id
stringlengths 13
19
| title
stringlengths 0
256
| description
stringlengths 3
13.3k
| cpes
listlengths 0
5.42k
|
|---|---|---|---|
GHSA-588h-3567-38rc
|
Buffer overflow in arp command in Solaris 7 and earlier allows local users to execute arbitrary commands via a long -f parameter.
|
[] |
|
GHSA-86v6-fr9j-x2vf
|
BadBlue server allows remote attackers to read restricted files, such as EXT.INI, via an HTTP request that contains a hex-encoded null byte.
|
[] |
|
CVE-2019-17538
|
Jiangnan Online Judge (aka jnoj) 0.8.0 has Directory Traversal for file reading via the web/polygon/problem/viewfile?id=1&name=../ substring.
|
[
"cpe:2.3:a:jnoj:jiangnan_online_judge:0.8.0:*:*:*:*:*:*:*"
] |
|
GHSA-p74c-jf66-6rw3
|
E-Series SANtricity OS Controller Software 11.x versions prior to 11.70.1 are susceptible to a vulnerability which when successfully exploited could allow a remote attacker to discover information via error messaging which may aid in crafting more complex attacks.
|
[] |
|
GHSA-g783-p3gp-4q89
|
: Improper Neutralization of Special Elements Used in a Template Engine vulnerability in Unlimited Elements Unlimited Elements For Elementor (Free Widgets, Addons, Templates) allows : Command Injection.This issue affects Unlimited Elements For Elementor (Free Widgets, Addons, Templates): from n/a through 1.5.121.
|
[] |
|
GHSA-r49c-w6f5-7rcw
|
The VBWinExec function in Node\AspVBObj.dll in Advantech WebAccess 8.3.0 allows remote attackers to execute arbitrary OS commands via a single argument (aka the command parameter).
|
[] |
|
GHSA-96hw-425v-fcg3
|
UltraVNC revision 1207 has multiple out-of-bounds access vulnerabilities connected with improper usage of SETPIXELS macro in VNC client code, which can potentially result in code execution. This attack appears to be exploitable via network connectivity. These vulnerabilities have been fixed in revision 1208.
|
[] |
|
GHSA-jrcm-c22j-9cm9
|
Unspecified vulnerability in Oracle Solaris Cluster 3.3 allows local users to affect confidentiality, integrity, and availability via unknown vectors related to Data Service for WebLogic Server.
|
[] |
|
CVE-2002-0554
|
webdriver in IBM Informix Web DataBlade 4.12 allows remote attackers to bypass user access levels or read arbitrary files via a SQL injection attack in an HTTP request.
|
[
"cpe:2.3:a:ibm:informix_web_datablade:4.10:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:informix_web_datablade:4.11:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:informix_web_datablade:4.12:*:*:*:*:*:*:*"
] |
|
GHSA-qq4v-v49x-w99c
|
Common Unix Printing System (CUPS) 1.1.14 through 1.1.17 allows local users with lp privileges to create or overwrite arbitrary files via file race conditions, as demonstrated by ice-cream.
|
[] |
|
GHSA-qpj6-77vj-fppc
|
Multiple cross-site scripting (XSS) vulnerabilities in Dolibarr ERP/CRM 3.5.3 allow remote attackers to inject arbitrary web script or HTML via the (1) dol_use_jmobile, (2) dol_optimize_smallscreen, (3) dol_no_mouse_hover, (4) dol_hide_topmenu, (5) dol_hide_leftmenu, (6) mainmenu, or (7) leftmenu parameter to index.php; the (8) dol_use_jmobile, (9) dol_optimize_smallscreen, (10) dol_no_mouse_hover, (11) dol_hide_topmenu, or (12) dol_hide_leftmenu parameter to user/index.php; the (13) dol_use_jmobile, (14) dol_optimize_smallscreen, (15) dol_no_mouse_hover, (16) dol_hide_topmenu, or (17) dol_hide_leftmenu parameter to user/logout.php; the (18) email, (19) firstname, (20) job, (21) lastname, or (22) login parameter in an update action in a "User Card" to user/fiche.php; or the (23) modulepart or (24) file parameter to viewimage.php.
|
[] |
|
CVE-2025-24115
|
A path handling issue was addressed with improved validation. This issue is fixed in macOS Ventura 13.7.3, macOS Sequoia 15.3, macOS Sonoma 14.7.3. An app may be able to read files outside of its sandbox.
|
[] |
|
CVE-2024-9392
|
A compromised content process could have allowed for the arbitrary loading of cross-origin pages. This vulnerability affects Firefox < 131, Firefox ESR < 128.3, Firefox ESR < 115.16, Thunderbird < 128.3, and Thunderbird < 131.
|
[
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:firefox_esr:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:*"
] |
|
CVE-2025-27642
|
Vasion Print (formerly PrinterLogic) before Virtual Appliance Host 22.0.933 Application 20.0.2368 allows Unauthenticated Driver Package Editing V-2024-008.
|
[] |
|
GHSA-hj4h-cmw3-42v5
|
DNSTools CGI applications allow remote attackers to execute arbitrary commands via shell metacharacters.
|
[] |
|
CVE-2023-46935
|
eyoucms v1.6.4 is vulnerable Cross Site Scripting (XSS), which can lead to stealing sensitive information of logged-in users.
|
[
"cpe:2.3:a:eyoucms:eyoucms:*:*:*:*:*:*:*:*",
"cpe:2.3:a:eyoucms:eyoucms:1.6.4:*:*:*:*:*:*:*"
] |
|
CVE-2023-25719
|
ConnectWise Control before 22.9.10032 (formerly known as ScreenConnect) fails to validate user-supplied parameters such as the Bin/ConnectWiseControl.Client.exe h parameter. This results in reflected data and injection of malicious code into a downloaded executable. The executable can be used to execute malicious queries or as a denial-of-service vector. NOTE: this CVE Record is only about the parameters, such as the h parameter (this CVE Record is not about the separate issue of signed executable files that are supposed to have unique configurations across customers' installations).
|
[
"cpe:2.3:a:connectwise:control:*:*:*:*:*:*:*:*"
] |
|
GHSA-2g22-24qq-rqw9
|
The kernel in Apple iOS before 5 and Apple TV before 4.4 does not properly recover memory allocated for incomplete TCP connections, which allows remote attackers to cause a denial of service (resource consumption) by making many connection attempts.
|
[] |
|
GHSA-fqqq-6828-rgx6
|
A vulnerability in Trend Micro Apex One and Apex One as a Service could allow an attacker to intercept and decode certain communication strings that may contain some identification attributes of a particular Apex One server.
|
[] |
|
GHSA-5xvv-4r9w-mw22
|
Missing validation in DAST analyzer affecting all versions from 1.11.0 prior to 3.0.32, allows custom request headers to be sent with every request, regardless of the host.
|
[] |
|
CVE-2006-2547
|
Unspecified vulnerability in the sapdba command in SAP with Informix before 700, and 700 up to patch 100, allows local users to execute arbitrary commands via unknown vectors related to "insecure environment variable" handling.
|
[
"cpe:2.3:a:sap:sapdba:*:*:*:*:*:*:*:*"
] |
|
GHSA-h8rc-vwv6-26wf
|
Trend Micro InterScan Messaging Security Virtual Appliance (IMSVA) 9.1 is vulnerable to a server side request forgery vulnerability which could allow an authenticated attacker to abuse the product's web server and grant access to web resources or parts of local files. An attacker must already have obtained authenticated privileges on the product to exploit this vulnerability.
|
[] |
|
GHSA-4mh9-2pmq-746j
|
A vulnerability in Cisco Meeting Server (CMS) could allow an unauthenticated, adjacent attacker to access services running on internal device interfaces of an affected system. The vulnerability is due to incorrect default configuration of the device, which can expose internal interfaces and ports on the external interface of the system. A successful exploit could allow the attacker to gain unauthenticated access to configuration and database files and sensitive meeting information on an affected system. This vulnerability affects Cisco Meeting Server (CMS) 2000 Platforms that are running a CMS Software release prior to Release 2.2.13 or Release 2.3.4. Cisco Bug IDs: CSCvg76471.
|
[] |
|
GHSA-j7hj-5xvp-7w4p
|
The TAR file parser in Avira AntiVir 7.11.1.163, Antiy Labs AVL SDK 2.0.3.7, avast! Antivirus 4.8.1351.0 and 5.0.677.0, AVG Anti-Virus 10.0.0.1190, Bitdefender 7.2, Quick Heal (aka Cat QuickHeal) 11.00, ClamAV 0.96.4, Command Antivirus 5.2.11.5, Emsisoft Anti-Malware 5.1.0.1, eSafe 7.0.17.0, F-Prot Antivirus 4.6.2.117, G Data AntiVirus 21, Ikarus Virus Utilities T3 Command Line Scanner 1.1.97.0, Jiangmin Antivirus 13.0.900, K7 AntiVirus 9.77.3565, Kaspersky Anti-Virus 7.0.0.125, McAfee Anti-Virus Scanning Engine 5.400.0.1158, McAfee Gateway (formerly Webwasher) 2010.1C, Antimalware Engine 1.1.6402.0 in Microsoft Security Essentials 2.0, NOD32 Antivirus 5795, Norman Antivirus 6.06.12, PC Tools AntiVirus 7.0.3.5, Rising Antivirus 22.83.00.03, AVEngine 20101.3.0.103 in Symantec Endpoint Protection 11, Trend Micro AntiVirus 9.120.0.1004, Trend Micro HouseCall 9.120.0.1004, VBA32 3.12.14.2, and VirusBuster 13.6.151.0 allows remote attackers to bypass malware detection via a TAR archive entry with a length field that exceeds the total TAR file size. NOTE: this may later be SPLIT into multiple CVEs if additional information is published showing that the error occurred independently in different TAR parser implementations.
|
[] |
|
CVE-2023-48349
|
In video decoder, there is a possible out of bounds write due to a missing bounds check. This could lead to local denial of service with no additional execution privileges needed
|
[
"cpe:2.3:o:google:android:11.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:12.0:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:s8000:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:sc7731e:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:sc9832e:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:sc9863a:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t310:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t606:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t610:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t612:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t616:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t618:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t760:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t770:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t820:-:*:*:*:*:*:*:*"
] |
|
GHSA-25xh-49vg-48xq
|
IBM i2 Analyst Notebook 9.2.0 and 9.2.1 could allow a local attacker to execute arbitrary code on the system, caused by a memory corruption. By persuading a victim to open a specially-crafted file, an attacker could exploit this vulnerability to execute arbitrary code on the system. IBM X-Force ID: 187873.
|
[] |
|
CVE-2025-25992
|
SQL Injection vulnerability in FeMiner wms 1.0 allows a remote attacker to obtain sensitive information via the inquire_inout_item.php component.
|
[] |
|
GHSA-h6qp-2x7h-7x2g
|
Fuji Electric Tellus Lite V-Simulator versions 4.0.12.0 and prior are vulnerable to an out-of-bounds write which may allow an attacker to execute arbitrary code.
|
[] |
|
CVE-2013-4369
|
The xlu_vif_parse_rate function in the libxlu library in Xen 4.2.x and 4.3.x allows local users to cause a denial of service (NULL pointer dereference) by using the "@" character as the VIF rate configuration.
|
[
"cpe:2.3:o:xen:xen:4.2.0:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.1:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.2:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.2.3:*:*:*:*:*:*:*",
"cpe:2.3:o:xen:xen:4.3.0:*:*:*:*:*:*:*"
] |
|
GHSA-6jfx-jjm3-94jr
|
Cisco Unified Communications Manager (CUCM) does not properly limit the rate of authentication attempts, which allows remote attackers to cause a denial of service (application slowdown) via a series of requests, aka Bug ID CSCud39515.
|
[] |
|
CVE-2008-2240
|
Stack-based buffer overflow in the Web Server service in IBM Lotus Domino before 7.0.3 FP1, and 8.x before 8.0.1, allows remote attackers to cause a denial of service (daemon crash) or possibly execute arbitrary code via a long Accept-Language HTTP header.
|
[
"cpe:2.3:a:ibm:lotus_domino:6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_domino:6.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_domino:7.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_domino:8.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_domino:8.0.1:*:*:*:*:*:*:*"
] |
|
CVE-2011-3607
|
Integer overflow in the ap_pregsub function in server/util.c in the Apache HTTP Server 2.0.x through 2.0.64 and 2.2.x through 2.2.21, when the mod_setenvif module is enabled, allows local users to gain privileges via a .htaccess file with a crafted SetEnvIf directive, in conjunction with a crafted HTTP request header, leading to a heap-based buffer overflow.
|
[
"cpe:2.3:a:apache:http_server:2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.9:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.28:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.28:beta:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.32:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.32:beta:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.34:beta:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.35:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.36:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.37:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.38:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.39:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.40:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.41:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.42:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.43:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.44:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.45:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.46:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.47:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.48:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.49:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.50:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.51:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.52:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.53:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.54:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.55:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.56:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.57:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.58:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.59:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.60:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.61:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.63:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.0.64:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.3:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.4:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.6:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.8:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.9:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.10:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.11:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.12:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.13:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.14:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.15:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.16:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.18:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.19:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.20:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:http_server:2.2.21:*:*:*:*:*:*:*"
] |
|
CVE-2010-1413
|
WebKit in Apple Safari before 5.0 on Mac OS X 10.5 through 10.6 and Windows, and before 4.1 on Mac OS X 10.4, sends NTLM credentials in cleartext in unspecified circumstances, which allows man-in-the-middle attackers to obtain sensitive information via unspecified vectors.
|
[
"cpe:2.3:a:apple:safari:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:4.0.0b:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:4.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:4.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:4.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:4.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:webkit:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.4:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.5:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.6:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.7:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.5.8:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.6.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.6.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.6.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.4:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.5:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.6:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.7:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.5.8:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.6.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.6.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.6.3:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_7:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_vista:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_xp:*:sp2:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_xp:*:sp3:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.4:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.5:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.6:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.7:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.8:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.9:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.10:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.4.11:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.4:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.5:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.6:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.7:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.8:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.9:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.10:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x_server:10.4.11:*:*:*:*:*:*:*"
] |
|
CVE-2022-28868
|
Address Bar Spoofing Vulnerability in F-Secure SAFE Browser for Android
|
An Address bar spoofing vulnerability was discovered in Safe Browser for Android. When user clicks on a specially crafted malicious webpage/URL, user may be tricked for a short period of time (until the page loads) to think content may be coming from a valid domain, while the content comes from the attacker controlled site.
|
[
"cpe:2.3:a:f-secure:safe:*:*:*:*:*:android:*:*"
] |
CVE-2012-1860
|
Microsoft Office SharePoint Server 2007 SP2 and SP3, SharePoint Server 2010 Gold and SP1, and Office Web Apps 2010 Gold and SP1 do not properly check permissions for search scopes, which allows remote authenticated users to obtain sensitive information or cause a denial of service (data modification) by changing a parameter in a search-scope URL, aka "SharePoint Search Scope Vulnerability."
|
[
"cpe:2.3:a:microsoft:office_web_apps:2010:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:office_web_apps:2010:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:sharepoint_server:2007:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:sharepoint_server:2007:sp2:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:sharepoint_server:2007:sp3:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:sharepoint_server:2010:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:sharepoint_server:2010:sp1:*:*:*:*:*:*"
] |
|
GHSA-m3mq-x6x3-4537
|
A flaw was found in multiple versions of OpenvSwitch. Specially crafted LLDP packets can cause memory to be lost when allocating data to handle specific optional TLVs, potentially causing a denial of service. The highest threat from this vulnerability is to system availability.
|
[] |
|
GHSA-mmh6-5cpf-2c72
|
phpMyFAQ Path Traversal in Attachments
|
SummaryThere is a Path Traversal vulnerability in Attachments that allows attackers with admin rights to upload malicious files to other locations of the web root.PoCIn settings, the attachment location is vulnerable to path traversal and can be set to e.g ..\hacked
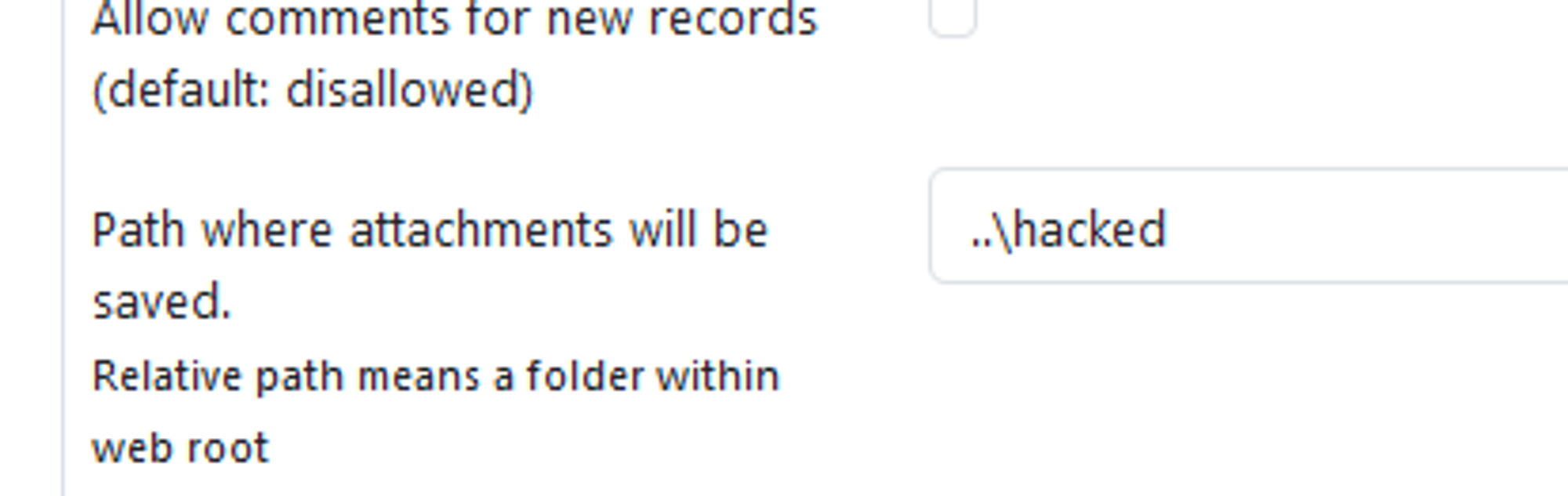When the above is set, attachments files are now uploaded to e.g C:\Apps\XAMPP\htdocs\hacked instead of C:\Apps\XAMPP\htdocs\phpmyfaq\attachmentsVerify this by uploading an attachment and see that the "hacked" directory is now created in the web root folder with the attachment file inside.
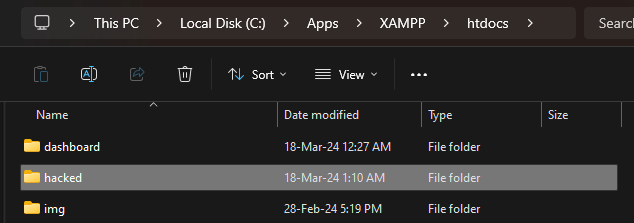
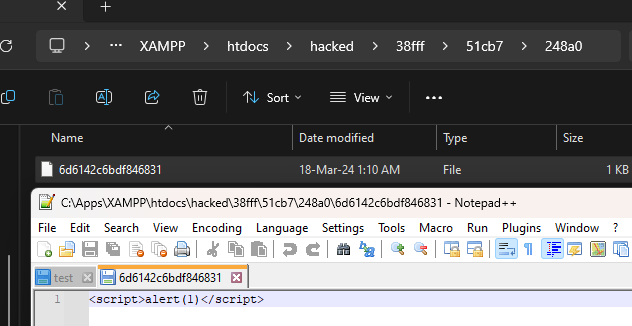ImpactAttackers can potentially upload malicious files outside the specified directory.
|
[] |
GHSA-jpvf-8hj8-56qq
|
libodm.a in IBM AIX 5.3, 6.1, and 7.1 allows local users to overwrite arbitrary files via a symlink attack on a temporary file.
|
[] |
|
CVE-2025-40714
|
SQL injection vulnerability in Quiter Gateway
|
SQL injection vulnerability in versions prior to 4.7.0 of Quiter Gateway by Quiter. This vulnerability allows an attacker to retrieve, create, update and delete databases through the campo id_factura in /<Client>FacturaE/listado_facturas_ficha.jsp.
|
[] |
GHSA-35w5-2xwx-jpp4
|
HP StorageWorks Modular Smart Array P2000 G3 firmware TS100R011, TS100R025, TS100P002, TS200R005, TS201R014, and TS201R015 installs an undocumented admin account with a default "!admin" password, which allows remote attackers to gain privileges.
|
[] |
|
CVE-2016-9992
|
IBM Kenexa LCMS Premier on Cloud 9.0, and 10.0.0 is vulnerable to SQL injection. A remote attacker could send specially-crafted SQL statements, which could allow the attacker to view, add, modify or delete information in the back-end database. IBM Reference #: 1992067.
|
[
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:9.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:10.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:10.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:kenexa_lcms_premier:10.2:*:*:*:*:*:*:*"
] |
|
GHSA-27w2-gfcm-69mr
|
A vulnerability was found in SourceCodester Dental Clinic Appointment Reservation System 1.0. It has been rated as problematic. Affected by this issue is some unknown functionality of the file /admin/service.php of the component POST Parameter Handler. The manipulation of the argument service leads to cross site scripting. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-229598 is the identifier assigned to this vulnerability.
|
[] |
|
GHSA-3xx7-wxpj-hg7p
|
Bitcoin SV before 0.1.1 allows uncontrolled resource consumption when receiving sendheaders messages.
|
[] |
|
CVE-2015-8818
|
The cpu_physical_memory_write_rom_internal function in exec.c in QEMU (aka Quick Emulator) does not properly skip MMIO regions, which allows local privileged guest users to cause a denial of service (guest crash) via unspecified vectors.
|
[
"cpe:2.3:a:qemu:qemu:*:*:*:*:*:*:*:*"
] |
|
CVE-2017-15263
|
IrfanView version 4.44 (32bit) with PDF plugin version 4.43 allows attackers to cause a denial of service or possibly have unspecified other impact via a crafted .pdf file, related to "Data from Faulting Address controls Branch Selection starting at PDF!xmlListWalk+0x00000000000166c4."
|
[
"cpe:2.3:a:irfanview:pdf:4.43:*:*:*:*:*:*:*",
"cpe:2.3:a:irfanview:irfanview:4.44:*:*:*:*:*:x86:*"
] |
|
CVE-2024-7747
|
Wallet for WooCommerce <= 1.5.6 - Authenticated (Subscriber+) Incorrect Conversion between Numeric Types
|
The Wallet for WooCommerce plugin for WordPress is vulnerable to incorrect conversion between numeric types in all versions up to, and including, 1.5.6. This is due to a numerical logic flaw when transferring funds to another user. This makes it possible for authenticated attackers, with Subscriber-level access and above, to create funds during a transfer and distribute these funds to any number of other users or their own account, rendering products free. Attackers could also request to withdraw funds if the Wallet Withdrawal extension is used and the request is approved by an administrator.
|
[] |
CVE-2019-12751
|
Symantec Messaging Gateway, prior to 10.7.1, may be susceptible to a privilege escalation vulnerability, which is a type of issue whereby an attacker may attempt to compromise the software application to gain elevated access to resources that are normally protected from an application or user.
|
[
"cpe:2.3:a:symantec:message_gateway:*:*:*:*:*:*:*:*"
] |
|
GHSA-pfc9-pj4x-5f23
|
Vulnerability in WBSAirback 21.02.04, which involves improper neutralisation of Server-Side Includes (SSI), through S3 disks (/admin/DeviceS3). Exploitation of this vulnerability could allow a remote user to execute arbitrary code.
|
[] |
|
CVE-2017-7105
|
An issue was discovered in certain Apple products. iOS before 11 is affected. tvOS before 11 is affected. watchOS before 4 is affected. The issue involves the "Wi-Fi" component. It might allow remote attackers to execute arbitrary code in a privileged context or cause a denial of service (memory corruption) via crafted Wi-Fi traffic.
|
[
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:tvos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:watchos:*:*:*:*:*:*:*:*"
] |
|
GHSA-hx29-wwjw-h4m7
|
The bbencode_second_pass and make_clickable functions in bbcode.php for phpBB before 2.0.15, as used in viewtopic.php, privmsg.php, and other scripts, allow remote attackers to execute arbitrary script via a BBcode tag with a (1) javascript:, (2) applet:, (3) about:, (4) activex:, (5) chrome:, or (6) script: URI scheme, as demonstrated using the URL tag.
|
[] |
|
GHSA-25fx-9jj6-385f
|
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in wpWax Product Carousel Slider & Grid Ultimate for WooCommerce allows Stored XSS. This issue affects Product Carousel Slider & Grid Ultimate for WooCommerce: from n/a through 1.10.0.
|
[] |
|
CVE-2018-20506
|
SQLite before 3.25.3, when the FTS3 extension is enabled, encounters an integer overflow (and resultant buffer overflow) for FTS3 queries in a "merge" operation that occurs after crafted changes to FTS3 shadow tables, allowing remote attackers to execute arbitrary code by leveraging the ability to run arbitrary SQL statements (such as in certain WebSQL use cases). This is a different vulnerability than CVE-2018-20346.
|
[
"cpe:2.3:a:sqlite:sqlite:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:tvos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:watchos:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:icloud:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:itunes:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:leap:42.3:*:*:*:*:*:*:*"
] |
|
CVE-2019-1764
|
Cisco IP Phone 8800 Series Cross-Site Request Forgery Vulnerability
|
A vulnerability in the web-based management interface of Session Initiation Protocol (SIP) Software for Cisco IP Phone 8800 Series could allow an unauthenticated, remote attacker to conduct a cross-site request forgery (CSRF) attack. The vulnerability is due to insufficient CSRF protections for the web-based management interface of an affected device. An attacker could exploit this vulnerability by persuading an authenticated user of the interface to follow a crafted link. A successful exploit could allow the attacker to perform arbitrary actions on a targeted device via a web browser and with the privileges of the user. This vulnerability affects Cisco IP Phone 8800 Series products running a SIP Software release prior to 11.0(5) for Wireless IP Phone 8821 and 8821-EX; and 12.5(1)SR1 for the IP Conference Phone 8832 and the rest of the IP Phone 8800 Series. Cisco IP Conference Phone 8831 is not affected.
|
[
"cpe:2.3:o:cisco:ip_phone_8821_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8821:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ip_phone_8821-ex_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8821-ex:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ip_conference_phone_8832_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_conference_phone_8832:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ip_phone_8800_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8800:-:*:*:*:*:*:*:*"
] |
CVE-2021-37702
|
Improper Neutralization of Formula Elements in a CSV File in pimcore/pimcore
|
Pimcore is an open source data & experience management platform. Prior to version 10.1.1, Data Object CSV import allows formular injection. The problem is patched in 10.1.1. Aside from upgrading, one may apply the patch manually as a workaround.
|
[
"cpe:2.3:a:pimcore:pimcore:*:*:*:*:*:*:*:*"
] |
GHSA-869w-47c6-fq8q
|
Babylon Integer Overflow in Distribution Module CumulativeRewardRatio Calculation Leading to Chain Halt
|
SummaryMinting large amount of tokens through ibc transfer and then depositing them in validator rewards pool (via `DepositValidatorRewardsPool` message) can lead to integer overflow panic when calculating `cumulative_reward_ratio` for the validator.This calculation happens in `x/epoching` module `EndBlocker`, thus the panic will halt the chain.ImpactDenial of Service - Due to panic in the `EndBlocker` Babylon Genesis will halt
|
[] |
GHSA-cqrv-6jr2-m8qj
|
A maliciously crafted MODEL file, when parsed in libodx.dll through Autodesk applications, can force an Out-of-Bounds Read. A malicious actor can leverage this vulnerability to cause a crash, read sensitive data, or execute arbitrary code in the context of the current process.
|
[] |
|
CVE-2024-10495
|
Out of bounds read when loading the font table in fontmgr.cpp in NI LabVIEW
|
An out of bounds read due to improper input validation when loading the font table in fontmgr.cpp in NI LabVIEW may disclose information or result in arbitrary code execution. Successful exploitation requires an attacker to provide a user with a specially crafted VI. This vulnerability affects LabVIEW 2024 Q3 and prior versions.
|
[] |
GHSA-4qqh-4p23-qw24
|
system_server in Android before 2016-10-05 on Nexus devices allows attackers to gain privileges via a crafted application, aka internal bug 30445380.
|
[] |
|
CVE-2022-23457
|
Path Traversal in ESAPI
|
ESAPI (The OWASP Enterprise Security API) is a free, open source, web application security control library. Prior to version 2.3.0.0, the default implementation of `Validator.getValidDirectoryPath(String, String, File, boolean)` may incorrectly treat the tested input string as a child of the specified parent directory. This potentially could allow control-flow bypass checks to be defeated if an attack can specify the entire string representing the 'input' path. This vulnerability is patched in release 2.3.0.0 of ESAPI. As a workaround, it is possible to write one's own implementation of the Validator interface. However, maintainers do not recommend this.
|
[
"cpe:2.3:a:owasp:enterprise_security_api:*:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:weblogic_server:12.2.1.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:weblogic_server:12.2.1.4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:weblogic_server:14.1.1.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:linux:*:*",
"cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:vmware_vsphere:*:*",
"cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:*",
"cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*"
] |
CVE-2008-1400
|
Directory traversal vulnerability in the Net Inspector HTTP Server (mghttpd) in MG-SOFT Net Inspector 6.5.0.828 and earlier for Windows allows remote attackers to read arbitrary files via a "..\" (dot dot backslash) or "../" (dot dot slash) in the URI.
|
[
"cpe:2.3:a:mg-soft:net_inspector:6.5.0.828:*:*:*:*:*:*:*"
] |
|
CVE-2021-28457
|
Visual Studio Code Remote Code Execution Vulnerability
|
Visual Studio Code Remote Code Execution Vulnerability
|
[
"cpe:2.3:a:microsoft:visual_studio_code:*:*:*:*:*:*:*:*"
] |
CVE-2015-9143
|
In Android before 2018-04-05 or earlier security patch level on Qualcomm Snapdragon Mobile and Snapdragon Wear IPQ4019, MDM9206, MDM9607, MDM9615, MDM9625, MDM9640, MDM9650, MDM9655, MSM8909W, SD 210/SD 212/SD 205, SD 400, SD 410/12, SD 600, SD 615/16/SD 415, and SDX20, when reading CDT from eMMC with a very large meta offset (>size of default CDT-array compiled in bootloader) for one of the CDBs, a buffer overflow occurs.
|
[
"cpe:2.3:o:qualcomm:mdm9206_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9206:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9607_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9607:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9615_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9615:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9625_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9625:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:ipq4019_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:ipq4019:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9640_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9640:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9645_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9645:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9650_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9650:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9655_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9655:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:msm8909w_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:msm8909w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_210_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_210:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_212_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_212:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_205_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_205:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_400_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_400:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_410_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_410:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_412_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_412:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_600_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_600:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_615_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_615:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_616_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_616:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_415_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_415:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sdx20_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sdx20:-:*:*:*:*:*:*:*"
] |
|
CVE-2024-22347
|
IBM UrbanCode Velocity information disclosure
|
IBM DevOps Velocity 5.0.0 and IBM UrbanCode Velocity 4.0.0 through 4.0. 25 uses weaker than expected cryptographic algorithms that could allow an attacker to decrypt highly sensitive information.
|
[
"cpe:2.3:a:ibm:urbancode_velocity:4.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:urbancode_velocity:4.0.15:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:devops_velocity:5.0.0:*:*:*:*:*:*:*"
] |
GHSA-6j42-f94q-5pq7
|
An issue was discovered in Asterisk Open Source 13 before 13.18.1, 14 before 14.7.1, and 15 before 15.1.1 and Certified Asterisk 13.13 before 13.13-cert7. A memory leak occurs when an Asterisk pjsip session object is created and that call gets rejected before the session itself is fully established. When this happens the session object never gets destroyed. Eventually Asterisk can run out of memory and crash.
|
[] |
|
CVE-2020-12511
|
Pepper+Fuchs Comtrol IO-Link Master Cross-Site Request Forgery
|
Pepperl+Fuchs Comtrol IO-Link Master in Version 1.5.48 and below is prone to a Cross-Site Request Forgery (CSRF) in the web interface.
|
[
"cpe:2.3:o:pepperl-fuchs:io-link_master_4-eip_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_4-eip:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_8-eip_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_8-eip:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_8-eip-l_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_8-eip-l:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_dr-8-eip_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_dr-8-eip:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_dr-8-eip-p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_dr-8-eip-p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_dr-8-eip-t_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_dr-8-eip-t:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_4-pnio_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_4-pnio:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_8-pnio_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_8-pnio:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_8-pnio-l_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_8-pnio-l:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_dr-8-pnio_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_dr-8-pnio:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_dr-8-pnio-p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_dr-8-pnio-p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:pepperl-fuchs:io-link_master_dr-8-pnio-t_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:pepperl-fuchs:io-link_master_dr-8-pnio-t:-:*:*:*:*:*:*:*"
] |
GHSA-2mh6-5954-wmgr
|
Denial of service through Solaris 2.5.1 telnet by sending ^D characters.
|
[] |
|
GHSA-5xr4-f845-39hv
|
Untrusted search path vulnerability in the Microsoft Active Accessibility component in Microsoft Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista SP2, Windows Server 2008 SP2, R2, and R2 SP1, and Windows 7 Gold and SP1 allows local users to gain privileges via a Trojan horse DLL in the current working directory, aka "Active Accessibility Insecure Library Loading Vulnerability."
|
[] |
|
GHSA-qp9j-573m-xrwq
|
A vulnerability, which was classified as critical, has been found in Tenda W9 1.0.0.7(4456). Affected by this issue is the function setWrlAccessList of the component httpd. The manipulation of the argument ssidIndex leads to stack-based buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-250706 is the identifier assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way.
|
[] |
|
CVE-2010-4592
|
The Mobile Network Connections functionality in the Connection Manager in IBM Lotus Mobile Connect before 6.1.4, when HTTP Access Services (HTTP-AS) is enabled, does not properly handle failed attempts at establishing HTTP-TCP sessions, which allows remote attackers to cause a denial of service (memory consumption and daemon crash) by making many TCP connection attempts.
|
[
"cpe:2.3:a:ibm:lotus_mobile_connect:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_mobile_connect:6.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_mobile_connect:6.1.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:lotus_mobile_connect:6.1.2:*:*:*:*:*:*:*"
] |
|
CVE-2025-52089
|
A hidden remote support feature protected by a static secret in TOTOLINK N300RB firmware version 8.54 allows an authenticated attacker to execute arbitrary OS commands with root privileges.
|
[] |
|
GHSA-mxpg-5fx8-pc45
|
A vulnerability in the FindMe feature of Cisco Expressway Series and Cisco TelePresence Video Communication Server (VCS) could allow an unauthenticated, remote attacker to conduct a cross-site request forgery (CSRF) attack and perform arbitrary actions on an affected system. The vulnerability is due to insufficient CSRF protections for the web-based management interface of the affected system. An attacker could exploit this vulnerability by persuading a user of the interface to follow a maliciously crafted link. A successful exploit could allow the attacker to perform arbitrary actions on an affected system with the privileges of the user. The arbitrary actions include adding an attacker-controlled device and redirecting calls intended for a specific user. For more information about CSRF attacks and potential mitigations, see Understanding Cross-Site Request Forgery Threat Vectors. This vulnerability is fixed in software version X12.5.1 and later.
|
[] |
|
CVE-2023-49396
|
JFinalCMS v5.0.0 was discovered to contain a Cross-Site Request Forgery (CSRF) vulnerability via /admin/category/save.
|
[
"cpe:2.3:a:jfinalcms_project:jfinalcms:5.0.0:*:*:*:*:*:*:*"
] |
|
GHSA-chpr-r6hr-9q6g
|
AxxonSoft Axxon Next has Directory Traversal via an initial /css//..%2f substring in a URI.
|
[] |
|
GHSA-p67f-wm66-pw4x
|
A setup script for fabric interconnect devices in Cisco Unified Computing System (UCS) allows remote attackers to execute arbitrary commands via invalid parameters, aka Bug ID CSCtg20790.
|
[] |
|
GHSA-6426-p644-ffcf
|
Information exposure vulnerability in RT software affecting version 4.4.1. This vulnerability allows an attacker with local access to the device to retrieve sensitive information about the application, such as vulnerability tickets, because the application stores the information in the browser cache, leading to information exposure despite session termination.
|
[] |
|
CVE-2023-2901
|
NFine Rapid Development Platform access control
|
A vulnerability was found in NFine Rapid Development Platform 20230511. It has been declared as problematic. Affected by this vulnerability is an unknown functionality of the file /SystemManage/User/GetGridJson?_search=false&nd=1680855479750&rows=50&page=1&sidx=F_CreatorTime+desc&sord=asc. The manipulation leads to improper access controls. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-229975. NOTE: The vendor was contacted early about this disclosure but did not respond in any way.
|
[
"cpe:2.3:a:nfine_rapid_development_platform_project:nfine_rapid_development_platform:2023-05-11:*:*:*:*:*:*:*"
] |
CVE-2025-5057
|
Campcodes Online Shopping Portal insert-product.php sql injection
|
A vulnerability was found in Campcodes Online Shopping Portal 1.0. It has been rated as critical. Affected by this issue is some unknown functionality of the file /admin/insert-product.php. The manipulation of the argument Category leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. Other parameters might be affected as well.
|
[] |
GHSA-4mgv-g5j9-fr8q
|
A denial of service vulnerability exists in the ICMP and ICMPv6 parsing functionality of Weston Embedded uC-TCP-IP v3.06.01. A specially crafted network packet can lead to an out-of-bounds read. An attacker can send a malicious packet to trigger this vulnerability.This vulnerability concerns a denial of service within the parsing an IPv6 ICMPv6 packet.
|
[] |
|
GHSA-78qm-jggg-xmvh
|
Hoteldruid v3.0.5 was discovered to contain multiple SQL injection vulnerabilities at /hoteldruid/clienti.php via the annonascita, annoscaddoc, giornonascita, giornoscaddoc, lingua_cli, mesenascita, and mesescaddoc parameters.
|
[] |
|
CVE-2015-6352
|
Cisco Unified Communications Domain Manager before 10.6(1) provides different error messages for pathname access attempts depending on whether the pathname exists, which allows remote attackers to map a filesystem via a series of requests, aka Bug ID CSCut67891.
|
[
"cpe:2.3:a:cisco:hosted_collaboration_solution:10.6_base:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:unified_communications_domain_manager:10.6_base:*:*:*:*:*:*:*"
] |
|
CVE-2024-56646
|
ipv6: avoid possible NULL deref in modify_prefix_route()
|
In the Linux kernel, the following vulnerability has been resolved:
ipv6: avoid possible NULL deref in modify_prefix_route()
syzbot found a NULL deref [1] in modify_prefix_route(), caused by one
fib6_info without a fib6_table pointer set.
This can happen for net->ipv6.fib6_null_entry
[1]
Oops: general protection fault, probably for non-canonical address 0xdffffc0000000006: 0000 [#1] PREEMPT SMP KASAN NOPTI
KASAN: null-ptr-deref in range [0x0000000000000030-0x0000000000000037]
CPU: 1 UID: 0 PID: 5837 Comm: syz-executor888 Not tainted 6.12.0-syzkaller-09567-g7eef7e306d3c #0
Hardware name: Google Google Compute Engine/Google Compute Engine, BIOS Google 09/13/2024
RIP: 0010:__lock_acquire+0xe4/0x3c40 kernel/locking/lockdep.c:5089
Code: 08 84 d2 0f 85 15 14 00 00 44 8b 0d ca 98 f5 0e 45 85 c9 0f 84 b4 0e 00 00 48 b8 00 00 00 00 00 fc ff df 4c 89 e2 48 c1 ea 03 <80> 3c 02 00 0f 85 96 2c 00 00 49 8b 04 24 48 3d a0 07 7f 93 0f 84
RSP: 0018:ffffc900035d7268 EFLAGS: 00010006
RAX: dffffc0000000000 RBX: 0000000000000000 RCX: 0000000000000000
RDX: 0000000000000006 RSI: 1ffff920006bae5f RDI: 0000000000000030
RBP: 0000000000000000 R08: 0000000000000001 R09: 0000000000000001
R10: ffffffff90608e17 R11: 0000000000000001 R12: 0000000000000030
R13: ffff888036334880 R14: 0000000000000000 R15: 0000000000000000
FS: 0000555579e90380(0000) GS:ffff8880b8700000(0000) knlGS:0000000000000000
CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
CR2: 00007ffc59cc4278 CR3: 0000000072b54000 CR4: 00000000003526f0
DR0: 0000000000000000 DR1: 0000000000000000 DR2: 0000000000000000
DR3: 0000000000000000 DR6: 00000000fffe0ff0 DR7: 0000000000000400
Call Trace:
<TASK>
lock_acquire.part.0+0x11b/0x380 kernel/locking/lockdep.c:5849
__raw_spin_lock_bh include/linux/spinlock_api_smp.h:126 [inline]
_raw_spin_lock_bh+0x33/0x40 kernel/locking/spinlock.c:178
spin_lock_bh include/linux/spinlock.h:356 [inline]
modify_prefix_route+0x30b/0x8b0 net/ipv6/addrconf.c:4831
inet6_addr_modify net/ipv6/addrconf.c:4923 [inline]
inet6_rtm_newaddr+0x12c7/0x1ab0 net/ipv6/addrconf.c:5055
rtnetlink_rcv_msg+0x3c7/0xea0 net/core/rtnetlink.c:6920
netlink_rcv_skb+0x16b/0x440 net/netlink/af_netlink.c:2541
netlink_unicast_kernel net/netlink/af_netlink.c:1321 [inline]
netlink_unicast+0x53c/0x7f0 net/netlink/af_netlink.c:1347
netlink_sendmsg+0x8b8/0xd70 net/netlink/af_netlink.c:1891
sock_sendmsg_nosec net/socket.c:711 [inline]
__sock_sendmsg net/socket.c:726 [inline]
____sys_sendmsg+0xaaf/0xc90 net/socket.c:2583
___sys_sendmsg+0x135/0x1e0 net/socket.c:2637
__sys_sendmsg+0x16e/0x220 net/socket.c:2669
do_syscall_x64 arch/x86/entry/common.c:52 [inline]
do_syscall_64+0xcd/0x250 arch/x86/entry/common.c:83
entry_SYSCALL_64_after_hwframe+0x77/0x7f
RIP: 0033:0x7fd1dcef8b79
Code: 28 00 00 00 75 05 48 83 c4 28 c3 e8 c1 17 00 00 90 48 89 f8 48 89 f7 48 89 d6 48 89 ca 4d 89 c2 4d 89 c8 4c 8b 4c 24 08 0f 05 <48> 3d 01 f0 ff ff 73 01 c3 48 c7 c1 b8 ff ff ff f7 d8 64 89 01 48
RSP: 002b:00007ffc59cc4378 EFLAGS: 00000246 ORIG_RAX: 000000000000002e
RAX: ffffffffffffffda RBX: 0000000000000000 RCX: 00007fd1dcef8b79
RDX: 0000000000040040 RSI: 0000000020000140 RDI: 0000000000000004
RBP: 00000000000113fd R08: 0000000000000006 R09: 0000000000000006
R10: 0000000000000006 R11: 0000000000000246 R12: 00007ffc59cc438c
R13: 431bde82d7b634db R14: 0000000000000001 R15: 0000000000000001
</TASK>
|
[
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.13:rc1:*:*:*:*:*:*"
] |
CVE-2018-16613
|
An issue was discovered in the update function in the wpForo Forum plugin before 1.5.2 for WordPress. A registered forum is able to escalate privilege to the forum administrator without any form of user interaction.
|
[
"cpe:2.3:a:gvectors:wpforo_forum:*:*:*:*:*:wordpress:*:*"
] |
|
CVE-2022-26926
|
Windows Address Book Remote Code Execution Vulnerability
|
Windows Address Book Remote Code Execution Vulnerability
|
[
"cpe:2.3:o:microsoft:windows_10:-:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:-:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10:20h2:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_10:20h2:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:20h2:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10:21h1:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_10:21h1:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:21h1:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10:21h2:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_10:21h2:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:21h2:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10:1607:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:1607:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10:1809:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_10:1809:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:1809:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_10:1909:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_10:1909:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_10:1909:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_11:-:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_11:-:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_8.1:-:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_8.1:-:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_rt_8.1:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server:2022:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_server_2008:sp2:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_server_2008:sp2:*:*:*:*:*:x86:*",
"cpe:2.3:o:microsoft:windows_server_2012:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2019:-:*:*:*:*:*:*:*"
] |
GHSA-3q48-7vgf-gh5j
|
The SDDisk2k.sys driver of WinMagic SecureDoc v8.5 and earlier allows local users to write to arbitrary kernel memory addresses because the IOCTL dispatcher lacks pointer validation. Exploiting this vulnerability results in privileged code execution.
|
[] |
|
CVE-2025-49489
|
Resource leaks in cm
|
Improper Resource Shutdown or Release vulnerability in ASR Falcon_Linux、Kestrel、Lapwing_Linux on Linux (con_mgr
components) allows Resource Leak Exposure. This vulnerability is associated with program files con_mgr/dialer_task.C.
This issue affects Falcon_Linux、Kestrel、Lapwing_Linux: before v1536.
|
[] |
CVE-2024-32505
|
WordPress ElementsKit Elementor addons plugin <= 3.0.6 - Cross Site Scripting (XSS) vulnerability
|
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Wpmet Elements kit Elementor addons allows Stored XSS.This issue affects Elements kit Elementor addons: from n/a through 3.0.6.
|
[
"cpe:2.3:a:wpmet:elements_kit_elementor_addons:-:*:*:*:*:wordpress:*:*"
] |
CVE-2020-11812
|
Rukovoditel 2.5.2 is affected by a SQL injection vulnerability because of improper handling of the filters[0][value] or filters[1][value] parameter.
|
[
"cpe:2.3:a:rukovoditel:rukovoditel:2.5.2:*:*:*:*:*:*:*"
] |
|
GHSA-f37x-2cx7-rh6g
|
The “DeTheme Kit for Elementor� WordPress Plugin before 1.5.5.5 has a widget that is vulnerable to stored Cross-Site Scripting (XSS) by lower-privileged users such as contributors, all via a similar method.
|
[] |
|
GHSA-pp67-vh85-488h
|
Giflib Project v5.2.2 is vulnerable to a heap buffer overflow via gif2rgb.
|
[] |
|
CVE-2023-33236
|
MXsecurity Hardcoded Credential Vulnerability
|
MXsecurity version 1.0 is vulnearble to hardcoded credential vulnerability. This vulnerability has been reported that can be exploited to craft arbitrary JWT tokens and subsequently bypass authentication for web-based APIs.
|
[
"cpe:2.3:a:moxa:mxsecurity:1.0:*:*:*:*:*:*:*"
] |
CVE-2018-10073
|
joyplus-cms 1.6.0 has XSS in manager/admin_vod.php via the keyword parameter.
|
[
"cpe:2.3:a:joyplus-cms_project:joyplus-cms:1.6.0:*:*:*:*:*:*:*"
] |
|
CVE-2007-2781
|
Cross-site scripting (XSS) vulnerability in include/sessionRegister.php in WikyBlog before 1.4.13 allows remote attackers to inject arbitrary web script or HTML, probably via vectors related to a certain data2 array element.
|
[
"cpe:2.3:a:wikyblog:wikyblog:*:*:*:*:*:*:*:*"
] |
|
GHSA-8qh5-83cf-f7qw
|
Buffer Overflow vulnerability inALFA WiFi CampPro router ALFA_CAMPRO-co-2.29 allows a remote attacker to execute arbitrary code via the hiddenIndex in the function StorageEditUser
|
[] |
|
GHSA-3vf5-m872-p593
|
In Android before 2018-04-05 or earlier security patch level on Qualcomm Snapdragon Automobile and Snapdragon Mobile SD 410/12, SD 425, SD 430, SD 450, SD 617, SD 625, SD 650/52, SD 810, SD 820, and SD 820A, a buffer overflow can occur in SafeSwitch.
|
[] |
|
GHSA-pppq-x5vp-whw6
|
IBM i 7.2, 7.3, 7.4, and 7.5 could allow a user with the capability to compile or restore a program to gain elevated privileges due to an unqualified library call. A malicious actor could cause user-controlled code to run with administrator privilege.
|
[] |
|
GHSA-6v43-c7c5-6gg8
|
IBM QRadar User Behavior Analytics 4.1.1 is vulnerable to cross-site request forgery which could allow an attacker to execute malicious and unauthorized actions transmitted from a user that the website trusts. IBM X-Force ID: 202168.
|
[] |
|
CVE-2024-51054
|
A Cross Site Scriptng (XSS) vulnerability was found in /omrs/admin/search.php in PHPGurukul Online Marriage Registration System 1.0, which allows remote attackers to execute arbitrary code via the "searchdata" POST request parameter.
|
[
"cpe:2.3:a:phpgurukul:online_marriage_registration_system:1.0:*:*:*:*:*:*:*"
] |
|
CVE-2008-6234
|
SQL injection vulnerability in the com_musica module in Joomla! and Mambo allows remote attackers to execute arbitrary SQL commands via the id parameter to index.php.
|
[
"cpe:2.3:a:joomla:com_musica:-:*:*:*:*:*:*:*",
"cpe:2.3:a:mambo-foundation:com_musica:-:*:*:*:*:*:*:*",
"cpe:2.3:a:joomla:joomla:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mambo-foundation:mambo:*:*:*:*:*:*:*:*"
] |
|
CVE-2013-0210
|
The smart proxy Puppet run API in Foreman before 1.2.0 allows remote attackers to execute arbitrary commands via vectors related to escaping and Puppet commands.
|
[
"cpe:2.3:a:theforeman:foreman:*:*:*:*:*:*:*:*",
"cpe:2.3:a:theforeman:foreman:0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:theforeman:foreman:0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:theforeman:foreman:0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:theforeman:foreman:0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:theforeman:foreman:0.4.1:*:*:*:*:*:*:*"
] |
|
GHSA-p6cg-q445-g68f
|
The Formaloo Form Maker & Customer Analytics for WordPress & WooCommerce plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘address’ parameter in all versions up to, and including, 2.1.3.2 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
|
[] |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.