
* 93,30
* 54,78
* 26,19
* 7,53
* –
* * 515,00 bis 517,49
* 194,75
* 94,55
* 55,78
* 26,94
* 8,03
* –
* * 517,50 bis 519,99
* 196,50
* 95,80
* 56,78
* 27,69
* 8,53
* –
* * 520,00 bis 522,49
* 198,25
* 97,05
* 57,78
* 28,44
* 9,03
* –
* * 522,50 bis 524,99
* 200,00
* 98,30
* 58,78
* 29,19
* 9,53
* –
* * 525,00 bis 527,49
* 201,75
* 99,55
* 59,78
* 29,94
* 10,03
* 0,05
* * 527,50 bis 529,99
* 203,50
* 100,80
* 60,78
* 30,69
* 10,53
* 0,30
* * 530,00 bis 532,49
* 205,25
* 102,05
* 61,78
* 31,44
* 11,03
* 0,55
* * 532,50 bis 534,99
* 207,00
* 103,30
* 62,78
* 32,19
* 11,53
* 0,80
* * 535,00 bis 537,49
* 208,75
* 104,55
* 63,78
* 32,94
* 12,03
* 1,05
* * 537,50 bis 539,99
* 210,50
* 105,80
* 64,78
* 33,69
* 12,53
* 1,30
* * 540,00 bis 542,49
* 212,25
* 107,05
* 65,78
* 34,44
* 13,03
* 1,55
* * 542,50 bis 544,99
* 214,00
* 108,30
* 66,78
* 35,19
* 13,53
* 1,80
* * 545,00 bis 547,49
* 215,75
* 109,55
* 67,78
* 35,94
* 14,03
* 2,05
* * 547,50 bis 549,99
* 217,50
* 110,80
* 68,78
* 36,69
* 14,53
* 2,30
* * 550,00 bis 552,49
* 219,25
* 112,05
* 69,78
* 37,44
* 15,03
* 2,55
* * 552,50 bis 554,99
* 221,00
* 113,30
* 70,78
* 38,19
* 15,53
* 2,80
* * 555,00 bis 557,49
* 222,75
* 114,55
* 71,78
* 38,94
* 16,03
* 3,05
* * 557,50 bis 559,99
* 224,50
* 115,80
* 72,78
* 39,69
* 16,53
* 3,30
* * 560,00 bis 562,49
* 226,25
* 117,05
* 73,78
* 40,44
* 17,03
* 3,55
* * 562,50 bis 564,99
* 228,00
* 118,30
* 74,78
* 41,19
* 17,53
* 3,80
* * 565,00 bis 567,49
* 229,75
* 119,55
* 75,78
* 41,94
* 18,03
* 4,05
* * 567,50 bis 569,99
* 231,50
* 120,80
* 76,78
* 42,69
* 18,53
* 4,30
* * 570,00 bis 572,49
* 233,25
* 122,05
* 77,78
* 43,44
* 19,03
* 4,55
* * 572,50 bis 574,99
* 235,00
* 123,30
* 78,78
* 44,19
* 19,53
* 4,80
* * 575,00 bis 577,49
* 236,75
* 124,55
* 79,78
* 44,94
* 20,03
* 5,05
* * 577,50 bis 579,99
* 238,50
* 125,80
* 80,78
* 45,69
* 20,53
* 5,30
* * 580,00 bis 582,49
* 240,25
* 127,05
* 81,78
* 46,44
* 21,03
* 5,55
* * 582,50 bis 584,99
* 242,00
* 128,30
* 82,78
* 47,19
* 21,53
* 5,80
* * 585,00 bis 587,49
* 243,75
* 129,55
* 83,78
* 47,94
* 22,03
* 6,05
* * 587,50 bis 589,99
* 245,50
* 130,80
* 84,78
* 48,69
* 22,53
* 6,30
* * 590,00 bis 592,49
* 247,25
* 132,05
* 85,78
* 49,44
* 23,03
* 6,55
* * 592,50 bis 594,99
* 249,00
* 133,30
* 86,78
* 50,19
* 23,53
* 6,80
* * 595,00 bis 597,49
* 250,75
* 134,55
* 87,78
* 50,94
* 24,03
* 7,05
* * 597,50 bis 599,99
* 252,50
* 135,80
* 88,78
* 51,69
* 24,53
* 7,30
* * 600,00 bis 602,49
* 254,25
* 137,05
* 89,78
* 52,44
* 25,03
* 7,55
* * 602,50 bis 604,99
* 256,00
* 138,30
* 90,78
* 53,19
* 25,53
* 7,80
* * 605,00 bis 607,49
* 257,75
* 139,55
* 91,78
* 53,94
* 26,03
* 8,05
* * 607,50 bis 609,99
* 259,50
* 140,80
* 92,78
* 54,69
* 26,53
* 8,30
* * 610,00 bis 612,49
* 261,25
* 142,05
* 93,78
* 55,44
* 27,03
* 8,55
* * 612,50 bis 614,99
* 263,00
* 143,30
* 94,78
* 56,19
* 27,53
* 8,80
* * 615,00 bis 617,49
* 264,75
* 144,55
* 95,78
* 56,94
* 28,03
* 9,05
* * 617,50 bis 619,99
* 266,50
* 145,80
* 96,78
* 57,69
* 28,53
* 9,30
* * 620,00 bis 622,49
* 268,25
* 147,05
* 97,78
* 58,44
* 29,03
* 9,55
* * 622,50 bis 624,99
* 270,00
* 148,30
* 98,78
* 59,19
* 29,53
* 9,80
* * 625,00 bis 627,49
* 271,75
* 149,55
* 99,78
* 59,94
* 30,03
* 10,05
* * 627,50 bis 629,99
* 273,50
* 150,80
* 100,78
* 60,69
* 30,53
* 10,30
* * 630,00 bis 632,49
* 275,25
* 152,05
* 101,78
* 61,44
* 31,03
* 10,55
* * 632,50 bis 634,99
* 277,00
* 153,30
* 102,78
* 62,19
* 31,53
* 10,80
* * 635,00 bis 637,49
* 278,75
* 154,55
* 103,78
* 62,94
* 32,03
* 11,05
* * 637,50 bis 639,99
* 280,50
* 155,80
* 104,78
* 63,69
* 32,53
* 11,30
* * 640,00 bis 642,49
* 282,25
* 157,05
* 105,78
* 64,44
* 33,03
* 11,55
* * 642,50 bis 644,99
* 284,00
* 158,30
* 106,78
* 65,19
* 33,53
* 11,80
* * 645,00 bis 647,49
* 285,75
* 159,55
* 107,78
* 65,94
* 34,03
* 12,05
* * 647,50 bis 649,99
* 287,50
* 160,80
* 108,78
* 66,69
* 34,53
* 12,30
* * 650,00 bis 652,49
* 289,25
* 162,05
* 109,78
* 67,44
* 35,03
* 12,55
* * 652,50 bis 654,99
* 291,00
* 163,30
* 110,78
* 68,19
* 35,53
* 12,80
* * 655,00 bis 657,49
* 292,75
* 164,55
* 111,78
* 68,94
* 36,03
* 13,05
* * 657,50 bis 659,99
* 294,50
* 165,80
* 112,78
* 69,69
* 36,53
* 13,30
* * 660,00 bis 662,49
* 296,25
* 167,05
* 113,78
* 70,44
* 37,03
* 13,55
* * 662,50 bis 664,99
* 298,00
* 168,30
* 114,78
* 71,19
* 37,53
* 13,80
* * 665,00 bis 667,49
* 299,75
* 169,55
* 115,78
* 71,94
* 38,03
* 14,05
* * 667,50 bis 669,99
* 301,50
* 170,80
* 116,78
* 72,69
* 38,53
* 14,30
* * 670,00 bis 672,49
* 303,25
* 172,05
* 117,78
* 73,44
* 39,03
* 14,55
* * 672,50 bis 674,99
* 305,00
* 173,30
* 118,78
* 74,19
* 39,53
* 14,80
* * 675,00 bis 677,49
* 306,75
* 174,55
* 119,78
* 74,94
* 40,03
* 15,05
* * 677,50 bis 679,99
* 308,50
* 175,80
* 120,78
* 75,69
* 40,53
* 15,30
* * 680,00 bis 682,49
* 310,25
* 177,05
* 121,78
* 76,44
* 41,03
* 15,55
* * 682,50 bis 684,99
* 312,00
* 178,30
* 122,78
* 77,19
* 41,53
* 15,80
* * 685,00 bis 687,49
* 313,75
* 179,55
* 123,78
* 77,94
* 42,03
* 16,05
* * 687,50 bis 689,99
* 315,50
* 180,80
* 124,78
* 78,69
* 42,53
* 16,30
* * 690,00 bis 692,49
* 317,25
* 182,05
* 125,78
* 79,44
* 43,03
* 16,55
* * 692,50 bis 694,99
* 319,00
* 183,30
* 126,78
* 80,19
* 43,53
* 16,80
* * 695,00 bis 697,49
* 320,75
* 184,55
* 127,78
* 80,94
* 44,03
* 17,05
* * 697,50 bis 699,99
* 322,50
* 185,80
* 128,78
* 81,69
* 44,53
* 17,30
* * 700,00 bis 702,49
* 324,25
* 187,05
* 129,78
* 82,44
* 45,03
* 17,55
* * 702,50 bis 704,99
* 326,00
* 188,30
* 130,78
* 83,19
* 45,53
* 17,80
* * 705,00 bis 707,49
* 327,75
* 189,55
* 131,78
* 83,94
* 46,03
* 18,05
* * 707,50 bis 709,99
* 329,50
* 190,80
* 132,78
* 84,69
* 46,53
* 18,30
* * 710,00 bis 712,49
* 331,25
* 192,05
* 133,78
* 85,44
* 47,03
* 18,55
* * 712,50 bis 714,99
* 333,00
* 193,30
* 134,78
* 86,19
* 47,53
* 18,80
* * 715,00 bis 717,49
* 334,75
* 194,55
* 135,78
* 86,94
* 48,03
* 19,05
* * 717,50 bis 719,99
* 336,50
* 195,80
* 136,78
* 87,69
* 48,53
* 19,30
* * 720,00 bis 722,49
* 338,25
* 197,05
* 137,78
* 88,44
* 49,03
* 19,55
* * 722,50 bis 724,99
* 340,00
* 198,30
* 138,78
* 89,19
* 49,53
* 19,80
* * 725,00 bis 725,89
* 341,75
* 199,55
* 139,78
* 89,94
* 50,03
* 20,05
* * Der Mehrbetrag über 725,89 Euro ist voll pfändbar.
Auszahlung für Tage
##
* *
* Pfändbarer Betrag bei
Unterhaltspflicht für ... Personen
* * Nettolohn
täglich
* 0
* 1
* 2
* 3
* 4
* 5 und
mehr
* * in Euro
* * bis 47,49
* –
* –
* –
* –
* –
* –
* * 47,50 bis 47,99
* 0,10
* –
* –
* –
* –
* –
* * 48,00 bis 48,49
* 0,45
* –
* –
* –
* –
* –
* * 48,50 bis 48,99
* 0,80
* –
* –
* –
* –
* –
* * 49,00 bis 49,49
* 1,15
* –
* –
* –
* –
* –
* * 49,50 bis 49,99
* 1,50
* –
* –
* –
* –
* –
* * 50,00 bis 50,49
* 1,85
* –
* –
* –
* –
* –
* * 50,50 bis 50,99
* 2,20
* –
* –
* –
* –
* –
* * 51,00 bis 51,49
* 2,55
* –
* –
* –
* –
* –
* * 51,50 bis 51,99
* 2,90
* –
* –
* –
* –
* –
* * 52,00 bis 52,49
* 3,25
* –
* –
* –
* –
* –
* * 52,50 bis 52,99
* 3,60
* –
* –
* –
* –
* –
* * 53,00 bis 53,49
* 3,95
* –
* –
* –
* –
* –
* * 53,50 bis 53,99
* 4,30
* –
* –
* –
* –
* –
* * 54,00 bis 54,49
* 4,65
* –
* –
* –
* –
* –
* * 54,50 bis 54,99
* 5,00
* –
* –
* –
* –
* –
* * 55,00 bis 55,49
* 5,35
* –
* –
* –
* –
* –
* * 55,50 bis 55,99
* 5,70
* –
* –
* –
* –
* –
* * 56,00 bis 56,49
* 6,05
* –
* –
* –
* –
* –
* * 56,50 bis 56,99
* 6,40
* –
* –
* –
* –
* –
* * 57,00 bis 57,49
* 6,75
* –
* –
* –
* –
* –
* * 57,50 bis 57,99
* 7,10
* –
* –
* –
* –
* –
* * 58,00 bis 58,49
* 7,45
* –
* –
* –
* –
* –
* * 58,50 bis 58,99
* 7,80
* –
* –
* –
* –
* –
* * 59,00 bis 59,49
* 8,15
* –
* –
* –
* –
* –
* * 59,50 bis 59,99
* 8,50
* –
* –
* –
* –
* –
* * 60,00 bis 60,49
* 8,85
* –
* –
* –
* –
* –
* * 60,50 bis 60,99
* 9,20
* –
* –
* –
* –
* –
* * 61,00 bis 61,49
* 9,55
* –
* –
* –
* –
* –
* * 61,50 bis 61,99
* 9,90
* –
* –
* –
* –
* –
* * 62,00 bis 62,49
* 10,25
* –
* –
* –
* –
* –
* * 62,50 bis 62,99
* 10,60
* –
* –
* –
* –
* –
* * 63,00 bis 63,49
* 10,95
* –
* –
* –
* –
* –
* * 63,50 bis 63,99
* 11,30
* –
* –
* –
* –
* –
* * 64,00 bis 64,49
* 11,65
* –
* –
* –
* –
* –
* * 64,50 bis 64,99
* 12,00
* –
* –
* –
* –
* –
* * 65,00 bis 65,49
* 12,35
* –
* –
* –
* –
* –
* * 65,50 bis 65,99
* 12,70
* 0,16
* –
* –
* –
* –
* * 66,00 bis 66,49
* 13,05
* 0,41
* –
* –
* –
* –
* * 66,50 bis 66,99
* 13,40
* 0,66
* –
* –
* –
* –
* * 67,00 bis 67,49
* 13,75
* 0,91
* –
* –
* –
* –
* * 67,50 bis 67,99
* 14,10
* 1,16
* –
* –
* –
* –
* * 68,00 bis 68,49
* 14,45
* 1,41
* –
* –
* –
* –
* * 68,50 bis 68,99
* 14,80
* 1,66
* –
* –
* –
* –
* * 69,00 bis 69,49
* 15,15
* 1,91
* –
* –
* –
* –
* * 69,50 bis 69,99
* 15,50
* 2,16
* –
* –
* –
* –
* * 70,00 bis 70,49
* 15,85
* 2,41
* –
* –
* –
* –
* * 70,50 bis 70,99
* 16,20
* 2,66
* –
* –
* –
* –
* * 71,00 bis 71,49
* 16,55
* 2,91
* –
* –
* –
* –
* * 71,50 bis 71,99
* 16,90
* 3,16
* –
* –
* –
* –
* * 72,00 bis 72,49
* 17,25
* 3,41
* –
* –
* –
* –
* * 72,50 bis 72,99
* 17,60
* 3,66
* –
* –
* –
* –
* * 73,00 bis 73,49
* 17,95
* 3,91
* –
* –
* –
* –
* * 73,50 bis 73,99
* 18,30
* 4,16
* –
* –
* –
* –
* * 74,00 bis 74,49
* 18,65
* 4,41
* –
* –
* –
* –
* * 74,50 bis 74,99
* 19,00
* 4,66
* –
* –
* –
* –
* * 75,00 bis 75,49
* 19,35
* 4,91
* –
* –
* –
* –
* * 75,50 bis 75,99
* 19,70
* 5,16
* 0,16
* –
* –
* –
* * 76,00 bis 76,49
* 20,05
* 5,41
* 0,36
* –
* –
* –
* * 76,50 bis 76,99
* 20,40
* 5,66
* 0,56
* –
* –
* –
* * 77,00 bis 77,49
* 20,75
* 5,91
* 0,76
* –
* –
* –
* * 77,50 bis 77,99
* 21,10
* 6,16
* 0,96
* –
* –
* –
* * 78,00 bis 78,49
* 21,45
* 6,41
* 1,16
* –
* –
* –
* * 78,50 bis 78,99
* 21,80
* 6,66
* 1,36
* –
* –
* –
* * 79,00 bis 79,49
* 22,15
* 6,91
* 1,56
* –
* –
* –
* * 79,50 bis 79,99
* 22,50
* 7,16
* 1,76
* –
* –
* –
* * 80,00 bis 80,49
* 22,85
* 7,41
* 1,96
* –
* –
* –
* * 80,50 bis 80,99
* 23,20
* 7,66
* 2,16
* –
* –
* –
* * 81,00 bis 81,49
* 23,55
* 7,91
* 2,36
* –
* –
* –
* * 81,50 bis 81,99
* 23,90
* 8,16
* 2,56
* –
* –
* –
* * 82,00 bis 82,49
* 24,25
* 8,41
* 2,76
* –
* –
* –
* * 82,50 bis 82,99
* 24,60
* 8,66
* 2,96
* –
* –
* –
* * 83,00 bis 83,49
* 24,95
* 8,91
* 3,16
* –
* –
* –
* * 83,50 bis 83,99
* 25,30
* 9,16
* 3,36
* –
* –
* –
* * 84,00 bis 84,49
* 25,65
* 9,41
* 3,56
* –
* –
* –
* * 84,50 bis 84,99
* 26,00
* 9,66
* 3,76
* –
* –
* –
* * 85,00 bis 85,49
* 26,35
* 9,91
* 3,96
* –
* –
* –
* * 85,50 bis 85,99
* 26,70
* 10,16
* 4,16
* 0,14
* –
* –
* * 86,00 bis 86,49
* 27,05
* 10,41
* 4,36
* 0,29
* –
* –
* * 86,50 bis 86,99
* 27,40
* 10,66
* 4,56
* 0,44
* –
* –
* * 87,00 bis 87,49
* 27,75
* 10,91
* 4,76
* 0,59
* –
* –
* * 87,50 bis 87,99
* 28,10
* 11,16
* 4,96
* 0,74
* –
* –
* * 88,00 bis 88,49
* 28,45
* 11,41
* 5,16
* 0,89
* –
* –
* * 88,50 bis 88,99
* 28,80
* 11,66
* 5,36
* 1,04
* –
* –
* * 89,00 bis 89,49
* 29,15
* 11,91
* 5,56
* 1,19
* –
* –
* * 89,50 bis 89,99
* 29,50
* 12,16
* 5,76
* 1,34
* –
* –
* * 90,00 bis 90,49
* 29,85
* 12,41
* 5,96
* 1,49
* –
* –
* * 90,50 bis 90,99
* 30,20
* 12,66
* 6,16
* 1,64
* –
* –
* * 91,00 bis 91,49
* 30,55
* 12,91
* 6,36
* 1,79
* –
* –
* * 91,50 bis 91,99
* 30,90
* 13,16
* 6,56
* 1,94
* –
* –
* * 92,00 bis 92,49
* 31,25
* 13,41
* 6,76
* 2,09
* –
* –
* * 92,50 bis 92,99
* 31,60
* 13,66
* 6,96
* 2,24
* –
* –
* * 93,00 bis 93,49
* 31,95
* 13,91
* 7,16
* 2,39
* –
* –
* * 93,50 bis 93,99
* 32,30
* 14,16
* 7,36
* 2,54
* –
* –
* * 94,00 bis 94,49
* 32,65
* 14,41
* 7,56
* 2,69
* –
* –
* * 94,50 bis 94,99
* 33,00
* 14,66
* 7,76
* 2,84
* –
* –
* * 95,00 bis 95,49
* 33,35
* 14,91
* 7,96
* 2,99
* 0,01
* –
* * 95,50 bis 95,99
* 33,70
* 15,16
* 8,16
* 3,14
* 0,11
* –
* * 96,00 bis 96,49
* 34,05
* 15,41
* 8,36
* 3,29
* 0,21
* –
* * 96,50 bis 96,99
* 34,40
* 15,66
* 8,56
* 3,44
* 0,31
* –
* * 97,00 bis 97,49
* 34,75
* 15,91
* 8,76
* 3,59
* 0,41
* –
* * 97,50 bis 97,99
* 35,10
* 16,16
* 8,96
* 3,74
* 0,51
* –
* * 98,00 bis 98,49
* 35,45
* 16,41
* 9,16
* 3,89
* 0,61
* –
* * 98,50 bis 98,99
* 35,80
* 16,66
* 9,36
* 4,04
* 0,71
* –
* * 99,00 bis 99,49
* 36,15
* 16,91
* 9,56
* 4,19
* 0,81
* –
* * 99,50 bis 99,99
* 36,50
* 17,16
* 9,76
* 4,34
* 0,91
* –
* * 100,00 bis 100,49
* 36,85
* 17,41
* 9,96
* 4,49
* 1,01
* –
* * 100,50 bis 100,99
* 37,20
* 17,66
* 10,16
* 4,64
* 1,11
* –
* * 101,00 bis 101,49
* 37,55
* 17,91
* 10,36
* 4,79
* 1,21
* –
* * 101,50 bis 101,99
* 37,90
* 18,16
* 10,56
* 4,94
* 1,31
* –
* * 102,00 bis 102,49
* 38,25
* 18,41
* 10,76
* 5,09
* 1,41
* –
* * 102,50 bis 102,99
* 38,60
* 18,66
* 10,96
* 5,24
* 1,51
* –
* * 103,00 bis 103,49
* 38,95
* 18,91
* 11,16
* 5,39
* 1,61
* –
* * 103,50 bis 103,99
* 39,30
* 19,16
* 11,36
* 5,54
* 1,71
* –
* * 104,00 bis 104,49
* 39,65
* 19,41
* 11,56
* 5,69
* 1,81
* –
* * 104,50 bis 104,99
* 40,00
* 19,66
* 11,76
* 5,84
* 1,91
* –
* * 105,00 bis 105,49
* 40,35
* 19,91
* 11,96
* 5,99
* 2,01
* 0,01
* * 105,50 bis 105,99
* 40,70
* 20,16
* 12,16
* 6,14
* 2,11
* 0,06
* * 106,00 bis 106,49
* 41,05
* 20,41
* 12,36
* 6,29
* 2,21
* 0,11
* * 106,50 bis 106,99
* 41,40
* 20,66
* 12,56
* 6,44
* 2,31
* 0,16
* * 107,00 bis 107,49
* 41,75
* 20,91
* 12,76
* 6,59
* 2,41
* 0,21
* * 107,50 bis 107,99
* 42,10
* 21,16
* 12,96
* 6,74
* 2,51
* 0,26
* * 108,00 bis 108,49
* 42,45
* 21,41
* 13,16
* 6,89
* 2,61
* 0,31
* * 108,50 bis 108,99
* 42,80
* 21,66
* 13,36
* 7,04
* 2,71
* 0,36
* * 109,00 bis 109,49
* 43,15
* 21,91
* 13,56
* 7,19
* 2,81
* 0,41
* * 109,50 bis 109,99
* 43,50
* 22,16
* 13,76
* 7,34
* 2,91
* 0,46
* * 110,00 bis 110,49
* 43,85
* 22,41
* 13,96
* 7,49
* 3,01
* 0,51
* * 110,50 bis 110,99
* 44,20
* 22,66
* 14,16
* 7,64
* 3,11
* 0,56
* * 111,00 bis 111,49
* 44,55
* 22,91
* 14,36
* 7,79
* 3,21
* 0,61
* * 111,50 bis 111,99
* 44,90
* 23,16
* 14,56
* 7,94
* 3,31
* 0,66
* * 112,00 bis 112,49
* 45,25
* 23,41
* 14,76
* 8,09
* 3,41
* 0,71
* * 112,50 bis 112,99
* 45,60
* 23,66
* 14,96
* 8,24
* 3,51
* 0,76
* * 113,00 bis 113,49
* 45,95
* 23,91
* 15,16
* 8,39
* 3,61
* 0,81
* * 113,50 bis 113,99
* 46,30
* 24,16
* 15,36
* 8,54
* 3,71
* 0,86
* * 114,00 bis 114,49
* 46,65
* 24,41
* 15,56
* 8,69
* 3,81
* 0,91
* * 114,50 bis 114,99
* 47,00
* 24,66
* 15,76
* 8,84
* 3,91
* 0,96
* * 115,00 bis 115,49
* 47,35
* 24,91
* 15,96
* 8,99
* 4,01
* 1,01
* * 115,50 bis 115,99
* 47,70
* 25,16
* 16,16
* 9,14
* 4,11
* 1,06
* * 116,00 bis 116,49
* 48,05
* 25,41
* 16,36
* 9,29
* 4,21
* 1,11
* * 116,50 bis 116,99
* 48,40
* 25,66
* 16,56
* 9,44
* 4,31
* 1,16
* * 117,00 bis 117,49
* 48,75
* 25,91
* 16,76
* 9,59
* 4,41
* 1,21
* * 117,50 bis 117,99
* 49,10
* 26,16
* 16,96
* 9,74
* 4,51
* 1,26
* * 118,00 bis 118,49
* 49,45
* 26,41
* 17,16
* 9,89
* 4,61
* 1,31
* * 118,50 bis 118,99
* 49,80
* 26,66
* 17,36
* 10,04
* 4,71
* 1,36
* * 119,00 bis 119,49
* 50,15
* 26,91
* 17,56
* 10,19
* 4,81
* 1,41
* * 119,50 bis 119,99
* 50,50
* 27,16
* 17,76
* 10,34
* 4,91
* 1,46
* * 120,00 bis 120,49
* 50,85
* 27,41
* 17,96
* 10,49
* 5,01
* 1,51
* * 120,50 bis 120,99
* 51,20
* 27,66
* 18,16
* 10,64
* 5,11
* 1,56
* * 121,00 bis 121,49
* 51,55
* 27,91
* 18,36
* 10,79
* 5,21
* 1,61
* * 121,50 bis 121,99
* 51,90
* 28,16
* 18,56
* 10,94
* 5,31
* 1,66
* * 122,00 bis 122,49
* 52,25
* 28,41
* 18,76
* 11,09
* 5,41
* 1,71
* * 122,50 bis 122,99
* 52,60
* 28,66
* 18,96
* 11,24
* 5,51
* 1,76
* * 123,00 bis 123,49
* 52,95
* 28,91
* 19,16
* 11,39
* 5,61
* 1,81
* * 123,50 bis 123,99
* 53,30
* 29,16
* 19,36
* 11,54
* 5,71
* 1,86
* * 124,00 bis 124,49
* 53,65
* 29,41
* 19,56
* 11,69
* 5,81
* 1,91
* * 124,50 bis 124,99
* 54,00
* 29,66
* 19,76
* 11,84
* 5,91
* 1,96
* * 125,00 bis 125,49
* 54,35
* 29,91
* 19,96
* 11,99
* 6,01
* 2,01
* * 125,50 bis 125,99
* 54,70
* 30,16
* 20,16
* 12,14
* 6,11
* 2,06
* * 126,00 bis 126,49
* 55,05
* 30,41
* 20,36
* 12,29
* 6,21
* 2,11
* * 126,50 bis 126,99
* 55,40
* 30,66
* 20,56
* 12,44
* 6,31
* 2,16
* * 127,00 bis 127,49
* 55,75
* 30,91
* 20,76
* 12,59
* 6,41
* 2,21
* * 127,50 bis 127,99
* 56,10
* 31,16
* 20,96
* 12,74
* 6,51
* 2,26
* * 128,00 bis 128,49
* 56,45
* 31,41
* 21,16
* 12,89
* 6,61
* 2,31
* * 128,50 bis 128,99
* 56,80
* 31,66
* 21,36
* 13,04
* 6,71
* 2,36
* * 129,00 bis 129,49
* 57,15
* 31,91
* 21,56
* 13,19
* 6,81
* 2,41
* * 129,50 bis 129,99
* 57,50
* 32,16
* 21,76
* 13,34
* 6,91
* 2,46
* * 130,00 bis 130,49
* 57,85
* 32,41
* 21,96
* 13,49
* 7,01
* 2,51
* * 130,50 bis 130,99
* 58,20
* 32,66
* 22,16
* 13,64
* 7,11
* 2,56
* * 131,00 bis 131,49
* 58,55
* 32,91
* 22,36
* 13,79
* 7,21
* 2,61
* * 131,50 bis 131,99
* 58,90
* 33,16
* 22,56
* 13,94
* 7,31
* 2,66
* * 132,00 bis 132,49
* 59,25
* 33,41
* 22,76
* 14,09
* 7,41
* 2,71
* * 132,50 bis 132,99
* 59,60
* 33,66
* 22,96
* 14,24
* 7,51
* 2,76
* * 133,00 bis 133,49
* 59,95
* 33,91
* 23,16
* 14,39
* 7,61
* 2,81
* * 133,50 bis 133,99
* 60,30
* 34,16
* 23,36
* 14,54
* 7,71
* 2,86
* * 134,00 bis 134,49
* 60,65
* 34,41
* 23,56
* 14,69
* 7,81
* 2,91
* * 134,50 bis 134,99
* 61,00
* 34,66
* 23,76
* 14,84
* 7,91
* 2,96
* * 135,00 bis 135,49
* 61,35
* 34,91
* 23,96
* 14,99
* 8,01
* 3,01
* * 135,50 bis 135,99
* 61,70
* 35,16
* 24,16
* 15,14
* 8,11
* 3,06
* * 136,00 bis 136,49
* 62,05
* 35,41
* 24,36
* 15,29
* 8,21
* 3,11
* * 136,50 bis 136,99
* 62,40
* 35,66
* 24,56
* 15,44
* 8,31
* 3,16
* * 137,00 bis 137,49
* 62,75
* 35,91
* 24,76
* 15,59
* 8,41
* 3,21
* * 137,50 bis 137,99
* 63,10
* 36,16
* 24,96
* 15,74
* 8,51
* 3,26
* * 138,00 bis 138,49
* 63,45
* 36,41
* 25,16
* 15,89
* 8,61
* 3,31
* * 138,50 bis 138,99
* 63,80
* 36,66
* 25,36
* 16,04
* 8,71
* 3,36
* * 139,00 bis 139,49
* 64,15
* 36,91
* 25,56
* 16,19
* 8,81
* 3,41
* * 139,50 bis 139,99
* 64,50
* 37,16
* 25,76
* 16,34
* 8,91
* 3,46
* * 140,00 bis 140,49
* 64,85
* 37,41
* 25,96
* 16,49
* 9,01
* 3,51
* * 140,50 bis 140,99
* 65,20
* 37,66
* 26,16
* 16,64
* 9,11
* 3,56
* * 141,00 bis 141,49
* 65,55
* 37,91
* 26,36
* 16,79
* 9,21
* 3,61
* * 141,50 bis 141,99
* 65,90
* 38,16
* 26,56
* 16,94
* 9,31
* 3,66
* * 142,00 bis 142,49
* 66,25
* 38,41
* 26,76
* 17,09
* 9,41
* 3,71
* * 142,50 bis 142,99
* 66,60
* 38,66
* 26,96
* 17,24
* 9,51
* 3,76
* * 143,00 bis 143,49
* 66,95
* 38,91
* 27,16
* 17,39
* 9,61
* 3,81
* * 143,50 bis 143,99
* 67,30
* 39,16
* 27,36
* 17,54
* 9,71
* 3,86
* * 144,00 bis 144,49
* 67,65
* 39,41
* 27,56
* 17,69
* 9,81
* 3,91
* * 144,50 bis 144,99
* 68,00
* 39,66
* 27,76
* 17,84
* 9,91
* 3,96
* * 145,00 bis 145,18
* 68,35
* 39,91
* 27,96
* 17,99
* 10,01
* 4,01
* * Der Mehrbetrag über 145,18 Euro ist voll pfändbar.
| 7.69597 | 72 | 0.281647 | yue_Hant | 0.118987 |
9bd865d45742d5305d5f441b5f61b4f9d724d16a | 2,422 | md | Markdown | docs/framework/windows-workflow-foundation/samples/advanced-policy.md | cy-org/docs-conceptual.zh-cn | 0c18cda3dd707efdcdd0e73bc480ab9fbbc4580c | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/framework/windows-workflow-foundation/samples/advanced-policy.md | cy-org/docs-conceptual.zh-cn | 0c18cda3dd707efdcdd0e73bc480ab9fbbc4580c | [
"CC-BY-4.0",
"MIT"
] | null | null | null | docs/framework/windows-workflow-foundation/samples/advanced-policy.md | cy-org/docs-conceptual.zh-cn | 0c18cda3dd707efdcdd0e73bc480ab9fbbc4580c | [
"CC-BY-4.0",
"MIT"
] | null | null | null | ---
title: "高级策略 | Microsoft Docs"
ms.custom: ""
ms.date: "03/30/2017"
ms.prod: ".net-framework-4.6"
ms.reviewer: ""
ms.suite: ""
ms.tgt_pltfrm: ""
ms.topic: "article"
ms.assetid: 75a22c88-5e54-4ae8-84cb-fbb22a612f0a
caps.latest.revision: 9
author: "Erikre"
ms.author: "erikre"
manager: "erikre"
caps.handback.revision: 9
---
# 高级策略
此示例扩展了简单策略示例。除了简单策略示例中的住户折扣和企业折扣规则外,还添加了若干新规则。
添加了一条高价值规则,可为高价值订单提供更大的折扣。该规则被赋予了比前两条规则更小的优先级值,因此它将覆盖折扣字段,并优先于住户折扣或企业折扣规则。
另外还添加了一条计算总计规则,可基于折扣级别计算出总计。它显示了如何引用工作流活动上定义的方法,以及如何使用其他操作。此规则还演示了链接行为,因为任何时候当折扣字段发生更改时都会计算该规则。而且,还通过 CalculateTotal 方法上的 RuleWriteAttribute 显示了方法属性设置。这样,无论何时在执行方法时,都会重新计算受影响的规则 \(ErrorTotalRule\)。
添加的最后一条规则是用于检测错误(本例中为总计小于 0)的规则。如果出现这种错误,策略执行将停止。
`Console.Writeline` 还以操作的形式向每条规则中添加了 Console.Writeline 调用,以使规则执行的可见性更高,同时还显示它可能访问所引用类型上的静态方法。您还可以使用跟踪来查看所执行的规则。
此示例中使用的规则包括:
**ResidentialDiscountRule:**
IF OrderValue \> 500 AND CustomerType \= Residential
THEN Discount \= 5%
**BusinessDiscountRule:**
IF OrderValue \> 10000 AND CustomerType \= Business
THEN Discount \= 10%
**HighValueDiscountRule:**
IF OrderValue \> 20000
THEN Discount \= 15%
**TotalRule:**
IF Discount \> 0
THEN CalculateTotal\(OrderValue, Discount\)
ELSE Total \= OrderValue
**ErrorTotalRule:**
IF Total \< 0
THEN Error \= "Fired ErrorTotalRule"; Halt
也可以通过追踪和跟踪看到规则的计算和执行过程。
### 生成示例
1. 在 [!INCLUDE[vs2010](../../../../includes/vs2010-md.md)] 中打开解决方案。
2. 按 Ctrl\+Shift\+B 生成解决方案。
3. 按 Ctrl\+F5 不进行调试运行解决方案。
### 运行示例
- 在 SDK 命令提示窗口中,运行 AdvancedPolicy\\bin\\debug 文件夹(对于该示例的 Visual Basic 版本为 AdvancedPolicy \\bin 文件夹)中的 .exe 文件,该文件夹位于该示例的主文件夹下。
> [!IMPORTANT]
> 您的计算机上可能已安装这些示例。在继续操作之前,请先检查以下(默认)目录:
>
> `<安装驱动器>:\WF_WCF_Samples`
>
> 如果此目录不存在,请访问[针对 .NET Framework 4 的 Windows Communication Foundation \(WCF\) 和 Windows Workflow Foundation \(WF\) 示例](http://go.microsoft.com/fwlink/?LinkId=150780)(可能为英文网页),下载所有 [!INCLUDE[indigo1](../../../../includes/indigo1-md.md)] 和 [!INCLUDE[wf1](../../../../includes/wf1-md.md)] 示例。此示例位于以下目录:
>
> `<安装驱动器>:\WF_WCF_Samples\WF\Basic\Rules\Policy\AdvancedPolicy`
## 请参阅
<xref:System.Workflow.Activities.Rules.RuleSet>
<xref:System.Workflow.Activities.PolicyActivity>
[简单策略](../../../../docs/framework/windows-workflow-foundation/samples/simple-policy.md) | 27.522727 | 302 | 0.693229 | yue_Hant | 0.712397 |
9bd8f99934b07db478645ab210c9590a13c9fe5a | 1,697 | md | Markdown | content/post/2014-03-07-per-capita-gdp-versus-years-since-women-received-right-to-vote.md | airjordan707/SimplyStatistics | 4faef1d99f4d184aa692d749b64b7fc1d3f17474 | [
"MIT"
] | 221 | 2017-05-07T20:52:01.000Z | 2021-08-31T19:12:14.000Z | content/post/2014-03-07-per-capita-gdp-versus-years-since-women-received-right-to-vote.md | airjordan707/SimplyStatistics | 4faef1d99f4d184aa692d749b64b7fc1d3f17474 | [
"MIT"
] | 11 | 2017-05-08T06:37:51.000Z | 2019-05-29T16:04:56.000Z | content/post/2014-03-07-per-capita-gdp-versus-years-since-women-received-right-to-vote.md | airjordan707/SimplyStatistics | 4faef1d99f4d184aa692d749b64b7fc1d3f17474 | [
"MIT"
] | 83 | 2017-05-15T21:45:30.000Z | 2021-09-06T10:39:12.000Z | ---
id: 2745
title: Per capita GDP versus years since women received right to vote
date: 2014-03-07T10:00:10+00:00
author: Rafael Irizarry
dsq_thread_id:
- 2376290660
al2fb_facebook_link_id:
- 136171103105421_10201744258227793
al2fb_facebook_link_time:
- 2014-03-07T15:00:18+00:00
al2fb_facebook_link_picture:
- post=http://simplystatistics.org/wp-content/uploads/2014/03/Rplot02.png
categories:
- Uncategorized
slug: "per-capita-gdp-versus-years-since-women-received-right-to-vote"
---
Below is a plot of per capita GPD (in log scale) against years since women received the right to vote for 42 countries. Is this cause, effect, both or neither? We all know correlation does not imply causation, but I see many (non statistical) arguments to support both cause and effect here. Happy [International Women's Day](http://en.wikipedia.org/wiki/International_Women's_Day) ! <a href="http://simplystatistics.org/2014/03/07/per-capita-gdp-versus-years-since-women-received-right-to-vote/rplot/" rel="attachment wp-att-2766"><img class="alignnone size-full wp-image-2766" alt="Rplot" src="http://simplystatistics.org/wp-content/uploads/2014/03/Rplot.png" width="983" height="591" srcset="http://simplystatistics.org/wp-content/uploads/2014/03/Rplot-300x180.png 300w, http://simplystatistics.org/wp-content/uploads/2014/03/Rplot.png 983w" sizes="(max-width: 983px) 100vw, 983px" /></a>
The data is from [here](http://www.infoplease.com/ipa/A0931343.html) and [here](http://en.wikipedia.org/wiki/List_of_countries_by_GDP_(PPP)_per_capita). I removed countries where women have had the right to vote for less than 20 years.
pd -What's with Switzerland?
update - R^2 and p-value added to graph
| 67.88 | 891 | 0.777843 | eng_Latn | 0.516982 |
9bdab821d6e14af383306fc30d813c6c10e1acd3 | 511 | md | Markdown | _posts/2021-10-08-StyleMapGAN.md | starBooo/starBooo.github.io | ad94125a1a97bd819682cc86f0597313db1afdac | [
"MIT"
] | null | null | null | _posts/2021-10-08-StyleMapGAN.md | starBooo/starBooo.github.io | ad94125a1a97bd819682cc86f0597313db1afdac | [
"MIT"
] | null | null | null | _posts/2021-10-08-StyleMapGAN.md | starBooo/starBooo.github.io | ad94125a1a97bd819682cc86f0597313db1afdac | [
"MIT"
] | null | null | null | ---
layout: post
title: Exploiting Spatial Dimensions of Latent in GAN for Real-time Image Editing, CVPR 2021
categories: Paper Paper-GAN
description: weekly report
keywords: stylegan
---
#### StyleMapGAN Desc
CVPR 2020 oral paper 인 SEAN 논문의 Style Matrix 기법을 GAN Inversion 분야에 적용시킨 논문.
Encoder 구조를 Discriminator와 동일하게 구현하여 상당히 좋은 Image Reconstruction을 가능하게 하였다.
Encoder-Decoder 구조이기 때문에 Optimization 방법보다 Runtime도 훨씬 짧다. (Real-time)

[Paper](https://arxiv.org/abs/2104.14754)
| 28.388889 | 92 | 0.772994 | kor_Hang | 0.993169 |
9bdb183dacd34fe21d07774ce9500dfd659df63b | 9,061 | md | Markdown | README.md | kasvtv/go-mockgen | 0162fefa2078407a378a508e27fceb08a091e90a | [
"MIT"
] | 36 | 2021-01-22T20:52:22.000Z | 2022-01-15T15:16:53.000Z | README.md | kasvtv/go-mockgen | 0162fefa2078407a378a508e27fceb08a091e90a | [
"MIT"
] | 15 | 2021-03-12T17:47:02.000Z | 2022-03-28T22:55:25.000Z | README.md | kasvtv/go-mockgen | 0162fefa2078407a378a508e27fceb08a091e90a | [
"MIT"
] | 3 | 2021-07-05T13:42:03.000Z | 2022-03-28T06:45:17.000Z | # go-mockgen
[](https://pkg.go.dev/github.com/derision-test/go-mockgen) [](https://circleci.com/gh/derision-test/go-mockgen) [](https://coveralls.io/github/derision-test/go-mockgen?branch=master)    
A mock interface code generator.
## Generating Mocks
Install with `go get -u github.com/derision-test/go-mockgen/...`.
Mocks should be generated via `go generate` and should be regenerated on each update to the target interface. For example, in `gen.go`:
```go
package mocks
//go:generate go-mockgen -f github.com/example/package -i ExampleInterface -o mock_example_interface_test.go
```
Depending on how you prefer to structure your code, you can either
1. generate mocks next to the implementation (as a sibling or in a sibling `mocks` package), or
2. generate mocks as needed in test code (generating them into a `_test.go` file).
### Flags
The following flags are defined by the binary.
| Name | Short Flag | Description |
| ------------------ | ---------- | ----------------------------------------------------------------------------------------------------------------- |
| package | p | The name of the generated package. Is the name of target directory if dirname or filename is supplied by default. |
| prefix | | A prefix used in the name of each mock struct. Should be TitleCase by convention. |
| interfaces | i | A list of interfaces to generate given the import paths. |
| exclude | e | A list of interfaces to exclude from generation. |
| filename | o | The target output file. All mocks are written to this file. |
| dirname | d | The target output directory. Each mock will be written to a unique file. |
| force | f | Do not abort if a write to disk would overwrite an existing file. |
| disable-formatting | | Do not run goimports over the rendered files (enabled by default). |
| goimports | | Path to the goimports binary (uses goimports on your PATH by default). |
| for-test | | Append _test suffix to generated package names and file names. |
## Testing with Mocks
A mock value fulfills all of the methods of the target interface from which it was generated. Unless overridden, all methods of the mock will return zero values for everything. To override a specific method, you can set its `hook` or its `return values`.
A hook is a method that is called on each invocation and allows the test to specify complex behaviors in the mocked interface (conditionally returning values, synchronizing on external state, etc,). The default hook for a method is set with the `SetDefaultHook` method.
```go
func TestCache(t *testing.T) {
cache := mocks.NewMockCache()
cache.GetFunc.SetDefaultHook(func (key string) (interface{}, bool) {
if key == "expected" {
return 42, true
}
return nil, false
})
testSubject := NewThingThatNeedsCache(cache)
// ...
}
```
In the cases where you don't need specific behaviors but just need to return some data, the setup gets a bit easier with `SetDefaultReturn`.
```go
func TestCache(t *testing.T) {
cache := mocks.NewMockCache()
cache.GetFunc.SetDefaultReturn(42, true)
testSubject := NewThingThatNeedsCache(cache)
// ...
}
```
Hook and return values can also be _stacked_ when your test can anticipate multiple calls to the same function. Pushing a hook or a return value will set the hook or return value for _one_ invocation of the mocked method. Once this hook or return value has been spent, it will be removed from the queue. Hooks and return values can be interleaved. If the queue is empty, the default hook will be invoked (or the default return values returned).
The following example will test a cache that returns values 50, 51, and 52 in sequence, then panic if there is an unexpected fourth call.
```go
func TestCache(t *testing.T) {
cache := mocks.NewMockCache()
cache.GetFunc.SetDefaultHook(func (key string) (interface{}, bool) {
panic("unexpected call")
})
cache.GetFunc.PushReturn(50, true)
cache.GetFunc.PushReturn(51, true)
cache.GetFunc.PushReturn(52, true)
testSubject := NewThingThatNeedsCache(cache)
// ...
}
```
### Assertions
Mocks track their invocations and can be retrieved via the `History` method. Structs are generated for each method type containing fields for each argument and result type. Raw assertions can be performed on these values.
```go
allCalls := cache.GetFunc.History()
allCalls[0].Arg0 // key
allCalls[0].Result0 // value
allCalls[0].Result1 // exists flag
```
### Testify integration
This library also contains an API that integrates with the style of [Testify](https://github.com/stretchr/testify) assertions.
To use the assertions, import the assert and require packages by name.
```go
import (
mockassert "github.com/derision-test/go-mockgen/testutil/assert"
mockrequire "github.com/derision-test/go-mockgen/testutil/require"
)
```
The following methods are defined in both packages.
- `Called(t, mockFn, msgAndArgs...)`
- `NotCalled(t, mockFn, msgAndArgs...)`
- `CalledOnce(t, mockFn, msgAndArgs...)`
- `CalledN(t, mockFn, n, msgAndArgs...)`
- `CalledWith(t, mockFn, msgAndArgs...)`
- `NotCalledWith(t, mockFn, msgAndArgs...)`
- `CalledOnceWith(t, mockFn, msgAndArgs...)`
- `CalledNWith(t, mockFn, n, msgAndArgs...)`
These methods can be used as follows.
```go
// cache.Get called 3 times
mockassert.CalledN(t, cache.GetFunc, 3)
// Ensure cache.Set("foo", "bar") was called
mockassert.CalledWith(cache.SetFunc, mockassert.Values("foo", "bar"))
// Ensure cache.Set("foo", _) was called
mockassert.CalledWith(cache.SetFunc, mockassert.Values("foo", mockassert.Skip))
```
### Gomega integration
This library also contains a set of [Gomega](https://onsi.github.io/gomega/) matchers which simplify assertions over a mocked method's call history.
To use the matchers, import the matchers package anonymously.
```go
import . "github.com/derision-test/go-mockgen/testutil/gomega"
```
The following matchers are defined.
- `BeCalled()`
- `BeCalledN(n)`
- `BeCalledOnce()`
- `BeCalledWith(args...)`
- `BeCalledNWith(args...)`
- `BeCalledOnceWith(args...)`
- `BeAnything()`
These matchers can be used as follows.
```go
// cache.Get called 3 times
Expect(cache.GetFunc).To(BeCalledN(3))
// Ensure cache.Set("foo", "bar") was called
Expect(cache.SetFunc).To(BeCalledWith("foo", "bar"))
// Ensure cache.Set("foo", _) was called
Expect(cache.SetFunc).To(BeCalledWith("foo", BeAnything()))
```
## License
Copyright (c) 2020 Eric Fritz
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
| 46.466667 | 985 | 0.672553 | eng_Latn | 0.928945 |
9bdb75d96347332fc9d205797478f30f19984198 | 53 | md | Markdown | IonicFrontEnd/README.md | IKalonji/mbongo_algorand_wallet | cd222c20ce6610268811d6aff45ef6af2725a9c7 | [
"MIT"
] | 4 | 2022-01-02T09:58:41.000Z | 2022-01-04T20:37:45.000Z | IonicFrontEnd/README.md | IKalonji/mbongo_algorand_wallet | cd222c20ce6610268811d6aff45ef6af2725a9c7 | [
"MIT"
] | null | null | null | IonicFrontEnd/README.md | IKalonji/mbongo_algorand_wallet | cd222c20ce6610268811d6aff45ef6af2725a9c7 | [
"MIT"
] | 1 | 2022-01-06T17:05:31.000Z | 2022-01-06T17:05:31.000Z | # Mbongo
## Tatum x Algorand Integration bounty hunt
| 17.666667 | 43 | 0.773585 | deu_Latn | 0.226681 |
9bdec614bbdad652b26d335f4e067c35264bb649 | 148 | md | Markdown | Platform Software/myriad/unittests/flash/README.md | EyesOfThings/Software | 8932c2bf78c729c285853e51c8875a863496b561 | [
"MIT"
] | 38 | 2016-06-08T19:47:43.000Z | 2021-07-02T15:14:13.000Z | Platform Software/myriad/unittests/flash_rtems/README.md | MAVProxyUser/Software | 8932c2bf78c729c285853e51c8875a863496b561 | [
"MIT"
] | 3 | 2017-07-24T03:41:53.000Z | 2021-02-23T16:48:05.000Z | Platform Software/myriad/unittests/flash_rtems/README.md | MAVProxyUser/Software | 8932c2bf78c729c285853e51c8875a863496b561 | [
"MIT"
] | 18 | 2016-02-18T08:34:17.000Z | 2021-07-11T17:57:28.000Z | # FlashIO unit test README
## Setup
To run the test:
- open terminal and type "make start_server"
- open another terminal and type "make setup run"
| 24.666667 | 49 | 0.75 | eng_Latn | 0.951958 |
9bdef1713bcd4cb73dad8c2ddecba1b8fb040b26 | 1,323 | md | Markdown | AlchemyInsights/check-aad-identity-sync-status.md | isabella232/OfficeDocs-AlchemyInsights-pr.tr-TR | 829935b72282a64e4ec4294adebf31fd30f93f68 | [
"CC-BY-4.0",
"MIT"
] | 3 | 2020-05-19T19:08:16.000Z | 2021-03-14T11:48:36.000Z | AlchemyInsights/check-aad-identity-sync-status.md | isabella232/OfficeDocs-AlchemyInsights-pr.tr-TR | 829935b72282a64e4ec4294adebf31fd30f93f68 | [
"CC-BY-4.0",
"MIT"
] | 2 | 2022-02-09T06:53:52.000Z | 2022-02-09T06:54:01.000Z | AlchemyInsights/check-aad-identity-sync-status.md | isabella232/OfficeDocs-AlchemyInsights-pr.tr-TR | 829935b72282a64e4ec4294adebf31fd30f93f68 | [
"CC-BY-4.0",
"MIT"
] | 2 | 2019-10-09T20:30:22.000Z | 2021-10-09T10:37:41.000Z | ---
title: AAD Kimlik Eşitleme Durumunu Denetleme
ms.author: pebaum
author: pebaum
manager: scotv
ms.date: 04/21/2020
ms.audience: Admin
ms.topic: article
ms.service: o365-administration
ROBOTS: NOINDEX, NOFOLLOW
localization_priority: Normal
ms.collection: Adm_O365
ms.custom:
- "304"
- "1300008"
ms.assetid: e7242604-6a81-44f3-86ac-7f1f5da29ce7
ms.openlocfilehash: d060791e8981576c526885f171ab592f96c98783a061acbf41e659b1f896b8cf
ms.sourcegitcommit: b5f7da89a650d2915dc652449623c78be6247175
ms.translationtype: MT
ms.contentlocale: tr-TR
ms.lasthandoff: 08/05/2021
ms.locfileid: "53930785"
---
# <a name="check-aad-identity-sync-status"></a>AAD Kimlik Eşitleme durumunu denetleme
Eşitleme durumunu kontrol etmek kolaydır:
- Oturum açma sayfasında Microsoft 365 yönetim merkezi giriş **sayfasında DirSync Durumu'mu** seçin.
- Alternatif olarak, Kullanıcılar Etkin kullanıcılar'a gidebilir ve Etkin kullanıcılar sayfasında Diğer \> Dizin eşitlemesi'ne \> seçebilirsiniz.
- Dizin Eşitlemesi bölmesinde DirSync yönetimine git'i seçin.
Dizin eşitlemeniz ile ilgili bir sorun varsa, hatalar bu sayfada listelenir. Karşılaşabilirsiniz farklı hatalar hakkında daha fazla bilgi için bkz. [Dizin eşitleme hatalarını görüntüleme](https://docs.microsoft.com//office365/enterprise/identify-directory-synchronization-errors).
| 37.8 | 280 | 0.817082 | tur_Latn | 0.976621 |
9bdf84f7bf652863fb8514c37dc7ae454464959e | 2,726 | md | Markdown | _posts/2021-03-23-comcom.md | beakoo/beakoo.github.io | c974f65c42eb8775f18dcacd337cb58a512ec62b | [
"MIT"
] | null | null | null | _posts/2021-03-23-comcom.md | beakoo/beakoo.github.io | c974f65c42eb8775f18dcacd337cb58a512ec62b | [
"MIT"
] | 1 | 2020-10-11T06:01:47.000Z | 2020-10-11T06:01:47.000Z | _posts/2021-03-23-comcom.md | beakoo/beakoo.github.io | c974f65c42eb8775f18dcacd337cb58a512ec62b | [
"MIT"
] | null | null | null | ---
title: "뜨겁게 휘청"
excerpt: "The statement and images from exhibition"
gallery:
- url: /assets/img/uploads/00.jpg
image_path: /assets/img/uploads/00.jpg
- url: /assets/img/uploads/01.jpg
image_path: /assets/img/uploads/01.jpg
- url: /assets/img/uploads/02.jpg
image_path: /assets/img/uploads/02.jpg
- url: /assets/img/uploads/03.jpg
image_path: /assets/img/uploads/03.jpg
- url: /assets/img/uploads/05.jpg
image_path: /assets/img/uploads/05.jpg
- url: /assets/img/uploads/06.jpg
image_path: /assets/img/uploads/06.jpg
- url: /assets/img/uploads/07.jpg
image_path: /assets/img/uploads/07.jpg
- url: /assets/img/uploads/08.jpg
image_path: /assets/img/uploads/08.jpg
- url: /assets/img/uploads/10.jpg
image_path: /assets/img/uploads/10.jpg
- url: /assets/img/uploads/13.jpg
image_path: /assets/img/uploads/13.jpg
- url: /assets/img/uploads/14.jpg
image_path: /assets/img/uploads/14.jpg
- url: /assets/img/uploads/15.jpg
image_path: /assets/img/uploads/15.jpg
---
<center><h5> **[BOOBIBOOBI]**
{% include gallery caption="작품 사진" %}
<h6><div style="text-align: left">이따금 식물을 생활반경에 들이거나 식물의 생활반경으로 여행하는 것은, 근본적으로 자연에 속해있는 동물인 인간이 추구하는 원초적인 욕구 중 하나로 여겨진다. 그러나 모순되게도 ‘자연’은 종종 비주류적 특징으로 인식되곤 한다. 인간은 ‘자연’을 벗어난지 오래되었으며, 자연에 속한 것을 원시, 원초, 야만과 연결짓거나 향유하고 이용할 수단으로 대상화한다. 인류가 달려가고 있는 현대화의 길은 곧 서구화를 발판삼아, 도시화, 기술적 발전, 반복, 인본주의 그리고 수치화된 지표와 연관되어 있으며 곧 여러 주요 국가들이 표방하고 있는 이데아다. 반면 자연주의, 인문학은 부수적인 것 또는 ‘올드 패션’으로 받아들여지며, 이는 곧 비주류적 특징이자 때로는 일상을 벗어나는 행위가 된다. 이를테면 뉴욕시 한가운데에는 센트럴 파크가 있다. 빌딩숲 가운데에 있는 비싼 땅 위에 ‘비개발’된 녹지는 시민들의 쉼터가 된다. 이 이상적이고 낭만적인 풍경에는 어쩌면 상대적 관점에 따라 정복된 대상들이 있을지도 모른다.
그러나 상대성이란 무한한 것이라, 침범하지 않고 또 침해받지 않으면서 살아갈 수 있는 방법이란 없다. 이러한 발상이 확장되면 때로는 의도와 관계없이 다른 존재를 나의 움벨트 안에 두려는 시도 자체가 비난받기도 한다. 가장 가까운 예로 반려-(어쩌구)가 있다. 합의가 가능한 존재인 반려인 외에, 개나 고양이가 사람의 보호 아래 일생을 건강에 좋은 사료를 먹으며 살면 좋겠(으므로 개를 키울 거야!로 이어지곤 하는)다는 생각은 지극히 인간중심적이라고 비난받을 소지가 있다. 반면 반려 식물은 그렇지 않다. 식물은 감정이 없고, 고통을 느끼지 않으며, 먹이사슬 최하단에서 모든 생물의 생리에 관여하고 있기 때문에 침해하지 않을래야 침해하지 않을 수 없어서, 식물권을 논의하는 것은 무의미하다는 결론에 이르러서다.
나는 동물에게 하듯 식물도 존중해주자는 식물해방주의자가 아니다. 부드러운 풀밭을 마구 깔아뭉개고 바위를 들춰서 작은 동물들을 관찰한다는 명목으로 겁주며 즐거워하고 싶은 무자비한 욕구가 늘 있으므로 작업이 어떤 방식으로든 환경보호운동과 연관되는 것은 두려운 일이다. 다만 인간이 당연하게 스스로의 정서와 심미적 쾌락을 위해 이용해온 대상이 있음을 식물로서 나타내고, 또 나아가 그러한 불가피한 정복으로 형성된 피정복자가 미시적으로 우리 주변에 있음을 인지하고 그러한 상대성 고리로부터 벗어나려는 시도가 이루어짐을 미약하게나마 드러낸다.
그리하여 래치훅, 펀칭, 터프팅으로 이끼 오브제를, 편직과 손바느질로 아가베나 선인장 등의 오브제를 제작하여 정서적으로 안정감을 주는 푸르른 식물을 생활반경에 들일 수 있게 함과 동시에, ‘다른 존재를 대하는 조심성’을 배제한 촉각적 쾌락을 선사하고자 한다. 패브릭으로 만들어진 식물 형상의 오브제는 그러한 욕구로 인해 피해받지 않는 피해자이자, 빚어진 비주류인 것이다.
스튜디오 컴컴의 두 번째 전시. 명진, 도은, 안서연, 정력공원, 최영진, Judy 여섯 명의 청년 작가가 모여 기획한 단체전. 작가들은 각자 '관계'를 탐구하고 고찰한다.
| 60.577778 | 538 | 0.689655 | kor_Hang | 1.00001 |
9bdfe78b2c8d50671f53bfbb9d117bf25ce5eb51 | 1,599 | md | Markdown | _posts/2019-08-03-Low-Dose-CT-via-Deep-CNN-with-Skip-Connection-and-Network-in-Network.md | AMDS123/papers | 80ccfe8c852685e4829848229b22ba4736c65a7c | [
"MIT"
] | 7 | 2018-02-11T01:50:19.000Z | 2020-01-14T02:07:17.000Z | _posts/2019-08-03-Low-Dose-CT-via-Deep-CNN-with-Skip-Connection-and-Network-in-Network.md | AMDS123/papers | 80ccfe8c852685e4829848229b22ba4736c65a7c | [
"MIT"
] | null | null | null | _posts/2019-08-03-Low-Dose-CT-via-Deep-CNN-with-Skip-Connection-and-Network-in-Network.md | AMDS123/papers | 80ccfe8c852685e4829848229b22ba4736c65a7c | [
"MIT"
] | 4 | 2018-02-04T15:58:04.000Z | 2019-08-29T14:54:14.000Z | ---
layout: post
title: "Low-Dose CT via Deep CNN with Skip Connection and Network in Network"
date: 2019-08-03 02:53:26
categories: arXiv_CV
tags: arXiv_CV Adversarial GAN CNN Quantitative
author: Chenyu You, Linfeng Yang, Yi Zhang, Ge Wang
mathjax: true
---
* content
{:toc}
##### Abstract
A major challenge in computed tomography (CT) is how to minimize patient radiation exposure without compromising image quality and diagnostic performance. The use of deep convolutional (Conv) neural networks for noise reduction in Low-Dose CT (LDCT) images has recently shown a great potential in this important application. In this paper, we present a highly efficient and effective neural network model for LDCT image noise reduction. Specifically, to capture local anatomical features we integrate Deep Convolutional Neural Networks (CNNs) and Skip connection layers for feature extraction. Also, we introduce parallelized $1\times 1$ CNN, called Network in Network, to lower the dimensionality of the output from the previous layer, achieving faster computational speed at less feature loss. To optimize the performance of the network, we adopt a Wasserstein generative adversarial network (WGAN) framework. Quantitative and qualitative comparisons demonstrate that our proposed network model can produce images with lower noise and more structural details than state-of-the-art noise-reduction methods.
##### Abstract (translated by Google)
##### URL
[http://arxiv.org/abs/1811.10564](http://arxiv.org/abs/1811.10564)
##### PDF
[http://arxiv.org/pdf/1811.10564](http://arxiv.org/pdf/1811.10564)
| 61.5 | 1,107 | 0.791119 | eng_Latn | 0.962326 |
9be2b7a93941caf6ebb0f0c0e51de4d79f1816c2 | 854 | md | Markdown | _posts/2011-08-12-affordable-digital-camcorders.md | BlogToolshed50/wellnessmanager.info | 1fe9abf2247ee71f84e83dde192888813364ebb8 | [
"CC-BY-4.0"
] | null | null | null | _posts/2011-08-12-affordable-digital-camcorders.md | BlogToolshed50/wellnessmanager.info | 1fe9abf2247ee71f84e83dde192888813364ebb8 | [
"CC-BY-4.0"
] | null | null | null | _posts/2011-08-12-affordable-digital-camcorders.md | BlogToolshed50/wellnessmanager.info | 1fe9abf2247ee71f84e83dde192888813364ebb8 | [
"CC-BY-4.0"
] | null | null | null | ---
id: 180
title: Affordable Digital Camcorders
date: 2011-08-12T18:34:42+00:00
author: admin
layout: post
guid: http://www.wellnessmanager.info/2011/08/12/affordable-digital-camcorders/
permalink: /2011/08/12/affordable-digital-camcorders/
categories:
- General
---
Anyone is planning to go for a trip with family and want to buy the best brand digital camera, you can find them at TheSource.ca. They offer the latest collection of digital cameras and digital [camcorders](http://www.thesource.ca/estore/category.aspx?language=en-CA&catalog=Online&category=digital-cameras-camcorders) with advanced features that meet all your digital photography needs. They carry the brands like Olympus, Canon, Sony, Fuji, and more, you can compare the features and choose the right brand for your needs and get the bright as well as perfect pictures for memories. | 71.166667 | 584 | 0.796253 | eng_Latn | 0.983582 |
9be372b39b6bbd0167832b53fa0f8d2c54ddd394 | 1,489 | md | Markdown | modulo_02/aula_07/README.md | gian8311/IPI | 0de6f7ac0b418542ddc19fbf5c09f05d69f22481 | [
"MIT"
] | null | null | null | modulo_02/aula_07/README.md | gian8311/IPI | 0de6f7ac0b418542ddc19fbf5c09f05d69f22481 | [
"MIT"
] | 1 | 2020-08-30T02:15:42.000Z | 2020-08-30T02:15:42.000Z | modulo_02/aula_07/README.md | gian8311/IPI | 0de6f7ac0b418542ddc19fbf5c09f05d69f22481 | [
"MIT"
] | null | null | null | <h1 align="center">👨🏻💻 INTRODUÇÃO À PROGRAMAÇÃO</h1>
## 🔨 Aula 7 - Atribuindo valores às variáveis
### Atribuição de valores
- O comando de atribuição _`=`_ é utilizado
- Exemplos
- Exemplo 1
- ```c
#include <stdio.h>
int main(void) {
int a;
a = 20;
return 0;
}
```
- No qual `a` recebe o valor `20`
- Exemplo 2
- ```c
#include <stdio.h>
int main(void) {
int a = 20;
return 0;
}
```
- No qual `a` recebe o valor `20`, porém dessa vez tudo feito na mesma linha
- Exemplo 3
- ```c
#include <stdio.h>
int main(void) {
int a, b;
a = b = 30;
return 0;
}
```
- No qual `a` e `b` recebem o valor `30`
- Exemplo 4
- ```c
#include <stdio.h>
int main(void) {
int a, b;
b = 100;
a = b;
return 0;
}
```
- No qual `b` recebe o valor `100` e `a` recebe o valor armazenado em `b` (_`100`_)
- Exemplo 5
- ```c
#include <stdio.h>
int main(void) {
int a;
float b;
b = 2.3;
a = b;
return 0;
}
```
- No qual `b` recebe o valor `2.3` e `a` recebe o valor armazenado em `b` (_`2.3`_) porém como `a` é um **inteiro** e `b` é um **real**, toda a parte depois da vírgula é **desconsiderada**. Sendo assim o valor de `a` passa a ser `2`
| 15.673684 | 236 | 0.457354 | por_Latn | 0.996805 |
9be39c7ca2624e1773160563d7e7a25e381fdae3 | 4,044 | md | Markdown | README.md | ScottHull/Field-Camp-Tools | 9a24cc5a041647d7baec09345a1cb02f60da78e5 | [
"CC0-1.0"
] | null | null | null | README.md | ScottHull/Field-Camp-Tools | 9a24cc5a041647d7baec09345a1cb02f60da78e5 | [
"CC0-1.0"
] | null | null | null | README.md | ScottHull/Field-Camp-Tools | 9a24cc5a041647d7baec09345a1cb02f60da78e5 | [
"CC0-1.0"
] | null | null | null | # Field-Camp-Tools
Tools I made at OSU Geology Field Camp, 2016.
_________________________________________________________________________________________________________________
TOOL 1: THREEPOINTPROBLEMI.PY
Three Point Problem Solver (work in progress)
Assists in the construction of a classic three point problem in geology.
By: Scott D. Hull, Field Camp 2016
This code is meant to be launched with Python 3 via the command terminal and is meant to be a calculator while the user is manually drawing the three point problem.
When prompted, enter (in feet) the elevation of your highest point, your lowest point, and an intermediate point. Then, enter the distance (in feet) from the lowest point to the highest point. The code will calculate and display the apparant dip as well as the distance from the highest point to the point where strike would intersect the line between the highest and lowest point.
Once this strike line is drawn on your paper, draw a line perpendicular from the strike line to the highest point. This should form a right triangle. Take the angle from the highest point to the strike line (within the right triangle) and enter when prompted. The code will calculate both the distance of this leg of the triangle (the distance from the highest point to where your perpendicular line intersects the strike line) as well as the true dip.
Disclaimer: This code is not finished. Please check your work and report any problems with the code to me.
_________________________________________________________________________________________________________________
TOOL 2: QUAD2AZI.PY
Quadrant to Azimuth Converter.
Converts quadrant compass measurements to azimuth.
By: Scott D. Hull, Field Camp 2016 (yeah, I got the quadrant compass)
Boot up 'quad2azi.py' with Python 3 via the command terminal.
Enter in a '.csv' file existing in the same directory as the python script at the prompt, formatted so that your quadrant measurements are in a single column, like in the following example:
N60W
S20E
N68E
The code will convert quadrant to azimuth notation and output a file called 'Quad2Azi_Out.csv', in which your quadrant measurements will be in the first column and the corresponding azimuth notation in the second.
_________________________________________________________________________________________________________________
TOOL 3: LITH_DESCR_MAKER.PY
Lithologic Description Maker.
Prints out an ordered lithologic description.
By: Scott D. Hull, Field Camp 2016
Boot up 'lith_descr_maker.py' in the command terminal with Python 3.
Enter in lithologic descriptions as prompted, and you may enter as may as you'd like per lithostratigraphic unit. A proper, ordered lithologic description will be printed at the end at saved to a file called "Lithologic_Description.txt'. This file will be deleted and recreated the next time the script is booted up.
_________________________________________________________________________________________________________________
TOOL 4: APPARENTDIPCALCULATOR.PY
Calculates apparent dip given true dip and angle between strike line and strike.
By: Scott D. Hull, Field Camp 2016
Boot up "apparentdipcalculator.py' in the command terminal with Python 3. Please make sure that all inputs, incluidng in .csv inputs, are in degrees. Please do not include dip direction in any inputs.
Enter either 'input' to manually enter in true dip and the angle between strike and the cross section line one at a time, or enter 'csv' to input a .csv file with multiple pairs of values. If inputting a .csv file, make sure that true dip is in the first column and the angle between the strike and the cross section line is in the second line. If using the .csv input, the program will not only output apparant dip to the screen but will write a file named "apparent_dip_outputs.txt' which will include true dip in the first column, the angle between the strike and the cross-section line in the second column, and the apparent dip in the third column.
| 54.648649 | 655 | 0.810831 | eng_Latn | 0.997399 |
9be5f615c106e644ebab49d370971bd5484a0982 | 579 | md | Markdown | README.md | alkorgun/urlcf | 3d8752ac94b4f57a07f8de2381ffbe53f815ebfb | [
"MIT"
] | 1 | 2017-07-06T02:10:23.000Z | 2017-07-06T02:10:23.000Z | README.md | alkorgun/urlcf | 3d8752ac94b4f57a07f8de2381ffbe53f815ebfb | [
"MIT"
] | null | null | null | README.md | alkorgun/urlcf | 3d8752ac94b4f57a07f8de2381ffbe53f815ebfb | [
"MIT"
] | null | null | null |
Urlcf URL Shortener
======
Tested under Python 2.7 on Ubuntu 14.04.
Runs on 80 with index on /.
* Install.
```bash
apt-get install python-flask python-sqlalchemy
wget -O urlcf.zip https://codeload.github.com/alkorgun/urlcf/zip/master
unzip urlcf.zip
rm urlcf.zip
cd urlcf-master
python setup.py install
```
* Test on **8080**.
```bash
urlcf-run8080
```
* Run as service.
```bash
service urlcf start
```
* Run on startup.
```bash
update-rc.d urlcf defaults
```
* Build **DEB**.
```bash
apt-get install python-stdeb
cd urlcf-master
./build_deb.sh
```
| 9.33871 | 71 | 0.670121 | kor_Hang | 0.27466 |
9be611082e053198ab16a5a93287dffb381d2adf | 490 | md | Markdown | site/content/tools/grunt.md | sagannotcarl/mattfinucane.com | 7384fd6e60204560bd9599e4917b761805f7e41a | [
"MIT"
] | 7 | 2017-05-14T18:13:54.000Z | 2020-03-26T10:48:22.000Z | site/content/tools/grunt.md | sagannotcarl/mattfinucane.com | 7384fd6e60204560bd9599e4917b761805f7e41a | [
"MIT"
] | 7 | 2017-05-12T07:13:27.000Z | 2019-07-06T19:55:12.000Z | site/content/tools/grunt.md | sagannotcarl/mattfinucane.com | 7384fd6e60204560bd9599e4917b761805f7e41a | [
"MIT"
] | 1 | 2019-02-04T14:19:00.000Z | 2019-02-04T14:19:00.000Z | ---
title: "Grunt"
description: "Grunt is an automated task runner for Javascript applications."
proficiency: 3
identifier: "home"
deprecated: true
---
## What is it?
[Grunt](https://gruntjs.com/) is a Javascript task runner commonly used when deploying applications. It carries out tasks such as copying files, concatenating source code and then compressing it.
## Projects
{{% categorised_projects taxonomy="tools" term="Grunt" %}}
## Deprecation
WebPack is a better tool to use.
| 28.823529 | 195 | 0.746939 | eng_Latn | 0.992051 |
9be62b17a652806574bca0aeaf75053d0fdee127 | 261 | md | Markdown | wp-content/themes/pai/README.md | TruePai/wp-pai-theme | e1f26185c9e4505bcbd008a2054c880bf393239f | [
"MIT"
] | 1 | 2021-02-02T08:12:53.000Z | 2021-02-02T08:12:53.000Z | wp-content/themes/pai/README.md | TruePai/wp-pai-theme | e1f26185c9e4505bcbd008a2054c880bf393239f | [
"MIT"
] | null | null | null | wp-content/themes/pai/README.md | TruePai/wp-pai-theme | e1f26185c9e4505bcbd008a2054c880bf393239f | [
"MIT"
] | null | null | null | ## Requirements
- Advanced Custom Field Pro plugin
- PHP 7.0+
- Wordpress 5.2.4+
## Installation
```
npm i -g gulp-cli
cd dev
npm i
```
## Build
#### Compile SCSS
```cmd
gulp styles
```
#### Optimize JS
```
gulp scripts
```
#### Build all
```
gulp build
``` | 9.666667 | 34 | 0.601533 | kor_Hang | 0.584844 |
9be6d279e38ed661d0b3658d9db5bf70162f0d1e | 21 | md | Markdown | README.md | carmenmateos/backend-shop-online | 48d06732b8140b22e49d19ed9c18aff0b4c60cff | [
"MIT"
] | null | null | null | README.md | carmenmateos/backend-shop-online | 48d06732b8140b22e49d19ed9c18aff0b4c60cff | [
"MIT"
] | null | null | null | README.md | carmenmateos/backend-shop-online | 48d06732b8140b22e49d19ed9c18aff0b4c60cff | [
"MIT"
] | null | null | null | # backend-shop-online | 21 | 21 | 0.809524 | dan_Latn | 0.547695 |
9be74b15cc0218341b85a942ee6af0f5c89d3c0e | 28 | md | Markdown | README.md | verekia/yarn-workspaces-playground | 28480929d63f25f5b76adb9843e3aab77dcf1c54 | [
"MIT"
] | null | null | null | README.md | verekia/yarn-workspaces-playground | 28480929d63f25f5b76adb9843e3aab77dcf1c54 | [
"MIT"
] | null | null | null | README.md | verekia/yarn-workspaces-playground | 28480929d63f25f5b76adb9843e3aab77dcf1c54 | [
"MIT"
] | null | null | null | # yarn-workspaces-playground | 28 | 28 | 0.857143 | eng_Latn | 0.420882 |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.