id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
139k
| cpes
sequencelengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
CVE-2003-1447 | IBM WebSphere Advanced Server Edition 4.0.4 uses a weak encryption algorithm (XOR and base64 encoding), which allows local users to decrypt passwords when the configuration file is exported to XML. | [
"cpe:2.3:a:ibm:websphere_application_server:4.0.4:*:advanced_server:*:*:*:*:*"
] | null | null | null | 1.9 |
|
CVE-2023-29255 | IBM DB2 for Linux, UNIX and Windows denial of service | IBM DB2 for Linux, UNIX and Windows (includes Db2 Connect Server) 10.5, 11.1, and 11.5 is vulnerable to a denial of service as it may trap when compiling a variation of an anonymous block. IBM X-Force ID: 251991. | [
"cpe:2.3:a:ibm:db2:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:-:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp1:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp10:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp2:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp3:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp3a:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp4:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp5:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp6:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp7:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp8:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:10.5:fp9:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:-:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:fp1:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:fp2:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:fp3:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:fp4:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:fp5:*:*:*:*:*:*",
"cpe:2.3:a:ibm:db2:11.1.4:fp6:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] | null | 7.5 | null | null |
GHSA-ph2j-5hxq-gxrr | Drupal Node Validation Bypass in the node module API | The node module API in Drupal 5.x before 5.11 allows remote attackers to bypass node validation and have unspecified other impact via unknown vectors related to contributed modules. | [] | null | null | null | null |
GHSA-7xm9-vjm6-2g2r | Zone Labs IMsecure and IMsecure Pro before 1.5 allow remote attackers to bypass Active Link Filtering via an instant message containing a URL with hex encoded file extensions. | [] | null | null | null | null |
|
GHSA-6g3c-2hjf-jwvq | Unspecified vulnerability in the JD Edwards EnterpriseOne Tools component in Oracle JD Edwards Products 8.9 GA through 8.98.4.1, and OneWorld Tools through 24.1.3, allows remote attackers to affect integrity and availability, related to Enterprise Infrastructure SEC. | [] | null | null | null | null |
|
GHSA-xjcr-w3v6-f46r | IBM AIX 7.1, 7.2, and VIOS 3.1 could allow a local user to exploit a vulnerability in Korn Shell (ksh) to gain root privileges. IBM X-Force ID: 201478. | [] | null | 7.8 | null | null |
|
CVE-2013-1913 | Integer overflow in the load_image function in file-xwd.c in the X Window Dump (XWD) plug-in in GIMP 2.6.9 and earlier, when used with glib before 2.24, allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a large color entries value in an X Window System (XWD) image dump. | [
"cpe:2.3:a:gimp:gimp:*:*:*:*:*:*:*:*",
"cpe:2.3:a:gnome:glib:*:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux:5.0:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*"
] | null | null | null | 6.8 |
|
GHSA-96vh-4rfp-c42c | HTSJDK is vulnerable to exposure of resource(s) to the wrong sphere | The package com.github.samtools:htsjdk before 3.0.1 are vulnerable to Creation of Temporary File in Directory with Insecure Permissions due to the createTempDir() function in util/IOUtil.java not checking for the existence of the temporary directory before attempting to create it. | [] | null | 7.8 | null | null |
GHSA-95gw-ppr7-wgvw | Cross-site scripting (XSS) vulnerability in ZOHO ManageEngine ServiceDesk Plus before 9.2 allows remote attackers to inject arbitrary web script or HTML via unspecified vectors. | [] | null | null | 5.4 | null |
|
GHSA-pqp3-8rrw-g8vm | PocketMine-MP vulnerable to server crash with certain invalid JSON payloads in `LoginPacket` due to vulnerable dependency | ImpactAn attacker could crash PocketMine-MP by sending malformed JSON in `LoginPacket`.This happened due to a bug in [`netresearch/jsonmapper`](https://github.com/cweiske/JsonMapper). The library wasn't doing proper checks when mapping JSON arrays and objects onto scalar model properties such as strings.PatchesThe problem was fixed in a fork of JsonMapper in dktapps/JsonMapper@a31902a31f5b6fdb832f57c0e3a3f16a3b41c012. PocketMine-MP releases 4.20.5 and 4.21.1 have been released with the fix.WorkaroundsUsers of PocketMine-MP source installations may manually install the patched version of JsonMapper by backporting commit pmmp/[email protected] plugin may also be able to workaround this issue by using `DataPacketReceiveEvent` to attempt detection of suspicious payloads. An `ErrorException` will be thrown in the crash case, which can be caught by plugins.Referencescweiske/jsonmapper#210 | [] | null | 7.5 | null | null |
CVE-2012-5769 | IBM SPSS Modeler 14.0, 14.1, 14.2 through FP3, and 15.0 before FP2 allows remote attackers to read arbitrary files, and possibly send HTTP requests to intranet servers or cause a denial of service (CPU and memory consumption), via an XML external entity declaration in conjunction with an entity reference. | [
"cpe:2.3:a:ibm:spss_modeler:14.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.0.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.0.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.1.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.1.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.1.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.2.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.2.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.2.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:14.2.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:15.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:spss_modeler:15.0.0.1:*:*:*:*:*:*:*"
] | null | null | null | 5.8 |
|
GHSA-2hg7-f974-32fp | Buffer overflow in Adobe Reader and Acrobat 9.x before 9.5.3, 10.x before 10.1.5, and 11.x before 11.0.1 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2013-0606, CVE-2013-0612, CVE-2013-0617, and CVE-2013-0621. | [] | null | null | null | null |
|
GHSA-4c7m-wxvm-r7gc | Improper parsing of octal bytes in netmask | Improper input validation of octal strings in netmask npm package v1.0.6 and below allows unauthenticated remote attackers to perform indeterminate SSRF, RFI, and LFI attacks on many of the dependent packages. A remote unauthenticated attacker can bypass packages relying on netmask to filter IPs and reach critical VPN or LAN hosts.:exclamation: NOTE: The fix for this issue was incomplete. A subsequent fix was made in version `2.0.1` which was assigned [CVE-2021-29418 / GHSA-pch5-whg9-qr2r](https://github.com/advisories/GHSA-pch5-whg9-qr2r). For complete protection from this vulnerability an upgrade to version 2.0.1 or later is recommended. | [] | null | 9.1 | null | null |
CVE-2022-36340 | WordPress MailOptin plugin <= 1.2.49.0 - Unauthenticated Optin Campaign Cache Deletion vulnerability | Unauthenticated Optin Campaign Cache Deletion vulnerability in MailOptin plugin <= 1.2.49.0 at WordPress. | [
"cpe:2.3:a:mailoptin:mailoptin:*:*:*:*:*:wordpress:*:*"
] | null | 6.5 | null | null |
CVE-2007-0103 | The Adobe PDF specification 1.3, as implemented by Adobe Acrobat before 8.0.0, allows remote attackers to have an unknown impact, possibly including denial of service (infinite loop), arbitrary code execution, or memory corruption, via a PDF file with a (1) crafted catalog dictionary or (2) a crafted Pages attribute that references an invalid page tree node. | [
"cpe:2.3:a:adobe:acrobat_reader:*:*:*:*:*:*:*:*"
] | null | null | null | 6.8 |
|
GHSA-mwxf-r2gx-rf4m | Auth. (admin+) Stored Cross-Site Scripting (XSS) vulnerability in Andreas Heigl authLdap plugin <= 2.5.9 versions. | [] | null | 5.9 | null | null |
|
GHSA-q7p4-5vmg-rr2r | A vulnerability in Cisco SD-WAN Solution software could allow an authenticated, local attacker to cause a buffer overflow on an affected device. The vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending crafted traffic to an affected device. A successful exploit could allow the attacker to gain access to information that they are not authorized to access and make changes to the system that they are not authorized to make. | [] | null | 7.1 | null | null |
|
GHSA-jvrp-gpvq-2crp | Multiple SQL injection vulnerabilities in Oracle Applications 11.0 and Oracle E-Business Suite 11.5.1 through 11.5.8 allow remote attackers to execute arbitrary SQL procedures and queries. | [] | null | null | null | null |
|
GHSA-5987-rf7v-24fh | Unspecified vulnerability in Oracle Sun Solaris 8, 9, and 10 allows local users to affect confidentiality via unknown vectors related to Utility/fdformat. | [] | null | null | null | null |
|
GHSA-9p7q-wmmc-3rgf | A vulnerability, which was classified as critical, has been found in Tenda FH1202 1.2.0.14(408). This issue affects the function formexeCommand of the file /goform/execCommand. The manipulation of the argument cmdinput leads to stack-based buffer overflow. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-258149 was assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | [] | null | 8.8 | null | null |
|
GHSA-fg83-957r-cgq5 | PHP remote file inclusion vulnerability in lib.editor.inc.php in Intelimen InteliEditor 1.2.x allows remote attackers to execute arbitrary PHP code via a URL in the sys_path parameter. | [] | null | null | null | null |
|
GHSA-78h8-6hmr-4752 | Multiple cross-site scripting (XSS) vulnerabilities in Elvin 1.2.2 allow remote attackers to inject arbitrary web script or HTML via the (1) component and (2) priority parameters to buglist.php; and the (3) Username (4) E-mail, (5) Pass, and (6) Confirm pass fields to createaccount.php. | [] | null | null | null | null |
|
GHSA-xrw3-wqph-3fxg | Withdrawn: wallabag subject to Improper Authorization via annotations | Duplicate advisoryThis advisory has been withdrawn because it is a duplicate of [GHSA-mrqx-mjc4-vfh3](https://github.com/advisories/GHSA-mrqx-mjc4-vfh3). This link is maintained to preserve external references.Original DescriptionImproper Authorization in GitHub repository wallabag/wallabag prior to 2.5.3. | [] | null | 4.3 | null | null |
GHSA-3c2p-r64j-24rr | A memory corruption issue was addressed with improved input validation. This issue affected versions prior to iOS 12, macOS Mojave 10.14, tvOS 12, watchOS 5, iTunes 12.9 for Windows, iCloud for Windows 7.7. | [] | null | null | 7.8 | null |
|
GHSA-7pg6-p9p2-jfjx | Missing Authorization vulnerability in WP Tasker WordPress Graphs & Charts allows Exploiting Incorrectly Configured Access Control Security Levels.This issue affects WordPress Graphs & Charts: from n/a through 2.0.8. | [] | null | 5.4 | null | null |
|
CVE-2003-0251 | ypserv NIS server before 2.7 allows remote attackers to cause a denial of service via a TCP client request that does not respond to the server, which causes ypserv to block. | [
"cpe:2.3:a:nis:ypserv_nis_server:*:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
GHSA-4vv7-8gg7-f95h | VMware Workstation 8.x before 8.0.2, VMware Player 4.x before 4.0.2, VMware Fusion 4.x before 4.1.2, VMware ESXi 3.5 through 5.0, and VMware ESX 3.5 through 4.1 use an incorrect ACL for the VMware Tools folder, which allows guest OS users to gain guest OS privileges via unspecified vectors. | [] | null | null | null | null |
|
CVE-2023-25344 | An issue was discovered in swig-templates thru 2.0.4 and swig thru 1.4.2, allows attackers to execute arbitrary code via crafted Object.prototype anonymous function. | [
"cpe:2.3:a:swig-templates_project:swig-templates:*:*:*:*:*:*:*:*",
"cpe:2.3:a:swig_project:swig:*:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
GHSA-9xw9-pvgv-6p76 | Insufficient Error Handling in http-proxy | Affected versions of `http-proxy` are vulnerable to a denial of service attack, wherein an attacker can force an error which will cause the server to crash.RecommendationUpdate to version 0.7.0 or later. | [] | null | 7.5 | null | null |
GHSA-g346-xv5g-x7c6 | Cross-site scripting (XSS) vulnerability in Microsoft SharePoint Server 2010 SP1 allows remote attackers to inject arbitrary web script or HTML via crafted content, leading to administrative command execution, aka "SharePoint XSS Vulnerability." | [] | null | null | null | null |
|
CVE-2016-4485 | The llc_cmsg_rcv function in net/llc/af_llc.c in the Linux kernel before 4.5.5 does not initialize a certain data structure, which allows attackers to obtain sensitive information from kernel stack memory by reading a message. | [
"cpe:2.3:a:novell:suse_linux_enterprise_software_development_kit:11.0:sp4:*:*:*:*:*:*",
"cpe:2.3:o:novell:suse_linux_enterprise_debuginfo:11:sp4:*:*:*:*:*:*",
"cpe:2.3:o:novell:suse_linux_enterprise_server:11:extra:*:*:*:*:*:*",
"cpe:2.3:o:novell:suse_linux_enterprise_server:11:sp4:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:12.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:14.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:15.10:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*"
] | null | null | 7.5 | 5 |
|
CVE-2021-2391 | Vulnerability in the Oracle BI Publisher product of Oracle Fusion Middleware (component: Scheduler). Supported versions that are affected are 5.5.0.0.0, 11.1.1.9.0, 12.2.1.3.0 and 12.2.1.4.0. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle BI Publisher. Successful attacks of this vulnerability can result in takeover of Oracle BI Publisher. CVSS 3.1 Base Score 8.8 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H). | [
"cpe:2.3:a:oracle:bi_publisher:5.5.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:bi_publisher:11.1.1.9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:bi_publisher:12.2.1.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:bi_publisher:12.2.1.4.0:*:*:*:*:*:*:*"
] | null | 8.8 | null | null |
|
RHSA-2020:2345 | Red Hat Security Advisory: bind security update | bind: BIND does not sufficiently limit the number of fetches performed when processing referrals bind: A logic error in code which checks TSIG validity can be used to trigger an assertion failure in tsig.c | [
"cpe:/a:redhat:rhel_eus:8.1::appstream",
"cpe:/o:redhat:rhel_eus:8.1::baseos"
] | null | 7.5 | null | null |
RHSA-2017:2553 | Red Hat Security Advisory: openvswitch security update | openvswitch: Integer underflow in the ofputil_pull_queue_get_config_reply10 function openvswitch: Invalid processing of a malicious OpenFlow role status message openvswitch: Buffer over-read while parsing the group mod OpenFlow message | [
"cpe:/a:redhat:openstack:9::el7"
] | null | null | 5.6 | null |
GHSA-wgw3-qjcr-m37w | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.324 and 19.x and 20.x before 20.0.0.267 on Windows and OS X and before 11.2.202.559 on Linux, Adobe AIR before 20.0.0.233, Adobe AIR SDK before 20.0.0.233, and Adobe AIR SDK & Compiler before 20.0.0.233 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2015-8634, CVE-2015-8635, CVE-2015-8638, CVE-2015-8639, CVE-2015-8640, CVE-2015-8641, CVE-2015-8642, CVE-2015-8643, CVE-2015-8647, CVE-2015-8648, CVE-2015-8649, and CVE-2015-8650. | [] | null | null | 8.8 | null |
|
GHSA-gp26-fcr7-gj7r | Cross-site scripting (XSS) vulnerability in TikiWiki (Tiki) CMS/Groupware 2.2 allows remote attackers to inject arbitrary web script or HTML via the PHP_SELF portion of a URI to (1) tiki-galleries.php, (2) tiki-list_file_gallery.php, (3) tiki-listpages.php, and (4) tiki-orphan_pages.php. | [] | null | null | null | null |
|
CVE-2013-7182 | Cross-site scripting (XSS) vulnerability in firewall/schedule/recurrdlg in Fortinet FortiOS 5.0.5 allows remote attackers to inject arbitrary web script or HTML via the mkey parameter. | [
"cpe:2.3:o:fortinet:fortios:5.0.5:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2024-46373 | Dedecms V5.7.115 contains an arbitrary code execution via file upload vulnerability in the backend. | [
"cpe:2.3:a:dedecms:dedecms:*:*:*:*:*:*:*:*"
] | null | 8.8 | null | null |
|
GHSA-22wm-6r58-545p | In the Microchip MiWi v6.5 software stack, there is a possibility of frame counters being being validated / updated prior to message authentication. | [] | null | 7.5 | null | null |
|
CVE-2011-1053 | Unspecified vulnerability in the Mach-O input file loader in Hex-Rays IDA Pro 5.7 and 6.0 allows user-assisted remote attackers to cause a denial of service (out-of-memory exception and inability to analyze code) via a crafted Mach-O file. | [
"cpe:2.3:a:hex-rays:ida:5.7:*:pro:*:*:*:*:*",
"cpe:2.3:a:hex-rays:ida:6.0:*:pro:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2023-42480 | Information Disclosure in NetWeaver AS Java Logon | The unauthenticated attacker in NetWeaver AS Java Logon application - version 7.50, can brute force the login functionality to identify the legitimate user ids. This will have an impact on confidentiality but there is no other impact on integrity or availability.
| [
"cpe:2.3:a:sap:netweaver_application_server_java:7.50:*:*:*:*:*:*:*"
] | null | 5.3 | null | null |
GHSA-h7xj-xr99-gpjr | H3C Magic R100 R100V100R005.bin was discovered to contain a stack overflow via the ipqos_lanip_dellist interface at /goform/aspForm. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted payload. | [] | null | 4.9 | null | null |
|
CVE-2021-29973 | Password autofill was enabled without user interaction on insecure websites on Firefox for Android. This was corrected to require user interaction with the page before a user's password would be entered by the browser's autofill functionality *This bug only affects Firefox for Android. Other operating systems are unaffected.*. This vulnerability affects Firefox < 90. | [
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:android:*:*"
] | null | 8.8 | null | 6.8 |
|
CVE-2022-25887 | Regular Expression Denial of Service (ReDoS) | The package sanitize-html before 2.7.1 are vulnerable to Regular Expression Denial of Service (ReDoS) due to insecure global regular expression replacement logic of HTML comment removal. | [
"cpe:2.3:a:apostrophecms:sanitize-html:*:*:*:*:*:node.js:*:*"
] | null | 5.3 | null | null |
CVE-2022-40048 | Flatpress v1.2.1 was discovered to contain a remote code execution (RCE) vulnerability in the Upload File function. | [
"cpe:2.3:a:flatpress:flatpress:1.2.1:*:*:*:*:*:*:*"
] | null | 7.2 | null | null |
|
CVE-2021-3863 | Cross-site Scripting (XSS) - Generic in snipe/snipe-it | snipe-it is vulnerable to Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') | [
"cpe:2.3:a:snipeitapp:snipe-it:*:*:*:*:*:*:*:*"
] | null | null | 5.5 | null |
GHSA-wxm7-7gfc-ppfv | Certain NETGEAR devices are affected by command injection by an authenticated user. This affects R6400 before 1.0.1.52, R6400v2 before 1.0.4.84, R6700v3 before 1.0.4.84, R6700v2 before 1.2.0.62, R6900v2 before 1.2.0.62, and R7000P before 1.3.2.124. | [] | null | null | null | null |
|
GHSA-f929-pjc3-gg99 | An elevation of privilege vulnerability exists in Windows when the Windows kernel-mode driver fails to properly handle objects in memory, aka 'Win32k Elevation of Privilege Vulnerability'. This CVE ID is unique from CVE-2020-0957, CVE-2020-0958. | [] | null | null | null | null |
|
CVE-2022-29148 | Visual Studio Remote Code Execution Vulnerability | Visual Studio Remote Code Execution Vulnerability | [
"cpe:2.3:a:microsoft:visual_studio_2017:*:*:*:*:*:*:*:*"
] | null | 7.8 | null | null |
CVE-2022-20880 | Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers Remote Command Execution and Denial of Service Vulnerabilities | Multiple vulnerabilities in the web-based management interface of Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers could allow an authenticated, remote attacker to execute arbitrary code on an affected device or cause the device to restart unexpectedly, resulting in a denial of service (DoS) condition. These vulnerabilities are due to insufficient validation of user fields within incoming HTTP packets. An attacker could exploit these vulnerabilities by sending a crafted request to the web-based management interface. A successful exploit could allow the attacker to execute arbitrary commands on an affected device with root-level privileges or to cause the device to restart unexpectedly, resulting in a DoS condition. To exploit these vulnerabilities, an attacker would need to have valid Administrator credentials on the affected device. Cisco has not released software updates that address these vulnerabilities. | [
"cpe:2.3:o:cisco:rv215w_firmware:1.0.3.55:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:rv215w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:rv130w_firmware:1.0.3.55:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:rv130w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:rv130_firmware:1.0.3.55:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:rv130:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:rv110w_firmware:1.0.3.55:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:rv110w:-:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:application_extension_platform:1.0.3.55:*:*:*:*:*:*:*"
] | null | 4.7 | null | null |
GHSA-jvjr-c2c2-jvj8 | Adobe Acrobat and Reader versions 2019.010.20100 and earlier, 2019.010.20099 and earlier, 2017.011.30140 and earlier, 2017.011.30138 and earlier, 2015.006.30495 and earlier, and 2015.006.30493 and earlier have a use after free vulnerability. Successful exploitation could lead to arbitrary code execution. | [] | null | null | null | null |
|
CVE-2025-32577 | WordPress Build App Online Plugin <= 1.0.23 - Local File Inclusion vulnerability | Improper Control of Filename for Include/Require Statement in PHP Program ('PHP Remote File Inclusion') vulnerability in hakeemnala Build App Online allows PHP Local File Inclusion. This issue affects Build App Online: from n/a through 1.0.23. | [] | null | 9.8 | null | null |
CVE-2024-5731 | A vulnerability in the IPS Manager, Central Manager, and Local Manager communication workflow allows an attacker to control the destination of a request by manipulating the parameter, thereby leveraging sensitive information. | [] | null | 6.8 | null | null |
|
CVE-2015-7286 | CSL DualCom GPRS CS2300-R devices with firmware 1.25 through 3.53 rely on a polyalphabetic substitution cipher with hardcoded keys, which makes it easier for remote attackers to defeat a cryptographic protection mechanism by capturing IP or V.22bis PSTN protocol traffic. | [
"cpe:2.3:o:csl_dualcom:gprs_cs2300-r_firmware:1.25:*:*:*:*:*:*:*",
"cpe:2.3:o:csl_dualcom:gprs_cs2300-r_firmware:3.53:*:*:*:*:*:*:*",
"cpe:2.3:h:csl_dualcom:gprs:cs2300-r:*:*:*:*:*:*:*"
] | null | null | null | 6.4 |
|
CVE-2014-4782 | IBM InfoSphere BigInsights 2.1.2 allows remote authenticated users to discover SMTP server credentials via vectors related to the Alert management service. IBM X-Force ID: 95029. | [
"cpe:2.3:a:ibm:infosphere_biginsights:2.1.2:*:*:*:*:*:*:*"
] | null | null | 6.5 | 4 |
|
GHSA-m9rr-495w-r5xp | Cross-site scripting (XSS) vulnerability in IBM InfoSphere Information Server through 8.5 FP3, 8.7 through FP2, and 9.1 allows remote authenticated users to inject arbitrary web script or HTML via vectors related to the web console. | [] | null | null | null | null |
|
CVE-2022-39862 | Improper authorization in Dynamic Lockscreen prior to SMR Sep-2022 Release 1 in Android R(11) and 3.3.03.66 in Android S(12) allows unauthorized use of javascript interface api. | [
"cpe:2.3:a:samsung:dynamic_lockscreen:*:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:11.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:12.0:*:*:*:*:*:*:*"
] | null | 5.3 | null | null |
|
GHSA-5fhf-5pr4-45fx | Adobe Flash Player before 11.2.202.229 in Google Chrome before 18.0.1025.151 allow attackers to cause a denial of service (memory corruption) or possibly have unspecified other impact via unknown vectors, a different vulnerability than CVE-2012-0724. | [] | null | null | null | null |
|
RHSA-2008:0508 | Red Hat Security Advisory: kernel security and bug fix update | kernel: linux x86_64 ia32 emulation leaks uninitialized data Kernel doesn't clear DF for signal handlers kernel: ptrace: Crash on PTRACE_{ATTACH,DETACH} race kernel: [x86_64] The string instruction version didn't zero the output on exception. | [
"cpe:/o:redhat:enterprise_linux:4::as",
"cpe:/o:redhat:enterprise_linux:4::desktop",
"cpe:/o:redhat:enterprise_linux:4::es",
"cpe:/o:redhat:enterprise_linux:4::ws"
] | null | null | null | null |
GHSA-cwx6-cx7x-4q34 | LibreNMS vulnerable to SQL injection time-based leads to database extraction | SummarySQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter.DetailsThere is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php
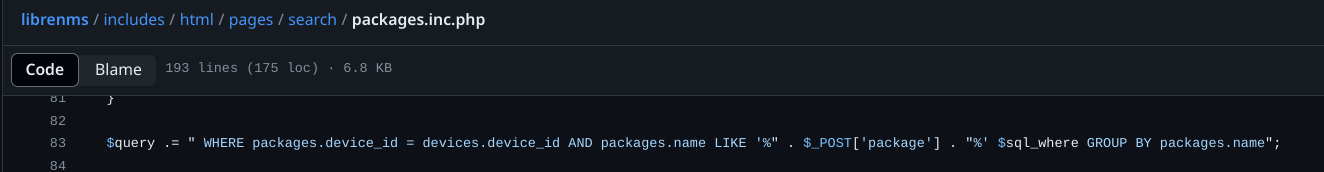PoChttps://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6ImpactWith this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials | [] | null | 8.8 | null | null |
CVE-2023-0468 | A use-after-free flaw was found in io_uring/poll.c in io_poll_check_events in the io_uring subcomponent in the Linux Kernel due to a race condition of poll_refs. This flaw may cause a NULL pointer dereference. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:-:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:rc4:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:rc5:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.1:rc6:*:*:*:*:*:*"
] | null | 4.7 | null | null |
|
GHSA-m793-w2w5-4gf3 | SQL injection vulnerability in index.php in MAXdev MDPro (MD-Pro) 1.0.76 allows remote attackers to execute arbitrary SQL commands via a "Firefox ID=" substring in a Referer HTTP header. | [] | null | null | null | null |
|
CVE-2012-3194 | Unspecified vulnerability in the Oracle BI Publisher component in Oracle Fusion Middleware 10.1.3.4.2, 11.1.1.5.0, 11.1.1.6.0, and 11.1.1.6.2 allows remote attackers to affect integrity via unknown vectors related to Administration. | [
"cpe:2.3:a:oracle:fusion_middleware:10.1.3.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:fusion_middleware:11.1.1.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:fusion_middleware:11.1.1.6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:fusion_middleware:11.1.1.6.2:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
GHSA-x774-v4vm-3h8m | An issue discovered in GitLab CE/EE affecting all versions from 16.11 prior to 17.6.5, 17.7 prior to 17.7.4, and 17.8 prior to 17.8.2 meant that long-lived connections in ActionCable potentially allowed revoked Personal Access Tokens access to streaming results. | [] | null | 4.2 | null | null |
|
CVE-2019-5040 | An exploitable information disclosure vulnerability exists in the Weave MessageLayer parsing of Openweave-core version 4.0.2 and Nest Cam IQ Indoor version 4620002. A specially crafted weave packet can cause an integer overflow to occur, resulting in PacketBuffer data reuse. An attacker can send a packet to trigger this vulnerability. | [
"cpe:2.3:a:openweave:openweave-core:4.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:google:nest_cam_iq_indoor_firmware:4620002:*:*:*:*:*:*:*",
"cpe:2.3:h:google:nest_cam_iq_indoor:-:*:*:*:*:*:*:*"
] | null | null | 8.2 | null |
|
CVE-2024-47654 | No Rate Limiting vulnerability | This vulnerability exists in Shilpi Client Dashboard due to lack of rate limiting and Captcha protection for OTP requests in certain API endpoint. An unauthenticated remote attacker could exploit this vulnerability by sending multiple OTP request through vulnerable API endpoints, which could lead to the OTP bombing on the targeted system. | [
"cpe:2.3:a:shilpisoft:client_dashboard:*:*:*:*:*:*:*:*"
] | 7.1 | null | null | null |
RHSA-2023:1590 | Red Hat Security Advisory: kpatch-patch security update | ALSA: pcm: Move rwsem lock inside snd_ctl_elem_read to prevent UAF | [
"cpe:/o:redhat:rhel_e4s:8.1::baseos"
] | null | 7.8 | null | null |
CVE-2023-35708 | In Progress MOVEit Transfer before 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), and 2023.0.3 (15.0.3), a SQL injection vulnerability has been identified in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer's database. An attacker could submit a crafted payload to a MOVEit Transfer application endpoint that could result in modification and disclosure of MOVEit database content. These are fixed versions of the DLL drop-in: 2020.1.10 (12.1.10), 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), and 2023.0.3 (15.0.3). | [
"cpe:2.3:a:progress:moveit_transfer:*:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
GHSA-ph65-4f3r-7fv8 | Awstats version 7.6 and earlier is vulnerable to a path traversal flaw in the handling of the "config" and "migrate" parameters resulting in unauthenticated remote code execution. | [] | null | null | 9.8 | null |
|
GHSA-3cfr-rpp6-j86f | Adobe Flash Player before 10.3.183.20 and 11.x before 11.3.300.257 on Windows and Mac OS X; before 10.3.183.20 and 11.x before 11.2.202.236 on Linux; before 11.1.111.10 on Android 2.x and 3.x; and before 11.1.115.9 on Android 4.x, and Adobe AIR before 3.3.0.3610, allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2012-2037. | [] | null | 7.5 | null | null |
|
GHSA-7cq4-vrj8-97j4 | Internet Explorer in Microsoft Windows 7 SP1, Windows Server 2008 R2 SP1, Windows 8.1 and Windows RT 8.1, Windows Server 2012 and R2, and Windows 10 Gold, 1511, 1607, 1703, 1709, and Windows Server 2016 allow information disclosure, due to how Internet Explorer handles objects in memory, aka "Internet Explorer Information Disclosure Vulnerability". | [] | null | null | 4.3 | null |
|
CVE-2024-50255 | Bluetooth: hci: fix null-ptr-deref in hci_read_supported_codecs | In the Linux kernel, the following vulnerability has been resolved:
Bluetooth: hci: fix null-ptr-deref in hci_read_supported_codecs
Fix __hci_cmd_sync_sk() to return not NULL for unknown opcodes.
__hci_cmd_sync_sk() returns NULL if a command returns a status event.
However, it also returns NULL where an opcode doesn't exist in the
hci_cc table because hci_cmd_complete_evt() assumes status = skb->data[0]
for unknown opcodes.
This leads to null-ptr-deref in cmd_sync for HCI_OP_READ_LOCAL_CODECS as
there is no hci_cc for HCI_OP_READ_LOCAL_CODECS, which always assumes
status = skb->data[0].
KASAN: null-ptr-deref in range [0x0000000000000070-0x0000000000000077]
CPU: 1 PID: 2000 Comm: kworker/u9:5 Not tainted 6.9.0-ga6bcb805883c-dirty #10
Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.15.0-1 04/01/2014
Workqueue: hci7 hci_power_on
RIP: 0010:hci_read_supported_codecs+0xb9/0x870 net/bluetooth/hci_codec.c:138
Code: 08 48 89 ef e8 b8 c1 8f fd 48 8b 75 00 e9 96 00 00 00 49 89 c6 48 ba 00 00 00 00 00 fc ff df 4c 8d 60 70 4c 89 e3 48 c1 eb 03 <0f> b6 04 13 84 c0 0f 85 82 06 00 00 41 83 3c 24 02 77 0a e8 bf 78
RSP: 0018:ffff888120bafac8 EFLAGS: 00010212
RAX: 0000000000000000 RBX: 000000000000000e RCX: ffff8881173f0040
RDX: dffffc0000000000 RSI: ffffffffa58496c0 RDI: ffff88810b9ad1e4
RBP: ffff88810b9ac000 R08: ffffffffa77882a7 R09: 1ffffffff4ef1054
R10: dffffc0000000000 R11: fffffbfff4ef1055 R12: 0000000000000070
R13: 0000000000000000 R14: 0000000000000000 R15: ffff88810b9ac000
FS: 0000000000000000(0000) GS:ffff8881f6c00000(0000) knlGS:0000000000000000
CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033
CR2: 00007f6ddaa3439e CR3: 0000000139764003 CR4: 0000000000770ef0
PKRU: 55555554
Call Trace:
<TASK>
hci_read_local_codecs_sync net/bluetooth/hci_sync.c:4546 [inline]
hci_init_stage_sync net/bluetooth/hci_sync.c:3441 [inline]
hci_init4_sync net/bluetooth/hci_sync.c:4706 [inline]
hci_init_sync net/bluetooth/hci_sync.c:4742 [inline]
hci_dev_init_sync net/bluetooth/hci_sync.c:4912 [inline]
hci_dev_open_sync+0x19a9/0x2d30 net/bluetooth/hci_sync.c:4994
hci_dev_do_open net/bluetooth/hci_core.c:483 [inline]
hci_power_on+0x11e/0x560 net/bluetooth/hci_core.c:1015
process_one_work kernel/workqueue.c:3267 [inline]
process_scheduled_works+0x8ef/0x14f0 kernel/workqueue.c:3348
worker_thread+0x91f/0xe50 kernel/workqueue.c:3429
kthread+0x2cb/0x360 kernel/kthread.c:388
ret_from_fork+0x4d/0x80 arch/x86/kernel/process.c:147
ret_from_fork_asm+0x1a/0x30 arch/x86/entry/entry_64.S:244 | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc4:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc5:*:*:*:*:*:*"
] | null | 5.5 | null | null |
GHSA-j394-52j2-56h6 | The Goat Forum (aka com.gcspublishing.goatspot) application 3.9.15 for Android does not verify X.509 certificates from SSL servers, which allows man-in-the-middle attackers to spoof servers and obtain sensitive information via a crafted certificate. | [] | null | null | null | null |
|
GHSA-pq2g-wx69-c263 | Netplex Json-smart Uncontrolled Recursion vulnerability | A security issue was found in Netplex Json-smart 2.5.0 through 2.5.1. When loading a specially crafted JSON input, containing a large number of ’{’, a stack exhaustion can be trigger, which could allow an attacker to cause a Denial of Service (DoS). This issue exists because of an incomplete fix for CVE-2023-1370.The fixed version only addresses the default modes provided by [JSONParser](https://github.com/netplex/json-smart-v2/blob/master/json-smart/src/main/java/net/minidev/json/parser/JSONParser.java#L118), such as `MODE_RFC4627`. If you create the JSONParser manually or with custom options, make sure to set the `LIMIT_JSON_DEPTH` option. | [] | null | 7.5 | null | null |
GHSA-p2mr-p4xw-7cm4 | The wp-ultimate-recipe plugin before 3.12.7 for WordPress has stored XSS. | [] | null | null | 5.4 | null |
|
CVE-2019-13187 | The Rich Text Formatter (Redactor) extension through v1.1.1 for Symphony CMS has an Unauthenticated arbitrary file upload vulnerability in content.fileupload.php and content.imageupload.php. | [
"cpe:2.3:a:symphonyextensions:rich_text_formatter:*:*:*:*:*:*:*:*"
] | null | null | 9.8 | 7.5 |
|
GHSA-p28j-xhp9-88wp | A vulnerability has been found in ajenti 2.1.31 and classified as critical. This vulnerability affects unknown code of the component API. The manipulation leads to privilege escalation. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. Upgrading to version 2.1.32 is able to address this issue. The name of the patch is 7aa146b724e0e20cfee2c71ca78fafbf53a8767c. It is recommended to upgrade the affected component. | [] | null | 8.8 | null | null |
|
CVE-2022-32948 | An out-of-bounds read was addressed with improved bounds checking. This issue is fixed in iOS 15.6 and iPadOS 15.6, macOS Monterey 12.5. An app may be able to execute arbitrary code with kernel privileges. | [
"cpe:2.3:o:apple:ipados:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:macos:*:*:*:*:*:*:*:*"
] | null | 7.8 | null | null |
|
CVE-2023-6758 | Thecosy IceCMS API PlanetCommentList access control | A vulnerability was found in Thecosy IceCMS 2.0.1. It has been rated as critical. Affected by this issue is some unknown functionality of the file /adplanet/PlanetCommentList of the component API. The manipulation leads to improper access controls. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-247886 is the identifier assigned to this vulnerability. | [
"cpe:2.3:a:thecosy:icecms:2.0.1:*:*:*:*:*:*:*"
] | null | 5.3 | 5.3 | 5 |
CVE-2024-36500 | Privilege escalation vulnerability in the AMS module
Impact: Successful exploitation of this vulnerability may affect service confidentiality. | [
"cpe:2.3:o:huawei:harmonyos:3.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:harmonyos:3.1.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:harmonyos:4.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:harmonyos:4.2.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:emui:13.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:emui:14.0.0:*:*:*:*:*:*:*"
] | null | 7.8 | null | null |
|
CVE-2022-21777 | In Autoboot, there is a possible permission bypass due to a missing permission check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS06713894; Issue ID: ALPS06713894. | [
"cpe:2.3:o:google:android:11.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:12.0:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6580:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6735:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6739:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6761:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6765:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6768:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6771:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6779:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6785:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6833:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6853:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6873:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6875:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6877:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6879:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6885:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6891:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6893:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6895:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt6983:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8167:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8167s:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8168:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8173:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8175:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8185:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8321:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8362a:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8365:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8385:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8666:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8667:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8675:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8765:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8766:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8768:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8786:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8788:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8789:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8791:-:*:*:*:*:*:*:*",
"cpe:2.3:h:mediatek:mt8797:-:*:*:*:*:*:*:*"
] | null | 7.8 | null | 4.6 |
|
GHSA-q93q-4mxv-67mp | The tempname_ensure function in lib/routines.h in a2ps 4.14 and earlier, as used by the spy_user function and possibly other functions, allows local users to modify arbitrary files via a symlink attack on a temporary file. | [] | null | null | null | null |
|
RHSA-2019:3742 | Red Hat Security Advisory: qemu-kvm-rhev security update | QEMU: qxl: null pointer dereference while releasing spice resources QEMU: slirp: heap buffer overflow during packet reassembly | [
"cpe:/a:redhat:openstack:14::el7"
] | null | null | 7 | null |
GHSA-48m2-xcr6-vx9f | Multiple PHP remote file inclusion vulnerabilities in Barry Nauta BRIM 1.2.1 and earlier allow remote attackers to execute arbitrary PHP code via a URL in the renderer parameter in template.tpl.php in (1) templates/barrel/, (2) templates/sidebar/, (3) templates/text-only, (4) templates/slashdot/, (5) templates/penguin/, (6) templates/pda/, (7) templates/oerdec/, (8) templates/nifty/, (9) templates/mylook, and (10) templates/barry/. | [] | null | null | null | null |
|
CVE-2021-1527 | Cisco Webex Player Memory Corruption Vulnerability | A vulnerability in Cisco Webex Player for Windows and MacOS could allow an attacker to cause the affected software to terminate or to gain access to memory state information that is related to the vulnerable application. The vulnerability is due to insufficient validation of values in Webex recording files that are stored in Webex Recording Format (WRF). An attacker could exploit this vulnerability by sending a malicious WRF file to a user as a link or email attachment and then persuading the user to open the file with the affected software on the local system. A successful exploit could allow the attacker to crash the affected software and view memory state information. | [
"cpe:2.3:a:cisco:webex_player:*:*:*:*:*:macos:*:*",
"cpe:2.3:a:cisco:webex_player:*:*:*:*:*:windows:*:*"
] | null | 5.3 | null | null |
GHSA-9m72-gvff-h492 | A vulnerability has been found in SourceCodester Automatic Question Paper Generator System 1.0 and classified as critical. Affected by this vulnerability is an unknown functionality of the file admin/courses/view_course.php of the component GET Parameter Handler. The manipulation of the argument id leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-223285 was assigned to this vulnerability. | [] | null | 9.8 | null | null |
|
CVE-2013-1793 | openstack-utils openstack-db has insecure password creation | [
"cpe:2.3:a:redhat:openstack:2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:redhat:openstack:3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:redhat:openstack:4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:redhat:openstack_essex:-:*:*:*:*:*:*:*"
] | null | 7.5 | null | 5 |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.