id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
57.2k
| cpes
sequencelengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
GHSA-82p3-6f5v-565p | Unspecified vulnerability in HP Integrated Lights-Out (iLO) firmware 3 before 1.85 and 4 before 2.22 allows remote authenticated users to cause a denial of service via unknown vectors. | [] | null | null | null | null |
|
CVE-2014-4656 | Multiple integer overflows in sound/core/control.c in the ALSA control implementation in the Linux kernel before 3.15.2 allow local users to cause a denial of service by leveraging /dev/snd/controlCX access, related to (1) index values in the snd_ctl_add function and (2) numid values in the snd_ctl_remove_numid_conflict function. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:suse:linux_enterprise_server:10:sp4:*:*:ltss:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:12.04:*:*:*:esm:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux_desktop:6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux_eus:6.6:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux_server:6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux_server_aus:6.6:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux_server_tus:6.6:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux_workstation:6.0:*:*:*:*:*:*:*"
] | null | null | null | 4.6 |
|
CVE-2018-0335 | A vulnerability in the web portal authentication process of Cisco Prime Collaboration Provisioning could allow an unauthenticated, local attacker to view sensitive data. The vulnerability is due to improper logging of authentication data. An attacker could exploit this vulnerability by monitoring a specific World-Readable file for this authentication data (Cleartext Passwords). An exploit could allow the attacker to gain authentication information for other users. Cisco Bug IDs: CSCvd86602. | [
"cpe:2.3:a:cisco:prime_collaboration:12.2:*:*:*:*:*:*:*"
] | null | null | 7.8 | 2.1 |
|
RHSA-2005:472 | Red Hat Security Advisory: kernel security update | security flaw security flaw security flaw | [
"cpe:/o:redhat:enterprise_linux:3::as",
"cpe:/o:redhat:enterprise_linux:3::desktop",
"cpe:/o:redhat:enterprise_linux:3::es",
"cpe:/o:redhat:enterprise_linux:3::ws"
] | null | null | null | null |
GHSA-jvv6-vvpc-5jxh | SQL injection vulnerability in the ElearningForce Flash Magazine Deluxe (com_flashmagazinedeluxe) component for Joomla! allows remote attackers to execute arbitrary SQL commands via the mag_id parameter in a magazine action to index.php. | [] | null | null | null | null |
|
GHSA-88p5-45fx-5x87 | A security flaw was found in the chap_server_compute_md5() function in the ISCSI target code in the Linux kernel in a way an authentication request from an ISCSI initiator is processed. An unauthenticated remote attacker can cause a stack buffer overflow and smash up to 17 bytes of the stack. The attack requires the iSCSI target to be enabled on the victim host. Depending on how the target's code was built (i.e. depending on a compiler, compile flags and hardware architecture) an attack may lead to a system crash and thus to a denial-of-service or possibly to a non-authorized access to data exported by an iSCSI target. Due to the nature of the flaw, privilege escalation cannot be fully ruled out, although we believe it is highly unlikely. Kernel versions 4.18.x, 4.14.x and 3.10.x are believed to be vulnerable. | [] | null | 7 | null | null |
|
PYSEC-2024-144 | null | Nullptr dereference in paddle.crop in PaddlePaddle before 2.6.0. This flaw can cause a runtime crash and a denial of service.
| [] | null | 7.5 | null | null |
GHSA-2mvc-xm6m-7jj5 | An elevation of privilege vulnerability in the Qualcomm camera driver in Android before 2016-11-05 could enable a local malicious application to execute arbitrary code within the context of the kernel. This issue is rated as High because it first requires compromising a privileged process. Android ID: A-30074605. References: Qualcomm QC-CR#1049826. | [] | null | null | 7.8 | null |
|
CVE-2019-12519 | An issue was discovered in Squid through 4.7. When handling the tag esi:when when ESI is enabled, Squid calls ESIExpression::Evaluate. This function uses a fixed stack buffer to hold the expression while it's being evaluated. When processing the expression, it could either evaluate the top of the stack, or add a new member to the stack. When adding a new member, there is no check to ensure that the stack won't overflow. | [
"cpe:2.3:a:squid-cache:squid:*:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:19.10:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:20.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*"
] | null | 9.8 | null | 7.5 |
|
CVE-2021-31178 | Microsoft Office Information Disclosure Vulnerability | Microsoft Office Information Disclosure Vulnerability | [
"cpe:2.3:a:microsoft:365_apps:-:*:*:*:enterprise:*:*:*",
"cpe:2.3:a:microsoft:excel:2013:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2013:sp1:*:*:rt:*:*:*",
"cpe:2.3:a:microsoft:excel:2016:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:office:2013:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:office:2013:sp1:*:*:rt:*:*:*",
"cpe:2.3:a:microsoft:office:2016:*:*:*:*:-:*:*",
"cpe:2.3:a:microsoft:office:2019:*:*:*:*:-:*:*",
"cpe:2.3:a:microsoft:office_online_server:-:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:office_web_apps_server:2013:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:word:2013:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:word:2013:sp1:*:*:rt:*:*:*",
"cpe:2.3:a:microsoft:word:2016:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:office:2019:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2016:*:*:*:*:*:x86:*",
"cpe:2.3:a:microsoft:excel:2016:*:*:*:*:*:x64:*",
"cpe:2.3:a:microsoft:office:2016:*:*:*:*:*:x86:*",
"cpe:2.3:a:microsoft:office:2016:*:*:*:*:*:x64:*",
"cpe:2.3:a:microsoft:excel:2013:sp1:*:*:*:*:x86:*",
"cpe:2.3:a:microsoft:excel:2013:sp1:*:*:*:*:x64:*",
"cpe:2.3:a:microsoft:office:2013:sp1:*:*:*:*:x86:*",
"cpe:2.3:a:microsoft:office:2013:sp1:*:*:*:*:x64:*"
] | null | 5.5 | null | null |
CVE-2021-43336 | An Out-of-Bounds Write vulnerability exists when reading a DXF or DWG file using Open Design Alliance Drawings SDK before 2022.11. The specific issue exists within the parsing of DXF and DWG files. Crafted data in a DXF or DWG file (an invalid number of properties) can trigger a write operation past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. | [
"cpe:2.3:a:opendesign:drawings_software_development_kit:*:*:*:*:*:*:*:*",
"cpe:2.3:a:siemens:jt2go:*:*:*:*:*:*:*:*",
"cpe:2.3:a:siemens:solid_edge:se2022:-:*:*:*:*:*:*",
"cpe:2.3:a:siemens:teamcenter_visualization:*:*:*:*:*:*:*:*",
"cpe:2.3:a:siemens:teamcenter_visualization:13.1.0:*:*:*:*:*:*:*"
] | null | 7.8 | null | 6.8 |
|
CVE-2018-14481 | Osclass 3.7.4 has XSS via the query string to index.php, a different vulnerability than CVE-2014-6280. | [
"cpe:2.3:a:osclass:osclass:3.7.4:*:*:*:*:*:*:*"
] | null | null | 6.1 | 4.3 |
|
CVE-2009-0780 | The aspath_prepend function in rde_attr.c in bgpd in OpenBSD 4.3 and 4.4 allows remote attackers to cause a denial of service (application crash) via an Autonomous System (AS) advertisement containing a long AS path. | [
"cpe:2.3:o:openbsd:openbsd:4.3:*:*:*:*:*:*:*",
"cpe:2.3:o:openbsd:openbsd:4.4:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
CVE-2019-10349 | A stored cross site scripting vulnerability in Jenkins Dependency Graph Viewer Plugin 0.13 and earlier allowed attackers able to configure jobs in Jenkins to inject arbitrary HTML and JavaScript in the plugin-provided web pages in Jenkins. | [
"cpe:2.3:a:jenkins:dependency_graph_viewer:*:*:*:*:*:jenkins:*:*"
] | null | 5.4 | null | 3.5 |
|
CVE-2017-13270 | A elevation of privilege vulnerability in the upstream kernel mnh_sm driver. Product: Android. Versions: Android kernel. Android ID: A-69474744. | [
"cpe:2.3:o:google:android:-:*:*:*:*:*:*:*"
] | null | null | 7.3 | 7.5 |
|
CVE-2013-4438 | Salt (aka SaltStack) before 0.17.1 allows remote attackers to execute arbitrary YAML code via unspecified vectors. NOTE: the vendor states that this might not be a vulnerability because the YAML to be loaded has already been determined to be safe. | [
"cpe:2.3:a:saltstack:salt:*:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.7.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.8.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.8.7:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.8.8:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.8.9:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.2:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.3:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.4:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.5:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.6:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.7:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.8:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.9.9:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.10.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.10.2:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.10.3:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.10.4:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.10.5:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.11.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.12.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.13.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.14.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.15.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.15.1:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.16.0:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.16.2:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.16.3:*:*:*:*:*:*:*",
"cpe:2.3:a:saltstack:salt:0.16.4:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
CVE-2022-39838 | Systematic FIX Adapter (ALFAFX) 2.4.0.25 13/09/2017 allows remote file inclusion via a UNC share pathname, and also allows absolute path traversal to local pathnames. | [
"cpe:2.3:o:systematicalpha:systematic_fix_adapter_firmware:2.4.0.25:*:*:*:*:*:*:*",
"cpe:2.3:h:systematicalpha:systematic_fix_adapter:-:*:*:*:*:*:*:*"
] | null | 8.6 | null | null |
|
GHSA-8429-c5x8-7qw9 | IBM BigFix Platform could allow an attacker on the local network to crash the BES server using a specially crafted XMLSchema request. | [] | null | null | 6.5 | null |
|
CVE-2010-4015 | Buffer overflow in the gettoken function in contrib/intarray/_int_bool.c in the intarray array module in PostgreSQL 9.0.x before 9.0.3, 8.4.x before 8.4.7, 8.3.x before 8.3.14, and 8.2.x before 8.2.20 allows remote authenticated users to cause a denial of service (crash) and possibly execute arbitrary code via integers with a large number of digits to unspecified functions. | [
"cpe:2.3:a:postgresql:postgresql:8.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.5:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.6:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.7:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.8:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.9:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.10:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.11:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.12:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.13:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.5:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.6:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.5:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.6:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.7:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.8:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.9:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.10:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.11:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.12:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.13:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.14:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.15:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.16:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.17:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.18:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.2.19:*:*:*:*:*:*:*"
] | null | null | null | 6.5 |
|
CVE-2008-0427 | Directory traversal vulnerability in file.php in bloofoxCMS 0.3 allows remote attackers to read arbitrary files via a .. (dot dot) in the file parameter. | [
"cpe:2.3:a:bloo:bloofoxcms:0.3:*:*:*:*:*:*:*"
] | null | null | null | 7.8 |
|
RHSA-2022:0226 | Red Hat Security Advisory: Red Hat OpenShift Enterprise Logging bug fix and security update (5.1.7) | nodejs-ua-parser-js: ReDoS via malicious User-Agent header log4j-core: remote code execution via JDBC Appender | [
"cpe:/a:redhat:logging:5.1::el8"
] | null | 6.6 | null | null |
GHSA-vq63-8f72-f486 | AspNetCore Remote Authenticator for CIE3.0 Allows SAML Response Signature Verification Bypass | DescriptionAuthentication using Spid and CIE is based on the SAML2 standard which provides for two entities:Identity Provider (IdP): the system that authenticates users and provides identity information ( SAML assertions ) to the Service Provider, essentially, it is responsible for managing user credentials and identity;
Service Provider (SP): The system that provides a service to the user and relies on the Identity Provider to authenticate the user, receives SAML assertions from the IdP to grant access to resources.
The library `cie-aspnetcorerefers` to the second entity, i.e. the SP, and implements the validation logic of the SAML assertions present within the SAML response . The following is a summary diagram of an authentication flow via SAML: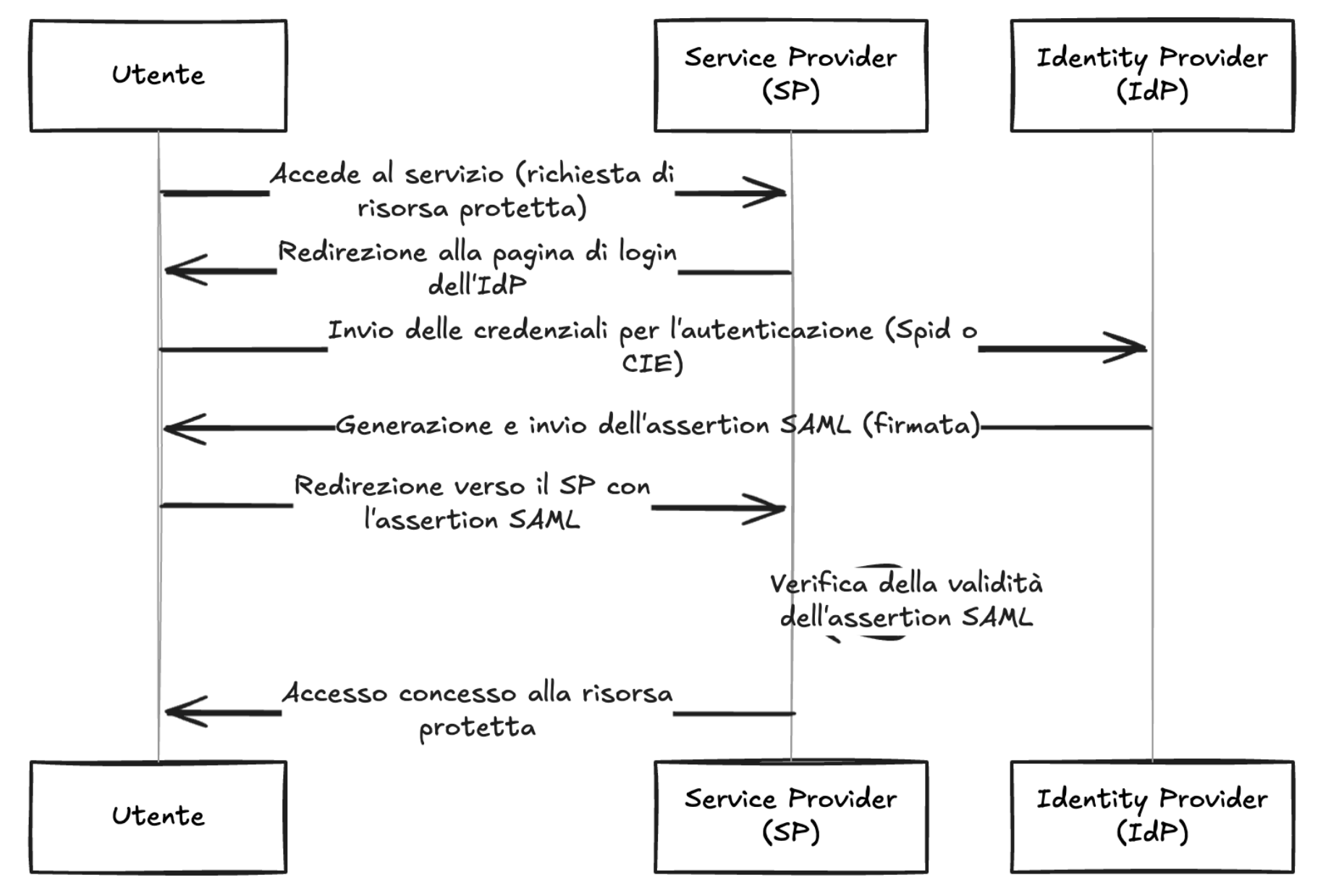As shown in the diagram, the IdP, after verifying the user's credentials, generates a signed SAML response, this is propagated to the SP by the user's browser and the SP, after verifying the signature, can extract the data needed to build the user's session.The signature validation logic is central as it ensures that you cannot craft a SAML response with arbitrary assertions and thus impersonate other users.The following is the validation code implemented in `cie-aspnetcore`.The parameter `signedDocument` contains the SAML response in XML format, while the parameter `identityProvider` can contain the IdP info. If the parameter `identityProvider` has been specified, the public certificates of that IdP are extracted, so as to force their use during the signature verification, otherwise the certificates configured within the application are used.Next, a response envelope is generated nodeList within which all XML elements containing an XML signature of part or all of the SAML response envelope are saved.Finally, the first element of this list, i.e. the first signature found, is extracted and verified.In a normal authentication flow, the SAML response looks like this (note that some fields and attributes have been omitted for ease of reading):The SDK code would get as the first element of the `nodeList`, that is `nodeList[0]`, the signature referring to the entire SAML response, in fact the reference of the first signature `<ds:Reference URI="#response_id">` points to the root object `<samlp:Response ID="response_id" ...>`. Therefore, verifying this signature will ensure that the entire content of the SAML response is intact and authentic.However, there is no guarantee that the first signature refers to the root object, so if an attacker injects a signed element as the first element, all other signatures will not be verified. The only requirement is to have a legitimately signed XML element from the IdP, which is easily accomplished using the public metadata of the IdP.The SAML response would be structured like this: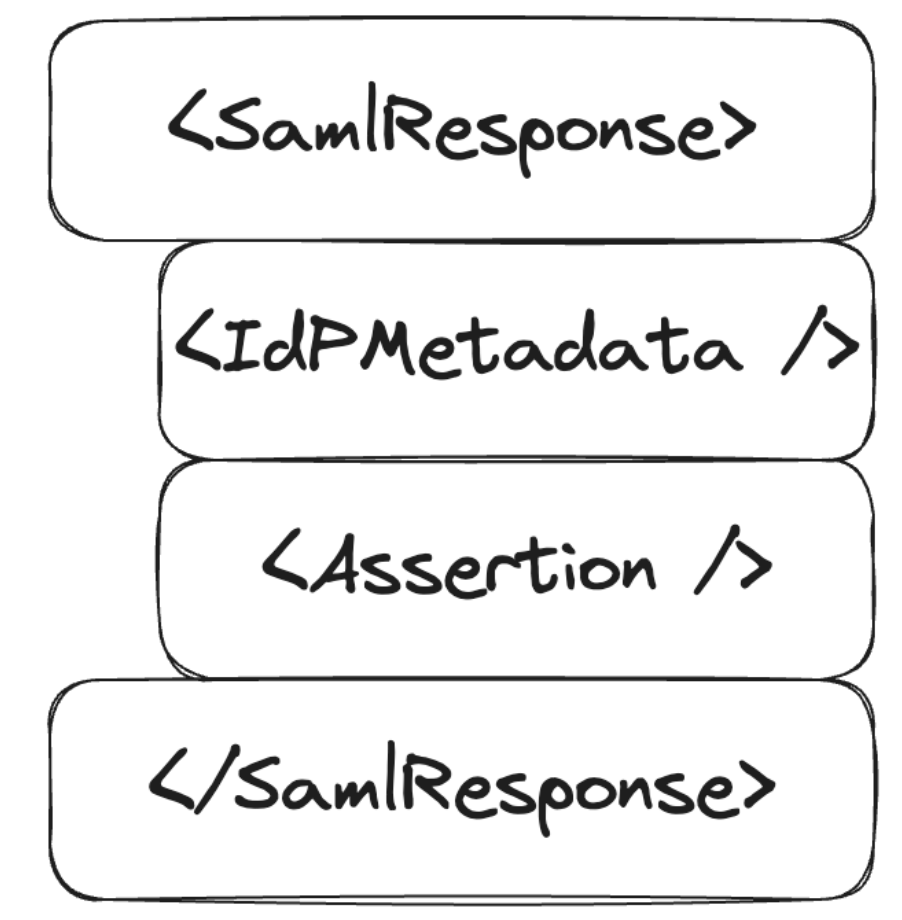ImpactAn attacker could craft an arbitrary SAML response that would be accepted by SPs using the vulnerable SDKs, allowing him to impersonate any Spid and/or CIE user.Complexity of the attackThe attacker needs an XML block containing a valid signature from one of the IdPs accepted by the SP. As described above, this requirement is satisfied by reading the public metadata of the IdP which is represented by a signed XML block of the IdP.Related issuesN/APoCClone the repository https://github.com/italia/spid-aspnetcore.gitFrom the root of the project, enter the folder relating to the example webapp: `samples/1_SimpleSPWebApp/SPID.AspNetCore.WebApp/`Change the value of the `AssertionConsumerServiceURL` key in the file `appsettings.json` to a custom domain: `https://$CUSTOM_DOMAIN:$CUSTOM_PORT/signin-spid`Compile and run the sample webapp using the following command, taking care to replace the placeholders with the same values used in step 3: `dotnet build "SPID.AspNetCore.WebApp.csproj" -o ./app/build && dotnet publish "SPID.AspNetCore.WebApp.csproj" -o ./app/publish && dotnet ./app/publish/SPID.AspNetCore.WebApp.dll -urls=https://$CUSTOM_DOMAIN:$CUSTOM_PORT`Visit URL: `https://$CUSTOM_DOMAIN:$CUSTOM_PORT/`Click "Enter with SPID" > "DemoSpid" (second IdP in the list)Visit the "Response" > "Check Response" sectionInsert the following string into the "Audience" field (right column): `https://spid.aspnetcore.it/`Click "Send response to Service Provider", note the redirect to `/home/loggedin` and consequently the correct execution of the login on the example portalRepeat steps 5 to 8 inclusiveIntercept the HTTP request generated in step 8 via an HTTP Proxy, such as PortSwigger's BurpSuitePerform URL-decoding and Base64-decoding of the POST `SAMLResponse` parameterInsert the content present at the following URL in the second line of the XML: https://demo.spid.gov.it/metadata.xmlChange the contents of the tag `<saml:Assertion>`, for example change the `email` attribute to an arbitrary value: `[email protected]`Run Base64-encoding and then URL-encoding the `SAMLResponse` parameterSend the request and note the redirect to `/home/loggedin` which demonstrates the correct identification and therefore also the verification of the arbitrary signature inserted in `SAMLResponse` despite the modification of the assertionRecommended SolutionVerify all signatures within the SAML response and do not accept unsigned XML elements.Referenceshttps://cheatsheetseries.owasp.org/cheatsheets/SAML_Security_Cheat_Sheet.htmlCredits[Abdel Adim `smaury` Oisfi](https://x.com/smaury92) di [Shielder](https://www.shielder.com)[Paolo`paupu` Cavaglià](https://x.com/paupu_95) di [Shielder](https://www.shielder.com)[Nicola `fromveeko` Davico](https://x.com/fromveeko) di [Shielder](https://www.shielder.com) | [] | null | 9.1 | null | null |
GHSA-2gmj-rvcm-f6j2 | An Improper Data Validation Vulnerability exists in Webmin 1.941 and earlier affecting the Command Shell Endpoint. A user may enter HTML code into the Command field and submit it. Then, after visiting the Action Logs Menu and displaying logs, the HTML code will be rendered (however, JavaScript is not executed). Changes are kept across users. | [] | null | null | null | null |
|
GHSA-jw9r-r4mj-mpxx | An unhandled exception vulnerability exists during Google Sign-In with Google API C++ Client before 2019-04-10. It potentially causes an outage of third-party services that were not designed to recover from exceptions. On the client, ID token handling can cause an unhandled exception because of misinterpretation of an integer as a string, resulting in denial-of-service and then other users can no longer login/sign-in to the affected third-party service. Once this third-party service uses Google Sign-In with google-api-cpp-client, a malicious user can trigger this client/auth/oauth2_authorization.cc vulnerability by requesting the client to receive the ID token from a Google authentication server. | [] | null | null | 8.6 | null |
|
GHSA-fmhc-m7qr-cvhx | genfilt in the AIX Packet Filtering Module does not properly filter traffic to destination ports greater than 32767. | [] | null | null | null | null |
|
CVE-2021-35996 | Adobe After Effects Memory Corruption Could Lead To Arbitrary Code Execution | Adobe After Effects version 18.2.1 (and earlier) is affected by a memory corruption vulnerability when parsing a specially crafted file. An unauthenticated attacker could leverage this vulnerability to achieve arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. | [
"cpe:2.3:a:adobe:after_effects:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] | null | 7.8 | null | null |
RHSA-2023:6137 | Red Hat Security Advisory: Migration Toolkit for Runtimes security update | HTTP/2: Multiple HTTP/2 enabled web servers are vulnerable to a DDoS attack (Rapid Reset Attack) | [
"cpe:/a:redhat:migration_toolkit_runtimes:1.0::el8"
] | null | 7.5 | null | null |
GHSA-7h8m-vrxx-vr4m | ZITADEL race condition in lockout policy execution | ImpactZITADEL provides administrators the possibility to define a `Lockout Policy` with a maximum amount of failed password check attempts. On every failed password check, the amount of failed checks is compared against the configured maximum.
Exceeding the limit, will lock the user and prevent further authentication.In the affected implementation it was possible for an attacker to start multiple parallel password checks, giving him the possibility to try out more combinations than configured in the `Lockout Policy`.Patches2.x versions are fixed on >= [2.40.5](https://github.com/zitadel/zitadel/releases/tag/v2.40.5)
2.38.x versions are fixed on >= [2.38.3](https://github.com/zitadel/zitadel/releases/tag/v2.38.3)WorkaroundsThere is no workaround since a patch is already available.ReferencesNoneQuestionsIf you have any questions or comments about this advisory, please email us at [[email protected]](mailto:[email protected]) | [] | null | 7.3 | null | null |
CVE-2020-1012 | WinINet API Elevation of Privilege Vulnerability | <p>An elevation of privilege vulnerability exists in the way that the Wininit.dll handles objects in memory. An attacker who successfully exploited the vulnerability could execute code with elevated permissions.</p>
<p>There are multiple ways an attacker could exploit the vulnerability:</p>
<ul>
<li><p>In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit this vulnerability and then convince a user to view the website. An attacker would have no way to force users to view the attacker-controlled content. Instead, an attacker would have to convince users to take action, typically by getting them to click a link in an email message or in an Instant Messenger message that takes users to the attacker's website, or by opening an attachment sent through email.</p>
</li>
<li><p>In a file sharing attack scenario, an attacker could provide a specially crafted document file that is designed to exploit this vulnerability, and then convince a user to open the document file.</p>
</li>
</ul>
<p>The security update addresses the vulnerability by ensuring the Wininit.dll properly handles objects in memory.</p>
| [
"cpe:2.3:a:microsoft:internet_explorer:11:-:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1607:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1709:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1803:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1809:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1903:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1909:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:2004:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_7:-:sp1:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_8.1:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_rt_8.1:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_server_2012:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2019:-:*:*:*:*:*:*:*"
] | null | 8.8 | null | null |
CVE-2023-20264 | A vulnerability in the implementation of Security Assertion Markup Language (SAML) 2.0 single sign-on (SSO) for remote access VPN in Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to intercept the SAML assertion of a user who is authenticating to a remote access VPN session. This vulnerability is due to insufficient validation of the login URL. An attacker could exploit this vulnerability by persuading a user to access a site that is under the control of the attacker, allowing the attacker to modify the login URL. A successful exploit could allow the attacker to intercept a successful SAML assertion and use that assertion to establish a remote access VPN session toward the affected device with the identity and permissions of the hijacked user, resulting in access to the protected network. | [
"cpe:2.3:o:cisco:adaptive_security_appliance_software:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:firepower_threat_defense:7.2.4:*:*:*:*:*:*:*"
] | null | 6.1 | null | null |
|
CVE-2014-4823 | The administration console in IBM Security Access Manager for Web 7.x before 7.0.0-ISS-WGA-IF0009 and 8.x before 8.0.0-ISS-WGA-FP0005, and Security Access Manager for Mobile 8.x before 8.0.0-ISS-ISAM-FP0005, allows remote attackers to inject system commands via unspecified vectors. | [
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.4:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.5:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.6:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.7:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_7.0_firmware:7.0.0.8:*:*:*:*:*:*:*",
"cpe:2.3:h:ibm:security_access_manager_for_web_appliance:7.0:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_8.0_firmware:8.0.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_8.0_firmware:8.0.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_web_8.0_firmware:8.0.0.4:*:*:*:*:*:*:*",
"cpe:2.3:h:ibm:security_access_manager_for_web_appliance:8.0:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_mobile_8.0_firmware:8.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_mobile_8.0_firmware:8.0.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_mobile_8.0_firmware:8.0.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:security_access_manager_for_mobile_8.0_firmware:8.0.0.4:*:*:*:*:*:*:*",
"cpe:2.3:h:ibm:security_access_manager_for_mobile_appliance:8.0:*:*:*:*:*:*:*"
] | null | null | null | 10 |
|
CVE-2006-4119 | SQL injection vulnerability in gc.php in GeheimChaos 0.5 and earlier allows remote attackers to execute arbitrary SQL commands via the Temp_entered_password parameter. NOTE: the provenance of this information is unknown; the details are obtained from third party information. | [
"cpe:2.3:a:chaossoft:geheimchaos:*:*:*:*:*:*:*:*"
] | null | null | null | 5.1 |
|
CVE-2024-50657 | An issue in Owncloud android apk v.4.3.1 allows a physically proximate attacker to escalate privileges via the PassCodeViewModel class, specifically in the checkPassCodeIsValid method | [
"cpe:2.3:a:owncloud:anroid_apk:*:*:*:*:*:*:*:*"
] | null | 6.8 | null | null |
|
CVE-2024-43812 | Kieback&Peter DDC4000 Series Path Traversal Insufficiently Protected Credentials | Kieback & Peter's DDC4000 series has an insufficiently protected credentials vulnerability, which may allow an unauthenticated attacker with access to /etc/passwd to read the password hashes of all users on the system. | [
"cpe:2.3:o:kieback\\&peter:ddc4400_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4002e_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4200e_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4002_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4100_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4200_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4200-l_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4400e_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4020e_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:kieback\\&peter:ddc4040e_firmware:*:*:*:*:*:*:*:*"
] | 8.6 | 8.4 | null | null |
GHSA-366h-qh6h-r996 | SQL injection vulnerability in hotel_habitaciones.php in Venalsur Booking Centre Booking System for Hotels Group 2.01 allows remote attackers to execute arbitrary SQL commands via the HotelID parameter. | [] | null | null | null | null |
|
GHSA-w7m8-qp22-mr27 | There is SQL Injection vulnerability at Helmet Store Showroom v1.0 Login Page. This vulnerability can be exploited to bypass admin access. | [] | null | 9.8 | null | null |
|
CVE-2018-6257 | NVIDIA GeForce Experience all versions prior to 3.14.1 contains a potential vulnerability when GameStream is enabled where improper access control may lead to a denial of service, escalation of privileges, or both. | [
"cpe:2.3:a:nvidia:geforce_experience:*:*:*:*:*:*:*:*"
] | null | null | 7 | 4.4 |
|
GHSA-33mx-vpmc-fg9c | Cross-Site Request Forgery (CSRF) vulnerability in Jenst Add to Header allows Stored XSS. This issue affects Add to Header: from n/a through 1.0. | [] | null | 7.1 | null | null |
|
GHSA-pc6c-fw6q-cfhj | In MuJS before version 1.1.2, a use-after-free flaw in the regexp source property access may cause denial of service. | [] | null | 10 | null | null |
|
GHSA-3pmr-x3j2-ff44 | In OpenCTI through 5.2.4, a broken access control vulnerability has been identified in the profile endpoint. An attacker can abuse the identified vulnerability in order to arbitrarily change their registered e-mail address as well as their API key, even though such action is not possible through the interface, legitimately. | [] | null | 7.5 | null | null |
|
CVE-2013-3503 | The Profile Importer feature in monarch.cgi in the MONARCH component in GroundWork Monitor Enterprise 6.7.0 allows remote authenticated users to read arbitrary files via an XML document containing an external entity declaration in conjunction with an entity reference, related to an XML External Entity (XXE) issue. | [
"cpe:2.3:a:gwos:groundwork_monitor:6.7.0:-:enterprise:*:*:*:*:*"
] | null | null | null | 3.5 |
|
GHSA-qj3r-6mr5-7w3m | Acrobat Reader DC versions 20.001.20085 (and earlier), 20.005.3031x (and earlier) and 17.012.30205 (and earlier) are affected by a use-after-free vulnerability that could lead to disclosure of sensitive memory. An attacker could leverage this vulnerability to bypass mitigations such as ASLR. Exploitation of this issue requires user interaction in that a victim must open a malicious file. | [] | null | 3.3 | null | null |
|
GHSA-wqgc-324m-v77q | In Symphony before 3.3.0, there is XSS in the Title under Post. The ID "articleTitle" of this is stored in the "articleTitle" JSON field, and executes a payload when accessing the /member/test/points URI, allowing remote attacks. Any Web script or HTML can be inserted by an admin-authenticated user via a crafted web site name. | [] | null | null | 4.8 | null |
|
GHSA-8x58-2qjg-xr22 | An issue was discovered in server.js in etcd-browser 87ae63d75260. By supplying a /../../../ Directory Traversal input to the URL's GET request while connecting to the remote server port specified during setup, an attacker can retrieve local operating system files from the remote system. | [] | null | 7.5 | null | null |
|
CVE-2023-23724 | WordPress WordPress Email Marketing Plugin – WP Email Capture Plugin <= 3.9.3 is vulnerable to Cross Site Request Forgery (CSRF) | Cross-Site Request Forgery (CSRF) vulnerability in Winwar Media WP Email Capture plugin <= 3.9.3 versions. | [
"cpe:2.3:a:winwar:wp_email_capture:*:*:*:*:*:wordpress:*:*"
] | null | 4.3 | null | null |
CVE-2000-1203 | Lotus Domino SMTP server 4.63 through 5.08 allows remote attackers to cause a denial of service (CPU consumption) by forging an email message with the sender as bounce@[127.0.0.1] (localhost), which causes Domino to enter a mail loop. | [
"cpe:2.3:a:lotus:domino:4.6.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:4.6.3:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:4.6.4:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:lotus:domino:5.0.8:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
CVE-2016-5882 | IBM iNotes is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. | [
"cpe:2.3:a:ibm:domino:8.5.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.2.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.2.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.2.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:8.5.3.6:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:domino:9.0.1.6:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.2.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.2.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:8.5.3.6:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:inotes:9.0.1.6:*:*:*:*:*:*:*"
] | null | null | 6.1 | 4.3 |
|
GHSA-6f54-mmf8-g8cp | NASM v2.16 was discovered to contain a segmentation violation in the component ieee_write_file at /output/outieee.c. | [] | null | 5.5 | null | null |
|
CVE-2023-6601 | Ffmpeg: hls unsafe file extension bypass in ffmpeg | A flaw was found in FFmpeg's HLS demuxer. This vulnerability allows bypassing unsafe file extension checks and triggering arbitrary demuxers via base64-encoded data URIs appended with specific file extensions. | [] | null | 4.7 | null | null |
GHSA-xq98-5rcf-5wqh | Directory Traversal in badjs-sourcemap-server | Affected versions of `badjs-sourcemap-server` resolve relative file paths, resulting in a directory traversal vulnerability. A malicious actor can use this vulnerability to access files outside of the intended directory root, which may result in the disclosure of private files on the vulnerable system.**Example request:**RecommendationNo patch is available for this vulnerability.It is recommended that the package is only used for local development, and if the functionality is needed for production, a different package is used instead. | [] | null | null | 7.5 | null |
GHSA-hv45-98mg-9h9w | Incorrect Access Control in the Preview Function of Gleamtech FileVista 9.2.0.0 allows remote attackers to gain unauthorized access via exploiting a vulnerability in access control mechanisms by removing authentication-related HTTP headers, such as the Cookie header, in the request. This bypasses the authentication process and grants attackers access to sensitive image files without proper login credentials. | [] | null | 9.4 | null | null |
|
CVE-2006-5569 | FtpXQ Server 3.0.1 installs with two default testing accounts, which allows remote attackers to read or write arbitrary files via unknown vectors. NOTE: the provenance of this information is unknown; the details are obtained from third party information. | [
"cpe:2.3:a:datawizard:ftpxq:3.0.1:*:*:*:*:*:*:*"
] | null | null | null | 6.4 |
|
GHSA-mmfc-3prc-gfcx | SQL injection vulnerability in post.php in Particle Blogger 1.0.0 through 1.2.0 allows remote attackers to execute arbitrary SQL commands via the postid parameter. | [] | null | null | null | null |
|
GHSA-484w-vg65-78pg | Stack-based buffer overflow in the *printf function implementations in PostgreSQL before 9.0.19, 9.1.x before 9.1.15, 9.2.x before 9.2.10, 9.3.x before 9.3.6, and 9.4.x before 9.4.1, when running on a Windows system, allows remote authenticated users to cause a denial of service (crash) and possibly execute arbitrary code via a floating point number with a large precision, as demonstrated by using the to_char function. | [] | null | null | null | null |
|
RHSA-2001:077 | Red Hat Security Advisory: : LPRng fails to drop supplemental group membership | security flaw | [
"cpe:/o:redhat:linux:7.0",
"cpe:/o:redhat:linux:7.1"
] | null | null | null | null |
CVE-2020-8174 | napi_get_value_string_*() allows various kinds of memory corruption in node < 10.21.0, 12.18.0, and < 14.4.0. | [
"cpe:2.3:a:nodejs:node.js:*:*:*:*:-:*:*:*",
"cpe:2.3:a:oracle:banking_extensibility_workbench:14.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:banking_extensibility_workbench:14.4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:blockchain_platform:*:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:mysql_cluster:*:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:retail_xstore_point_of_service:16.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:retail_xstore_point_of_service:17.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:retail_xstore_point_of_service:18.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:retail_xstore_point_of_service:19.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:retail_xstore_point_of_service:20.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:vmware_vsphere:*:*",
"cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:*",
"cpe:2.3:a:netapp:oncommand_insight:-:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"cpe:2.3:a:netapp:snapcenter:-:*:*:*:*:*:*:*"
] | null | 8.1 | null | 9.3 |
|
GHSA-95j5-rfpg-w4rp | The (1) AddWeightedPathSegLists and (2) SVGPathSegListSMILType::Interpolate functions in Mozilla Firefox before 42.0 and Firefox ESR 38.x before 38.4 lack status checking, which allows remote attackers to cause a denial of service (memory corruption) or possibly have unspecified other impact via a crafted SVG document. | [] | null | null | null | null |
|
CVE-2018-11045 | Pivotal Operations Manager, versions 2.1 prior to 2.1.6 and 2.0 prior to 2.0.15 and 1.12 prior to 1.12.22, contains a static Linux Random Number Generator (LRNG) seed file embedded in the appliance image. An attacker with knowledge of the exact version and IaaS of a running OpsManager could get the contents of the corresponding seed from the published image and therefore infer the initial state of the LRNG. | [
"cpe:2.3:a:pivotal_software:operations_manager:*:*:*:*:*:*:*:*"
] | null | null | 5.9 | 4.3 |
|
RHSA-2024:0421 | Red Hat Security Advisory: expat security update | expat: use-after free caused by overeager destruction of a shared DTD in XML_ExternalEntityParserCreate | [
"cpe:/o:redhat:rhel_eus:8.6::baseos"
] | null | 7.5 | null | null |
CVE-2004-1572 | AJ-Fork 167 does not restrict access to directories such as (1) data, (2) inc, (3) plugins, (4) skins, or (5) tools, which allows remote attackers to list files in those directories via a direct HTTP request. | [
"cpe:2.3:a:aj-fork:aj-fork:167:*:*:*:*:*:*:*"
] | null | null | null | 5 |
|
RHSA-2018:2161 | Red Hat Security Advisory: kernel security and bug fix update | hw: cpu: speculative store bypass | [
"cpe:/o:redhat:rhel_eus:7.3::computenode",
"cpe:/o:redhat:rhel_eus:7.3::server"
] | null | null | 5.6 | null |
RHSA-2022:2197 | Red Hat Security Advisory: rsync security update | zlib: A flaw found in zlib when compressing (not decompressing) certain inputs | [
"cpe:/o:redhat:rhel_e4s:8.1::baseos"
] | null | 8.2 | null | null |
GHSA-mf85-2mg4-mv8g | Multiple cross-site scripting (XSS) vulnerabilities in admin/index.php in moziloCMS 1.11.1 allow remote attackers to inject arbitrary web script or HTML via the (1) cat and (2) file parameters in an editsite action, different vectors than CVE-2008-6127 and CVE-2009-1367. | [] | null | null | null | null |
|
GHSA-v33p-6rrc-9595 | H3C B5 Mini B5MiniV100R005 was discovered to contain a stack overflow via the function SetMobileAPInfoById. | [] | null | 7.8 | null | null |
|
CVE-2024-20499 | Cisco Meraki MX and Z3 Teleworker Gateway AnyConnect VPN Denial of Service Vulnerability | Multiple vulnerabilities in the Cisco AnyConnect VPN server of Cisco Meraki MX and Cisco Meraki Z Series Teleworker Gateway devices could allow an unauthenticated, remote attacker to cause a DoS condition in the AnyConnect service on an affected device.
These vulnerabilities are due to insufficient validation of client-supplied parameters while establishing an SSL VPN session. An attacker could exploit these vulnerabilities by sending a crafted HTTPS request to the VPN server of an affected device. A successful exploit could allow the attacker to cause the Cisco AnyConnect VPN server to restart, resulting in the failure of the established SSL VPN connections and forcing remote users to initiate a new VPN connection and reauthenticate. A sustained attack could prevent new SSL VPN connections from being established.
Note: When the attack traffic stops, the Cisco AnyConnect VPN server recovers gracefully without requiring manual intervention. | [
"cpe:2.3:h:cisco:meraki_mx:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_z1:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_z4c_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_z4c:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_z4_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_z4:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_z3c_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_z3c:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_z3_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_z3:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_vmx_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_vmx:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx600_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx600:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx450_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx450:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx400_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx400:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx250_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx250:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx105_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx105:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx100_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx100:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx95_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx95:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx85_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx85:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx84_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx84:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx75_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx75:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx68w_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx68w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx68cw_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx68cw:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx68_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx68:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx67w_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx67w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx67c_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx67c:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx67_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx67:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx65w_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx65w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx65_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx65:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx64w_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx64w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:meraki_mx64_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:meraki_mx64:-:*:*:*:*:*:*:*"
] | null | 8.6 | null | null |
GHSA-wj25-rxgg-p3g9 | The Super Testimonials plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘alignment’ parameter in all versions up to, and including, 3.0.0 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | [] | null | 6.4 | null | null |
|
CVE-2018-1999 | IBM Business Automation Workflow 18.0.0.0, 18.0.0.1, and 18.0.0.2 could reveal sensitive version information about the server from error pages that could aid an attacker in further attacks against the system. IBM X-Force ID: 154889. | [
"cpe:2.3:a:ibm:business_automation_workflow:18.0.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_automation_workflow:18.0.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_automation_workflow:18.0.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.5.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.5.6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.5.6.0:cf1:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.5.6.0:cf2:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.5.7.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.5.7.0:cf2017.06:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.6.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:business_process_manager:8.6.0.0:cf2018.03:*:*:*:*:*:*"
] | null | null | 4.3 | null |
|
GHSA-3873-x9wv-xhwq | In Android before 2018-04-05 or earlier security patch level on Qualcomm Snapdragon Mobile and Snapdragon Wear MSM8909W, SD 210/SD 212/SD 205, SD 400, SD 410/12, and SD 800, while reading PlayReady rights string information from command buffer (which is sent from non-secure side), if length of rights string is very large, a buffer over read occurs, exposing TZ App memory to non-secure side. | [] | null | null | 7.5 | null |
|
RHSA-2023:4166 | Red Hat Security Advisory: java-1.8.0-openjdk security and bug fix update | OpenJDK: array indexing integer overflow issue (8304468) OpenJDK: improper handling of slash characters in URI-to-path conversion (8305312) | [
"cpe:/o:redhat:enterprise_linux:7::client",
"cpe:/o:redhat:enterprise_linux:7::computenode",
"cpe:/o:redhat:enterprise_linux:7::server",
"cpe:/o:redhat:enterprise_linux:7::workstation"
] | null | 3.7 | null | null |
CVE-2017-15054 | An arbitrary file upload vulnerability, present in TeamPass before 2.1.27.9, allows remote authenticated users to upload arbitrary files leading to Remote Command Execution. To exploit this vulnerability, an authenticated attacker has to tamper with parameters of a request to upload.files.php, in order to select the correct branch and be able to upload any arbitrary file. From there, it can simply access the file to execute code on the server. | [
"cpe:2.3:a:teampass:teampass:*:*:*:*:*:*:*:*"
] | null | null | 7.5 | 6.5 |
|
CVE-2024-11740 | Download Manager <= 3.3.03 - Unauthenticated Arbitrary Shortcode Execution | The The Download Manager plugin for WordPress is vulnerable to arbitrary shortcode execution in all versions up to, and including, 3.3.03. This is due to the software allowing users to execute an action that does not properly validate a value before running do_shortcode. This makes it possible for unauthenticated attackers to execute arbitrary shortcodes. | [] | null | 7.3 | null | null |
GHSA-r925-7gf3-qvf7 | OpenText Exceed OnDemand (EoD) 8 transmits the session ID in cleartext, which allows remote attackers to perform session fixation attacks by sniffing the network. | [] | null | null | null | null |
|
CVE-2024-12567 | Email Subscribers < 5.7.45 - Admin+ Stored XSS | The Email Subscribers by Icegram Express WordPress plugin before 5.7.45 does not sanitise and escape some of its form settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup). | [] | null | 4.8 | null | null |
ICSA-23-150-01 | Advantech WebAccess/SCADA | If an attacker can trick an authenticated user into loading a maliciously crafted .zip file onto Advantech WebAccess version 8.4.5, a web shell could be used to give the attacker full control of the SCADA server. | [] | null | null | 7.3 | null |
GHSA-4xg9-w3cx-2x89 | Incorrect implementation in user interface in Google Chrome on iOS prior to 83.0.4103.88 allowed a remote attacker to perform domain spoofing via a crafted HTML page. | [] | null | 6.5 | null | null |
|
CVE-2020-1158 | An elevation of privilege vulnerability exists when the Windows Runtime improperly handles objects in memory, aka 'Windows Runtime Elevation of Privilege Vulnerability'. This CVE ID is unique from CVE-2020-1077, CVE-2020-1086, CVE-2020-1090, CVE-2020-1125, CVE-2020-1139, CVE-2020-1149, CVE-2020-1151, CVE-2020-1155, CVE-2020-1156, CVE-2020-1157, CVE-2020-1164. | [
"cpe:2.3:o:microsoft:windows_10:1607:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1709:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1803:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1809:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1903:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1909:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:1803:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:1903:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:1909:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2019:-:*:*:*:*:*:*:*"
] | null | 7.8 | null | 6.8 |
|
GHSA-g7jh-888p-999r | The provided HCL Launch Container images contain non-unique HTTPS certificates and a database encryption key. The fix provides directions and tools to replace the non-unique keys and certificates. This does not affect the standard installer packages. | [] | null | 7.5 | null | null |
|
GHSA-q5v3-v9w6-hx5c | Vulnerability in the Oracle Financial Services Revenue Management and Billing product of Oracle Financial Services Applications (component: File Upload). Supported versions that are affected are 2.7.0.0, 2.7.0.1 and 2.8.0.0. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Financial Services Revenue Management and Billing. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Financial Services Revenue Management and Billing, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Financial Services Revenue Management and Billing accessible data as well as unauthorized read access to a subset of Oracle Financial Services Revenue Management and Billing accessible data. CVSS 3.0 Base Score 5.4 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N). | [] | null | null | null | null |
|
GHSA-542x-659m-wm39 | A HTTP Traversal Attack in earlier versions than ProSyst mBS SDK 8.2.6 and Bosch IoT Gateway Software 9.0.2 allows remote attackers to read files outside the http root. | [] | null | null | 7.5 | null |
|
GHSA-53q7-57w3-2j4r | Vulnerability in the MySQL Server product of Oracle MySQL (component: Server: DML). Supported versions that are affected are 8.0.21 and prior. Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in takeover of MySQL Server. CVSS 3.1 Base Score 7.2 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H). | [] | null | 7.2 | null | null |
|
CVE-2020-25493 | Oclean Mobile Application 2.1.2 communicates with an external website using HTTP so it is possible to eavesdrop the network traffic. The content of HTTP payload is encrypted using XOR with a hardcoded key, which allows for the possibility to decode the traffic. | [
"cpe:2.3:a:oclean:oclean:2.1.2:*:*:*:*:*:*:*"
] | null | 7.5 | null | 5 |
|
GHSA-gm28-rj7w-mj3m | An open redirect in the Login/Logout functionality of web management in AVSystem Unified Management Platform (UMP) 23.07.0.16567~LTS could allow attackers to redirect authenticated users to malicious websites. | [] | null | 5.4 | null | null |
|
GHSA-g3q3-27w2-fgmp | The Donation Forms by Charitable – Donations Plugin & Fundraising Platform for WordPress plugin for WordPress is vulnerable to privilege escalation in all versions up to, and including, 1.8.1.14. This is due to the plugin not properly verifying a user's identity when the ID parameter is supplied through the update_core_user() function. This makes it possible for unauthenticated attackers to update the email address and password of arbitrary user accounts, including administrators, which can then be used to log in to those user accounts. | [] | null | 9.8 | null | null |
|
CVE-2018-14972 | An issue was discovered in QCMS 3.0.1. upload/System/Controller/backend/down.php has XSS. | [
"cpe:2.3:a:q-cms:qcms:3.0.1:*:*:*:*:*:*:*"
] | null | null | 4.8 | 3.5 |
|
CVE-2022-40675 | Some cryptographic issues in Fortinet FortiNAC versions 9.4.0 through 9.4.1, 9.2.0 through 9.2.7, 9.1.0 through 9.1.8, 8.8.0 through 8.8.11, 8.7.0 through 8.7.6, 8.6.0 through 8.6.5, 8.5.0 through 8.5.4, 8.3.7 may allow an attacker to decrypt and forge protocol communication messages. | [
"cpe:2.3:a:fortinet:fortinac:*:*:*:*:*:*:*:*",
"cpe:2.3:a:fortinet:fortinac-f:*:*:*:*:*:*:*:*"
] | null | 6 | null | null |
|
GHSA-jpcj-fp88-pcp3 | The WebTextRenderer(WebInternal) _CG_drawRun:style:geometry: function in Apple Safari 2.0.3 allows remote attackers to cause a denial of service (application crash) via an HTML LI tag with a large VALUE attribute (list item number), which triggers a null dereference in QPainter::drawText, probably due to a failed memory allocation that uses the VALUE. | [] | null | null | null | null |
|
GHSA-h9r3-c5wc-q2vm | nCipher HSM before 2.22.6, when generating a Diffie-Hellman public/private key pair without any specified DiscreteLogGroup parameters, chooses random parameters that could allow an attacker to crack the private key in significantly less time than a brute force attack. | [] | null | null | null | null |
|
CVE-2023-39714 | Multiple cross-site scripting (XSS) vulnerabilities in Free and Open Source Inventory Management System v1.0 allows attackers to execute arbitrary web scripts or HTML via injecting a crafted payload into the Name, Address, and Company parameters under the Add New Member section. | [
"cpe:2.3:a:free_and_open_source_inventory_management_system_project:free_and_open_source_inventory_management_system:1.0:*:*:*:*:*:*:*"
] | null | 6.1 | null | null |
|
CVE-2017-9650 | An Unrestricted Upload of File with Dangerous Type issue was discovered in Automated Logic Corporation (ALC) ALC WebCTRL, i-Vu, SiteScan Web 6.5 and prior; ALC WebCTRL, SiteScan Web 6.1 and prior; ALC WebCTRL, i-Vu 6.0 and prior; ALC WebCTRL, i-Vu, SiteScan Web 5.5 and prior; and ALC WebCTRL, i-Vu, SiteScan Web 5.2 and prior. An authenticated attacker may be able to upload a malicious file allowing the execution of arbitrary code. | [
"cpe:2.3:a:automatedlogic:i-vu:*:*:*:*:*:*:*:*",
"cpe:2.3:a:automatedlogic:sitescan_web:*:*:*:*:*:*:*:*",
"cpe:2.3:a:carrier:automatedlogic_webctrl:*:*:*:*:*:*:*:*"
] | null | null | 7.8 | 4.6 |
|
GHSA-7g98-5gp8-66pw | UCMS 1.6 is vulnerable to arbitrary file upload via ucms/sadmin/file PHP file. | [] | null | 9.8 | null | null |
|
CVE-2024-12252 | SEO LAT Auto Post <= 2.2.1 - Missing Authorization to File Overwrite/Upload (Remote Code Execution) | The SEO LAT Auto Post plugin for WordPress is vulnerable to file overwrite due to a missing capability check on the remote_update AJAX action in all versions up to, and including, 2.2.1. This makes it possible for unauthenticated attackers to overwrite the seo-beginner-auto-post.php file which can be leveraged to achieve remote code execution. | [] | null | 9.8 | null | null |
CVE-2011-3195 | shared/inc/sql/lists.php in Domain Technologie Control (DTC) before 0.34.1 allows remote authenticated users to execute arbitrary commands via shell metacharacters in mailing list tunable options. | [
"cpe:2.3:a:gplhost:domain_technologie_control:*:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.24.6:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.25.1:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.25.2:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.25.3:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.26.7:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.26.8:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.26.9:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.27.3:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.28.2:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.28.3:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.28.4:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.28.6:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.28.9:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.28.10:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.1:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.6:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.8:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.10:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.14:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.15:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.16:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.29.17:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.30.6:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.30.8:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.30.10:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.30.18:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.30.20:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.1:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.2:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.3:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.4:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.5:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.6:*:*:*:*:*:*:*",
"cpe:2.3:a:gplhost:domain_technologie_control:0.32.7:*:*:*:*:*:*:*"
] | null | null | null | 6.5 |
|
CVE-2024-5823 | File Overwrite Vulnerability in gaizhenbiao/chuanhuchatgpt | A file overwrite vulnerability exists in gaizhenbiao/chuanhuchatgpt versions <= 20240410. This vulnerability allows an attacker to gain unauthorized access to overwrite critical configuration files within the system. Exploiting this vulnerability can lead to unauthorized changes in system behavior or security settings. Additionally, tampering with these configuration files can result in a denial of service (DoS) condition, disrupting normal system operation. | [
"cpe:2.3:a:gaizhenbiao:chuanhuchatgpt:*:*:*:*:*:*:*:*"
] | null | null | 6.5 | null |
CVE-2020-7759 | SQL Injection | The package pimcore/pimcore from 6.7.2 and before 6.8.3 are vulnerable to SQL Injection in data classification functionality in ClassificationstoreController. This can be exploited by sending a specifically-crafted input in the relationIds parameter as demonstrated by the following request: http://vulnerable.pimcore.example/admin/classificationstore/relations?relationIds=[{"keyId"%3a"''","groupId"%3a"'asd'))+or+1%3d1+union+(select+1,2,3,4,5,6,name,8,password,'',11,12,'',14+from+users)+--+"}] | [
"cpe:2.3:a:pimcore:pimcore:*:*:*:*:*:*:*:*"
] | null | 6.5 | null | null |
CVE-2024-28871 | Excessive CPU used on malformed traffic | LibHTP is a security-aware parser for the HTTP protocol and the related bits and pieces. Version 0.5.46 may parse malformed request traffic, leading to excessive CPU usage. Version 0.5.47 contains a patch for the issue. No known workarounds are available. | [
"cpe:2.3:a:oisf:libhtp:*:*:*:*:*:*:*:*"
] | null | 7.5 | null | null |
CVE-2024-7918 | Pocket Widget <= 0.1.3 - Admin+ Stored XSS | The Pocket Widget WordPress plugin through 0.1.3 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup). | [
"cpe:2.3:a:pocket_widget_wordpress_plugin:pocket_widget_wordpress_plugin:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ronvalstar:pocket_widget:*:*:*:*:*:wordpress:*:*"
] | null | 4.8 | null | null |
GHSA-4v28-8jj3-x7g5 | Exploiting Incorrectly Configured Access Control Security Levels vulnerability in McAfee Data Loss Prevention (DLP) for Windows versions prior to 10.0.505 and 11.0.405 allows local users to bypass DLP policy via editing of local policy files when offline. | [] | null | null | 7.4 | null |
|
CVE-2021-33923 | Insecure permissions in Confluent Ansible (cp-ansible) 5.5.0, 5.5.1, 5.5.2 and 6.0.0 allows local attackers to access some sensitive information (private keys, state database). | [
"cpe:2.3:a:confluent:cp-ansible:5.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:confluent:cp-ansible:5.5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:confluent:cp-ansible:5.5.2:*:*:*:*:*:*:*",
"cpe:2.3:a:confluent:cp-ansible:6.0.0:*:*:*:*:*:*:*"
] | null | 5.5 | null | 2.1 |
|
GHSA-4hq8-3ffh-25xf | Denial of service in BIND named via maxdname. | [] | null | null | null | null |
|
CVE-2003-1035 | The default installation of SAP R/3 46C/D allows remote attackers to bypass account locking by using the RFC API instead of the SAPGUI to conduct a brute force password guessing attack, which does not lock out the account like the SAPGUI does. | [
"cpe:2.3:a:sap:sap_r_3:*:*:*:*:*:*:*:*",
"cpe:2.3:a:sap:sapgui:4.6c:*:windows:*:*:*:*:*",
"cpe:2.3:a:sap:sapgui:4.6d:*:windows:*:*:*:*:*"
] | null | null | null | 7.5 |
Subsets and Splits
No saved queries yet
Save your SQL queries to embed, download, and access them later. Queries will appear here once saved.