id
stringlengths 13
19
| title
stringlengths 0
256
| description
stringlengths 3
13.3k
| cpes
listlengths 0
5.42k
|
|---|---|---|---|
GHSA-crh9-ppwm-j9xc
|
In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the GSS-API dissector could crash. This was addressed in epan/dissectors/packet-gssapi.c by ensuring that a valid dissector is called.
|
[] |
|
GHSA-mmcv-w5m4-3p9m
|
MediaWiki before 1.19.24, 1.2x before 1.23.9, and 1.24.x before 1.24.2, when using HHVM, allows remote attackers to cause a denial of service (CPU and memory consumption) via a large number of nested entity references in an (1) SVG file or (2) XMP metadata in a PDF file, aka a "billion laughs attack," a different vulnerability than CVE-2015-2937.
|
[] |
|
CVE-2025-30613
|
WordPress Nmedia MailChimp plugin <= 5.4 - Cross Site Scripting (XSS) Vulnerability
|
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in N-Media Nmedia MailChimp allows Stored XSS. This issue affects Nmedia MailChimp: from n/a through 5.4.
|
[] |
GHSA-6xfq-wgr5-vqc6
|
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Tripetto WordPress form builder plugin for contact forms, surveys and quizzes – Tripetto allows Stored XSS.This issue affects WordPress form builder plugin for contact forms, surveys and quizzes – Tripetto: from n/a through 8.0.5.
|
[] |
|
GHSA-jv4w-rfq7-wmcq
|
IBM EntireX 11.1 could allow a local user to obtain sensitive information when a detailed technical error message is returned. This information could be used in further attacks against the system.
|
[] |
|
CVE-2018-2649
|
Vulnerability in the Oracle FLEXCUBE Universal Banking component of Oracle Financial Services Applications (subcomponent: Infrastructure). Supported versions that are affected are 11.3.0, 11.4.0, 12.0.1, 12.0.2, 12.0.3, 12.1.0, 12.2.0, 12.3.0 and 12.4.0. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle FLEXCUBE Universal Banking. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Oracle FLEXCUBE Universal Banking accessible data and unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle FLEXCUBE Universal Banking. CVSS 3.0 Base Score 8.1 (Integrity and Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:H).
|
[
"cpe:2.3:a:oracle:flexcube_universal_banking:11.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:11.4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:flexcube_universal_banking:12.4.0:*:*:*:*:*:*:*"
] |
|
CVE-2014-3497
|
Cross-site scripting (XSS) vulnerability in OpenStack Swift 1.11.0 through 1.13.1 allows remote attackers to inject arbitrary web script or HTML via the WWW-Authenticate header.
|
[
"cpe:2.3:a:openstack:swift:1.11.0:*:*:*:*:*:*:*",
"cpe:2.3:a:openstack:swift:1.12.0:*:*:*:*:*:*:*",
"cpe:2.3:a:openstack:swift:1.13.0:*:*:*:*:*:*:*",
"cpe:2.3:a:openstack:swift:1.13.1:*:*:*:*:*:*:*",
"cpe:2.3:a:openstack:swift:1.13.1:rc1:*:*:*:*:*:*",
"cpe:2.3:a:openstack:swift:1.13.1:rc2:*:*:*:*:*:*"
] |
|
GHSA-mcx7-xrrv-484m
|
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Colin Tomele Board Document Manager from CHUHPL allows Reflected XSS.This issue affects Board Document Manager from CHUHPL: from n/a through 1.9.1.
|
[] |
|
CVE-2021-21557
|
Dell PowerEdge Server BIOS and select Dell Precision Rack BIOS contain an out-of-bounds array access vulnerability. A local malicious user with high privileges may potentially exploit this vulnerability, leading to a denial of service, arbitrary code execution, or information disclosure in System Management Mode.
|
[
"cpe:2.3:o:dell:poweredge_r640_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r640:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r740_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r740:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r740xd_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r740xd:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r940_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r940:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r540_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r540:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r440_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r440:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_t440_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_t440:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_xr2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_xr2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r740xd2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r740xd2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r840_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r840:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r940xa_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r940xa:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_t640_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_t640:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_c6420_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_c6420:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_fc640_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_fc640:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_m640_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_m640:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_m640p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_m640p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_mx740c_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_mx740c:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_mx840c_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_mx840c:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_c4140_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_c4140:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_t140_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_t140:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_t340_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_t340:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r240_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r240:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r340_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r340:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r6415_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r6415:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r7415_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r7415:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r7425_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r7425:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r6515_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r6515:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r7515_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r7515:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r6525_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r6525:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_r7525_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_r7525:-:*:*:*:*:*:*:*",
"cpe:2.3:o:dell:poweredge_c6525_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:dell:poweredge_c6525:-:*:*:*:*:*:*:*"
] |
|
CVE-2006-0932
|
Directory traversal vulnerability in zip.lib.php 0.1.1 in PEAR::Archive_Zip allows remote attackers to create and overwrite arbitrary files via certain crafted pathnames in a ZIP archive.
|
[
"cpe:2.3:a:pear:pear_archive_zip:1.1:*:*:*:*:*:*:*"
] |
|
CVE-2017-16556
|
In K7 Antivirus Premium before 15.1.0.53, user-controlled input can be used to allow local users to write to arbitrary memory locations.
|
[
"cpe:2.3:a:k7computing:antivirus:*:*:*:*:premium:*:*:*",
"cpe:2.3:a:k7computing:antivirus:*:*:*:*:plus:*:*:*",
"cpe:2.3:a:k7computing:endpoint:*:*:*:*:*:*:*:*",
"cpe:2.3:a:k7computing:internet_security:*:*:*:*:*:*:*:*",
"cpe:2.3:a:k7computing:total_security:*:*:*:*:*:*:*:*",
"cpe:2.3:a:k7computing:total_security:*:*:*:*:plus:*:*:*",
"cpe:2.3:a:k7computing:ultimate_security:*:*:*:*:*:*:*:*"
] |
|
CVE-2006-4234
|
PHP remote file inclusion vulnerability in classes/query.class.php in dotProject 2.0.4 and earlier allows remote attackers to execute arbitrary PHP code via a URL in the baseDir parameter.
|
[
"cpe:2.3:a:dotproject:dotproject:2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:dotproject:dotproject:2.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:dotproject:dotproject:2.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:dotproject:dotproject:2.0.4:*:*:*:*:*:*:*"
] |
|
CVE-2005-4227
|
Multiple "potential" SQL injection vulnerabilities in DCP-Portal 6.1.1 might allow remote attackers to execute arbitrary SQL commands via (1) the password and username parameters in advertiser.php, (2) the aid parameter in announcement.php, (3) the dcp5_member_id, year, agid, day, day_s, hour, minute, month, month_s, and year_s parameters in calendar.php, (4) the cid parameter in contents.php, (5) the dcp5_member_id parameter in forums.php, (6) the bid parameter in go.php, (7) the lid parameter in golink.php, (8) the dcp5_member_id and mid parameters in inbox.php, (9) the catid, dcat, and dl parameters in index.php, (10) the dcp5_member_id in informer.php, (11) the nid parameter in news.php, (12) the type and rate parameters in rate.php, (13) the q parameter in search.php, and (14) the dcp5_member_id in update.php. NOTE: other vectors in the PHP-CHECKER report are also covered by CVE-2005-3365 and CVE-2005-0454.
|
[
"cpe:2.3:a:codeworx_technologies:dcp-portal:3.7:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:4.5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.2:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.3:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:5.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:6.1:*:*:*:*:*:*:*",
"cpe:2.3:a:codeworx_technologies:dcp-portal:6.1.1:*:*:*:*:*:*:*"
] |
|
GHSA-whjw-qrgv-pm72
|
Cybozu Garoon 4.0.0 to 5.0.1 allows remote authenticated attackers to bypass access restriction to alter the data for the file attached to Report via unspecified vectors.
|
[] |
|
GHSA-64g3-cj3g-3566
|
A NULL pointer dereference was discovered in newVar3 in util/decompile.c in libming 0.4.8. The vulnerability causes a segmentation fault and application crash, which leads to denial of service.
|
[] |
|
CVE-2013-3050
|
SQL injection vulnerability in ZAPms 1.41 and earlier allows remote attackers to execute arbitrary SQL commands via the pid parameter to product.
|
[
"cpe:2.3:a:zapms:zapms:*:*:*:*:*:*:*:*",
"cpe:2.3:a:zapms:zapms:1.33:*:*:*:*:*:*:*",
"cpe:2.3:a:zapms:zapms:1.40:*:*:*:*:*:*:*"
] |
|
GHSA-r837-6rm6-h9pj
|
Authentication bypass by capture-replay vulnerability exists in Machine automation controller NJ series all models V 1.48 and earlier, Machine automation controller NX7 series all models V1.28 and earlier, Machine automation controller NX1 series all models V1.48 and earlier, Automation software 'Sysmac Studio' all models V1.49 and earlier, and Programmable Terminal (PT) NA series NA5-15W/NA5-12W/NA5-9W/NA5-7W models Runtime V1.15 and earlier, which may allow a remote attacker who can analyze the communication between the affected controller and automation software 'Sysmac Studio' and/or a Programmable Terminal (PT) to access the controller.
|
[] |
|
GHSA-w8c3-84vf-2vq8
|
A vulnerability was found in Bug Finder Wedding Wonders 1.0. It has been classified as problematic. Affected is an unknown function of the file /user/ticket/create of the component Ticket Handler. The manipulation of the argument message leads to cross site scripting. It is possible to launch the attack remotely. VDB-235158 is the identifier assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way.
|
[] |
|
CVE-2008-0028
|
Unspecified vulnerability in Cisco PIX 500 Series Security Appliance and 5500 Series Adaptive Security Appliance (ASA) before 7.2(3)6 and 8.0(3), when the Time-to-Live (TTL) decrement feature is enabled, allows remote attackers to cause a denial of service (device reload) via a crafted IP packet.
|
[
"cpe:2.3:o:cisco:adaptive_security_appliance_software:*:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:adaptive_security_appliance_software:8.0\\(3\\):*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:pix_firewall_software:*:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:pix_firewall_software:8.0\\(3\\):*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:5500_series_adaptive_security_appliance:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:pix_500:-:*:*:*:*:*:*:*"
] |
|
CVE-2022-49563
|
crypto: qat - add param check for RSA
|
In the Linux kernel, the following vulnerability has been resolved:
crypto: qat - add param check for RSA
Reject requests with a source buffer that is bigger than the size of the
key. This is to prevent a possible integer underflow that might happen
when copying the source scatterlist into a linear buffer.
|
[] |
GHSA-q64h-3pq3-w59f
|
Remote Code Execution in the TCL script interpreter in eQ-3 AG Homematic CCU2 2.29.2 and earlier allows remote attackers to obtain read/write access and execute system commands on the device. This vulnerability can be exploited by unauthenticated attackers with access to the web interface.
|
[] |
|
GHSA-m474-22p6-39cr
|
Possibility of null pointer deference as the array of video codecs from media info is referenced without null checking while processing SDP messages in Snapdragon Auto, Snapdragon Compute, Snapdragon Consumer IOT, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wearables in MSM8905, MSM8909, MSM8917, MSM8920, MSM8937, MSM8940, MSM8953, Nicobar, QCM2150, QM215, Rennell, SC7180, SC8180X, SDA845, SDM429, SDM439, SDM450, SDM632, SDM845, SDM850, SDX24, SM6150, SM7150, SM8150
|
[] |
|
CVE-2024-0128
|
NVIDIA vGPU software contains a vulnerability in the Virtual GPU Manager that allows a user of the guest OS to access global resources. A successful exploit of this vulnerability might lead to information disclosure, data tampering, and escalation of privileges.
|
[
"cpe:2.3:a:nvidia:virtual_gpu_manager:*:*:*:*:*:*:*:*",
"cpe:2.3:a:nvidia:cloud_gaming_virtual_gpu:*:*:*:*:*:*:*:*"
] |
|
CVE-2025-25685
|
An issue was discovered in GL-INet Beryl AX GL-MT3000 v4.7.0. Attackers are able to download arbitrary files from the device's file system via adding symbolic links on an external drive used as a samba share.
|
[] |
|
GHSA-gc8m-99qv-67w4
|
In BIG-IP 14.0.0-14.0.0.2, 13.0.0-13.1.0.7, 12.1.0-12.1.3.5, 11.6.1-11.6.3.2, or 11.5.1-11.5.8 or Enterprise Manager 3.1.1, malformed requests to the Traffic Management User Interface (TMUI), also referred to as the BIG-IP Configuration utility, may lead to disruption of TMUI services. This attack requires an authenticated user with any role (other than the No Access role). The No Access user role cannot login and does not have the access level to perform the attack.
|
[] |
|
CVE-2022-28300
|
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Bentley MicroStation 10.16.02.034 CONNECT. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of JP2 images. Crafted data in a JP2 file can trigger a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-16202.
|
[
"cpe:2.3:a:bentley:microstation:*:*:*:*:*:*:*:*",
"cpe:2.3:a:bentley:view:*:*:*:*:*:*:*:*"
] |
|
CVE-2013-4356
|
Xen 4.3.x writes hypervisor mappings to certain shadow pagetables when live migration is performed on hosts with more than 5TB of RAM, which allows local 64-bit PV guests to read or write to invalid memory and cause a denial of service (crash).
|
[
"cpe:2.3:o:xen:xen:4.3.0:*:*:*:*:*:*:*"
] |
|
GHSA-3h2r-mh7w-gr5w
|
Authenticated (shop manager+) Reflected Cross-Site Scripting (XSS) vulnerability in AlgolPlus Advanced Order Export For WooCommerce plugin <= 3.3.1 at WordPress.
|
[] |
|
GHSA-53qp-p4j3-jj3w
|
An privilege elevation vulnerability exists in Cloud-init before 0.7.0 when requests to an untrusted system are submitted for EC2 instance data.
|
[] |
|
CVE-2018-6484
|
In ZZIPlib 0.13.67, there is a memory alignment error and bus error in the __zzip_fetch_disk_trailer function of zzip/zip.c. Remote attackers could leverage this vulnerability to cause a denial of service via a crafted zip file.
|
[
"cpe:2.3:a:zziplib_project:zziplib:0.13.67:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:14.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:17.10:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*"
] |
|
CVE-2017-3888
|
A vulnerability in the web-based management interface of Cisco Unified Communications Manager could allow an authenticated, remote attacker to conduct a reflected cross-site scripting (XSS) attack against a user of the web-based management interface of an affected device. This vulnerability affects Cisco Unified Communications Manager with a default configuration running an affected software release with the attacker authenticated as the administrative user. More Information: CSCvc83712. Known Affected Releases: 12.0(0.98000.452). Known Fixed Releases: 12.0(0.98000.750) 12.0(0.98000.708) 12.0(0.98000.707) 12.0(0.98000.704) 12.0(0.98000.554) 12.0(0.98000.546) 12.0(0.98000.543) 12.0(0.98000.248) 12.0(0.98000.244) 12.0(0.98000.242).
|
[
"cpe:2.3:a:cisco:unified_communications_manager:12.0\\(0.98000.452\\):*:*:*:*:*:*:*"
] |
|
CVE-2023-37658
|
fast-poster v2.15.0 is vulnerable to Cross Site Scripting (XSS). File upload check binary of img, but without strictly check file suffix at /server/fast.py -> ApiUploadHandler.post causes stored XSS
|
[
"cpe:2.3:a:fastposter:fast-poster:2.15.0:*:*:*:*:*:*:*"
] |
|
GHSA-f362-3wmq-4vf5
|
Microsoft Office Security Feature Bypass Vulnerability.
|
[] |
|
GHSA-h8qw-xqm9-q66j
|
An issue was discovered in Mattermost Server before 3.1.0. It allows XSS via theme color-code values.
|
[] |
|
GHSA-37hr-rhw9-q43g
|
Format string vulnerability in TrACESroute 6.0 GOLD (aka NANOG traceroute) allows local users to execute arbitrary code via the -T (terminator) command line argument.
|
[] |
|
GHSA-6wh6-h5jg-ghcx
|
Vulnerability in the Oracle Applications Framework product of Oracle E-Business Suite (component: Personalization). Supported versions that are affected are 12.2.3-12.2.12. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Applications Framework. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Applications Framework, attacks may significantly impact additional products (scope change). Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Applications Framework accessible data as well as unauthorized read access to a subset of Oracle Applications Framework accessible data. CVSS 3.1 Base Score 6.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N).
|
[] |
|
CVE-2023-31714
|
Chitor-CMS before v1.1.2 was discovered to contain multiple SQL injection vulnerabilities.
|
[
"cpe:2.3:a:waqaskanju:chitor-cms:*:*:*:*:*:*:*:*"
] |
|
GHSA-g8h8-pg73-gcw3
|
An issue was discovered in Acuant AcuFill SDK before 10.22.02.03. During installation, an EXE gets executed out of C:\Windows\Temp. A standard user can create the path file ahead of time and obtain elevated code execution. Permissions need to be modified to prevent manipulation.
|
[] |
|
GHSA-5phf-q389-vx4x
|
Buffer overflow in the calc_coeff function in libass/ass_blur.c in libass before 0.13.4 allows remote attackers to cause a denial of service via unspecified vectors.
|
[] |
|
GHSA-pgq6-ccqj-hpqr
|
Elasticsearch privilege escalation
|
A flaw was discovered in Elasticsearch 7.17.0’s upgrade assistant, in which upgrading from version 6.x to 7.x would disable the in-built protections on the security index, allowing authenticated users with “*” index permissions access to this index. Users running a cluster on an affected version that had previously been upgraded from 6.x, should upgrade to 7.17.1. Users that are planning to upgrade from 6.x should not perform an upgrade from 6.x to versions 7.16 through 7.17.0 and should use 7.17.1+ for upgrades from 6.x.
|
[] |
CVE-2024-27386
|
A vulnerability was discovered in the slsi_handle_nan_rx_event_log_ind function in Samsung Mobile Processor Exynos 1380 and Exynos 1480 related to no input validation check on tag_len for tx coming from userspace, which can lead to heap overwrite.
|
[
"cpe:2.3:h:samsung:exynos_1380:-:*:*:*:*:*:*:*",
"cpe:2.3:h:samsung:exynos_1480:-:*:*:*:*:*:*:*"
] |
|
GHSA-6jxh-gmwr-m73p
|
MonicaHQ version 4.0.0 allows an authenticated remote attacker to execute malicious code in the application via CSTI in the `people:id/introductions` endpoint and first_met_additional_info parameter.
|
[] |
|
GHSA-vh83-jr96-3v3h
|
B1i module of SAP Business One - version 10.0, application allows an authenticated user with deep knowledge to send crafted queries over the network to read or modify the SQL data. On successful exploitation, the attacker can cause high impact on confidentiality, integrity and availability of the application.
|
[] |
|
GHSA-gcmj-72p6-4pf5
|
An issue was discovered on Momentum Axel 720P 5.1.8 devices. Custom Firmware Upgrade is possible via an SD Card. With physical access, an attacker can upgrade the firmware in under 60 seconds by inserting an SD card containing the firmware with name 'ezviz.dav' and rebooting.
|
[] |
|
GHSA-cqqm-8g3r-4grm
|
The Nokaut Offers Box WordPress plugin through 1.4.0 does not have CSRF check in place when updating its settings, which could allow attackers to make a logged in admin reset the Nokaut Offers Box WordPress plugin through 1.4.0 via a CSRF attack
|
[] |
|
GHSA-grmj-gpwm-98ww
|
Moodle Cross-site Scripting vulnerability
|
The vulnerability was found Moodle which exists due to insufficient sanitization of user-supplied data in blog search. A remote attacker can trick the victim to follow a specially crafted link and execute arbitrary HTML and script code in user's browser in context of vulnerable website. This flaw allows a remote attacker to perform cross-site scripting (XSS) attacks.
|
[] |
CVE-2024-36410
|
SuiteCRM authenticated SQL Injection in EmailUIAjax messages count controller
|
SuiteCRM is an open-source Customer Relationship Management (CRM) software application. In versions prior to 7.14.4 and 8.6.1, poor input validation allows for SQL Injection in EmailUIAjax messages count controller. Versions 7.14.4 and 8.6.1 contain a fix for this issue.
|
[
"cpe:2.3:a:salesagility:suitecrm:*:*:*:*:*:*:*:*"
] |
GHSA-xw3g-f28m-3q7j
|
An issue in personal-management-system Personal Management System 1.4.65 allows a remote attacker to obtain sensitive information via the Travel Ideas" function.
|
[] |
|
CVE-2017-3458
|
Vulnerability in the MySQL Server component of Oracle MySQL (subcomponent: Server: DML). Supported versions that are affected are 5.7.17 and earlier. Easily "exploitable" vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server. CVSS 3.0 Base Score 4.9 (Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H).
|
[
"cpe:2.3:a:oracle:mysql:*:*:*:*:*:*:*:*"
] |
|
GHSA-5vpp-fv65-gw43
|
Path Traversal: '.../...//' vulnerability in VibeThemes WPLMS allows Path Traversal.This issue affects WPLMS: from n/a before 1.9.9.5.2.
|
[] |
|
CVE-2019-14511
|
Sphinx Technologies Sphinx 3.1.1 by default has no authentication and listens on 0.0.0.0, making it exposed to the internet (unless filtered by a firewall or reconfigured to listen to 127.0.0.1 only).
|
[
"cpe:2.3:a:sphinxsearch:sphinx:3.1.1:*:*:*:*:*:*:*"
] |
|
CVE-2025-7566
|
jshERP SystemConfigController.java exportExcelByParam path traversal
|
A vulnerability has been found in jshERP up to 3.5 and classified as critical. This vulnerability affects the function exportExcelByParam of the file /src/main/java/com/jsh/erp/controller/SystemConfigController.java. The manipulation of the argument Title leads to path traversal. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
|
[] |
CVE-2021-27152
|
An issue was discovered on FiberHome HG6245D devices through RP2613. The web daemon contains the hardcoded awnfibre / fibre@dm!n credentials for an ISP.
|
[
"cpe:2.3:o:fiberhome:hg6245d_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:fiberhome:hg6245d:-:*:*:*:*:*:*:*"
] |
|
CVE-2018-7439
|
An issue was discovered in FreeXL before 1.0.5. There is a heap-based buffer over-read in the function read_mini_biff_next_record.
|
[
"cpe:2.3:a:freexl_project:freexl:*:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:7.0:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*"
] |
|
CVE-2020-18131
|
Cross Site Request Forgery (CSRF) vulnerability in Bluethrust Clan Scripts v4 allows attackers to escilate privledges to an arbitrary account via a crafted request to /members/console.php?cID=5.
|
[
"cpe:2.3:a:clanscripts_project:clanscripts:4.0:*:*:*:*:*:*:*"
] |
|
GHSA-85vx-v88h-wg26
|
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Wouter Dijkstra DD Rating allows Stored XSS.This issue affects DD Rating: from n/a through 1.7.1.
|
[] |
|
GHSA-cwq8-g58r-32hg
|
MinIO vulnerable to privilege escalation in IAM import API
|
ImpactPrivilege escalation in IAM import API, all users are impacted since MinIO commit 580d9db85e04f1b63cc2909af50f0ed08afa965fPatchesWorkaroundsThere are no workarounds possible, all users are advised to upgrade immediately if you don't run MinIO behind a load balancer.Behind a load balancer / firewall such as `nginx` .Following locations can be blocked from external access, temporarily disallowing the API calls completely until the deployments can be upgraded.ReferencesRefer https://github.com/minio/minio/pull/20756 for more informationBinary ReleasesAiStor ContainersAiStor BinariesArchitecture: `linux/amd64`https://dl.min.io/aistor/minio/release/linux-amd64/archive/minio.RELEASE.2024-12-13T13-42-41ZArchitecture: `linux/arm64`https://dl.min.io/aistor/minio/release/linux-arm64/archive/minio.RELEASE.2024-12-13T13-42-41ZArchitecture: `windows/amd64`https://dl.min.io/aistor/minio/release/windows-amd64/archive/minio.RELEASE.2024-12-13T13-42-41ZCommunity ContainersCommunity BinariesArchitecture: `linux/amd64`https://dl.min.io/server/minio/release/linux-amd64/archive/minio.RELEASE.2024-12-13T22-19-12ZArchitecture: `linux/arm64`https://dl.min.io/server/minio/release/linux-arm64/archive/minio.RELEASE.2024-12-13T22-19-12ZArchitecture: `windows/amd64`https://dl.min.io/server/minio/release/windows-amd64/archive/minio.RELEASE.2024-12-13T22-19-12ZCreditsCredit goes to [National Security Agency](https://www.nsa.gov/) for reporting this issue.
|
[] |
GHSA-mq4v-fvj7-qhmj
|
The installation confirmation dialog in Firefox before 1.0.1, Thunderbird before 1.0.1, and Mozilla before 1.7.6 allows remote attackers to use InstallTrigger to spoof the hostname of the host performing the installation via a long "user:pass" sequence in the URL, which appears before the real hostname.
|
[] |
|
GHSA-5jg2-4xpf-rvpc
|
bloofoxCMS v0.5.2.1 was discovered to contain an arbitrary file deletion vulnerability via the component /include/inc_content_media.php.
|
[] |
|
GHSA-h42x-xx2q-6v6g
|
Flowise Pre-auth Arbitrary File Upload
|
SummaryAn unauthorized attacker can leverage the whitelisted route `/api/v1/attachments` to upload arbitrary files when the `storageType` is set to **local** (default).DetailsWhen a new request arrives, the system first checks if the URL starts with `/api/v1/`. If it does, the system then verifies whether the URL is included in the whitelist (*whitelistURLs*). If the URL is whitelisted, the request proceeds; otherwise, the system enforces authentication.@ */packages/server/src/index.ts***The whitelist is defined as follows**This means that every route in the whitelist does not require authentication. Now, let's examine the `/api/v1/attachments` route.@ */packages/server/src/routes/attachments/index.ts*After several calls, the request reaches the `createFileAttachment` function @ (*packages/server/src/utils/createAttachment.ts*)
Initially, the function retrieves *chatflowid* and *chatId* from the request without any additional validation. The only check performed is whether these parameters exist in the request.Next, the function retrieves the uploaded files and attempts to add them to the storage by calling the `addArrayFilesToStorage` function.Now lets take a look at `addArrayFilesToStorage` function @ (*/packages/components/src/storageUtils.ts*)As noted in the comment, to construct the directory, the function joins the output of the `getStoragePath` function with `...paths`, which are essentially the `chatflowid` and `chatId` extracted earlier from the request.
However, as mentioned previously, these values are not validated to ensure they are UUIDs or numbers. As a result, an attacker could manipulate these variables to set the **dir** variable to any value.
Combined with the fact that the filename is also provided by the user, this leads to **unauthenticated arbitrary file upload**.POCThis is the a HTTP request. As observed, we are not authenticated, and by manipulating the `chatId` parameter, we can perform a path traversal. In this example, we overwrite the `api.json` file, which contains the API keys for the system.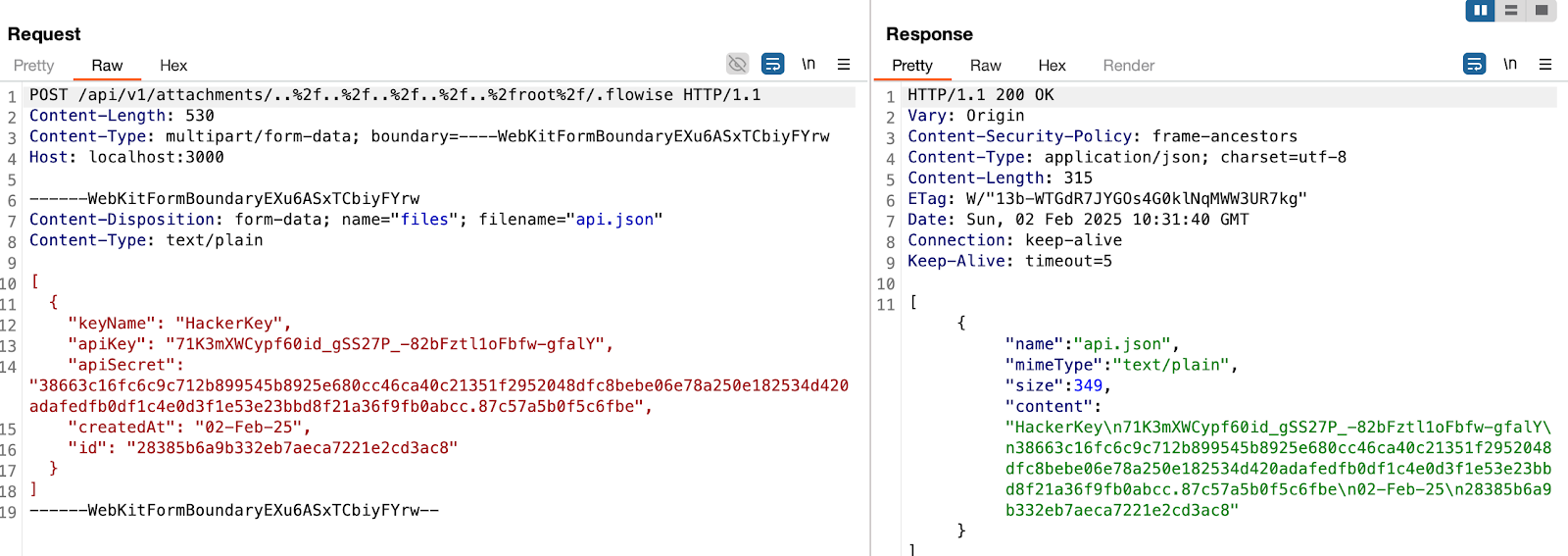in this example, the **dir** variable will beand the file name is `api.json`And the API Keys in the UI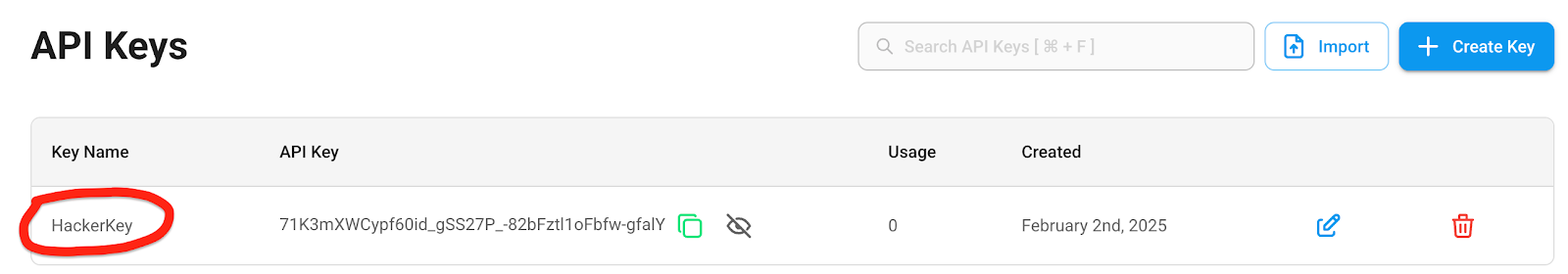ImpactThis vulnerability could potentially lead toRemote Code ExecutionServer TakeoverData Theft
And more
|
[] |
GHSA-gfgp-pwhh-84rx
|
An issue was discovered in yiqicms through 2016-11-20. There is stored XSS in comment.php because a length limit can be bypassed.
|
[] |
|
CVE-2008-7194
|
Unspecified vulnerability in Fujitsu Interstage HTTP Server, as used in Interstage Application Server 5.0, 7.0, 7.0.1, and 8.0.0 for Windows, allows attackers to cause a denial of service via a crafted request.
|
[
"cpe:2.3:a:fujitsu:interstage_application_server:5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:5.0:*:enterprise:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:5.0:*:standard:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:5.0:*:standard_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:5.0:*:web_j:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:5.0:*:web_j_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:enterprise:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:enterprise_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:plus:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:plus_developer:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:plus_developer_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:plus_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0:*:standard:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0.1:*:enterprise:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0.1:*:enterprise_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0.1:*:plus:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:7.0.1:*:plus_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:8.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:8.0.0:*:enterprise:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:8.0.0:*:enterprise_windows:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:8.0.0:*:standard_j:*:*:*:*:*",
"cpe:2.3:a:fujitsu:interstage_application_server:8.0.0:*:standard_j_windows:*:*:*:*:*"
] |
|
CVE-2001-0857
|
Cross-site scripting vulnerability in status.php3 in Imp Webmail 2.2.6 and earlier allows remote attackers to gain access to the e-mail of other users by hijacking session cookies via the message parameter.
|
[
"cpe:2.3:a:imp:webmail:*:*:*:*:*:*:*:*"
] |
|
CVE-2006-1846
|
Cross-site scripting (XSS) vulnerability in the Your_Account module in PHP-Nuke 7.8 might allows remote attackers to inject arbitrary HTML and web script via the ublock parameter, which is saved in the user's personal menu. NOTE: the provenance of this information is unknown; the details are obtained solely from third party information. In addition, it is unclear whether this issue is a vulnerability, since it is related to the user's personal menu, which presumably is not modifiable by others.
|
[
"cpe:2.3:a:francisco_burzi:php-nuke:7.8:*:*:*:*:*:*:*"
] |
|
CVE-2011-1016
|
The Radeon GPU drivers in the Linux kernel before 2.6.38-rc5 do not properly validate data related to the AA resolve registers, which allows local users to write to arbitrary memory locations associated with (1) Video RAM (aka VRAM) or (2) the Graphics Translation Table (GTT) via crafted values.
|
[
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.38:-:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.38:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.38:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.38:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.38:rc4:*:*:*:*:*:*"
] |
|
CVE-2018-14252
|
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Foxit Reader 9.0.1.1049. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the getField method. By performing actions in JavaScript, an attacker can trigger a type confusion condition. An attacker can leverage this vulnerability to execute code under the context of the current process. Was ZDI-CAN-6015.
|
[
"cpe:2.3:a:foxitsoftware:foxit_reader:*:*:*:*:*:*:*:*",
"cpe:2.3:a:foxitsoftware:phantompdf:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] |
|
CVE-2012-5306
|
Stack-based buffer overflow in the SelectDirectory method in DcsCliCtrl.dll in Camera Stream Client ActiveX Control, as used in D-Link DCS-5605 PTZ IP Network Camera, allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a long string argument.
|
[
"cpe:2.3:a:dlink:camera_stream_client_activex_control:1.0.0.4519:*:*:*:*:*:*:*",
"cpe:2.3:h:dlink:dcs-5605_ptz_ip_network_camera:-:*:*:*:*:*:*:*"
] |
|
CVE-2007-4392
|
Winamp 5.35 allows remote attackers to cause a denial of service (program stack overflow and application crash) via an M3U file that recursively includes itself.
|
[
"cpe:2.3:a:nullsoft:winamp:5.35:*:*:*:*:*:*:*"
] |
|
CVE-2011-4622
|
The create_pit_timer function in arch/x86/kvm/i8254.c in KVM 83, and possibly other versions, does not properly handle when Programmable Interval Timer (PIT) interrupt requests (IRQs) when a virtual interrupt controller (irqchip) is not available, which allows local users to cause a denial of service (NULL pointer dereference) by starting a timer.
|
[
"cpe:2.3:a:redhat:kvm:83:*:*:*:*:*:*:*"
] |
|
CVE-2008-5851
|
SQL injection vulnerability in index.php in My PHP Baseball Stats (MyPBS) allows remote attackers to execute arbitrary SQL commands via the seasonID parameter.
|
[
"cpe:2.3:a:mypbs:mypbs:_nil_:*:*:*:*:*:*:*"
] |
|
CVE-2008-3570
|
PHP remote file inclusion vulnerability in index.php in Africa Be Gone (ABG) 1.0a allows remote attackers to execute arbitrary PHP code via a URL in the abg_path parameter.
|
[
"cpe:2.3:a:africabegone:africa_be_gone:1.0a:*:*:*:*:*:*:*"
] |
|
CVE-2024-0466
|
code-projects Employee Profile Management System file_table.php sql injection
|
A vulnerability, which was classified as critical, has been found in code-projects Employee Profile Management System 1.0. This issue affects some unknown processing of the file file_table.php. The manipulation of the argument per_id leads to sql injection. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-250571.
|
[
"cpe:2.3:a:code-projects:employee_profile_management_system:1.0:*:*:*:*:*:*:*"
] |
GHSA-wmm3-p4c7-hhvc
|
This vulnerability allows remote attackers to disclose sensitive information on affected installations of Foxit PDF Reader 11.2.1.53537. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the processing of AcroForms. Crafted data in an AcroForm can trigger a read past the end of an allocated buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of the current process. Was ZDI-CAN-16523.
|
[] |
|
CVE-2025-34065
|
AVTECH IP camera, DVR, and NVR Devices Authentication Bypass via /nobody URL Path
|
An authentication bypass vulnerability exists in AVTECH IP camera, DVR, and NVR devices’ streamd web server. The strstr() function allows unauthenticated access to any request containing "/nobody" in the URL, bypassing login controls.
|
[] |
CVE-2021-41613
|
An issue was discovered in the controller unit of the OpenRISC mor1kx processor. The write logic of Exception Effective Address Register (EEAR) is not implemented correctly. User programs from authorized privilege levels will be unable to write to EEAR.
|
[
"cpe:2.3:o:openrisc:mor1kx_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:openrisc:mor1kx:-:*:*:*:*:*:*:*"
] |
|
CVE-2005-0878
|
Cross-site scripting (XSS) vulnerability in MercuryBoard before 1.1.3 allows remote attackers to inject arbitrary web script or HTML via the title field of a PM (private message).
|
[
"cpe:2.3:a:mercuryboard:mercuryboard_message_board:1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:mercuryboard:mercuryboard_message_board:1.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:mercuryboard:mercuryboard_message_board:1.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:mercuryboard:mercuryboard_message_board:1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:mercuryboard:mercuryboard_message_board:1.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:mercuryboard:mercuryboard_message_board:1.1.2:*:*:*:*:*:*:*"
] |
|
CVE-2022-20830
|
Cisco Software-Defined Application Visibility and Control on Cisco vManage Authentication Bypass Vulnerability
|
A vulnerability in authentication mechanism of Cisco Software-Defined Application Visibility and Control (SD-AVC) on Cisco vManage could allow an unauthenticated, remote attacker to access the GUI of Cisco SD-AVC without authentication. This vulnerability exists because the GUI is accessible on self-managed cloud installations or local server installations of Cisco vManage. An attacker could exploit this vulnerability by accessing the exposed GUI of Cisco SD-AVC. A successful exploit could allow the attacker to view managed device names, SD-AVC logs, and SD-AVC DNS server IP addresses.
|
[
"cpe:2.3:a:cisco:catalyst_sd-wan_manager:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:catalyst_sd-wan_manager:20.7:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:sd-wan_vmanage:*:*:*:*:*:*:*:*"
] |
CVE-2019-8989
|
TIBCO Spotfire Data Science Spoofing Vulnerability
|
The application server component of TIBCO Software Inc.'s TIBCO Data Science for AWS, and TIBCO Spotfire Data Science contains a vulnerability that theoretically enables a user to spoof their account to look like a different user in the affected system. Affected releases are TIBCO Software Inc.'s TIBCO Data Science for AWS: versions up to and including 6.4.0, and TIBCO Spotfire Data Science: versions up to and including 6.4.0.
|
[
"cpe:2.3:a:tibco:data_science_for_aws:*:*:*:*:*:*:*:*",
"cpe:2.3:a:tibco:spotfire_data_science:*:*:*:*:*:*:*:*"
] |
GHSA-rm85-gxcg-pjxv
|
Emerson AMS Device Manager v12.0 to v13.5. A specially crafted script may be run that allows arbitrary remote code execution.
|
[] |
|
GHSA-77h6-w392-v7x5
|
Vulnerability in the PeopleSoft Enterprise PeopleTools component of Oracle PeopleSoft Products (subcomponent: Sawbridge). Supported versions that are affected are 8.54, 8.55 and 8.56. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. While the vulnerability is in PeopleSoft Enterprise PeopleTools, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized read access to a subset of PeopleSoft Enterprise PeopleTools accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of PeopleSoft Enterprise PeopleTools. CVSS 3.0 Base Score 7.2 (Confidentiality and Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:L).
|
[] |
|
CVE-2013-3752
|
Unspecified vulnerability in Oracle Solaris 11 allows remote attackers to affect integrity via vectors related to Service Management Facility (SMF).
|
[
"cpe:2.3:o:sun:sunos:5.11:*:*:*:*:*:*:*"
] |
|
GHSA-qxg5-9hcj-qp59
|
This vulnerability allows network-adjacent attackers to bypass authentication on affected installations of NETGEAR R7800. Authentication is not required to exploit this vulnerability. The specific flaw exists within the apply_save.cgi endpoint. This issue results from the use of hard-coded encryption key. An attacker can leverage this vulnerability to execute arbitrary code in the context of root. Was ZDI-CAN-12287.
|
[] |
|
CVE-2025-4702
|
PHPGurukul Vehicle Parking Management System add-category.php sql injection
|
A vulnerability, which was classified as critical, was found in PHPGurukul Vehicle Parking Management System 1.13. Affected is an unknown function of the file /admin/add-category.php. The manipulation of the argument catename leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
|
[] |
CVE-2024-43649
|
Authenticated command injection via <redacted>.exe <redacted> parameter
|
Authenticated command injection in the filename of a <redacted>.exe request leads to remote code execution as the root user.
This issue affects Iocharger firmware for AC models before version 24120701.
Likelihood: Moderate – This action is not a common place for command injection vulnerabilities to occur. Thus, an attacker will likely only be able to find this vulnerability by reverse-engineering the firmware or trying it on all <redacted> fields. The attacker will also need a (low privilege) account to gain access to the <redacted> binary, or convince a user with such access to execute a payload.
Impact: Critical – The attacker has full control over the charging station as the root user, and can arbitrarily add, modify and delete files and services.
CVSS clarification: This attack can be performed over any network conenction serving the web interfacr (AV:N), and there are not additional mitigating measures that need to be circumvented (AC:L) or other prerequisites (AT:N). The attack does require privileges, but the level does not matter (PR:L), there is no user interaction required (UI:N). The attack leeds to a full compromised of the charger (VC:H/VI:H/VA:H) and a compromised charger can be used to "pivot" to networks that should normally not be reachable (SC:L/SI:L/SA:H). Because this is an EV chargers with significant pwoer, there is a potential safety imp0act (S:P). THis attack can be automated (AU:Y).
|
[] |
CVE-2017-13291
|
In avrc_ctrl_pars_vendor_rsp of avrc_pars_ct.cc, there is a possible NULL pointer dereference due to missing bounds checks. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation. Product: Android. Versions: 7.0, 7.1.1, 7.1.2, 8.0, 8.1. Android ID: A-71603553.
|
[
"cpe:2.3:o:google:android:7.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:7.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:7.1.2:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:8.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:8.1:*:*:*:*:*:*:*"
] |
|
CVE-2014-6126
|
Cross-site scripting (XSS) vulnerability in IBM WebSphere Portal 8.5.0 before CF03 allows remote attackers to inject arbitrary web script or HTML via unspecified vectors.
|
[
"cpe:2.3:a:ibm:websphere_portal:8.5.0.0:*:*:*:*:*:*:*"
] |
|
GHSA-9qhw-fgvr-j3cm
|
The PayPal Pro PayFlow module in osCommerce does not verify that the server hostname matches a domain name in the subject's Common Name (CN) or subjectAltName field of the X.509 certificate, which allows man-in-the-middle attackers to spoof SSL servers via an arbitrary valid certificate.
|
[] |
|
CVE-2015-8105
|
Cross-site scripting (XSS) vulnerability in program/js/app.js in Roundcube webmail before 1.0.7 and 1.1.x before 1.1.3 allows remote authenticated users to inject arbitrary web script or HTML via the file name in a drag-n-drop file upload.
|
[
"cpe:2.3:o:opensuse:opensuse:13.1:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:opensuse:13.2:*:*:*:*:*:*:*",
"cpe:2.3:a:roundcube:webmail:*:*:*:*:*:*:*:*",
"cpe:2.3:a:roundcube:webmail:1.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:roundcube:webmail:1.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:roundcube:webmail:1.1.2:*:*:*:*:*:*:*"
] |
|
GHSA-qx4c-77h7-7fwj
|
The Easy Forms for Mailchimp WordPress plugin through 6.8.8 does not sanitise and escape a parameter before outputting it back in the page when the debug option is enabled, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin.
|
[] |
|
CVE-2023-25880
|
ZDI-CAN-19412: Adobe Dimension GLTF File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability
|
Adobe Dimension versions 3.4.7 (and earlier) is affected by an out-of-bounds write vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file.
|
[
"cpe:2.3:a:adobe:dimension:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:macos:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] |
GHSA-pf3c-qwr7-fjcj
|
The YOGO Booking plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'yogo-calendar' shortcode in all versions up to, and including, 1.6.2 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
|
[] |
|
GHSA-rxfm-4f47-fj5q
|
IBM Tivoli Key Lifecycle Manager 3.0, 3.0.1, 4.0, and 4.1 is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 212791.
|
[] |
|
GHSA-xrgg-cx2j-f5vm
|
Multiple PHP remote file inclusion vulnerabilities in Weblogicnet allow remote attackers to execute arbitrary PHP code via a URL in the files_dir parameter in (1) es_desp.php, (2) es_custom_menu.php, and (3) es_offer.php.
|
[] |
|
CVE-2022-40988
|
Several stack-based buffer overflow vulnerabilities exist in the DetranCLI command parsing functionality of Siretta QUARTZ-GOLD G5.0.1.5-210720-141020. A specially-crafted network packet can lead to arbitrary command execution. An attacker can send a sequence of requests to trigger these vulnerabilities.This buffer overflow is in the function that manages the 'ipv6 static dns WORD WORD WORD' command template.
|
[
"cpe:2.3:o:siretta:quartz-gold_firmware:g5.0.1.5-210720-141020:*:*:*:*:*:*:*",
"cpe:2.3:h:siretta:quartz-gold:-:*:*:*:*:*:*:*"
] |
|
CVE-2024-21766
|
Uncontrolled search path for some Intel(R) oneAPI Math Kernel Library software before version 2024.1 may allow an authenticated user to potentially enable escalation of privilege via local access.
|
[
"cpe:2.3:a:intel:oneapi_math_kernel_library:*:*:*:*:*:*:*:*"
] |
|
CVE-2021-31461
|
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Foxit Reader 10.1.1.37576. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the the handling of app.media objects. The issue results from the lack of proper validation of user-supplied data, which can result in a type confusion condition. An attacker can leverage this vulnerability to execute code in the context of the current process Was ZDI-CAN-13333.
|
[
"cpe:2.3:a:foxitsoftware:phantompdf:*:*:*:*:*:*:*:*",
"cpe:2.3:a:foxitsoftware:reader:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] |
|
GHSA-8467-f3pr-377c
|
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Foxit PDF Reader 11.0.0.49893. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of Annotation objects. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-14023.
|
[] |
|
CVE-2022-22586
|
An out-of-bounds write issue was addressed with improved bounds checking. This issue is fixed in macOS Monterey 12.2. A malicious application may be able to execute arbitrary code with kernel privileges.
|
[
"cpe:2.3:o:apple:macos:*:*:*:*:*:*:*:*"
] |
|
CVE-2022-38475
|
An attacker could have written a value to the first element in a zero-length JavaScript array. Although the array was zero-length, the value was not written to an invalid memory address. This vulnerability affects Firefox < 104.
|
[
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*"
] |
|
GHSA-3f99-xvp7-g4c7
|
IBM Financial Transaction Manager for ACH Services for Multi-Platform 3.0.2 could allow an authenticated user to obtain sensitive information from an undocumented URL. IBM X-Force ID: 130735.
|
[] |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.